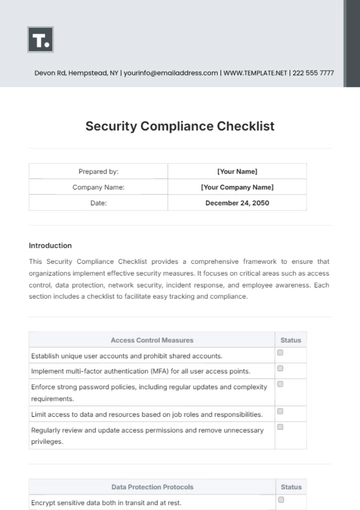
Security Compliance Checklist
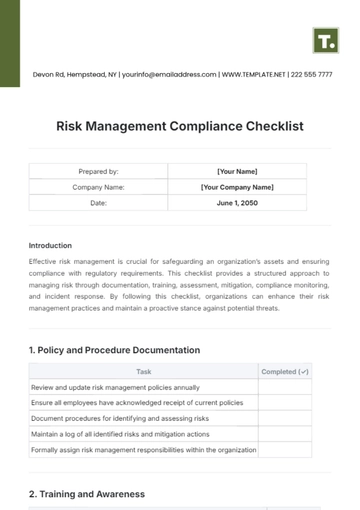
Prepared by: | [Your Name] |
Company Name: | [Your Company Name] |
Date: | December 24, 2050 |
Introduction
This Security Compliance Checklist provides a comprehensive framework to ensure that organizations implement effective security measures. It focuses on critical areas such as access control, data protection, network security, incident response, and employee awareness. Each section includes a checklist to facilitate easy tracking and compliance.
Access Control Measures | Status |
|---|
Establish unique user accounts and prohibit shared accounts. | |
Implement multi-factor authentication (MFA) for all user access points. | |
Enforce strong password policies, including regular updates and complexity requirements. | |
Limit access to data and resources based on job roles and responsibilities. | |
Regularly review and update access permissions and remove unnecessary privileges. | |
Data Protection Protocols | Status |
|---|
Encrypt sensitive data both in transit and at rest. | |
Establish data classification standards to identify and protect sensitive data. | |
Implement data loss prevention (DLP) solutions to monitor and control data movement. | |
Regularly back up data and test restoration procedures. | |
Create and enforce a data retention policy to limit the storage duration of sensitive data. | |
Network Security Controls | Status |
|---|
Deploy firewalls to monitor and control incoming and outgoing network traffic. | |
Install and maintain anti-virus and anti-malware software on all endpoints. | |
Set up intrusion detection and prevention systems (IDS/IPS) to identify and mitigate threats. | |
Segment networks to limit access to critical systems and sensitive data. | |
Regularly update and patch network devices and software to fix vulnerabilities. | |
Incident Response Planning | Status |
|---|
Develop and document an incident response plan outlining roles, responsibilities, and procedures. | |
Conduct regular incident response training and simulations for all relevant personnel. | |
Establish communication protocols for internal and external stakeholders during an incident. | |
Maintain an up-to-date list of contacts for incident response, including law enforcement and forensic experts. | |
Continuously update the incident response plan based on lessons learned from incidents and exercises. | |
Employee Security Awareness | Status |
|---|
Implement a comprehensive security awareness training program for all employees. | |
Conduct regular phishing simulations to educate employees on identifying email threats. | |
Update training materials regularly to include the latest security threats and best practices. | |
Ensure employees know how to report suspicious activities and potential security incidents. | |
Reinforce security awareness with periodic reminders and updates on current threats and mitigation strategies. | |
Checklist Templates @ Template.net