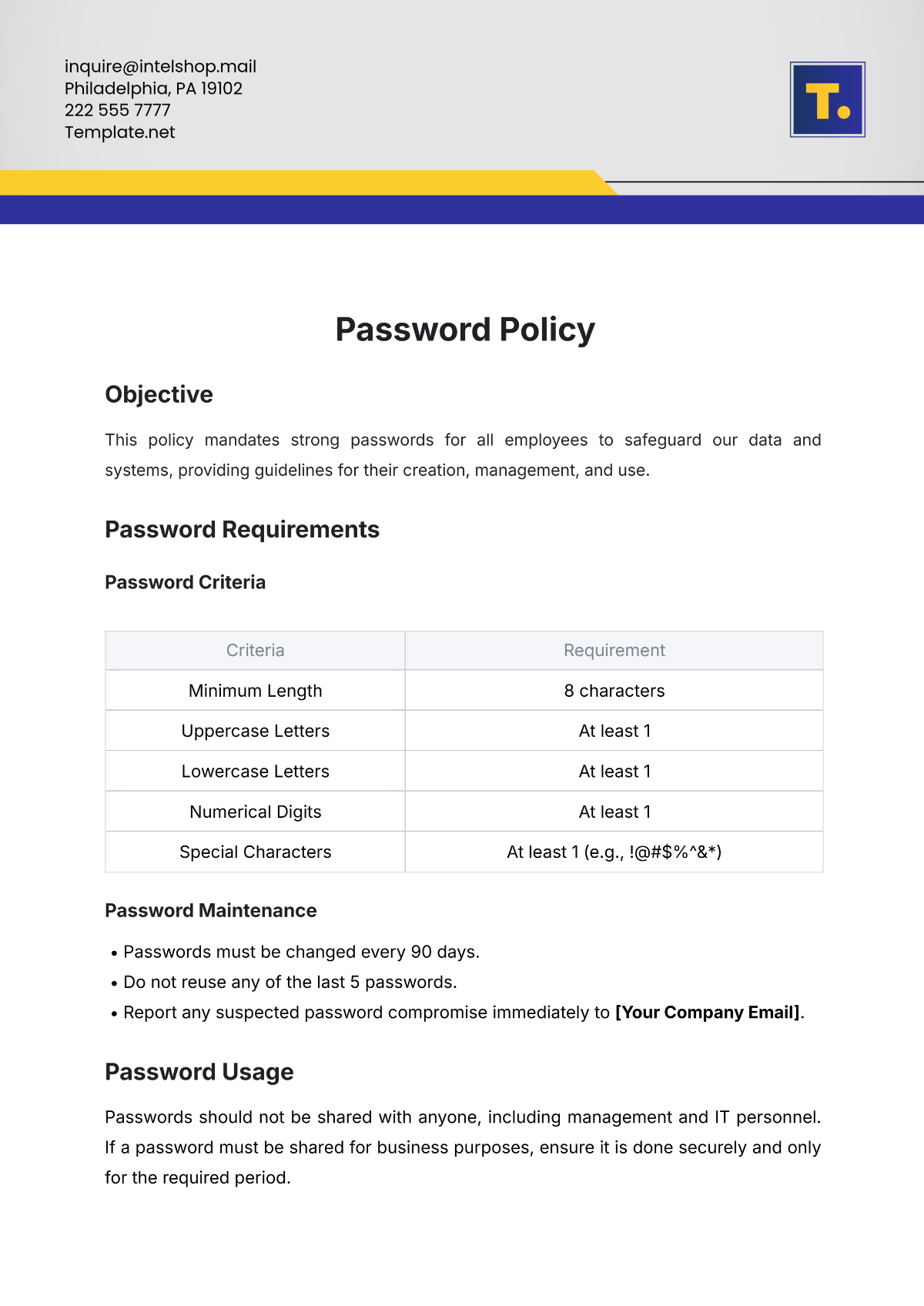
Financial Systems Security Policy Template
This policy, which has been thoughtfully created and implemented by [Your Company Name], serves a significant purpose. Its primary aim is to lay out a clear, systematic, and comprehensive process that will be used for identifying any potential risks that may exist. Additionally, it seeks to evaluate these risks across every sector within an organization. Once identified and understood, the plan then dictates how these risks should be mitigated.
I. Policy Statement
This policy's main objective is to establish a methodical and extensive system for managing risk across all departments of any organization that chooses to adapt and follow this strategy. Through this approach, we aim to cultivate a culture where decisions are made with a conscious understanding and measure of the inherent risks. This culture is not just about risk management but also about ensuring the preservation and sustenance of the organization. Such a culture allows the organization to maintain its financial integrity, uphold its brand's reputation, and ensure sustainability in the long run. The policy, therefore, becomes an integral tool in establishing and promoting risk awareness within the organizational structure.
