Crisis Solution Research Process
Prepared by: [Your Name]
Company: [Your Company Name]
Date: [Date]
1. Introduction
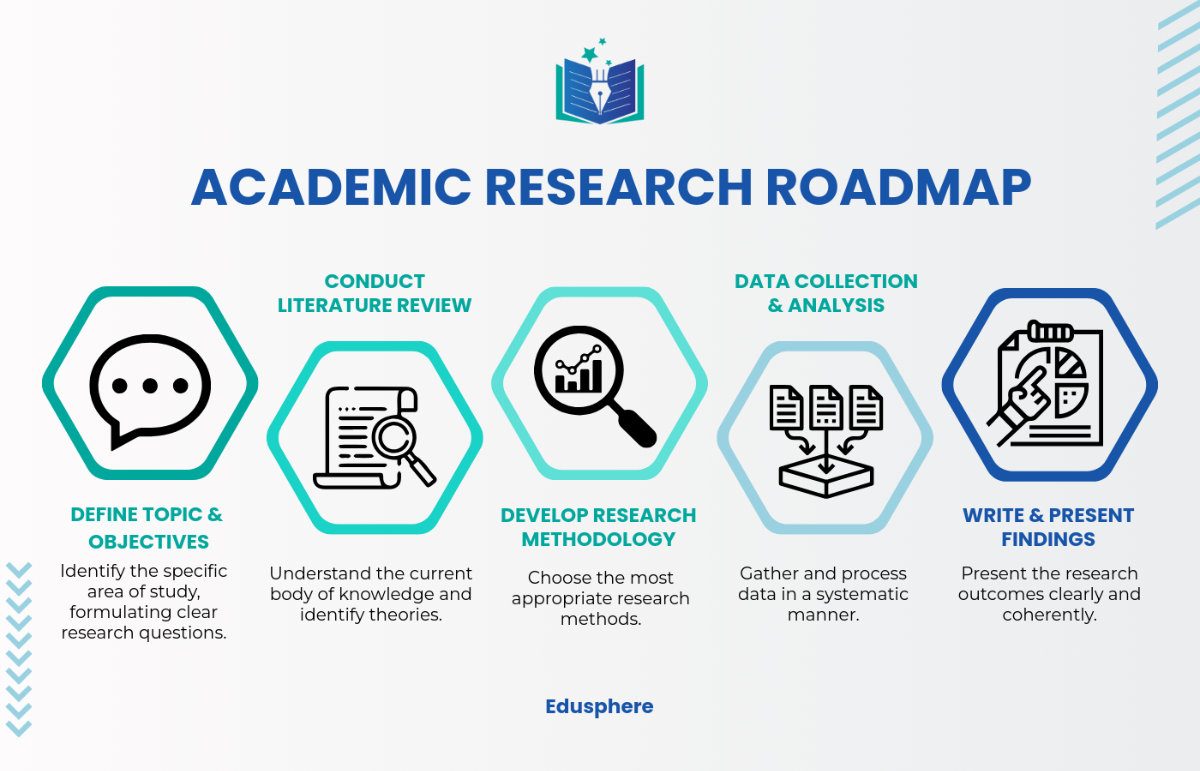
The purpose of this document is to outline the Crisis Solution Research Process for the cybersecurity breach. This research aims to identify the causes of the breach, assess its impact, and develop effective solutions to mitigate future risks. The scope includes an in-depth analysis of the breach's effects on operations, data integrity, and stakeholder confidence.
2. Crisis Description
In January 2051, a significant cybersecurity breach occurred, compromising sensitive customer data and disrupting internal operations. The breach was identified as a sophisticated attack by an unknown external entity, leading to unauthorized access to confidential information. The impact includes potential legal liabilities, loss of customer trust, and operational downtime.
3. Data Collection
Data collection methods included:
Internal Security Logs: Analysis of system logs and breach detection alerts.
Customer Feedback: Surveys and interviews with affected customers to gauge impact and concerns.
Expert Interviews: Consultations with cybersecurity experts to understand attack vectors and vulnerabilities.
Incident Reports: Review of incident reports from internal and external sources to compile a comprehensive overview.
4. Analysis
The analysis revealed several key issues:
Security Vulnerabilities: Identified gaps in the current cybersecurity framework, including outdated software and inadequate encryption methods.
Impact Assessment: Estimated that approximately 30% of customer data was compromised, leading to potential financial losses and reputational damage.
Root Causes: The breach was traced back to a combination of weak access controls and phishing attacks that exploited employee weaknesses.
5. Solution Development
Proposed solutions include:
Enhanced Cybersecurity Measures: Implementing advanced encryption protocols, multi-factor authentication, and regular security updates.
Employee Training: Conducting comprehensive cybersecurity training programs to improve awareness and response to phishing attempts.
System Upgrades: Upgrading outdated software and integrating more robust security systems to prevent future breaches.
Incident Response Plan: Develop a detailed incident response plan to quickly address and mitigate any future security threats.
6. Recommendations
Based on the analysis, the following recommendations are made:
Immediate Implementation: Adopt advanced cybersecurity measures and system upgrades within the next six months.
Ongoing Training: Establish a continuous employee training program with refresher courses every quarter.
Monitoring and Evaluation: Regularly review and update the cybersecurity framework, with a focus on emerging threats and technologies.
7. Implementation Plan
The implementation plan includes:
Timeline: Immediate actions are to begin in February 2051, with full implementation expected by August 2051.
Resource Allocation: Budget allocation of $5 million for cybersecurity enhancements and training programs.
Responsibilities: Assigning a dedicated cybersecurity team to oversee the implementation and ensure compliance with the new protocols.
8. Evaluation and Conclusion
8.1 Evaluation
Evaluation methods will involve:
Performance Metrics: Monitoring key performance indicators, such as the number of security incidents and system vulnerabilities.
Customer Feedback: Regular surveys to assess customer satisfaction and trust levels post-implementation.
Ongoing Audits: Conduct quarterly audits to evaluate the effectiveness of the new measures and make necessary adjustments.
8.2 Conclusion
The Crisis Solution Research Process provides a comprehensive framework for addressing the cybersecurity breach. By implementing the proposed solutions and recommendations, the organization will significantly enhance its security posture, restore customer trust, and mitigate the risk of future breaches. Ongoing monitoring and evaluation will ensure that the implemented measures remain effective and adaptable to emerging threats. This proactive approach is essential for safeguarding the organization’s operations and maintaining its reputation in the rapidly evolving cybersecurity landscape.