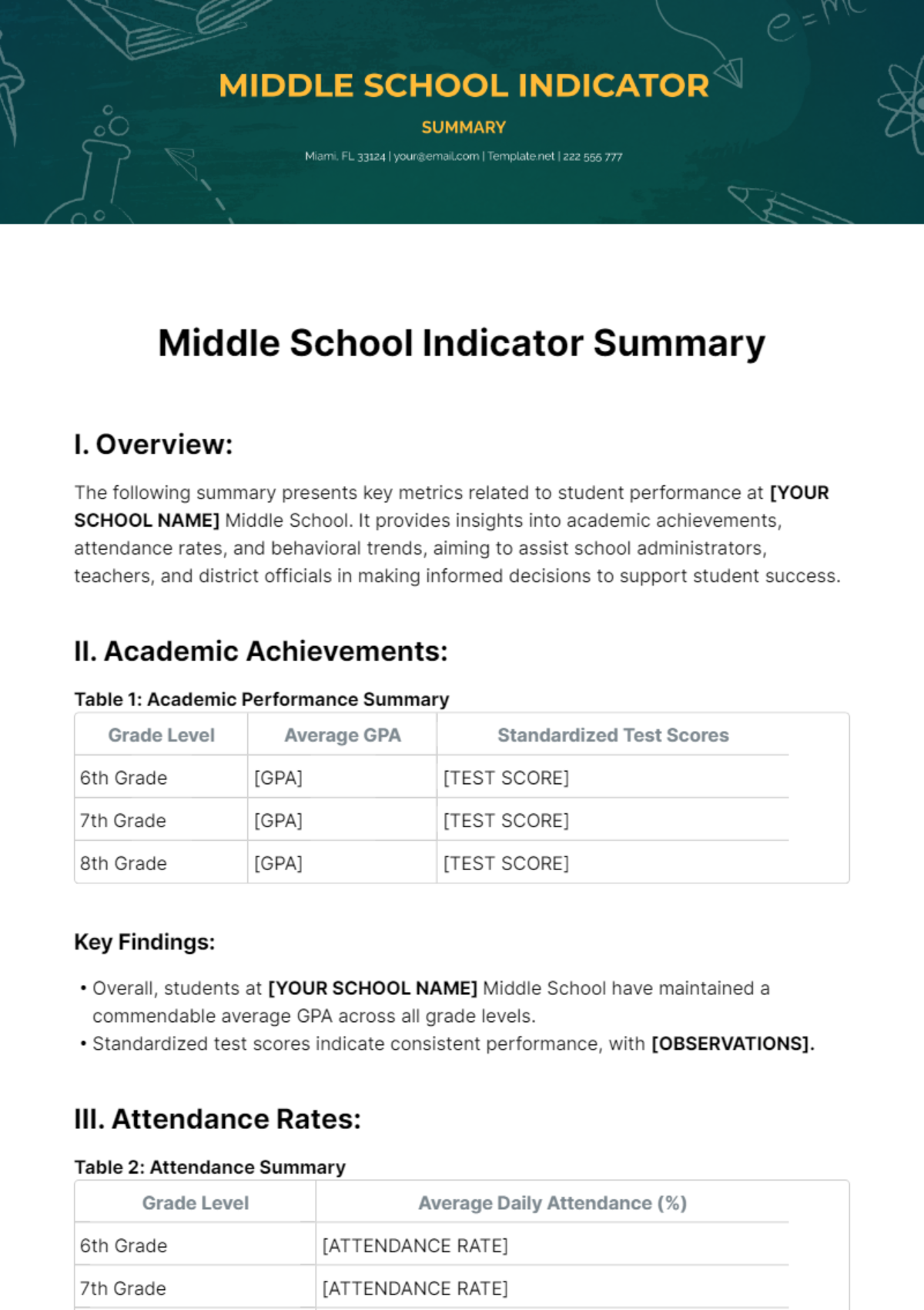
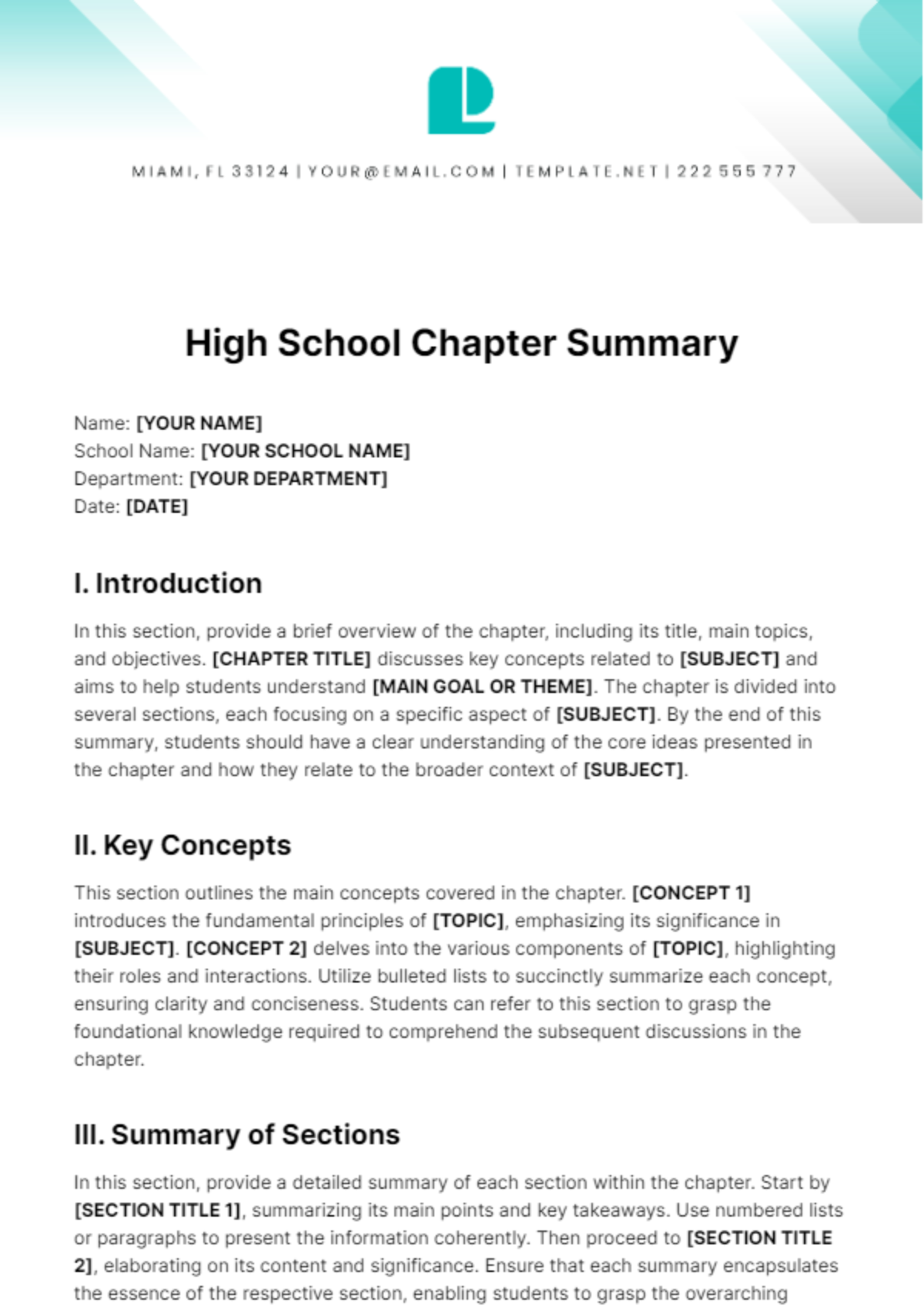
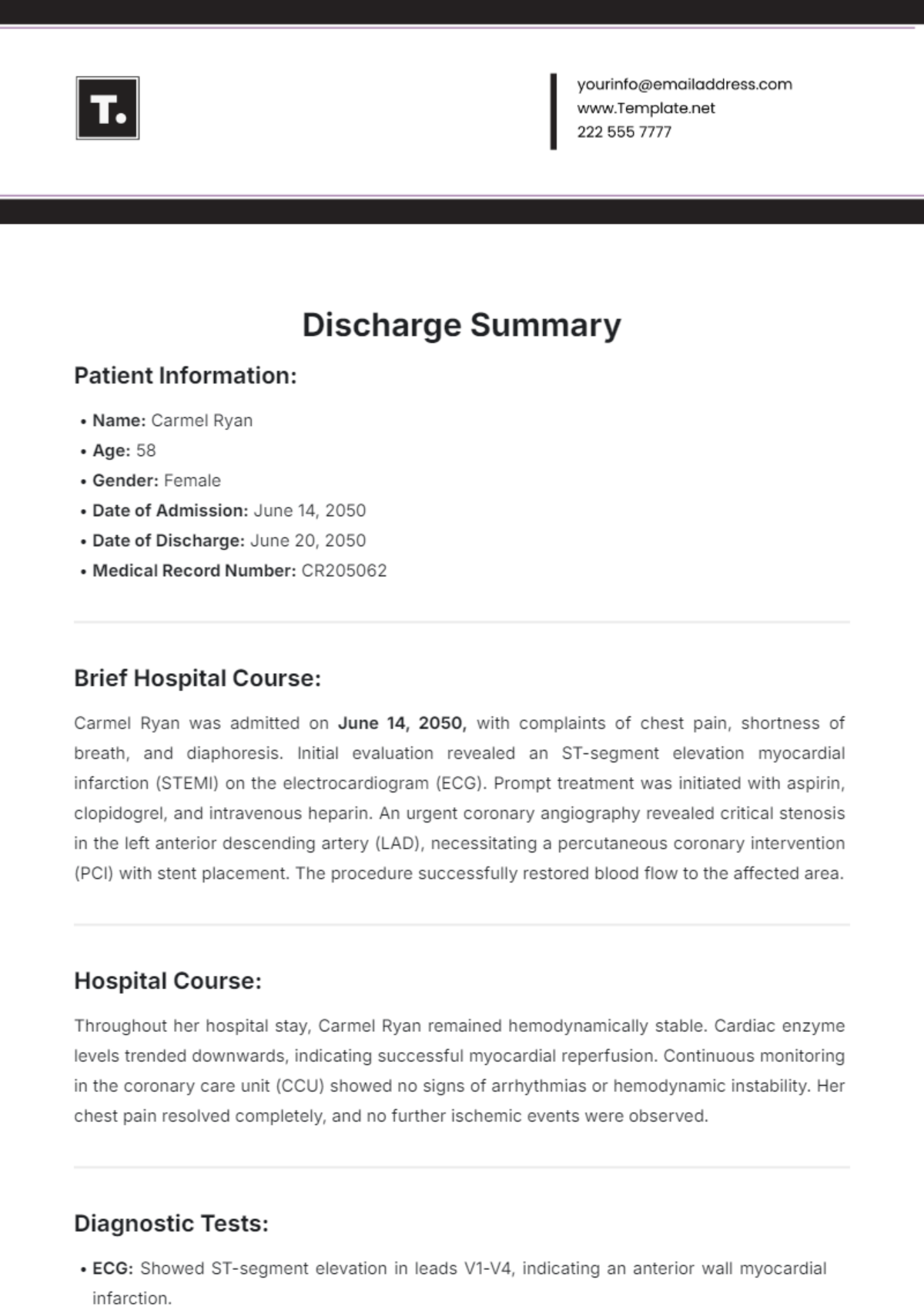
