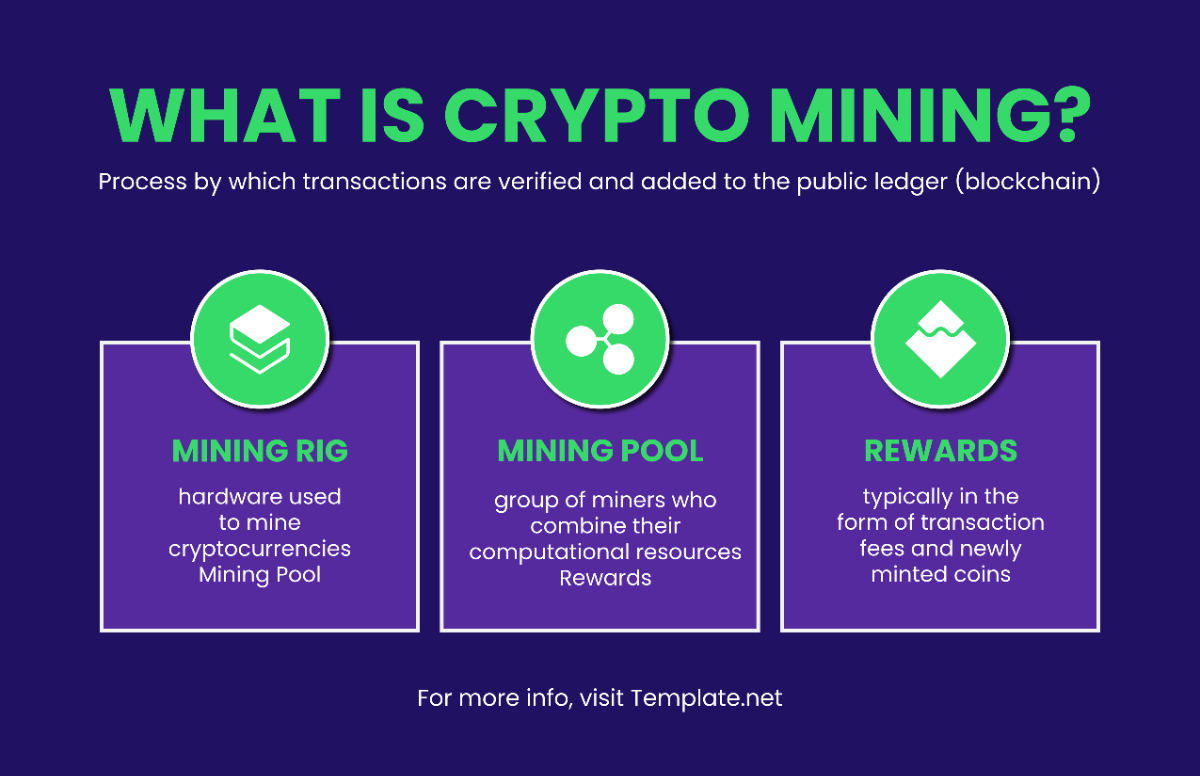
Key Handover Protocol
Name | [YOUR NAME] |
|---|---|
Company | [YOUR COMPANY NAME] |
Department | [YOUR DEPARTMENT] |
Date | [DATE] |
1. Introduction
The Key Handover Protocol (KHP) delineates the procedures and guidelines essential for the secure exchange of cryptographic keys between involved parties in real estate transactions. This protocol serves as a cornerstone in ensuring communication channels' confidentiality, integrity, and authenticity, thereby safeguarding sensitive information exchanged during key handover processes.
2. Scope
The scope of this protocol encompasses all phases of key handover, including but not limited to, initial key generation, key distribution, key storage, and key revocation. It applies to all entities involved in real estate transactions, including buyers, sellers, real estate agents, and legal representatives.
3. Objectives
The primary objectives of the Key Handover Protocol are as follows:
Facilitate secure and efficient exchange of cryptographic keys.
Ensure confidentiality of sensitive information related to property transactions.
Guarantee the integrity of data transmitted during key handover processes.
Authenticate the identities of parties involved in the key exchange.
Provide clear guidelines for key management and storage.
4. Procedures
4.1 Key Generation:
Cryptographic keys shall be generated using industry-standard algorithms.
Keys should be of sufficient length to withstand cryptographic attacks.
Key generation should occur in a secure environment, free from potential threats or vulnerabilities.
4.2 Key Distribution:
Before key exchange, parties must establish mutual authentication.
Keys shall be exchanged securely via encrypted channels, such as secure messaging protocols or secure file transfer mechanisms.
Parties must verify the authenticity of received keys through digital signatures or certificates.
4.3 Key Storage:
Cryptographic keys shall be stored securely in encrypted formats.
Access to key storage facilities shall be restricted to authorized personnel only.
Regular audits and assessments of key storage mechanisms shall be conducted to ensure compliance with security standards.
4.4 Key Revocation:
In the event of compromise or loss of cryptographic keys, immediate revocation procedures shall be initiated.
Revoked keys shall be securely archived and replaced with new keys using established key distribution channels.
All relevant parties shall be promptly notified of key revocation and replacement.
5. Compliance and Enforcement
All parties involved in real estate transactions are required to adhere to the Key Handover Protocol. Non-compliance may result in the termination of contractual agreements and legal ramifications as stipulated by relevant laws and regulations.
6. Revision History
This section shall document any revisions or updates made to the Key Handover Protocol, including dates of revision and details of modifications.
7. Conclusion
The Key Handover Protocol serves as a vital framework for ensuring the secure exchange of cryptographic keys within real estate transactions. By adhering to the procedures outlined herein, parties can uphold the confidentiality, integrity, and authenticity of key handover processes, thereby fostering trust and security in real estate transactions.