VPN Protocol
I. Introduction
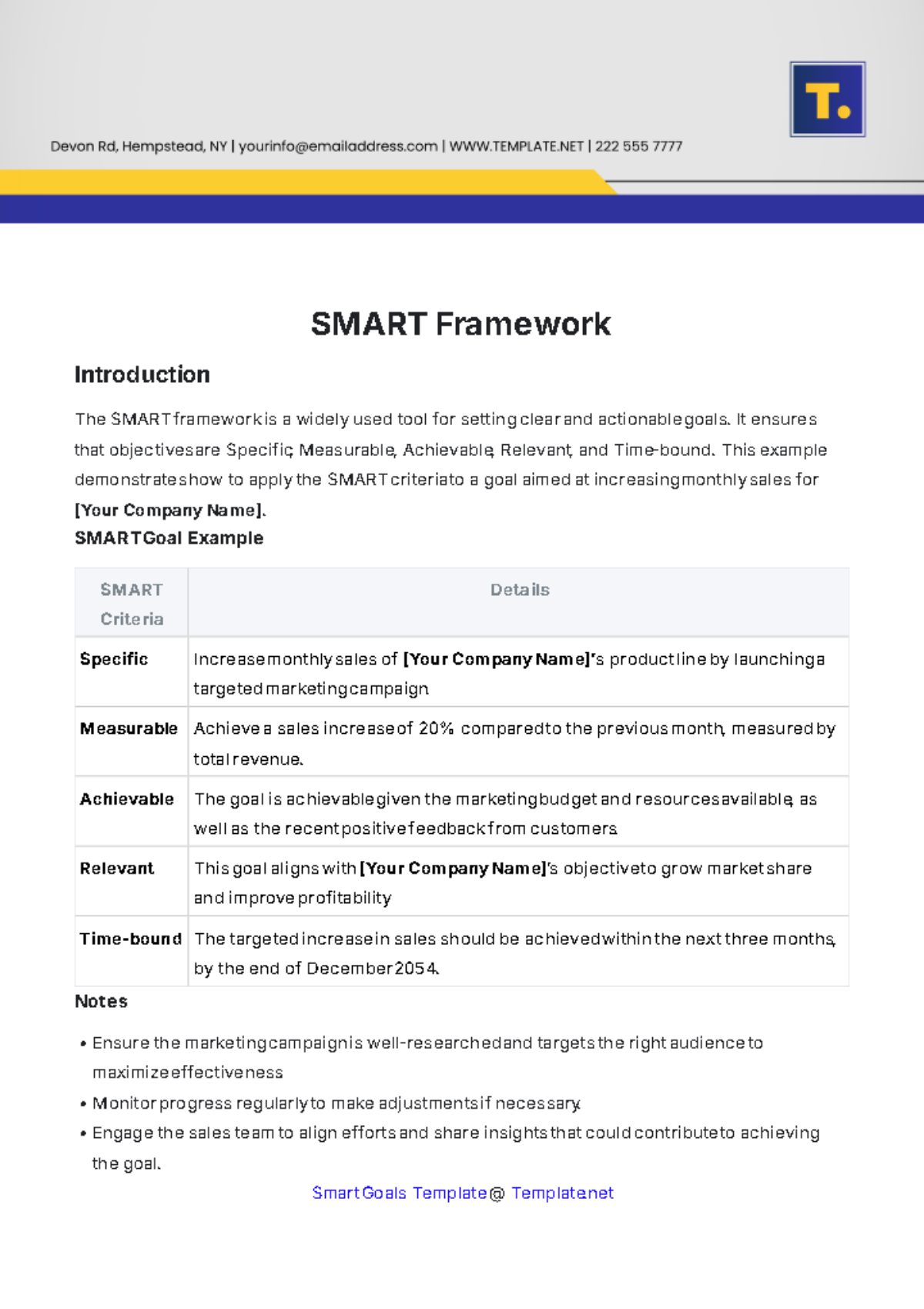
In an increasingly interconnected digital world, protecting personal data has become paramount. This VPN Protocol is designed to enhance data privacy, ensuring that users can browse the internet securely and anonymously. By implementing robust encryption methods and secure connection protocols, this framework empowers users to reclaim control over their online presence.
II. Purpose of the Protocol
The primary objective of this VPN Protocol is to safeguard user data by:
Encrypting data traffic between the user and the VPN server.
Hiding the user's IP address to prevent tracking.
Allowing secure access to websites and services without exposure to surveillance.
