Free Operations IT Security Policy Manual Template
Operations IT Security Policy Manual
1. Introduction and Purpose
The Operations IT Security Policy Manual serves as a foundational document for [Your Company Name], outlining the comprehensive guidelines and protocols designed to protect our information technology assets and data. The purpose of this manual is to ensure the confidentiality, integrity, and availability of our IT resources, safeguarding against cyber threats, unauthorized access, and data breaches. This manual aligns with US laws and industry standards, providing a clear framework for employees, management, and IT staff to follow.
By establishing these security policies, [Your Company Name] demonstrates its commitment to maintaining the highest level of IT security. It is essential for all staff to adhere to these guidelines, as doing so is crucial for protecting our digital infrastructure and the information we manage. This manual not only addresses the technical aspects of IT security but also emphasizes the importance of a security-conscious culture within our organization.
2. Roles and Responsibilities
All employees, regardless of role, play an integral part in maintaining IT security. Responsibilities vary depending on individual roles and positions:
|
Role |
Responsibility |
|---|---|
|
IT Staff |
Implement and monitor security measures, handle security incidents, and provide guidance to other employees. |
|
Employees |
Follow IT security policies in daily operations, report any observed security incidents and participate in regular security training. |
|
Management |
Oversee the compliance with the security policy, ensure resources for security efforts and lead by example. |
|
Third-party service providers |
Adhere to contractually agreed security requirements, report security incidents, and cooperate in security audits. |
3. Data Classification and Handling
Data classification and handling standards ensure that the sensitivity level of information determines how we treat, store and transmit data:
Classifications:
-
Public: This information is intended for public disclosure.
-
Confidential: This information requires strict control and access restrictions.
-
Sensitive: Compromise of this information could severely impact the company and its operations.
4. Access Control
The Access Control section of the Operations IT Security Policy Manual outlines the mechanisms and procedures [Your Company Name] employs to regulate access to its information systems and data, ensuring that such access is restricted to authorized users only. This is critical for preventing unauthorized access, data breaches, and maintaining the integrity of our systems.
User Account Management
Defines the process for creating, issuing, managing, and revoking user accounts. It includes guidelines on user identity verification, the assignment of access rights based on roles, and periodic review of user access privileges.
Password Policy
Specifies the requirements for creating strong passwords, including minimum length, complexity, and change frequency. It emphasizes the importance of safeguarding passwords and the prohibition of password sharing.
Physical Access Controls
Details the physical security measures to prevent unauthorized access to facilities housing critical IT infrastructure, including data centers and server rooms. It covers access control systems, visitor management, and security of workstations and devices.
Monitoring and Logging
Describes the procedures for monitoring user activities and system access to detect and respond to security incidents. It includes the collection, analysis, and retention of log data, ensuring accountability and aiding in the investigation of breaches.
5. Network Security
The Network Security section delineates the strategic defenses [Your Company Name] employs to protect its network infrastructure against unauthorized access, attacks, and other cyber threats. This comprehensive approach ensures the security and reliability of our network resources.
Firewall and Intrusion Prevention
Outlines the deployment and management of firewalls and intrusion prevention systems (IPS) to monitor and control incoming and outgoing network traffic based on an applied rule set, effectively blocking malicious traffic and unauthorized access attempts.
Secure Network Architecture
Details the design and implementation of a network architecture that prioritizes security. This includes the use of segmented networks to reduce the attack surface, employing secure protocols for data transmission, and ensuring proper configuration of network devices.
VPN and Remote Access
Specifies the guidelines for secure remote access to the company's network, including the use of Virtual Private Networks (VPNs) to encrypt data traffic. It defines the conditions under which remote access is granted and the security measures, such as multi-factor authentication, to protect against unauthorized access.
6. Physical Security
The Physical Security section focuses on safeguarding [Your Company Name]'s physical IT assets and infrastructure. These measures are crucial for preventing unauthorized physical access, damage, or theft of hardware and ensuring the continuous operation of our IT services.
Access Control Systems
Details the implementation of access control systems to secure areas containing sensitive IT equipment, such as data centers and server rooms. This includes key card systems, biometric scanners, and security personnel protocols to manage access.
Surveillance and Monitoring
Outlines the use of surveillance cameras and monitoring systems to oversee critical IT infrastructure locations. This serves as a deterrent against unauthorized access and provides a means to investigate security incidents. Regular audits and maintenance of these systems ensure their effectiveness and compliance with security policies.
