9+ Logistics Risk Assessment Templates in PDF | MS Word
Risks are everywhere, and they significantly affect businesses. And when dealing with the supply chain, transportation, warehousing, and manufacturing all…
Jun 20, 2020
A fraud risk assessment is a type of management that is a device utilized by the board to distinguish and comprehend dangers to its business and shortcomings in controls that present a misrepresentation hazard to the association. When fraudulent activity is distinguished, an arrangement can be created to alleviate those dangers by establishing controls or methodology and allotting people to screen and effectuate the arrangement of moderation.

 nd.gov
nd.gov ec.gc.ca
ec.gc.ca protiviti.com
protiviti.com algaonline.org
algaonline.org brownwoodtexas.gov
brownwoodtexas.gov media.defense.gov
media.defense.gov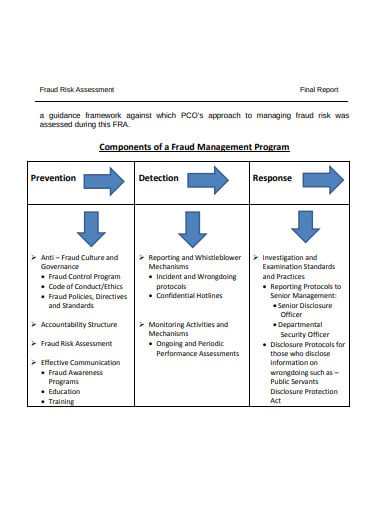 canada.ca
canada.ca valdosta.edu
valdosta.edu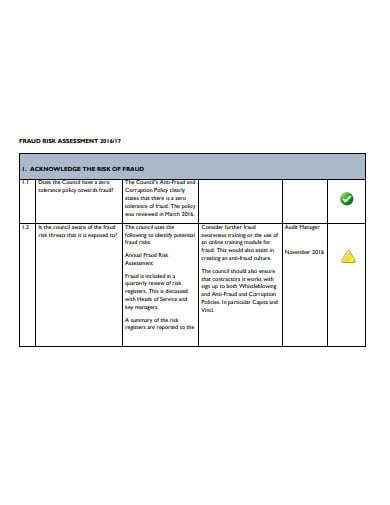 hart.gov.uk
hart.gov.uk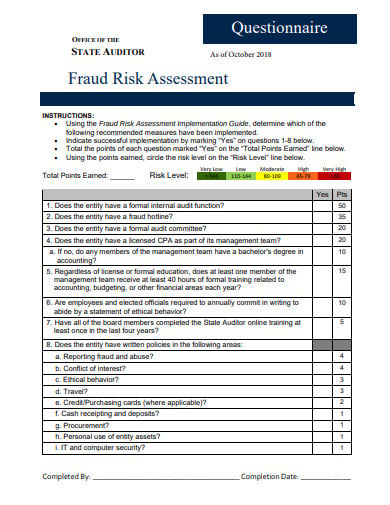 auditor.utah.gov
auditor.utah.gov unwe-yearbook.org
unwe-yearbook.orgIneffective to compelling.
Risks have now become a part and parcel of our day to day life. Every company has certain motives that are prone to risks and might issue them a liability. The stake they put up is to risk their assets in terms of high benefits. Just like the shareholders play their cards risking a good deal of money, a risk analyst can determine and introspect the outcomes coming out.
During the initial phase during the time spent its evaluation dangers, you first need to comprehend what establishes IT dangers. IT dangers are those issues and worries that are raised identified with the utilization of data and innovation in the association. When you comprehend this idea, you have to continue to the distinguishing proof procedure. This procedure includes recognizing all the significant IT resources of the organization. After you have recognized that, you have to organize the benefits.
The following stage of the procedure is to foresee the potential dangers of the organization. These dangers can be both inner just as outside. The interior dangers include those risks that emerge inside the association and can be put under check. The outer dangers of the organization include those dangers that emerge outside the association and are commonly outside the control of the association. You have to foresee these dangers before proceeding onward to the subsequent stage.
The third step of the procedure is to do the evaluation. For this, you have to allude to the two arrangements of dangers you have made before. To start with, allude to the rundown where you have noted down the different IT resources and their hazard, and contrast it with the inward and outside danger list. You have to consider every advantage and hazard separately cautiously. Likewise, the evaluation additionally should be done separately.
At the point when you are done with the evaluation of the dangers, you can continue to the relief step. In this progression, you have to allude to the appraisal results you got. In light of these outcomes, you have to build up an arrangement or approach to relieving the dangers. The best instrument for this undertaking is a security strategy. The security strategy sets up decides and guidelines that guarantee the wellbeing and security of the considerable number of advantages of the organization.
The last advance of this procedure is to make an anticipation arrangement. This arrangement should be made remembering the evaluation results and the moderation plan. The counteraction plan will guarantee that there are no such dangers later on. Also, if such dangers emerge, the counteraction plan must feature steps that ought to be taken to relieve those dangers.

Risks are everywhere, and they significantly affect businesses. And when dealing with the supply chain, transportation, warehousing, and manufacturing all…

The audit assessment indicates to the general, orderly, examination, evaluation and the analysis of the business marketing conditions, both internal…

Security Assessment Questionnaire (SAQ) is basically a cloud duty for guiding business method management evaluations among your external and internal…

The leadership assessment survey template is formed with the aim of understanding business success to be an instantaneous reflection of…

Portfolio Assessment is the collective term for the assessment of a student’s work. This is the assessment of the student’s…

Formative assessment refers to a large sort of strategy that lecturers use to conduct in-process evaluations of student comprehension, learning…

A fraud risk assessment is a type of management that is a device utilized by the board to distinguish and…

assessment templates word assessment pdf assessment pages assessment free assessment template health assessment hospitality industry risk assessment gifts and hospitality…

The establishment of an audit is referred to as risk assessment. Audit risk assessment methods are performed to acquire an…