Proof of Concept Use Case
I. Use Case Identification
Use Case ID: UCT-001
Title: Manage [YOUR FUNCTIONALITY]
Created By: [YOUR NAME]
Date Created: [DATE]
Last Updated: [DATE]
Version: 1.0
II. Use Case Overview
A brief description of what the Use Case seeks to achieve within the context of the POC. This section outlines high-level goals and the scope of the POC.
Goal: Establish a verification method for the proposed solution.
Scope: Limit the POC to key functionalities to showcase basic capabilities and benefits.
III. Actors
Identify all the actors who interact with the system, defining their roles within this Use Case.
Actor | Role |
|---|---|
[USER/SENDER] | Primary user initiating the use case actions |
System | Responds to actions performed by [USER/SENDER] |
IV. Pre-Conditions
Identify what must be true or satisfied before the use case is initiated.
[USER/SENDER] must be logged into the system.
System data must be pre-loaded with necessary configuration settings.
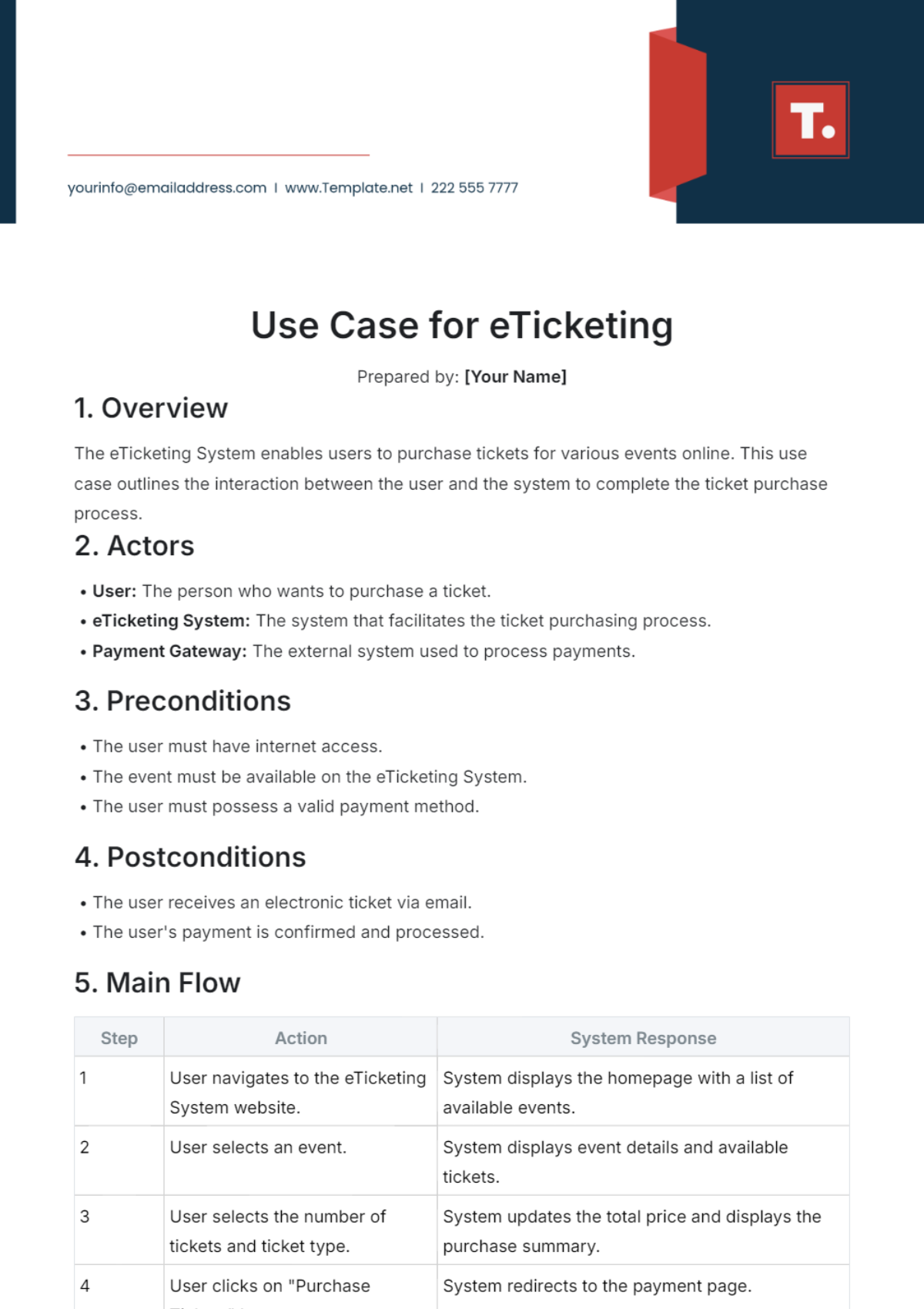
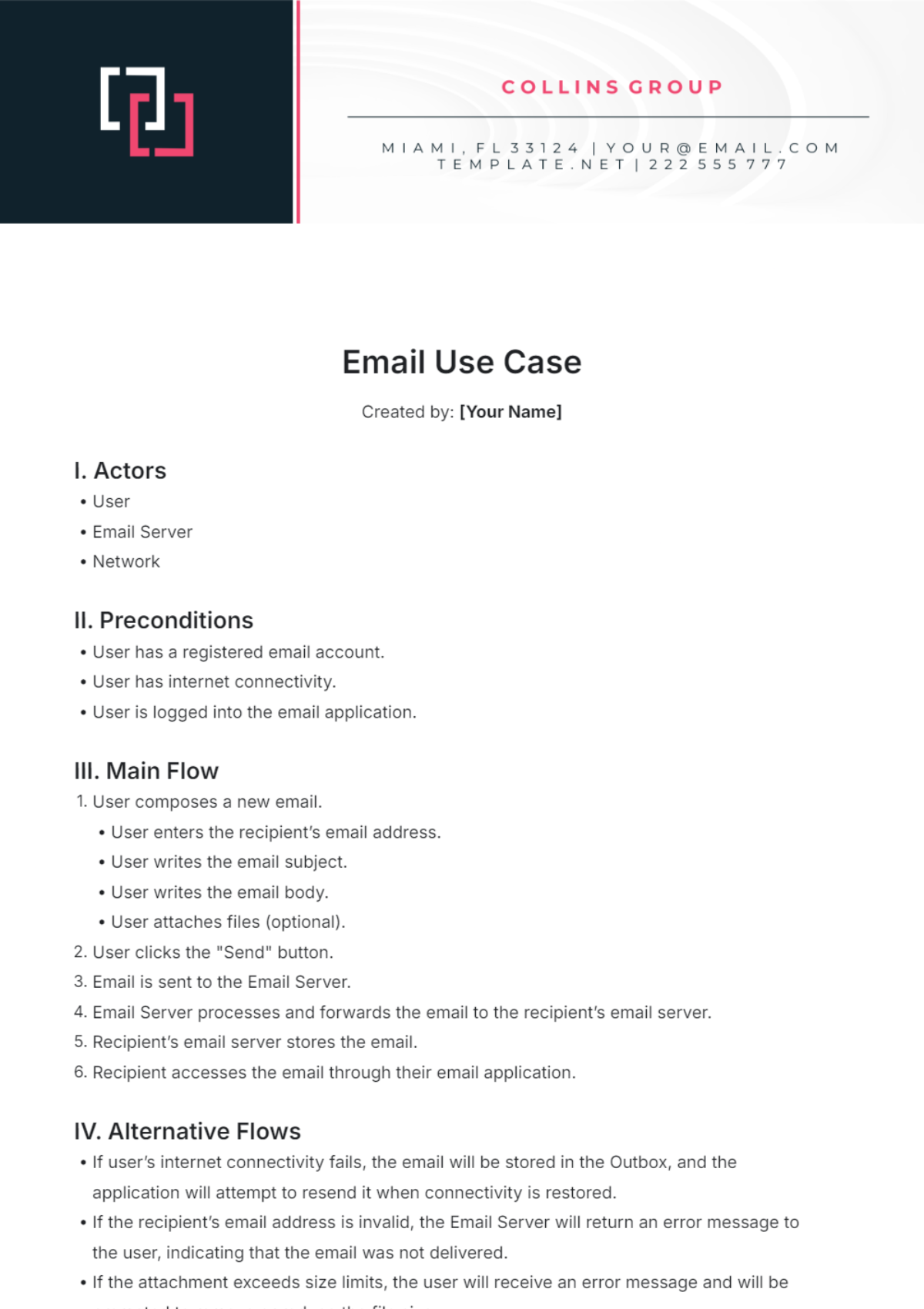
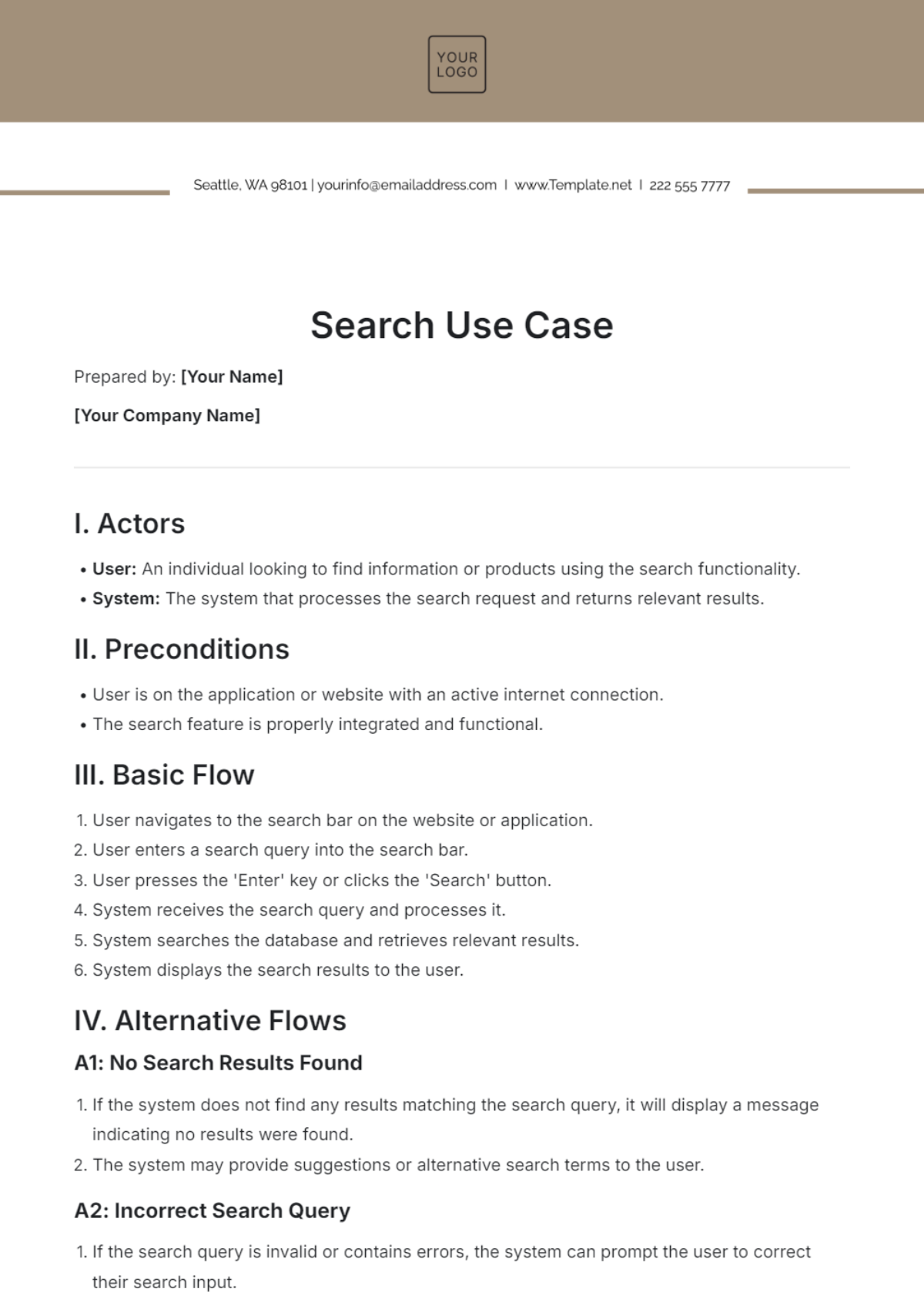
V. Basic Flow of Events
This section provides a step-by-step narrative of the use case’s basic flow, depicting interactions between the actor and the system to achieve the goal.
[USER/SENDER] initiates the process.
The system validates input against pre-defined criteria.
Data processing is performed, and results are generated.
Results are displayed to [USER/SENDER].
VI. Alternative Flows
Detail any alternative sequences of events that may happen in the use case’s execution.
If data validation fails, the system alerts [USER/SENDER] and requests re-entry of data.
If the system experiences a technical issue, [USER/SENDER] is notified, and the issue is logged for system administrators.
VII. Post-Conditions
Outline what must be true upon completing the basic flow and any alternative flows.
Data is stored correctly in database.
[USER/SENDER] has received appropriate confirmation of successful execution.
VIII. Assumptions and Constraints
List any assumptions and constraints that impact the use case execution, including limitations.
System uptime is guaranteed 99% of the time.
Only registered users can initiate this use case.
IX. Appendices
Additional information that is pertinent but not integral to the main body of the use case.
Appendix A: System Configuration Settings
Appendix B: Data Validation Criteria