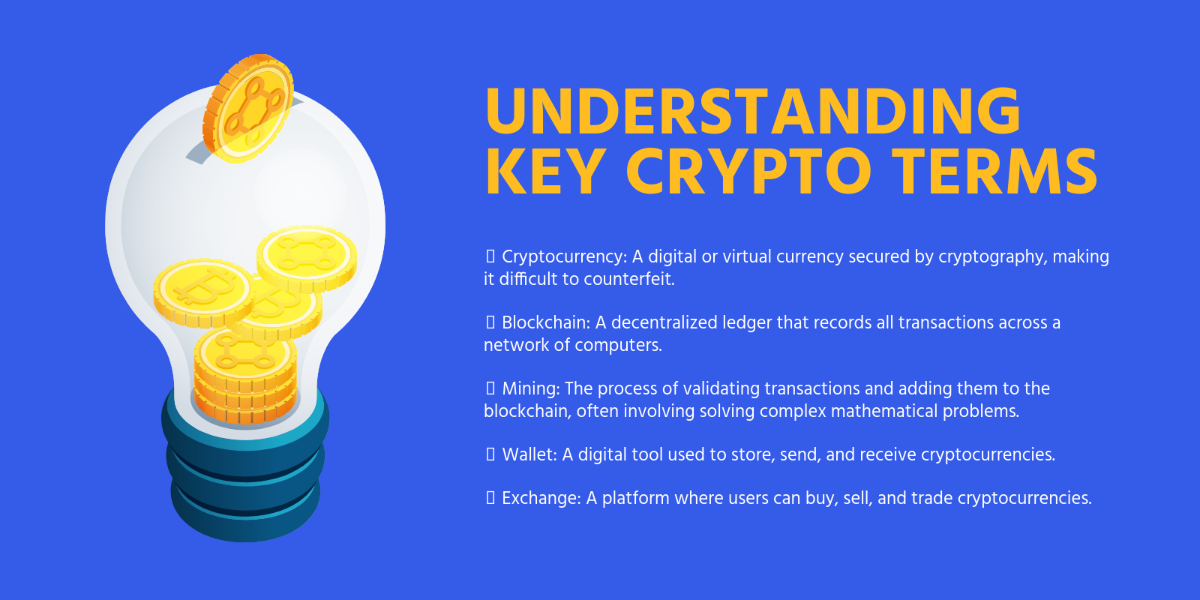
DATA SEARCH PROTOCOL
Name: | [Your Name] |
Company Name: | [Your Company Name] |
Department: | [Your Department] |
Date: | [Date] |
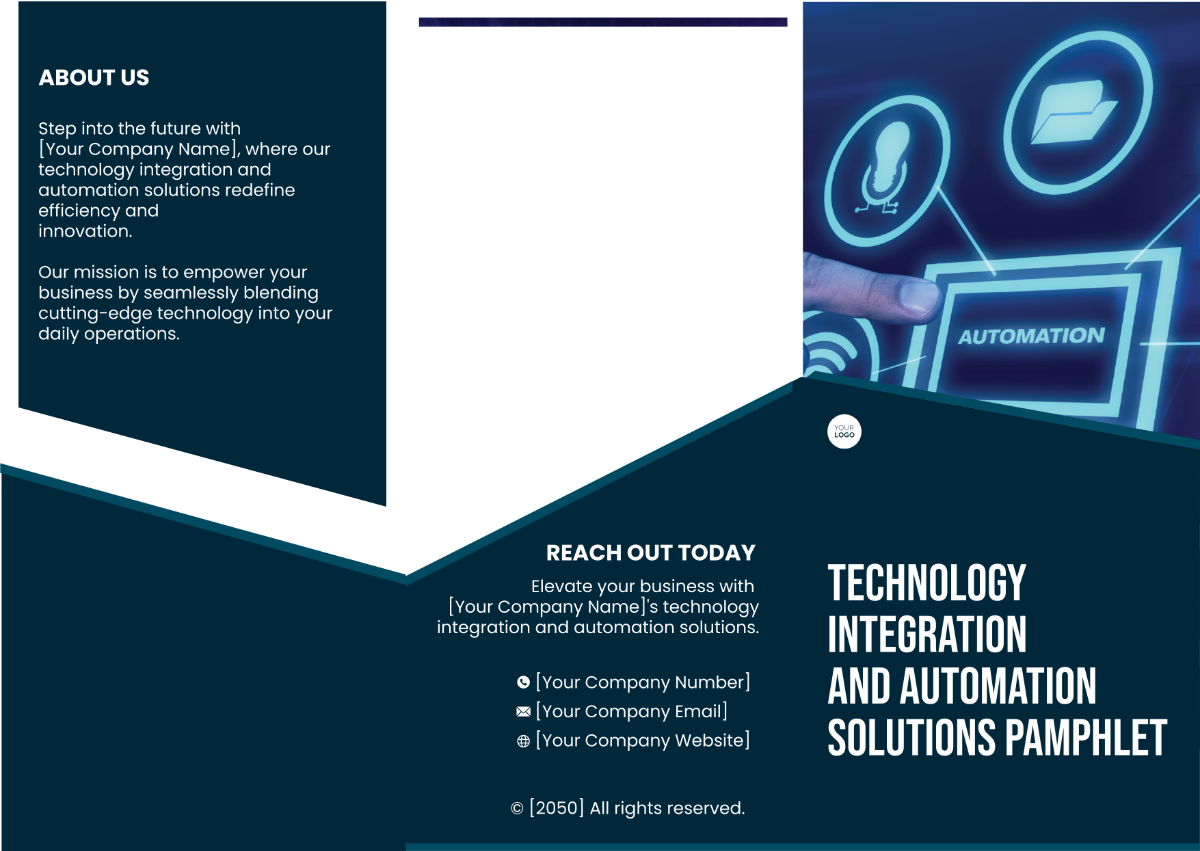
In today's digital age, efficient data management is essential for organizational success. This protocol serves as a comprehensive guide for all employees on the procedures and best practices for conducting data searches within our systems. By following this protocol diligently, we can streamline information retrieval processes, safeguard sensitive data, and maintain compliance with relevant regulations and industry standards. Let's optimize our data search practices to drive productivity and uphold the integrity of our operations.
I. Objectives
The objective of this Data Search Protocol is twofold:
Promote efficient retrieval of information: Contributing to the productivity and effectiveness of staff by facilitating streamlined access to necessary data.
Ensure data security, compliance, governance, risk management, and knowledge management: Uphold to the highest standard to mitigate risks associated with data handling and promote responsible data management practices.
II. Protocol Overview
This protocol serves as a comprehensive framework governing the access and retrieval of data within our organization's systems. It outlines the types of data accessible, authorization levels, search procedures, compliance requirements, and responsibility for oversight. By providing a clear and structured framework, the protocol aims to enhance operational efficiency, mitigate risks associated with data handling, and foster a culture of data stewardship and compliance within the organization.
III. Procedure
The following are the steps to follow when conducting a data search within systems:
Authenticate Your Credentials: Log in to the data management system using authorized credentials to ensure accountability and traceability of data access.
Select Data Type: Identify and select the type of data you need to access, ensuring that it aligns with your authorized access level and job responsibilities.
Enter Search Parameters: Input relevant search parameters, such as keywords, dates, or specific criteria, to narrow down the search results effectively.
Retrieve and Review Data: Access the retrieved data and review it for accuracy, relevance, and compliance with internal policies and external regulations.
Log Out Securely: After completing the data search, log out from the data management system to prevent unauthorized access and maintain data security.
