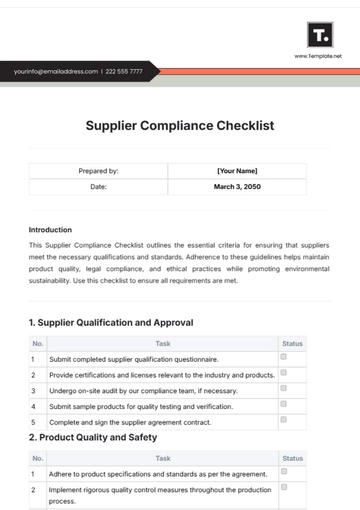
Free FEDRAMP Compliance Checklist

I. Compliance Overview:
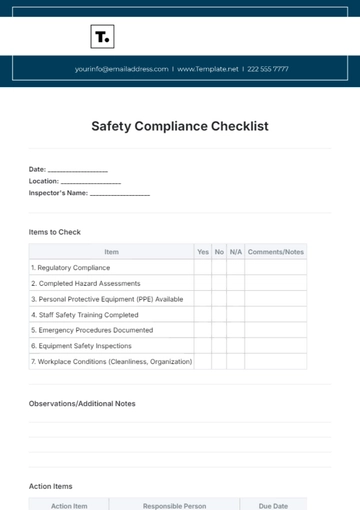
The Federal Risk and Authorization Management Program (FEDRAMP) establishes standardized security requirements for cloud service providers (CSPs) that provide services to federal agencies. FEDRAMP compliance ensures that CSPs adhere to strict security controls and processes to protect sensitive government data in the cloud
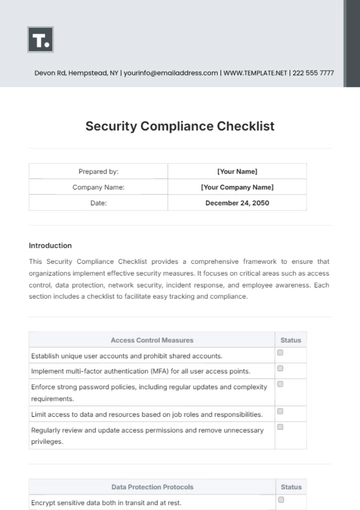
II. Access Control
Implement role-based access control (RBAC) to restrict access to authorized personnel.
Enforce strong password policies, including regular password updates and complexity requirements.
Utilize multi-factor authentication (MFA) for accessing sensitive systems and data.
Regularly review and update access permissions based on personnel changes or job roles.
III. Data Protection
Encrypt data both at rest and in transit using FIPS 140-2 compliant algorithms.
Implement data loss prevention (DLP) mechanisms to prevent unauthorized data disclosure.
Maintain data integrity through mechanisms such as hashing and digital signatures.
Establish clear data classification policies and procedures.
IV. Security Configuration Management
Regularly update and patch all software and systems to mitigate known vulnerabilities.
Implement secure configuration baselines for operating systems, applications, and network devices.
Conduct regular vulnerability scanning and remediation.
Utilize intrusion detection and prevention systems (IDS/IPS) to monitor and respond to security threats.
V. Incident Response
Develop and maintain an incident response plan outlining procedures for detecting, reporting, and responding to security incidents.
Conduct regular tabletop exercises to test the effectiveness of the incident response plan.
Ensure clear communication channels and points of contact for reporting security incidents.
Document and analyze security incidents to improve future incident response procedures.
VI. Physical Security
Restrict physical access to data centers, server rooms, and other sensitive areas.
Implement environmental controls such as temperature and humidity monitoring.
Maintain documented procedures for handling and disposing of physical media containing sensitive data.
Regularly audit and monitor physical security controls to ensure compliance.
VII. Continuous Monitoring
Implement continuous monitoring tools and processes to detect and respond to security events in real-time.
Conduct regular security assessments and penetration testing to identify and remediate vulnerabilities.
Maintain comprehensive audit logs for all systems and applications.
Establish metrics and key performance indicators (KPIs) to measure the effectiveness of security controls.
VIII. Security Training and Awareness
Provide regular security awareness training for all personnel with access to sensitive systems and data.
Ensure employees are aware of their security responsibilities and best practices.
Conduct phishing simulations to test employee awareness and responsiveness.
Maintain documentation of security training activities and employee participation.
IX. Signature:
I hereby confirm that all the above security controls and processes have been implemented and maintained to achieve FEDRAMP compliance.

[YOUR POSITION]
Date: ________________________
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
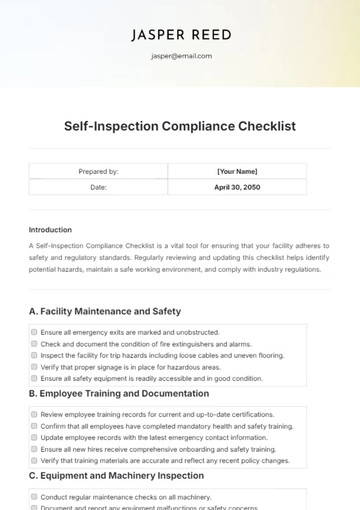
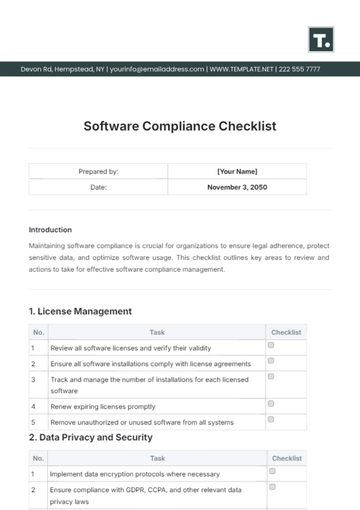
Discover unparalleled convenience with Template.net's FEDRAMP Compliance Checklist Template. Crafted for seamless integration into your workflow, this editable and customizable resource empowers your team to streamline compliance efforts effortlessly. Editable in our AI Editor Tool, it ensures tailored solutions for your unique requirements, ensuring compliance with ease
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist