
40+ Word Checklist Templates
Due to limited memory and attention, we humans often forget to do tasks which we were supposed to perform. Our…
Sep 20, 2023
955 In any multinational company, you should manage database security to avoid any unauthorized or unintended access to your private data. Database security includes a wide range of topics like computer security, risk management, and information security as well. To protect the database system from cyber attackers you should be prepared to secure the database and ensure the protection of the organization’s operations. Use checklist templates to prepare a convenient database security checklist with all the necessary details.


This means that you need to check if users are authenticated with the database during setup. Yo need to grant access to users to strict datasets and permissions. A sophisticated configuration needs to be developed between application users and database users. Therefore, you need to figure out a strong authentication mechanism.
The next step is to check whether you can monitor and track who can access sensitive data related to the database. For that, you also need to identify the type of database you can use. You need special auditing to separate application users from database users.
Checking the encryption system is to affirm the data storage and backups. Strong encrypting codes protect the stored files and backup history from cyber theft. You may also need to identify the specific data that requires encryption like different clients wth single encryption or vice versa.
To ensure security issues, you have to check the requirements that are important to segregate clients who share the same database server. These databases need specific treatment for auditing, authorization and restricting them from subsets of the database.
Data governance is necessary to monitor data across different silos since the data is complex and requires transforming from the internal to an external organization or vice versa. For this process to complete successfully, you can implement management policies to complete the data lifecycle and then check their data flow.
 who.int
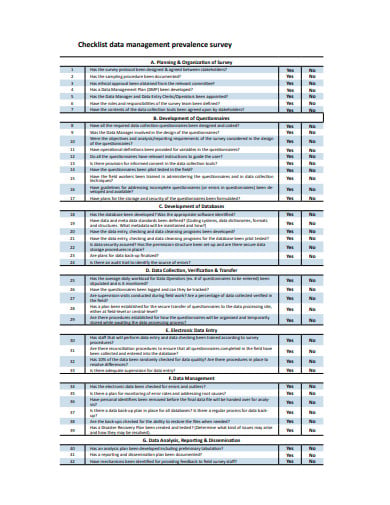
who.intIf you are worried about the security of your company database, then you should get yourself this Database Security Checklist Template in PDF format. You can make check whichever criteria should be maintained to keep your database secure. Since it is compatible with your editing software you can easily monitor the changes for a secured system of your organization!
 missouri.edu
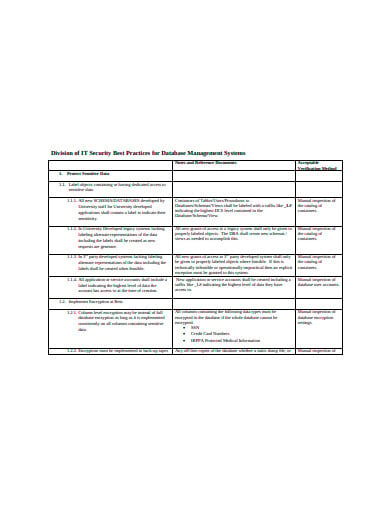
missouri.eduThis Database Security Management checklist template will make your life easier as we have designed this keeping the requirements of a secured database server in mind. This sample checklist can be of great use if you want to confirm the key and domain elements of a robust software management system. However, if you need some other file format to view and edit your document then explore some of our checklists in Pages format for Apple users!
 eac.gov
eac.govWhen the elections are approaching soon, then you need to be well-prepared with a uniform and non-discriminatory election system. One way to make sure that your policies are implemented is to download and use this Voter Registration Database Security Checklist Example that has all the prerequisites of a form checklist. You will get all the ready-made information about access control, audibility, and detection and database control. We also provide multiple versatile sample checklists that you can check out if you are willing to try out different file formats!
 meity.gov.in
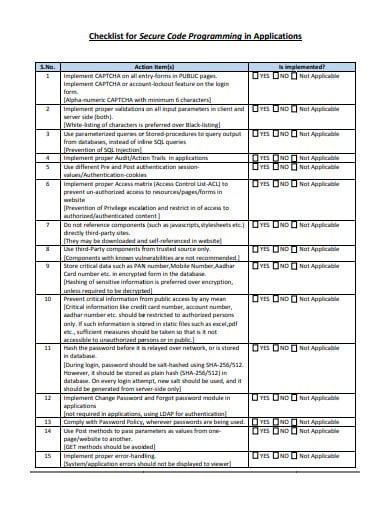
meity.gov.inTo maintain data confidentiality of your database systems, it’s important to draft appropriate agreements between two parties so that information remains within the internal workflow within the system. This Database Security Application Checklist Template is designed to provide you with the required data that you need to create a secure system. For your convenience, we have designed multiple other checklist examples that you can follow and refer to while creating your personalized checklist. So what are you waiting for?
 novascotia.ca
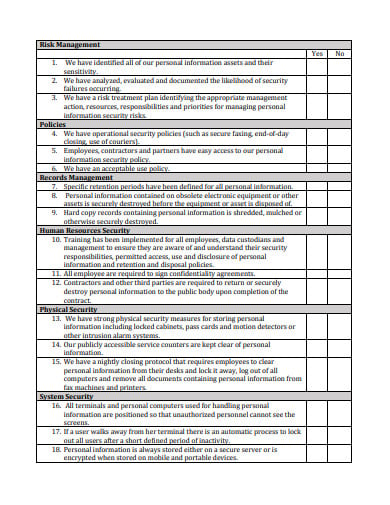
novascotia.caToo much involved in making a safe and secure system for your IT software? However, you can save both your time and energy in preparing a well-protected server for your computer security by downloading this Simple Database Security Checklist and getting all your tasks done in a jiffy. The best part about this template is that you can easily make changes to the checklist if you find any of the data misleading. Still, if you have other file formats then you should check out these samples of checklists in Google Sheets for your convenience!
 pcisecuritystandards.org
pcisecuritystandards.orgThis Database Security Awareness checklist sample template has been created to enhance the knowledge of your employees in your department about data security and management. It compiles all the information related to creating a security awareness program, implementing awareness, sustaining and documenting the program. This file highly customizable and adaptable with all your portable devices so you can make any changes you want in the template before you put it to use!
 hopkinsmedicine.org
hopkinsmedicine.orgTo enable data security management in your organization, all you need to do check the domain elements of a secured system and what better way to do it other than using a security checklist? Our Database Security Checklist Template in DOC format helps you to rule out all the necessary components of database security. You can use its pre-built content or choose to make your customizations. You can even check out other samples of checklist templates form our websites to see if they suit your purpose!

Due to limited memory and attention, we humans often forget to do tasks which we were supposed to perform. Our…

A facility maintenance checklist is a priceless defense means to keep a building reliable and safe by periodical planning, checkups,…
A Recruitment Checklist is the to-do-list where you list down all the important details that you need to do or…

Logistics Performance Index indicates that America is one of the leading logistics industries in the globe. Its networks coordinate with…

The best way you can make sure that all cleaning go as planned is to have a cleaning checklist samples.…

A Resume Screening Checklist is a checklist that is prepared by the recruiter to list all the important points based…

HR Compliance Checklist is the tool that is used by HR professionals to make the preparations for the HR tools.…

A retirement party is the opportunity to celebrate the retiree’s past achievements as well as their future efforts. The party…

The mortgage business has gone through a lot of chapters in the industry, combating business challenges every year. According to…