Startup Office Security Policy
I. Introduction
Welcome to [Your Company Name] Office Security Policy. The safety and security of our office environment are paramount. This document outlines our comprehensive approach to maintaining a secure workplace. All employees, contractors, and visitors are expected to adhere to these guidelines to ensure a collective effort in our security measures.
II. Objective
The primary objective of the Office Security Policy is to safeguard the company's assets, which include personnel, physical property, and confidential information. This policy aims to establish a secure and safe working environment by mitigating risks associated with unauthorized access, theft, data breaches, and other security threats. Ensuring the well-being of employees and the protection of company resources is central to maintaining operational integrity and trust.
III. Scope
The scope of this policy encompasses all individuals who interact with or have access to the company's premises and systems. This includes not only full-time and part-time employees but also contractors, visitors, and any other personnel who are present on the company's property or have access to its information systems. The policy outlines the responsibilities and expected behaviors of everyone under its umbrella to maintain a secure and protected work environment.
IV. Security Measures
A. Physical Security
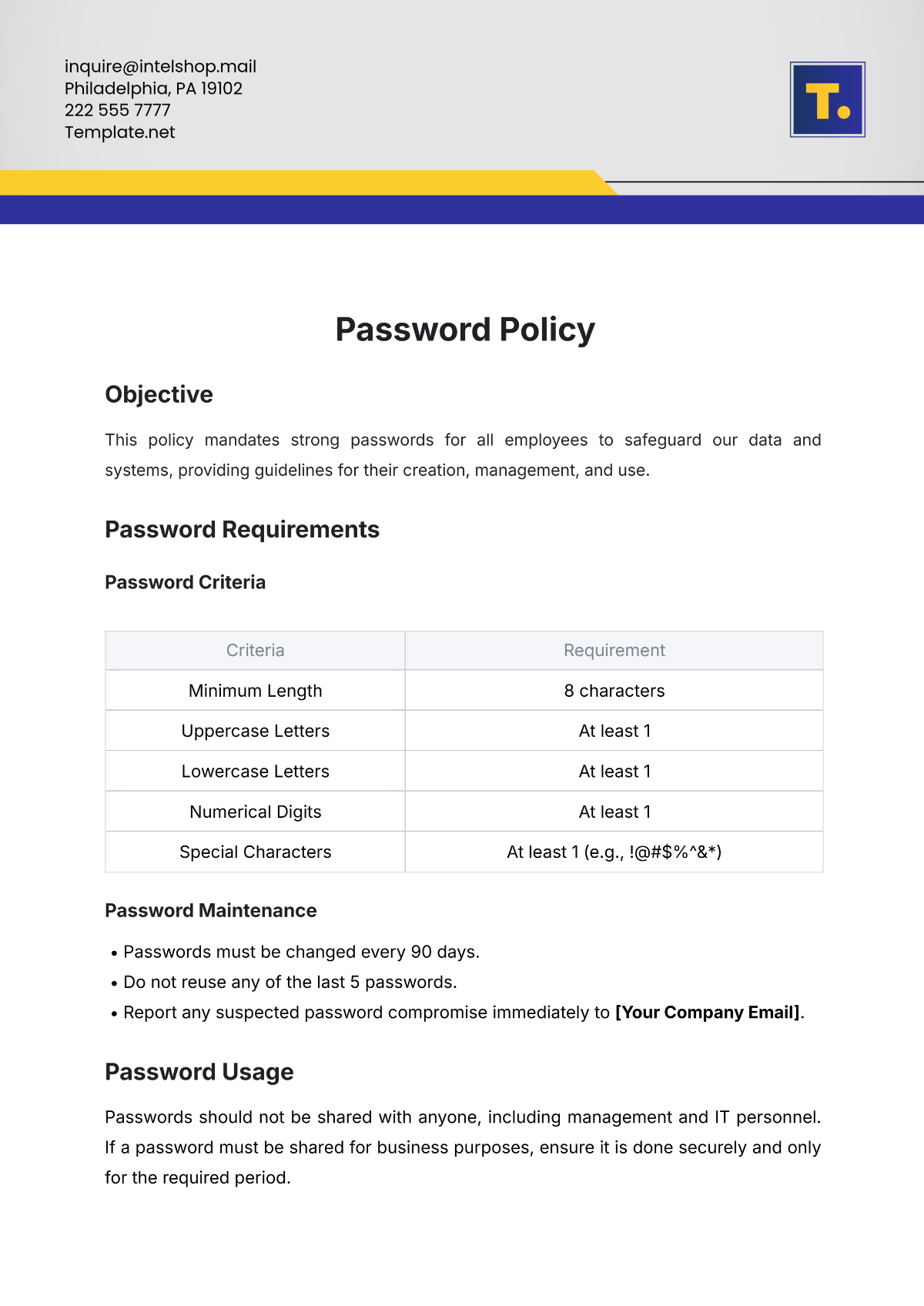
Measures | Description |
|---|---|
Access Control | Access to the office is controlled through electronic keycards. All employees are issued a keycard, and access levels are assigned based on job roles. |
Visitor Management | Visitors must sign in at reception, provide identification, and are issued visitor badges. Employees must accompany visitors at all times. |
Surveillance | CCTV cameras are installed in common areas and entry points to monitor and record activities 24/7. |
Secure Areas | Sensitive areas, such as server rooms and file storage rooms, are restricted to authorized personnel only. |
B. Information Security
Measures | Description |
|---|---|
Data Protection | Employees must follow strict guidelines for handling and storing sensitive data, including the use of encrypted storage devices and secure passwords. |
Cybersecurity | The IT department ensures that all systems are protected with up-to-date antivirus software and firewalls. Regular cybersecurity training is provided to employees. |
Incident Reporting | Any security incidents, including suspected data breaches or unauthorized access, must be immediately reported to the IT department. |
C. Personal Security
Measures | Description |
|---|---|
Emergency Procedures | Fire, evacuation, and other emergency procedures are clearly posted throughout the office. Regular drills are conducted to ensure preparedness. |
Workplace Violence | [Your Company Name] has a zero-tolerance policy for workplace violence. Threats, intimidation, and physical violence are strictly prohibited and may result in immediate termination and legal action. |
V. Compliance
Compliance with the Office Security Policy is non-negotiable and mandatory for everyone within its scope. The policy sets clear expectations for behavior and outlines the consequences of non-compliance, which can range from disciplinary actions to termination of employment or contracts. This strict enforcement ensures that security measures are taken seriously and that the company maintains a high standard of security. Regular audits and reviews are part of the compliance process, ensuring that the policy remains effective and up-to-date with evolving security challenges.
VI. Acknowledgment
Acknowledgment of the Office Security Policy is a critical step in ensuring that all individuals are aware of and understand their role in maintaining security. By acknowledging the policy, individuals affirm that they have read, understood, and agree to abide by the security measures and guidelines outlined. This acknowledgment is typically documented through a signed statement or electronic confirmation, serving as a commitment to uphold the company's standards for security and safety.
VII. Contact Information
For any questions or concerns about security measures or to report a security incident, please contact:
Security Coordinator: [Your Name]
Email: [Your Company Email]
Phone: [Your Company Number]