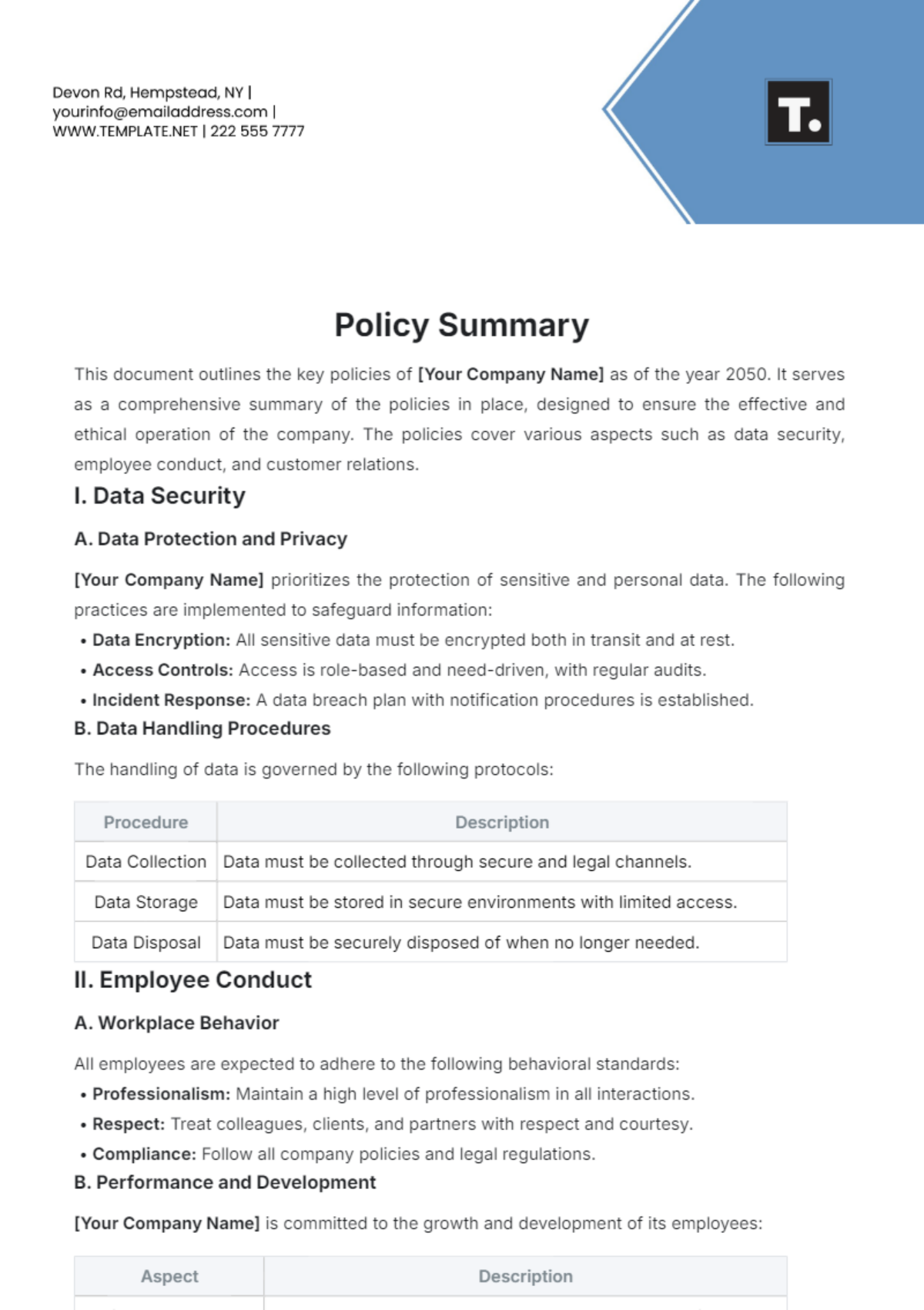
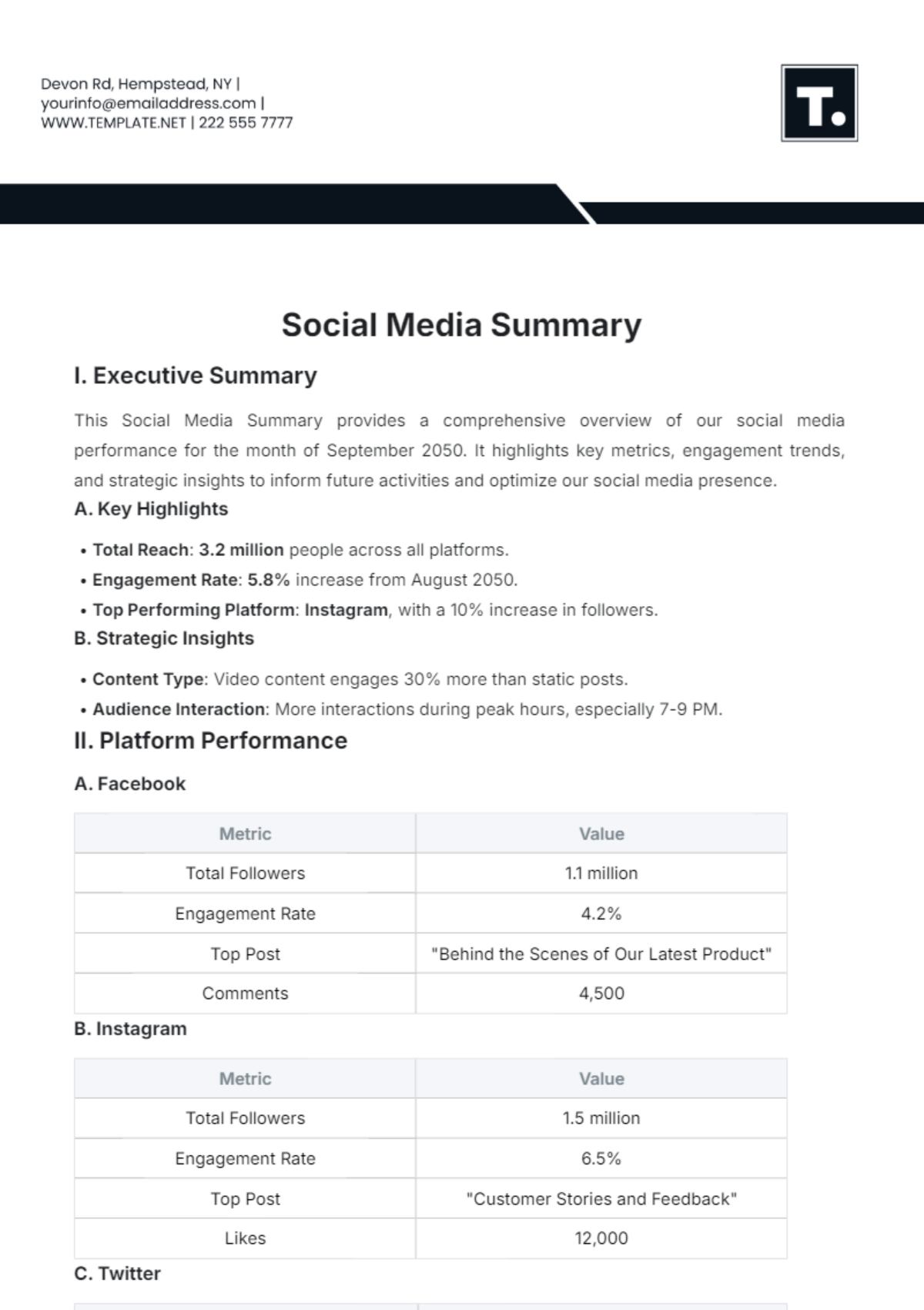
