
11+ Remuneration Policy Templates in PDF | Ms Word
Arrangements on a remuneration policy are significant reports made by associations crosswise over different fields for giving standards to moral…
Sep 14, 2023
An Info Technology (IT) Security Policy identifies the foundations and procedures for all people accessing an organization’s IT assets and resources. Effective IT Security Policy could be a model of the organization’s culture, during which rules and procedures are driven from its employees’ approach to their info and work. Thus, an efficient IT security policy could be a distinctive document for every organization, cultivated from its people’s views on risk tolerance, however, they see and price their info, and also the ensuing availableness that they maintain of that info.


 cert-in.org.in
cert-in.org.inThe safety and security of an IT company require the utmost importance. This can be done by considering all the situations and having an idea about what IT security policy is about. You’ll be able to create this policy simply with the assistance of this Standard IT Security Policy Template. This example has been created to make it obtainable for you and to assist you with this precise task.
 hse.ie
hse.ieWhen you are running a company, you want to have a security policy in situ. This policy highlights the item to be safeguarded and is done to assist, keep the assets of the corporate safe and secure. If you wish to create this policy for your business/company, then you will necessitate using this IT security policy example template in PDF format.
 bsc.edu
bsc.eduWondering why you would like a security policy in place? Well, while not this policy you would like to just accept the fact that something unforeseen situation might arise in the future and might destroy the IT assets of your company. Eliminate such a risk for your company and create an acceptable security policy with the assistance of our security policy example. This example will assist you to create such policies with ease.
 nsit.ac.in
nsit.ac.inA corporate security policy is formed to confirm the protection and security of the varied assets of the corporate. This policy isn’t simple to create. That is why we tend to give our company data security policy examples to assist you to create this policy for your corporation which can even help you to complete your IT Auditing. All you would like to try and do is transfer this PDF example and fill within the needed details.
 acinitial.com
acinitial.comMaking company security policies is extremely necessary. However, all corporates agree that creating this policy isn’t the least bit simple. What if we are saying that we can now help you with examples based on IT Security summary templates which is a lot easier and less complicated for you? A hassle basic cognitive process? Then transfer this sample security policy example now in PDF format!
 mpg.de
mpg.deAn IT corporate security policy template is the best tool to confirm that the assets of your company area unit are safe and secure. It can be tedious to make a security policy following the Max Planck Society without reading and understanding what it is. Make sure to go through this template and understand things in subjective details with brief intersections mentioned in this PDF template.
 intelligencenode.com
intelligencenode.comSome folks assume that a cyber security policy is a concern of solely the IT department. However, that’s much not true. Each worker of a corporation plays a job in maintaining the safety of the cyber-security department of the corporation. Create an apt security policy for your organization preventing any exploitation of company data by following the guidelines from this template.
 prbdb.gov.in
prbdb.gov.inWith this Information Technology Security policy example, you’ll get access to a file containing a model security policy that may function the guide to assist you to create yours. The example options original and suggestive headings and content written by skilled writers. So don’t delay in guarding your benefits and assets of your company.
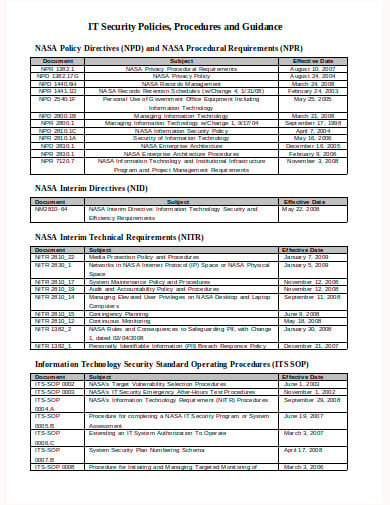 nasa.gov
nasa.govThe most necessary factor to recollect concerning creating a security policy arrange is to create it as a straightforward document as attainable. It can’t be expected that the staff can follow a security policy that they are doing not perceive. Do you find an inquisitive way to do this? Use this example template on the IT Security Policy example. This example has been created specifically to assist you to create company security policies.
