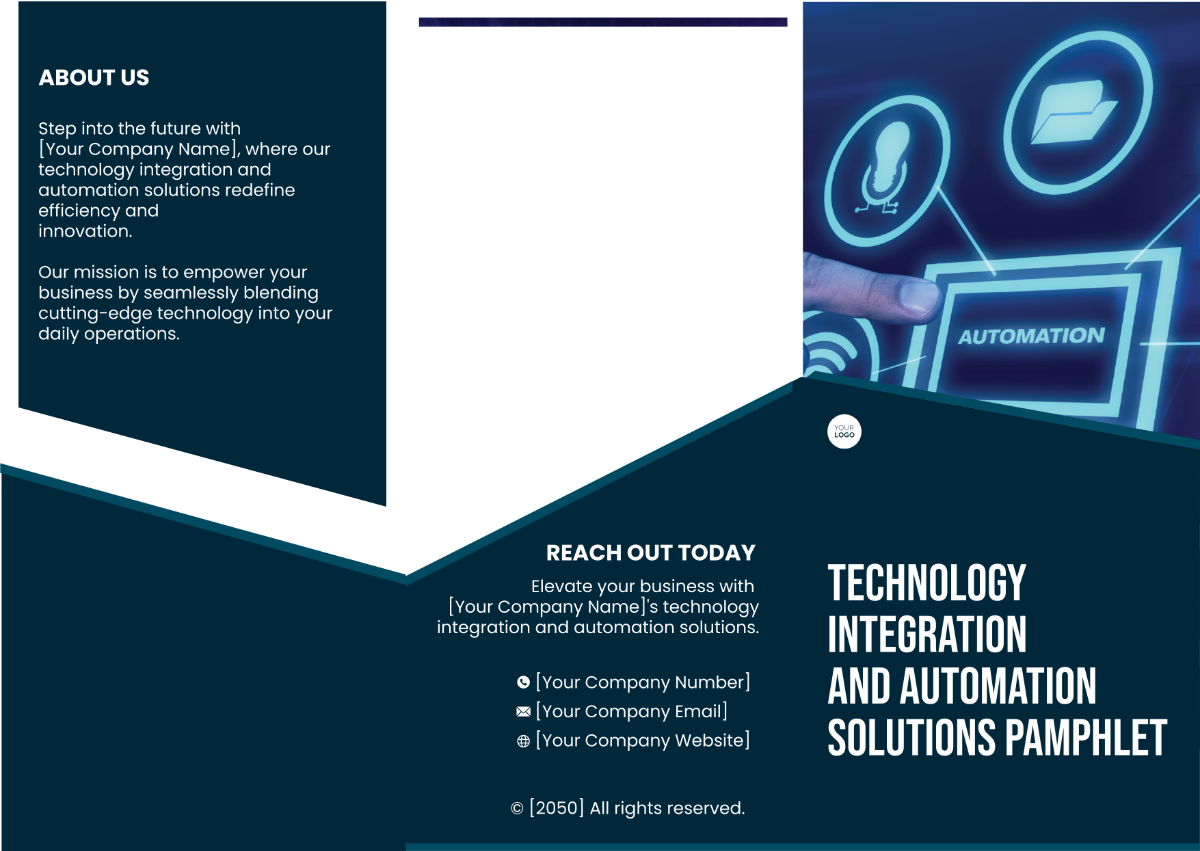
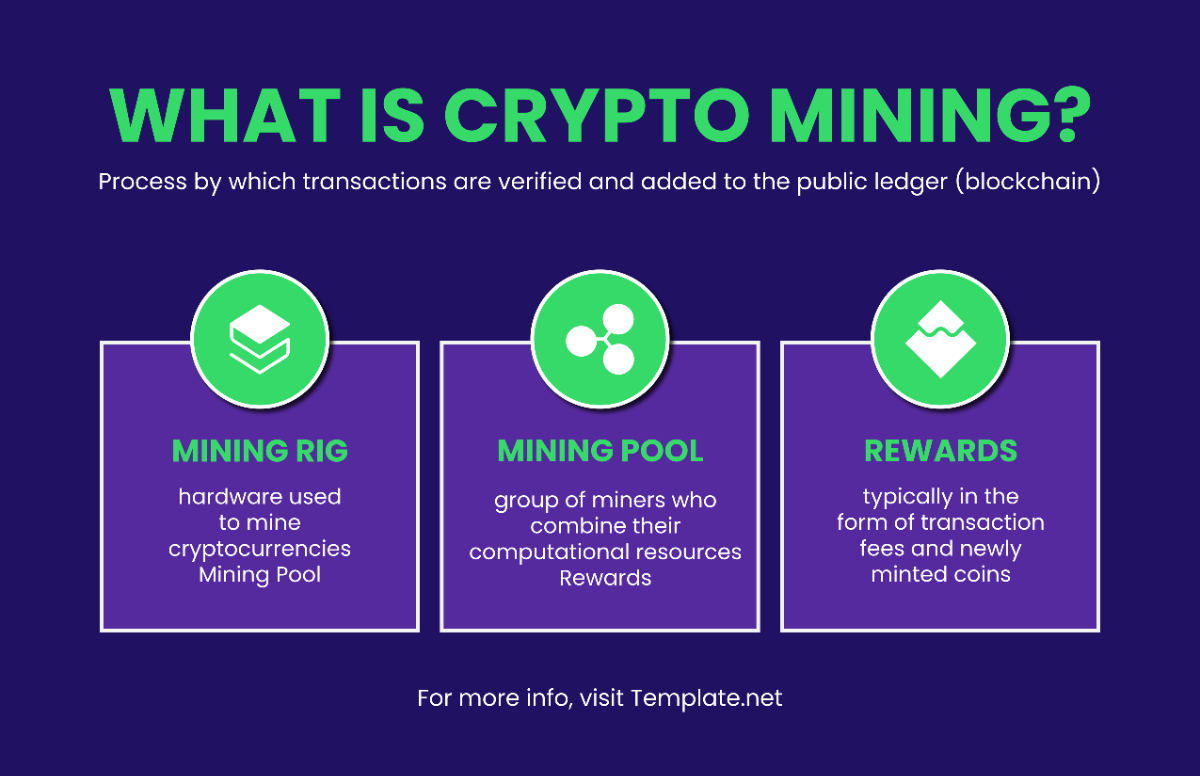
Data Security Protocols
This protocol detailed below is a comprehensive guide to ensure the secure transmission and receipt of data in a communication system. Its purpose is to create a safe environment for messages to be exchanged between interconnected devices without the risk of unauthorized access, modification, or data leakage.
1. Data Encryption
Data Encryption is an integral part of this protocol. It converts clear text data into ciphertext. The original text cannot be accessed or understood without the appropriate decryption key.
Use advanced encryption standards (AES-256) for encrypting data before transmission.
Ensure that the algorithm is implemented correctly to prevent vulnerabilities.
2. Secure Network Connection
Always connect the devices through a secure network connection. Public Wi-Fi and other non-trusted networks may have security vulnerabilities that make your data prone to interception.
Always use Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols for network communication.
3. Authentication Protocol
Use two-factor authentication (2FA) or multi-factor authentication where possible. This significantly reduces the possibility of unauthorized users gaining access to the communication.
4. Regular Updates and Security Patches
To prevent newly discovered security loopholes from being exploited, always keep the systems, applications, and security measures up-to-date.
Regularly schedule updates and security patches. Typically, these updates contain patches for known vulnerabilities, thus making the system more secure.
5. Monitor and Report Any Suspicious Activity
Monitoring systems are essential to identify any abnormalities in data transmission early. The use of intrusion detection systems (IDS) and intrusion prevention systems (IPS) should be utilized.
Set up a protocol for reporting any suspicious findings - this allows for quick mitigation of potential threats.
By adhering to these guidelines, you will be promoting data integrity, confidentiality, and availability, crucial to maintaining trust in any communication system.
Protocol Templates @ Template.net