II. Purpose
This document, known as the Risk Identification and Mitigation Policy, has been designed with the primary intent of offering an established and uniform method that can be used when the tasks of identifying, assessing, and determining the order of importance of various potential risk factors are being carried out. By adhering strictly to this specific model, effective and efficient strategies can be developed and implemented accordingly to reduce or completely neutralize the impact of the aforementioned risks, hence ensuring the smooth running of operations and overall productivity of the organization or project this policy is designed for.
III. Scope
The policy we have in place, which includes absolutely no exclusions, applies uniformly to every single department that falls within the structure of our organization. Further, the enforcement of this policy extends beyond our core workforce, to also encompass the multitude of other professionals who are affiliated with our company, be they contractors, consultants, or any other stakeholders. These individuals all fall under the extensive umbrella of our organization and hence are obliged to strictly adhere to this policy. Furthermore, it is crucial to underscore that the applicability of this policy remains steadfast and absolute, irrespective of the particular department involved or the specific industry sector in which our organization operates. Our policy remains ubiquitous across all units of our organization, thereby creating a standardized code of conduct for all who are a part of it.
IV. Risk Identification Process
A. Risk Discovery
We will employ a systematic process to identify risks. This methodical process will encompass several critical stages. Initially, it will involve the collection of crucial data from pertinent sources. After gathering the necessary data, we will move on to the monitoring phase which will ensure that the gathered information is pertinent, current, and accurate. Following monitoring, an analysis of the amassed data will be conducted to identify any underlying patterns, trends, or potential risks. Speaking to, and garnering feedback from the employees within the organization and consulting with them regarding the risks is also an intrinsic part of this process. Their first-hand experiences and insights can often shed light on areas that may be overlooked.
Furthermore, a comprehensive analysis of the financial performance will be conducted regularly to ensure the economic stability and sustainability of the organization. In this step, we will specifically examine revenue growth, profitability, liquidity and solvency, operational efficiency, and capital structure of the organization to detect any potential risks.
Finally, extensive research on market trends and industry behavior will be carried out. This will allow us to understand the external factors that might affect the organization's functioning and to foresee and prepare for any major shifts or changes in market conditions.+
B. Risk Analysis
After the identification process of potential risks has been completed, an evaluation process will follow. Each risk will be assessed based on both the potential effect it could have and the likelihood of its occurrence. This subsequent analysis will serve as a guide to determine the priority level of each risk, essentially ranking them according to the level of threat they pose. Once the risks have been put in order of priority, the next step involves selecting proper and suitable responsive actions that intend to address each of these identified risks.
V. Risk Mitigation
Risks that have been classified as having a high priority will be subjected to a comprehensive process of mitigation. The process of mitigating such high-priority risks may involve the deployment of multiple strategies. For starters, it may require strategic planning that involves a systematic approach to deciding the actions to be taken to mitigate the risk. Furthermore, the mitigation process may also involve the allocation of resources, which may include the distribution of personnel, finances, or other assets dedicated to addressing the risk at hand. To ensure the functional efficacy of the mitigation process, there may be a need for the development of systems ideally suited for this purpose. Above all, for optimal risk mitigation, a consistent and steadfast monitoring setup may need to be put in place to ensure that the risk levels are kept under control and do not escalate dangerously.
VI. Monitoring and Review
To manage risks effectively, it is essential to maintain consistent supervision coupled with reviews at regular intervals. According to the guidelines outlined within this policy, it is distinctly commanded that these reviews must be beyond a mere routine process, with a requirement for them to be comprehensive. The purpose of conducting these exhaustive reviews is driven by a desire to ensure the solidity of the procedures that are involved in identifying potential risks. Not only is the identification of these risks important, but also curbing the detrimental impacts they can present is critical. The ultimate goal of these comprehensive reviews is to continuously guarantee the robustness of these risk management procedures and to maintain an environment where risks are not only identified but effectively mitigated as well.
VII. Responsibility
Compliance with this policy lies in the hands of every staff member working within the organization, as well as any external associates who have a relationship or dealings with the organization. Simply stated, everyone involved with the organization must adhere to this policy. Along with this, the organization assigns the responsibility of both overseeing and coordinating the implementation of this policy to the Risk Management Team. This means ensuring that everyone is following the guidelines laid out by the policy and that it's properly executed and falls into the hands of the Risk Management Team.
VIII. Policy Review
The policy in question will be subjected to a review process on an annual basis as a minimum requirement. However, should there be any substantial changes within our organization or in our external environmental conditions, additional reviews might be necessitated accordingly. If you seek added information or clarity about this policy, we welcome you to reach out to us. Please direct your inquiries toward [Your Company Email]. We are more than delighted to provide you with timely and prompt responses.
Policy Effective Date: 01 January 2050