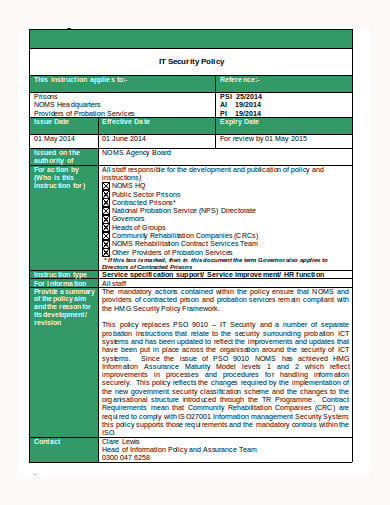 justice.gov.uk
justice.gov.ukAn organization’s security policy can play an over sized role in its choices and direction, however, it shouldn’t alter its strategy or mission. Therefore, it’s vital to put in writing a policy that’s drawn from the organization’s existing cultural and structural framework which can be done with this template to support the continuity of excellent productivity and innovation, and not as a generic policy that impedes the organization and its folks from meeting its mission and goals.
 nalcoindia.com
nalcoindia.comThe objectives of the IT security policy is the preservation of confidentiality, integrity, and availableness of systems and knowledge utilized by an organization’s members. This template based on the Format IT security policy will help you to make you amend your policies and make the best fit for your company. Also, look at marketing policy templates to make your IT firm the largest.
The first factor that you simply have to be compelled to do whereas creating a security policy is to work out the necessity for it. Generally, a security policy is placed into action within the company sector to safeguard the assorted assets of the corporate. However, your corporation might produce other reasons too. Take into account these reasons fastidiously and you may get to grasp what content to incorporate within the policy.
The main reality regarding security policy is that it works as long as it’s followed by everyone. And for everyone to follow the policy, you wish to form positivity that the policy is easy and simple to know. Consequently, you wish to feature content to the policy that’s straightforward to interpret. Attempt to keep the policy as short and as precise as potential. You can’t expect the staff within the company to abide by rules that they are not able to understand due to the complexity of the content.
You are creating the protection policy certainly specific reasons. These reasons determine the goals that you simply wish to realize through the implementation of the policy. For instance, if you’re creating the protection policy for the protection and security of your physical assets, then your established goal would be to form ways that the assets stay safe.
As stipulated by the National Analysis Council (NRC), the specifications of any company policy ought to address:
1. Objectives
2. Scope
3. Specific goals
4. Responsibilities for compliance and actions to be taken within the event of rebelliousness.
Whenever any new policy is formed within the company, a team is formed to hold out the roles and responsibilities to take care of that policy. Similarly, it applies to the protection policy to confirm that the policy is functioning effectively, which needs to be compelled to assign duties to the individuals. In general, the protection policy of an organization involves all the staff to perform some role or have some responsibility.
The last vital item that has to be enclosed within the policy is that the list of consequences. These consequences confirm what’s going to happen if somebody fails to follow any of the principles mentioned in the policy. The common consequence is an action at law because it involves the protection of the assets of the corporate. For a lot of infringed cases, warnings are given per the actions performed.

Arrangements on a remuneration policy are significant reports made by associations crosswise over different fields for giving standards to moral…

Grooming policy is the rule or the protocol that an employee has to follow when he becomes the employee of…

A dress code policy is defined as a set of guidelines to make it easy for the employees to know…

A sales commission policy fulfills the policy of establishing responsibilities for setting commission rates and to define the point at…

A confidentiality policy implies individual correspondence or data identifying with an association’s business that is obscure to general society and…

The dividend policy is a financial decision that indicates the balance of the firm’s wages to be paid out to…

The payment policy is the set of rules or directions that guides a customer to make the bill payment templates.…

Bonus Policy can be referred to as the protocol formulated in an organization based on which the employees are given a…

Recruitment policy is the practice that a company exhibits while hiring employees. It a statement that outlines the rules and…