
40+ Word Checklist Templates
Due to limited memory and attention, we humans often forget to do tasks which we were supposed to perform. Our…
Sep 20, 2023
A checklist refers to the list of items or tasks that need to done to reach a predetermined goal or objective. Network or cyber security is a defense against intrusion, abuse and unwanted code changes from the access to files and directories in a computer network. The anti-virus program is an example of network security.


 cosn.org
cosn.org techtalk.gfi.com
techtalk.gfi.com dell.com
dell.com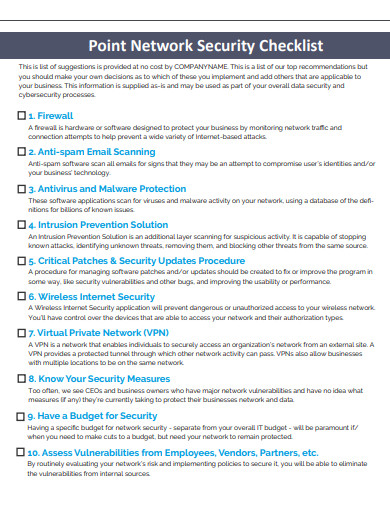 midnightbluetech.com
midnightbluetech.com fifedirect.org.uk
fifedirect.org.uk losmedanos.edu
losmedanos.eduTrack the traffic going in and out of your firewall, and carefully read the files. Allow no dependence on warnings to flag dangerous activity. Be sure that everyone on the team understands the data and is prepared to take the action necessary.
Keep a close eye on potential threats as they emerge and are posted on the internet. Trend Micro’s Trend Watch platform, for instance, monitors current threat behavior. You may also get U.S. Software Emergency Readiness Team (US-CERT, a Homeland Security division) email warns you about the vulnerabilities and exploits of recently verified devices.
Your company must install strong front line security at the edge of the network to prevent threats from getting in. Enable daily updates to ensure your firewall and antivirus software is stable.
Continuously train staff so they recognize any modifications to the policy of appropriate use. Sometimes, promote a surveillance strategy called “neighborhood watch.” When an individual finds something unusual, such as not being able to sign in to an email address promptly, he or she will instantly alert the correct person.
Install a system to protect the data. This type of system will protect your company against loss of data if it violates the security of your network.
Consider external protection technologies that will further secure your infrastructure, and extend the capabilities of your business.
Not every user ought to be able to access their network. You need to remember every user and every system to keep out possible attackers. Then you will get your security measures implemented. You can restrict un-compliant endpoint tools or only allow restricted access to them. This method is the Control of Network Access (NAC).
“Malware,” or “malevolent applications or software,” includes malware, worms, Trojans, ransomware, spyware and other such things. Malware often infects a network but remains inactive for weeks or even months. In addition to scanning for malware upon entry, the best anti malware programs often continuously monitor files afterward to detect irregularities, delete malware, and repair damages.
Every technology you use to run your company needs to be secured, whether it is being developed by your IT department or whether you are buying it. However, there may be gaps or bugs in any program that criminals may use to penetrate your network. Application protection includes the hardware, software, and procedures that you are using to close those gaps.
You need to learn what normal activity looks like to detect irregular network behaviors. Tools for conduct analytics automatically detect actions that diverge from the norm. Your safety team will then better identify vulnerability signs that pose a potential risk, and address threats quickly.
Institutions need to ensure that their personnel is not sending sensitive data outside the system. Avoidance of data loss, or Data Loss Prevention (DLP), innovations can halt the uploading, transmitting, or even publishing of crucial information in an unsafe way.
Firewalls create a buffer between your trustworthy internal network and untrustworthy external networks, including the Internet. They make use of a set of regulations specified to permit or block traffic. A firewall can be an application, hardware, or both. Cisco provides unified threat management (UTM) tools and next-generation firewalls (NGFW) based on threats.
On many fronts, your company faces threats and the more customers, gadgets, and applications you introduce, the more insecure your network is. Network or cybersecurity is a defense against intrusion, abuse and unwanted code changes from the access to files and directories in a computer network. The anti-virus program is an example of network security.
The authentication key to the network is best known as the password for the Wifi or Wireless network. It is the code you use while connecting to a wireless connection. Each wireless network or router comes with a preset network security key which can be changed in the device’s settings tab.
There are several types of networks available in operation. Some of the forms of network protection available include Distributed Denial of Service (DDoS) Attack Prevention, Firewalls, Email Gateways, Intrusion Prevention / Detection System (IPS / IDS), Protection for Information and Event Management (SIEM) Systems, Network Access Control (NAC), Virtual Private Networks (VPNs), etc.
Network security is of four types. This includes:
LAN or Local Area Network
PAN or Personal Area Network
MAN or Metropolitan Area Network
WAN or Wide Area Network
Network Security is aimed at keeping the network running and secure for all legitimate customers. A strong network protection program helps reduce the risk of succumbing to data theft and manipulation by companies. Network protection helps protect your workstations from spyware which is dangerous. It also guarantees the safeguarding of shared records.

Due to limited memory and attention, we humans often forget to do tasks which we were supposed to perform. Our…

A facility maintenance checklist is a priceless defense means to keep a building reliable and safe by periodical planning, checkups,…
A Recruitment Checklist is the to-do-list where you list down all the important details that you need to do or…

Logistics Performance Index indicates that America is one of the leading logistics industries in the globe. Its networks coordinate with…

The best way you can make sure that all cleaning go as planned is to have a cleaning checklist samples.…

A Resume Screening Checklist is a checklist that is prepared by the recruiter to list all the important points based…

HR Compliance Checklist is the tool that is used by HR professionals to make the preparations for the HR tools.…

A retirement party is the opportunity to celebrate the retiree’s past achievements as well as their future efforts. The party…

The mortgage business has gone through a lot of chapters in the industry, combating business challenges every year. According to…