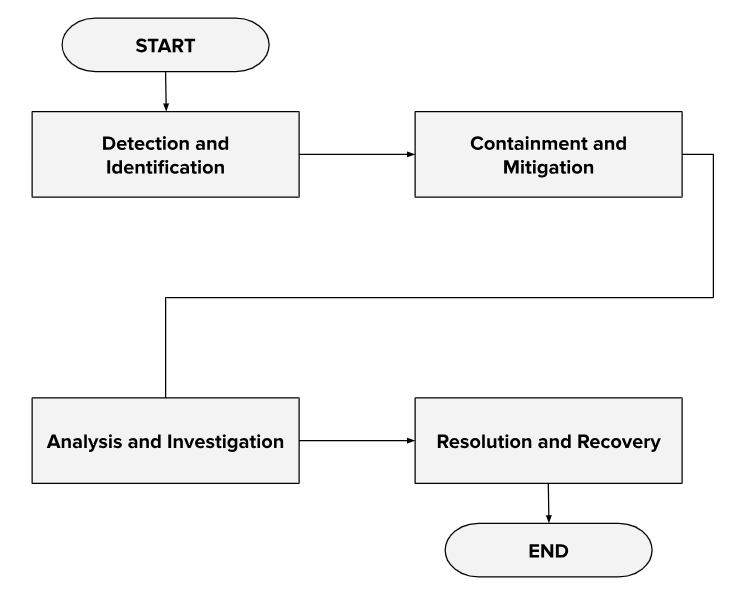
7. Incident Response and Management
The Incident Response and Management section is a critical component of [Your Company Name]'s IT Security Policy, designed to minimize the impact of security incidents on our operations. It outlines a structured approach for responding to and managing incidents, ensuring a swift and effective resolution. This proactive strategy is essential for protecting our information assets, maintaining trust with our stakeholders, and complying with legal and regulatory requirements.
By detailing a clear process for incident response, [Your Company Name] demonstrates its commitment to cybersecurity resilience. The outlined steps provide a roadmap for identifying, containing, eradicating, and recovering from security incidents, thereby reducing their potential impact and preventing recurrence.
8. Business Continuity and Disaster Recovery
The Business Continuity and Disaster Recovery section of [Your Company Name]'s IT Security Policy Manual ensures the organization's ability to continue operations during and after any disruptive events. It focuses on minimizing downtime and data loss, ensuring rapid recovery and resumption of business activities, thereby safeguarding our reputation, customer trust, and financial stability.
Risk Assessment
Identifies potential risks and vulnerabilities that could impact business operations, guiding the development of strategies to mitigate these risks.
Business Impact Analysis (BIA)
Evaluates the potential impact of different disaster scenarios on business operations to prioritize recovery efforts on critical services and functions.
Recovery Strategies
Outlines specific strategies and procedures for recovering IT systems, data, and infrastructure after a disaster, including the use of offsite backups and redundant systems.
Plan Development and Implementation
Details the creation of a comprehensive business continuity and disaster recovery plan, including roles, responsibilities, and actions to be taken before, during, and after a disaster.
Testing and Maintenance
Describes the regular testing of the disaster recovery plan to ensure its effectiveness and the updating of the plan to reflect changes in the business environment, technology, and potential threats.
9. User Education and Awareness
The User Education and Awareness section is pivotal in fostering a security-conscious culture within [Your Company Name]. It ensures that all employees are equipped with the knowledge and tools needed to recognize and prevent security threats, thereby playing an active role in safeguarding the organization's information assets.
Training Programs
Outlines the implementation of regular, mandatory training sessions for employees on IT security policies, emerging cyber threats, and safe computing practices to enhance their understanding and adherence to security protocols.
Awareness Campaigns
Describes the use of ongoing awareness campaigns, including newsletters, posters, and intranet resources, to keep security at the forefront of employees' minds. These campaigns aim to promote a continuous focus on security best practices and updates.
Phishing Simulation and Testing
Details the conduct of periodic phishing simulations and other testing mechanisms to assess employee awareness and responsiveness to potential security threats. Feedback and additional training are provided based on the outcomes, reinforcing the importance of vigilance in cybersecurity.
10. Policy Review and Update
The Policy Review and Update section guarantees that [Your Company Name]'s IT Security Policy Manual stays current and effective, adapting to evolving cybersecurity threats, technological advancements, and regulatory requirements. This process is vital for maintaining robust security measures and compliance.
Review Schedule
Specifies the regular schedule for reviewing the IT security policy manual, typically on an annual basis or following significant changes to IT infrastructure, to ensure its continued relevance and effectiveness.
Stakeholder Involvement
Outlines the inclusion of key stakeholders, including IT security, legal, and management teams, in the review process to provide comprehensive insights and recommendations for updates.
Update Procedures
Details the procedures for making amendments to the policy manual, including the documentation of changes, approval processes, and communication of updates to all employees to ensure awareness and understanding of new policies.
Compliance Monitoring
Defines the mechanisms for monitoring compliance with the updated policies, including audits and assessments, to enforce adherence and identify areas for improvement. This section also clarifies the roles and responsibilities related to compliance tasks, ensuring accountability within the organization.