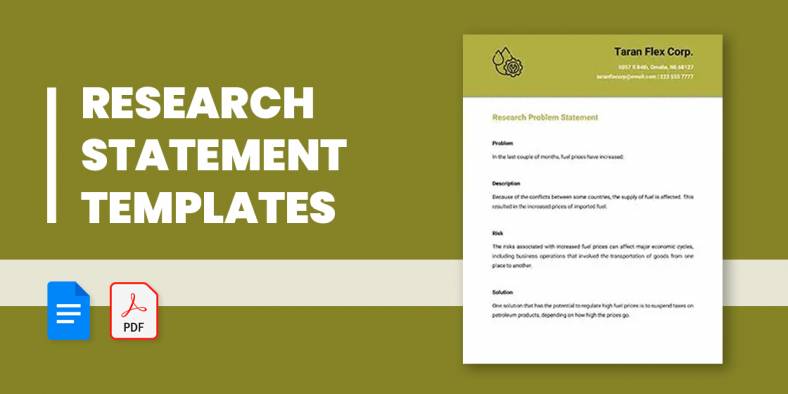
24+ Research Statement Templates in PDF | DOC
In a statement of purpose for research, you would like to try an in-depth analysis of knowledge and stats. You…
Sep 06, 2023
A security statement refers to any written or verbal declaration of an undertaking to provide protection. Safety and privacy policies are now used with the advent of the digital technologies to protect internet users and customers. It is also known as a security report. Every time a specific incident happens a security report should be issued. The type of the incident depends on your company, but could involve burglary, a break-in, a fire, abuse of property by employees and trespassing.

 goldmansachs.com
goldmansachs.com checkpoint.com
checkpoint.com websense.com
websense.com hubspot.net
hubspot.net elekta.com
elekta.com dl.tvcdn.de
dl.tvcdn.de m-files.com
m-files.com traviscu.org
traviscu.org plantronics.com
plantronics.com foi.nhsgrampian.org
foi.nhsgrampian.org doe.state.nj.us
doe.state.nj.usThe important security methods to protect data, information and privacy should be applied from the router that provides access to the Internet in the home to the infrastructure of the top modern cities. There is an increasing threat of cyber-attacks on equipment, whether from terrorists, cyber criminals seeking useful data or simply bored people seeking a new thrill or challenge. That’s why it’s essential to have some information about security issues and how each of us can affect that.
Malware is a common term representing any virus. When you mix malicious intent with tech, that is what you get: malware. Trojans and worms are known malware versions. Risk assessment agencies should also suggest that you do not click on links or attachments in emails you do not know.
An emerging persistent threat (APT) is a network intrusion in which an unknown individual achieves entrance to a network and stays undetected there for a long time. An APT assault is intended to steal data rather than inflict network or organizational harm. APT assaults high-value information targeting organizations in sectors such as national defense, production, and the financial sector.
Ransomware is malicious software that blocks access to the authentication server system, typically by encoding data on a hard drive to extortion a ransom to restore access for the criminals responsible. The theft of data collected by users and businesses on various sites has been one of the many significant phenomena in recent years. The effect that it can have on users is very troubling by stopping them from accessing any of their information due to malicious code activity.
This is a mixture of illegal data theft by hacking and public disclosure of internal information that reflects a problem that is growing.
Security notices are not only written when an incident occurs, as events hopefully do not occur with regularity of any kind. You might also need to write safety reports such as:
The daily security statement or daily security report, generally referred to as the DAR of an officer, is the first and most significant form of security reporting. This report is a first-hand account of your guard’s activities as a Security Officer while in duty. No manager should be unable to comprehend what a report is trying to mean.
A report refers to a document that provides data for a specific audience and intent in an structured format. Even though abstracts of reports that be presented verbally, full reports are mostly in the form of written articles. Documents play an significant role in company growth in the current business scenario.
A security officer has an essential critical job to do, whether he works in a mall or office building. It’s his duty to be vigilant and to secure his clientele. The few elements that are needed to be there in a security officer are alertness, honesty, physical fitness, good communication skills, and ability to serve client’s needs.
There are two main types of informal and formal reports: descriptive and quantitative reports. It is essential to bear in mind that both informal and formal documents that fit into those groups; in other words, you might have an informal document or a formal report.
The event report’s aim is to record the exact details of the occurrence while it’s fresh in the minds of those who witnessed the case. In the future, this information can be useful when dealing with the liability problems arising from the accident.

In a statement of purpose for research, you would like to try an in-depth analysis of knowledge and stats. You…
A suitable statement for employment outlines any supporting explanation of your skills, proving that you are ideal for the employment…

The written statement is a legal statement that the people have to go through when they face some legal ups…

A disclosure statement is the synopsis of the terms, conditions, risks, and rules that are involved in any financial transactions…

A salary statement is a form that provides different components of an employee’s salary and the cost incurred payments. It…

A document that explains the significance of the research work you did is known as an impact statement. It is…

Statement of Expenditure is a multi-column self-balancing monthly statement of expenditures of an operative level workplace. It is created to…

When you write a sworn statement or testimony, you’re testifying beneath oath, and your words can become a part of…

A purpose statement announces the aim, scope, and direction of the paper. It tells the reader what to expect in…