Security Use Case
Created by: [YOUR NAME]
Company: [YOUR COMPANY NAME]
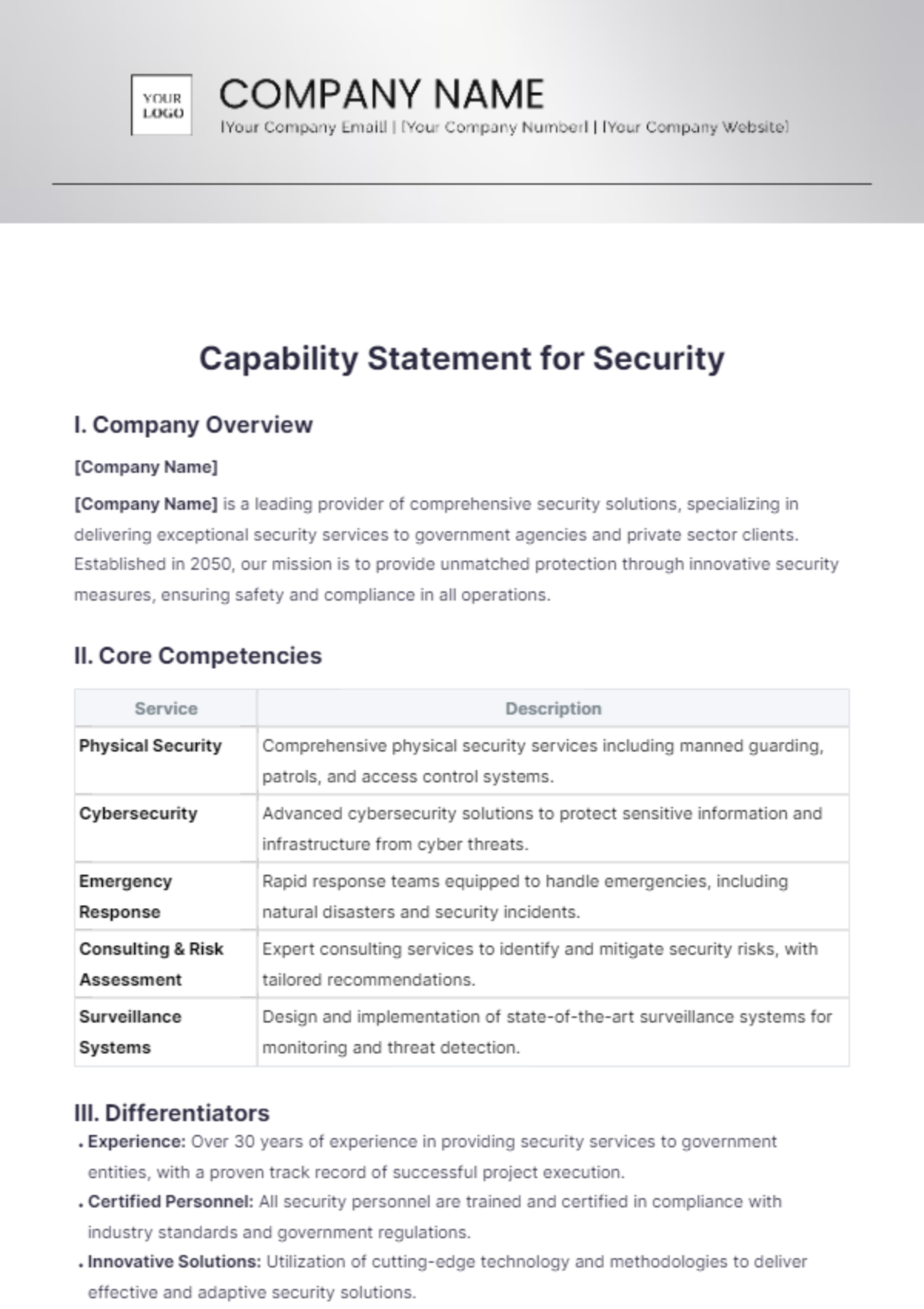
I. Introduction
This Security Use Case Template is designed to outline the processes and procedures involved in managing security tasks within [YOUR COMPANY NAME]. This document will aid in identifying, executing, and assessing security measures effectively.
II. Use Case Identification
Use Case Name: [USE CASE NAME]
Use Case ID: [USE CASE ID]
III. Stakeholders and Roles
Security Manager: [SECURITY MANAGER NAME]
IT Specialist: [IT SPECIALIST NAME]
Data Protection Officer: [DATA PROTECTION OFFICER NAME]
IV. Use Case Overview
Provide a detailed overview of the security use case, including the main objectives and significance to overall organizational security. Be clear on the impact of successful implementation.
V. Preconditions
Describe the conditions that must be met before the use case can be executed. Example preconditions include:
User authentication must be verified.
Relevant security policies should be up to date and accessible.
VI. Use Case Steps
Identify the security requirement: [SPECIFIC SECURITY REQUIREMENT]
Analyze current infrastructure for vulnerabilities: [VULNERABILITY ASSESSMENT TOOLS/METHODS]
Develop mitigation strategies: [MITIGATION TOOLS/TECHNIQUES]
Implement security measures
Monitor and review the effectiveness of the implemented security measures
VII. Alternative Paths
Discuss possible alternative actions in case the main use case path is obstructed or fails. Examples include:
If authentication fails, use an alternative verification method like [ALTERNATIVE VERIFICATION METHOD].
If a mitigation strategy fails, reevaluate the threat and develop a new strategy.
VIII. Postconditions
Detail what must be true upon the successful completion of the use case. For instance:
Security measures are fully operational.
All system vulnerabilities identified in the use case are addressed.
IX. Security Requirements
Specify the security requirements that are associated with this use case, such as:
Data encryption standards: [SPECIFY STANDARDS]
Access control mechanisms
Regular security audits should be conducted
X. Exception Handling
List potential exceptions during the use case execution and describe how these should be handled. For example:
Data breach or data leak situations
Fraud detection and response procedures
XI. Approval
Name | Role | Signature | Date |
|---|---|---|---|
[APPROVER NAME] | [APPROVER ROLE] | [DIGITAL/PHYSICAL SIGNATURE] | [APPROVAL DATE] |