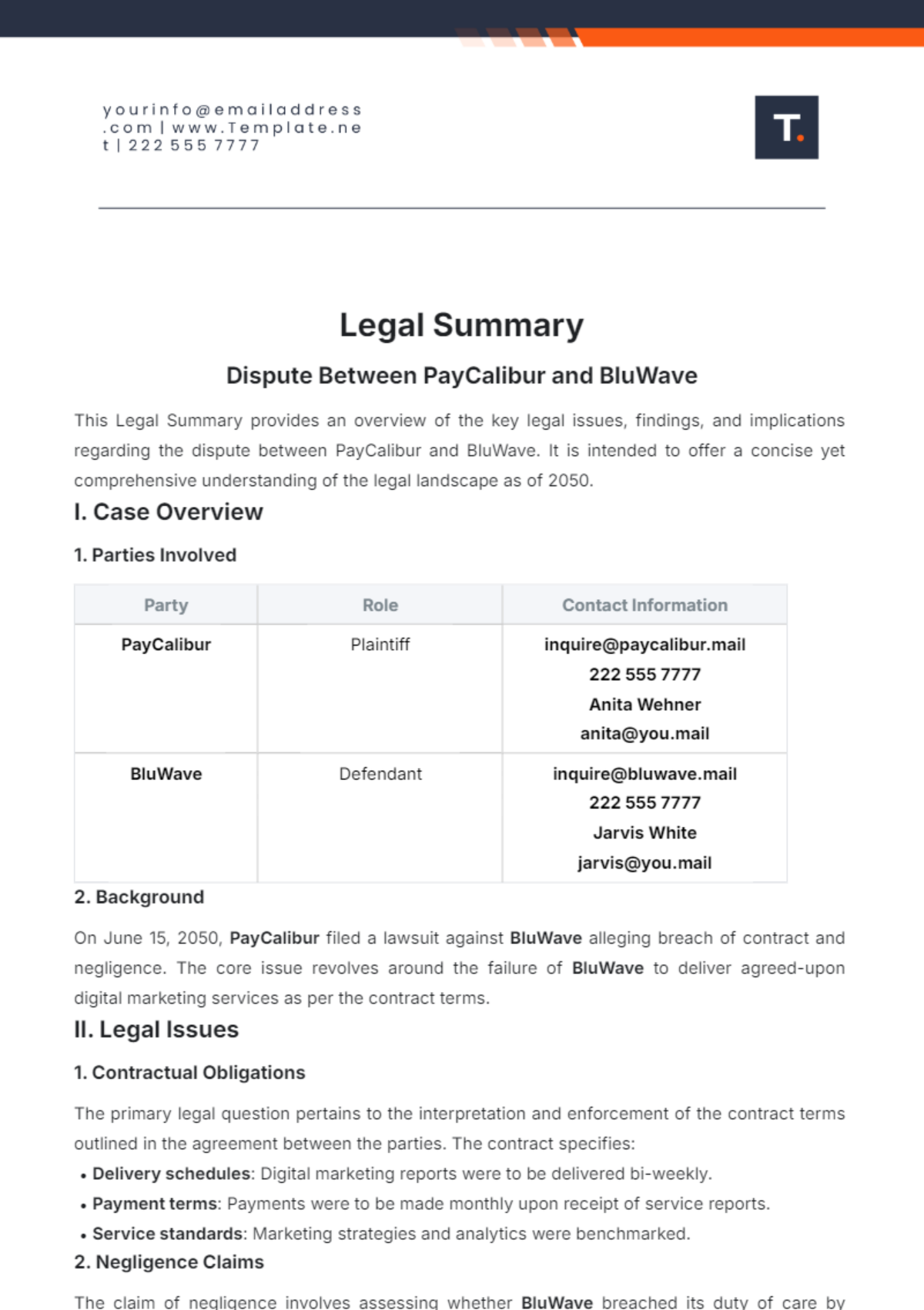
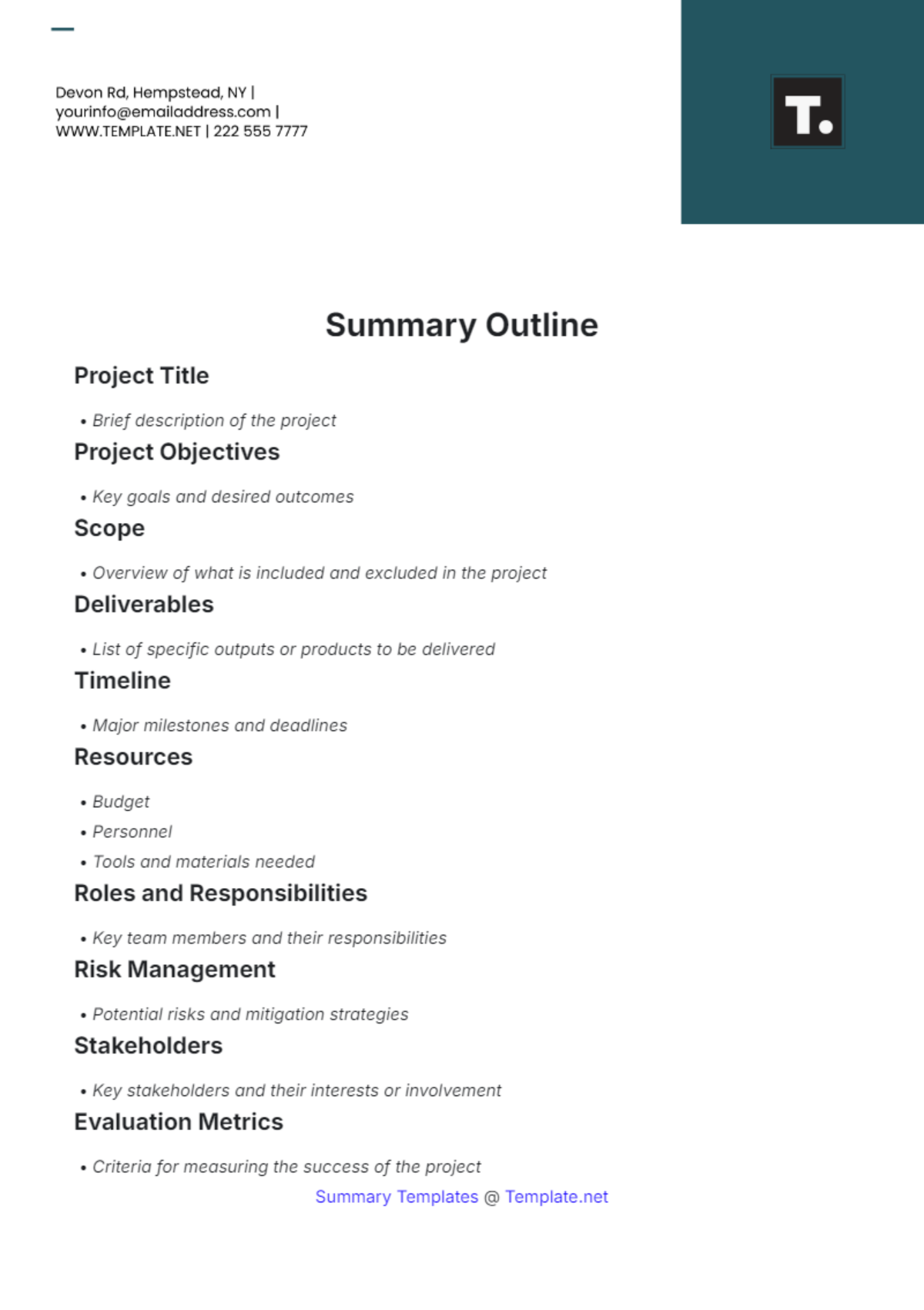
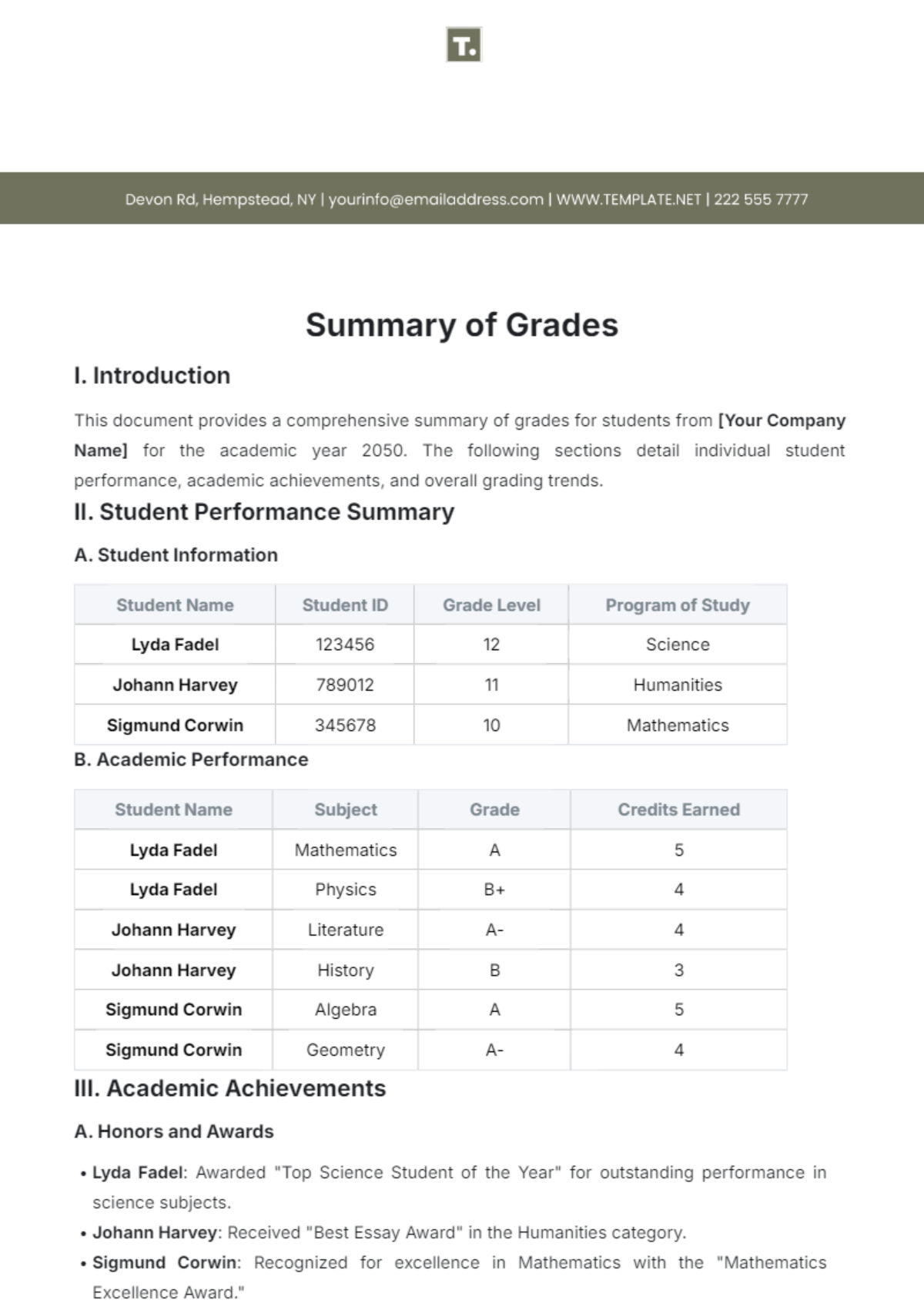