IV. Data Collection
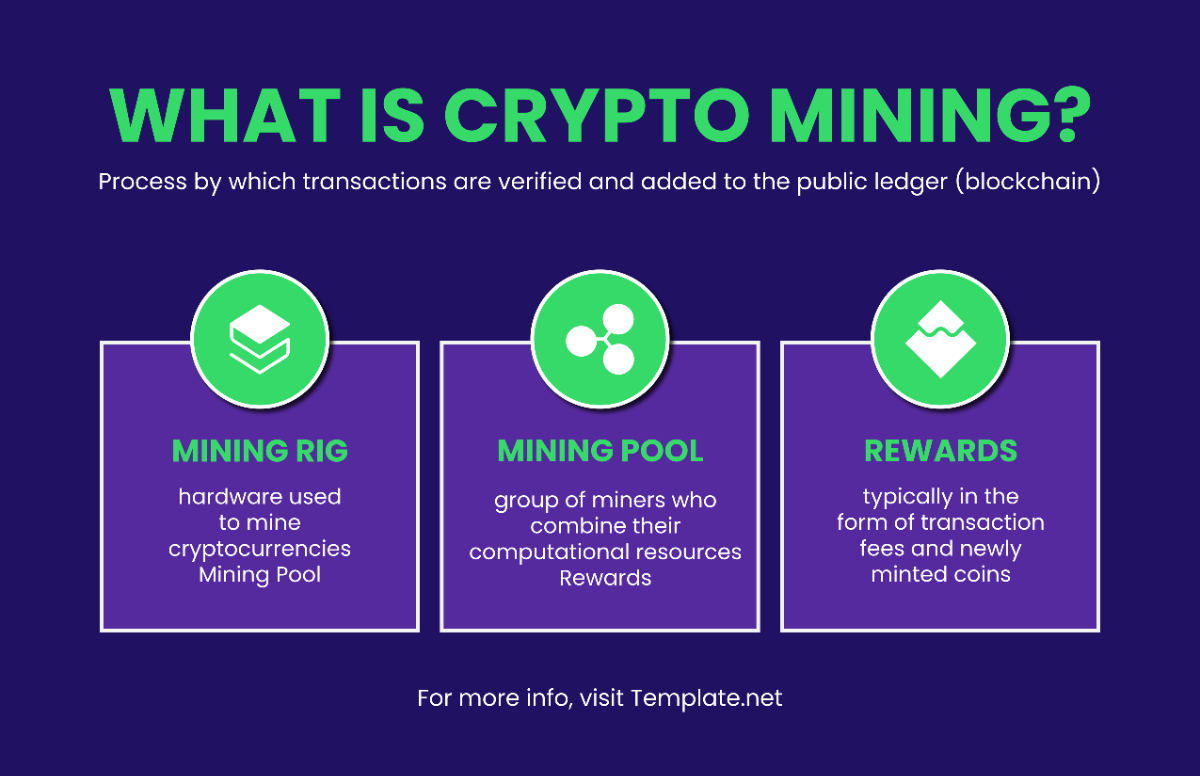
Data for this protocol was collected from several sources, including:
Internal Databases: Information stored within the company's internal systems and databases.
Regulatory Guidance Documents: Such as those provided by GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and PCI DSS (Payment Card Industry Data Security Standard), ensuring alignment with legal and regulatory requirements.
Feedback from Staff and Stakeholders: Input from employees, management, and other stakeholders regarding their experiences and concerns related to data search and management processes.
V. Safety Considerations
This protocol focuses on data safety by ensuring only authorized personnel access sensitive data and enforcing measures to prevent unauthorized access or data breaches. Safety considerations include:
Access Control: Implementing role-based access controls to restrict data access to authorized personnel only.
Encryption: Utilizing encryption techniques to protect data both in transit and at rest, safeguarding it from unauthorized interception or theft.
Monitoring and Auditing: Regularly monitoring data access and usage patterns, conducting audits to detect and mitigate potential security risks or policy violations.
VI. Expected Results
The expected results of implementing this protocol include:
Improved Efficiency in Data Retrieval: Streamlined processes for accessing and retrieving data, leading to increased productivity and effectiveness.
Enhanced Data Security: Implementation of robust security measures to protect sensitive data from unauthorized access, breaches, or misuse.
Increased Compliance with Data Regulations: Adherence to legal and regulatory requirements, such as GDPR, HIPAA, and PCI DSS, to avoid penalties and reputational damage.
Reduced Risk of Data Breaches or Misuse: Proactive measures to identify and mitigate potential risks, minimizing the likelihood of data breaches or unauthorized data access.
By adhering to this Data Search Protocol, employees can ensure not only efficient access to necessary information but also the safeguarding of sensitive data and adherence to regulatory standards. Continuously following and refining this protocol will contribute to the company's overall success by maintaining high standards of data management, security, and compliance. Thank you for your commitment to upholding these principles in your work.
_____________________________________________________________________________________