HIPAA Compliance
I. Introduction
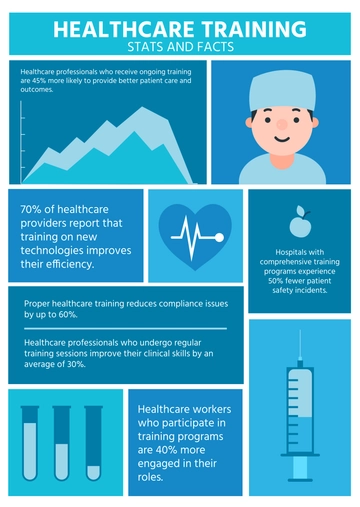
HIPAA is a key legislation ensuring confidentiality, security, and privacy of patient health information, thus building trust with healthcare providers.
II. Employee Training and Awareness
III. Training Objectives
Understanding HIPAA Regulations:
IV. Ensuring Patient Privacy
V. Security Protocols
Comprehensive Security Measures: Employees will be trained to implement a range of security protocols tailored to safeguard electronic Protected Health Information (ePHI). This includes:
VI. Training Content
HIPAA Basics:
VII. Privacy Practices
Intensive HIPAA training on patients' rights, covering aspects such as:
Practical guidance on handling PHI, emphasizing:
VIII. Security Protocols
Instructions on securing ePHI:
IX. Training Methods
Online modules, customized for various organizational roles, enable flexible, self-paced learning for employees.
X. Assessment and Evaluation
XI. Documentation and Record-keeping
XII. Ongoing Training and Updates
Timely communication of regulatory updates and policy changes through various channels, including email bulletins, intranet announcements, and training sessions.
XIII. Signature

[Compliance Manager]
[Date]
Compliance Templates @ Template.net