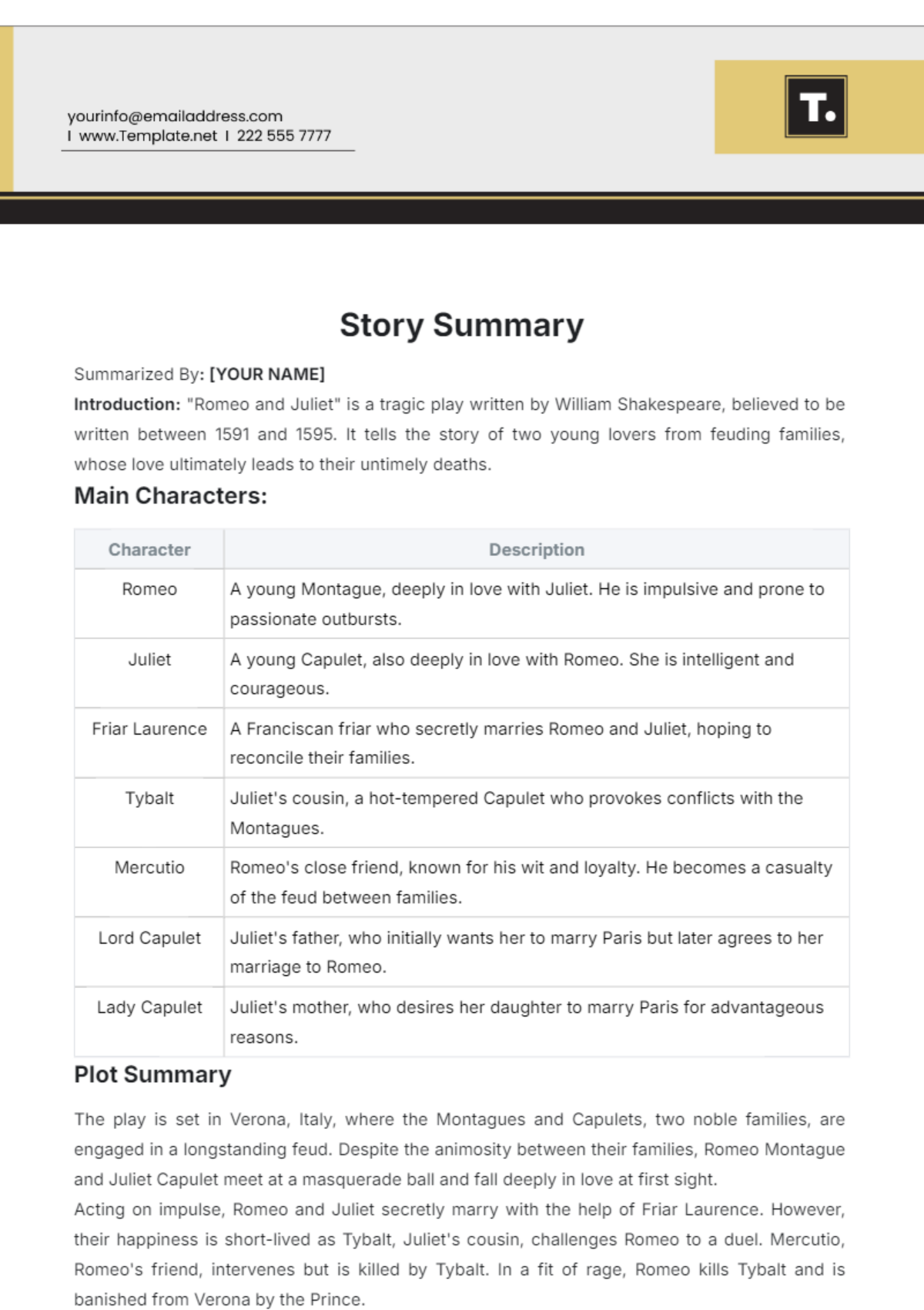
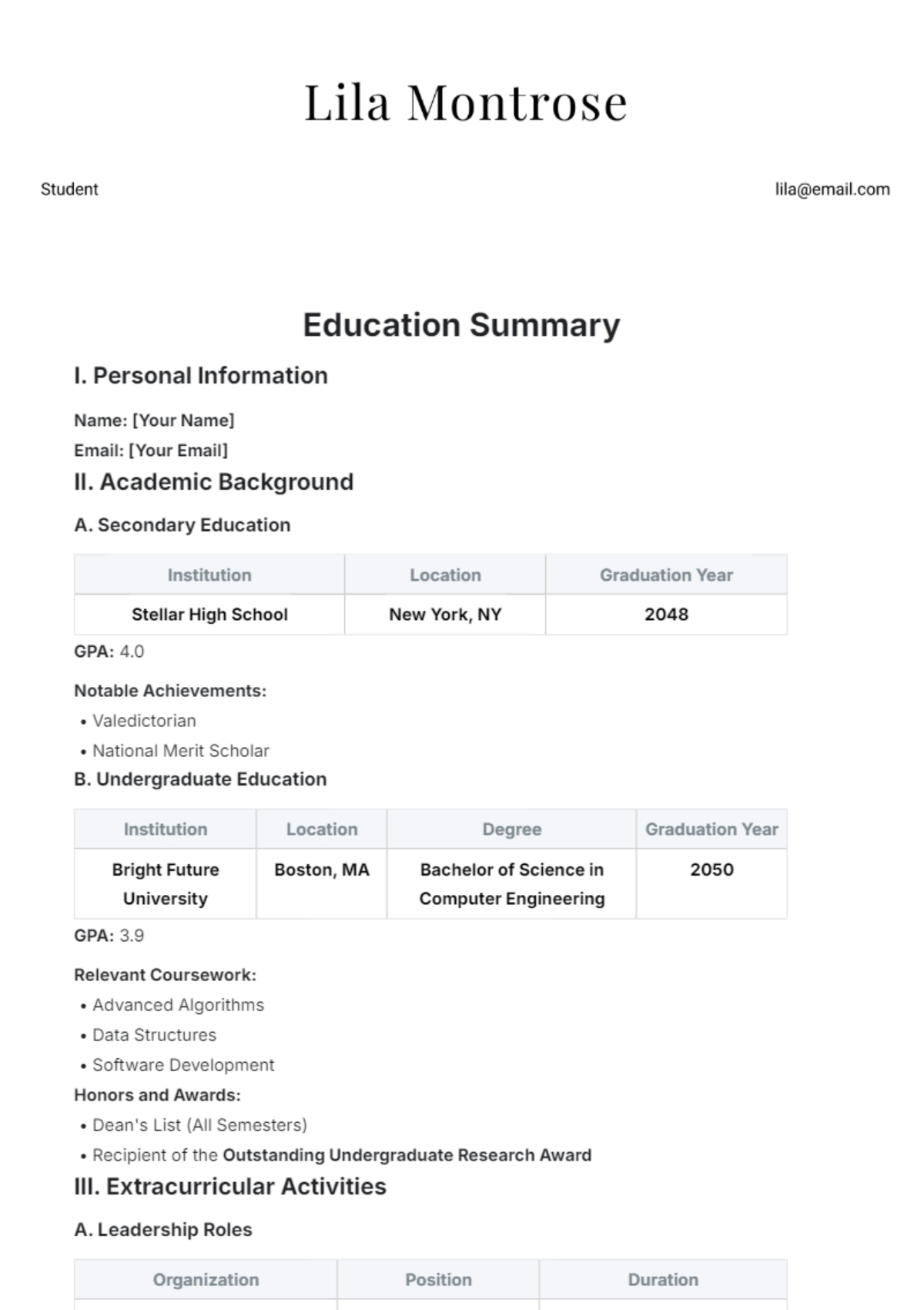
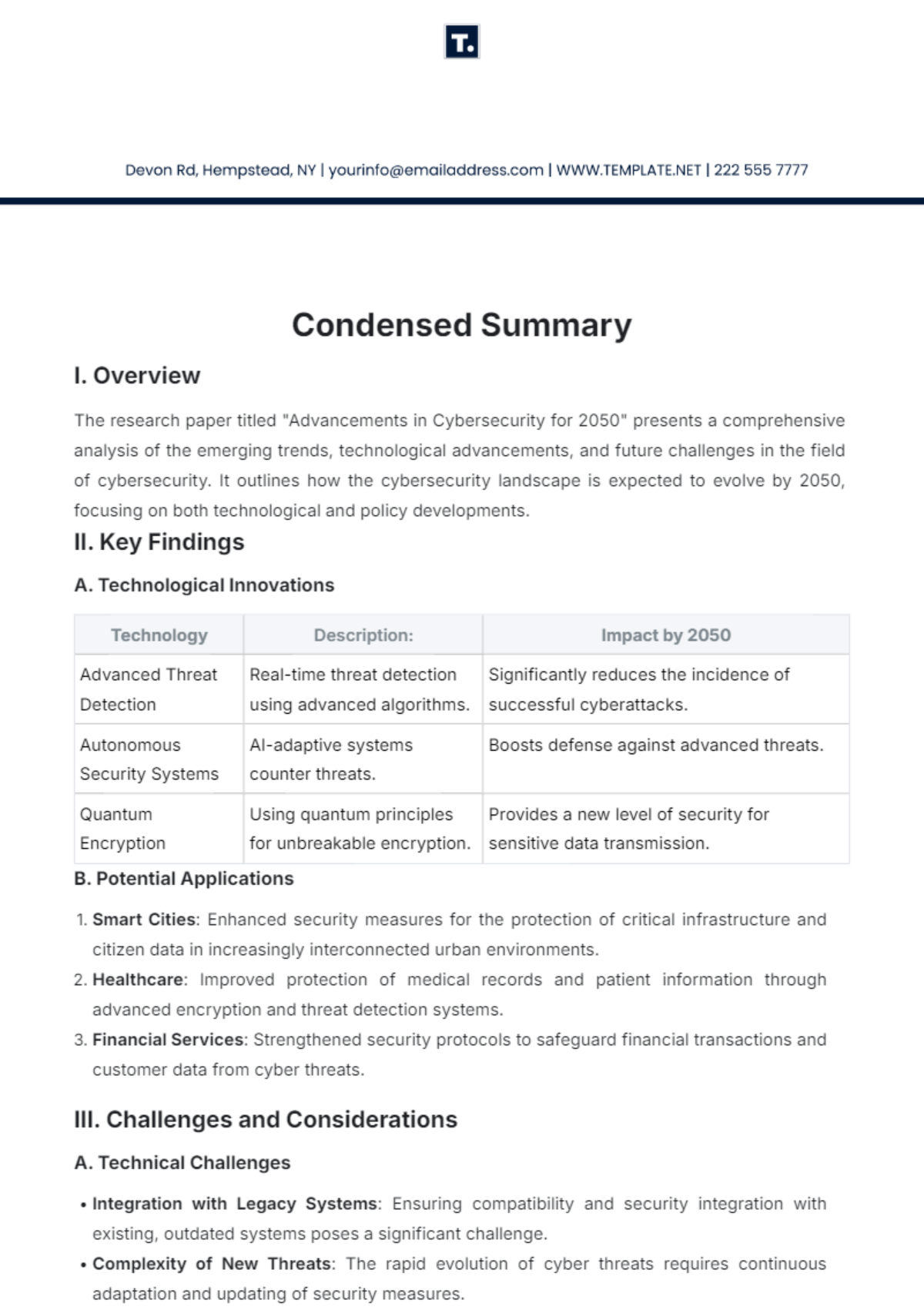
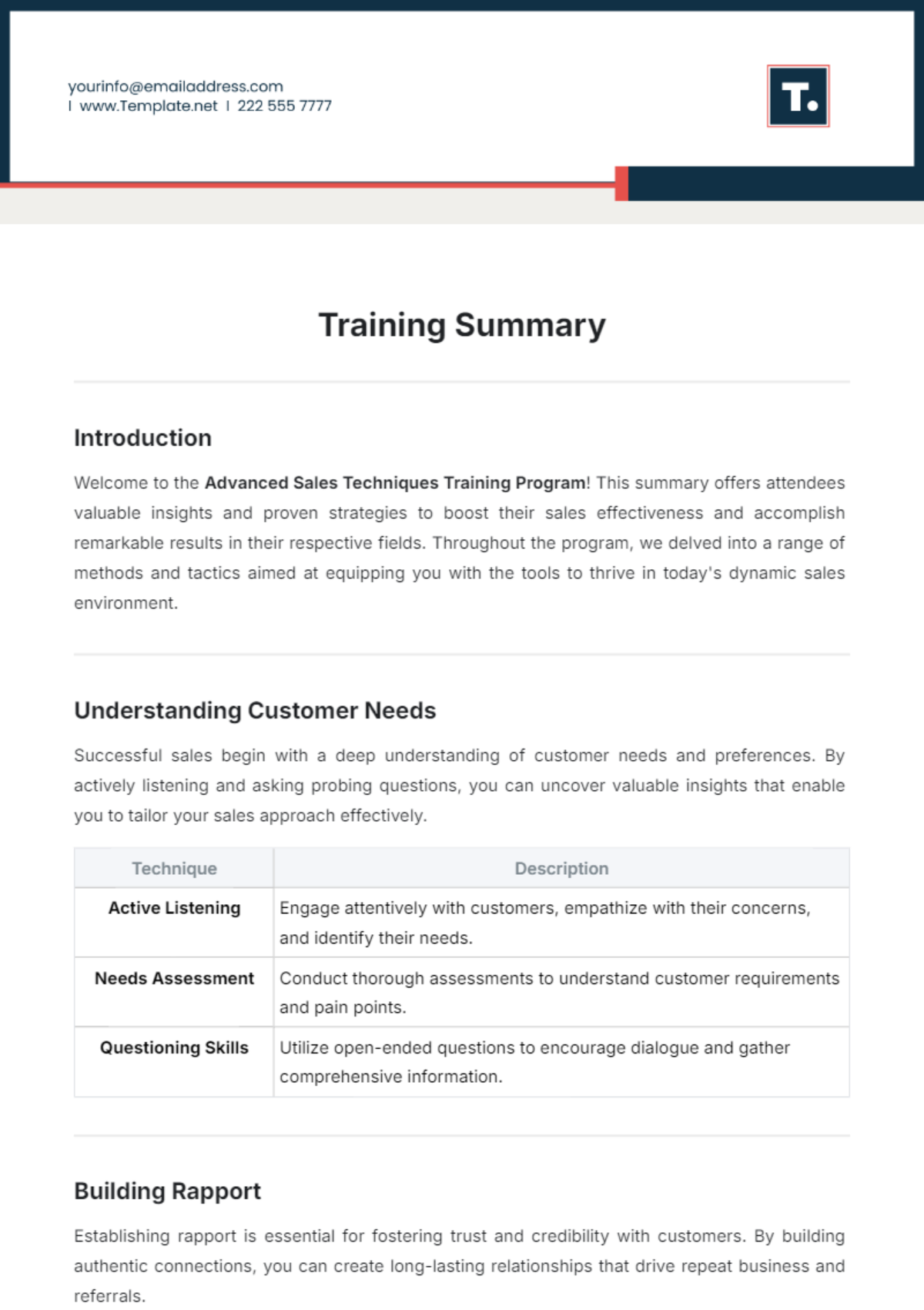
Free Incident Summary
Introducing the Incident Summary Template from Template.net - your go-to solution for streamlined documentation. This editable and customizable template simplifies incident reporting with its user-friendly format. Crafted for efficiency, it's seamlessly editable in our Ai Editor Tool, ensuring hassle-free customization. Elevate your reporting process today!