III. Protocol Overview
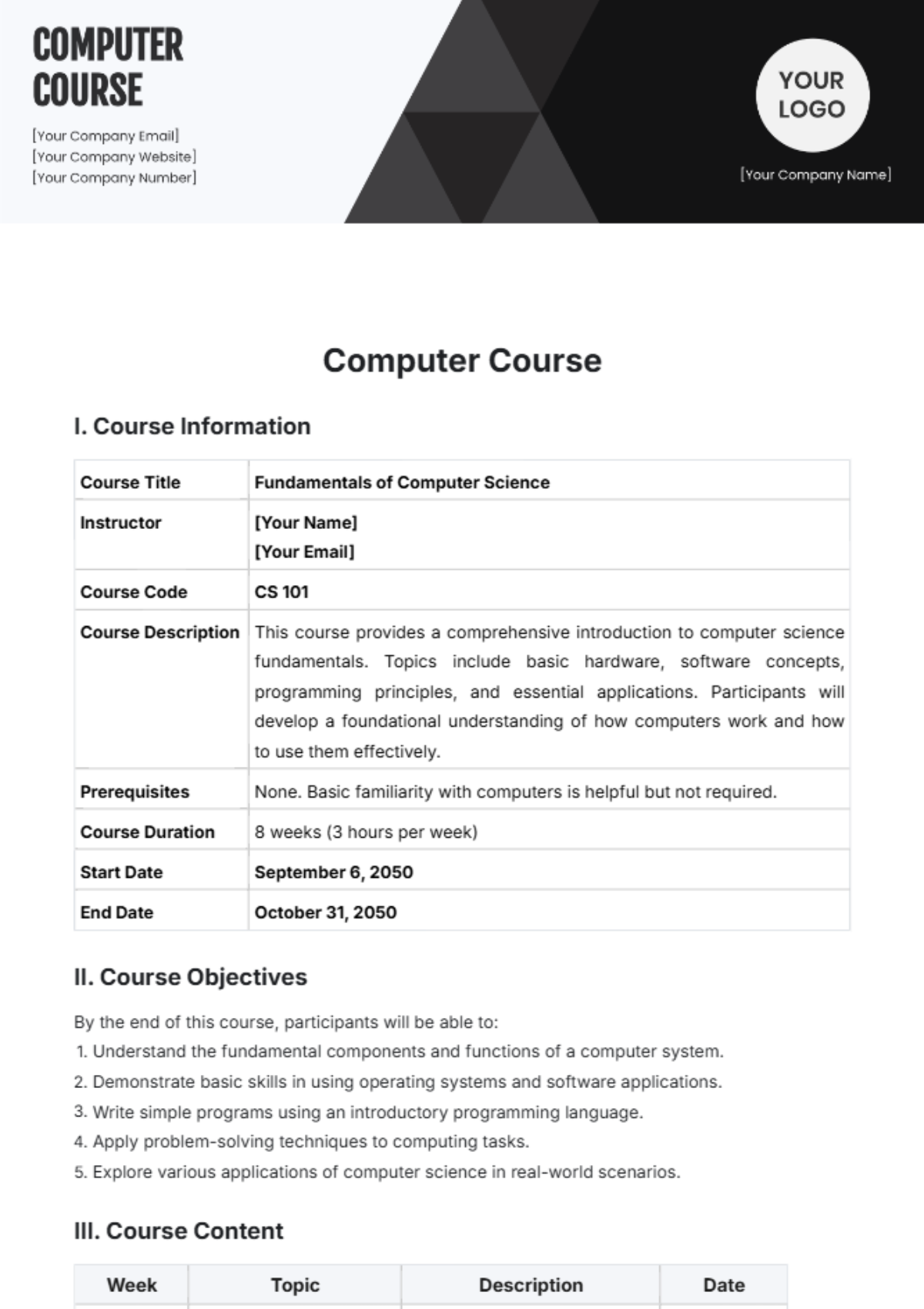
The VPN Protocol encompasses the following components:
Encryption Standards: Utilize advanced encryption algorithms such as AES-256 to secure data.
Authentication Mechanisms: Implement multi-factor authentication for user verification.
Connection Management: Ensure seamless connectivity with minimal latency and reliable uptime.
Data Leak Prevention: Integrate measures to prevent DNS and IP leaks.
Logging Policy: Maintain a strict no-logs policy to ensure user privacy.
IV. Implementation Steps
To effectively implement this VPN Protocol, the following steps should be taken:
User Enrollment: Users must sign up for the VPN service, providing necessary information.
Software Installation: Users download and install the VPN client on their devices.
Configuration Settings: Configure the VPN settings to use the specified protocols and encryption standards.
Connection Initiation: Users initiate a connection to the VPN server to start browsing securely.
V. User Guidelines
To ensure optimal data privacy, users should follow these guidelines:
Always connect to the VPN when using public Wi-Fi.
Regularly update the VPN client to benefit from the latest security features.
Avoid logging into sensitive accounts without the VPN enabled.
VI. Maintenance and Support
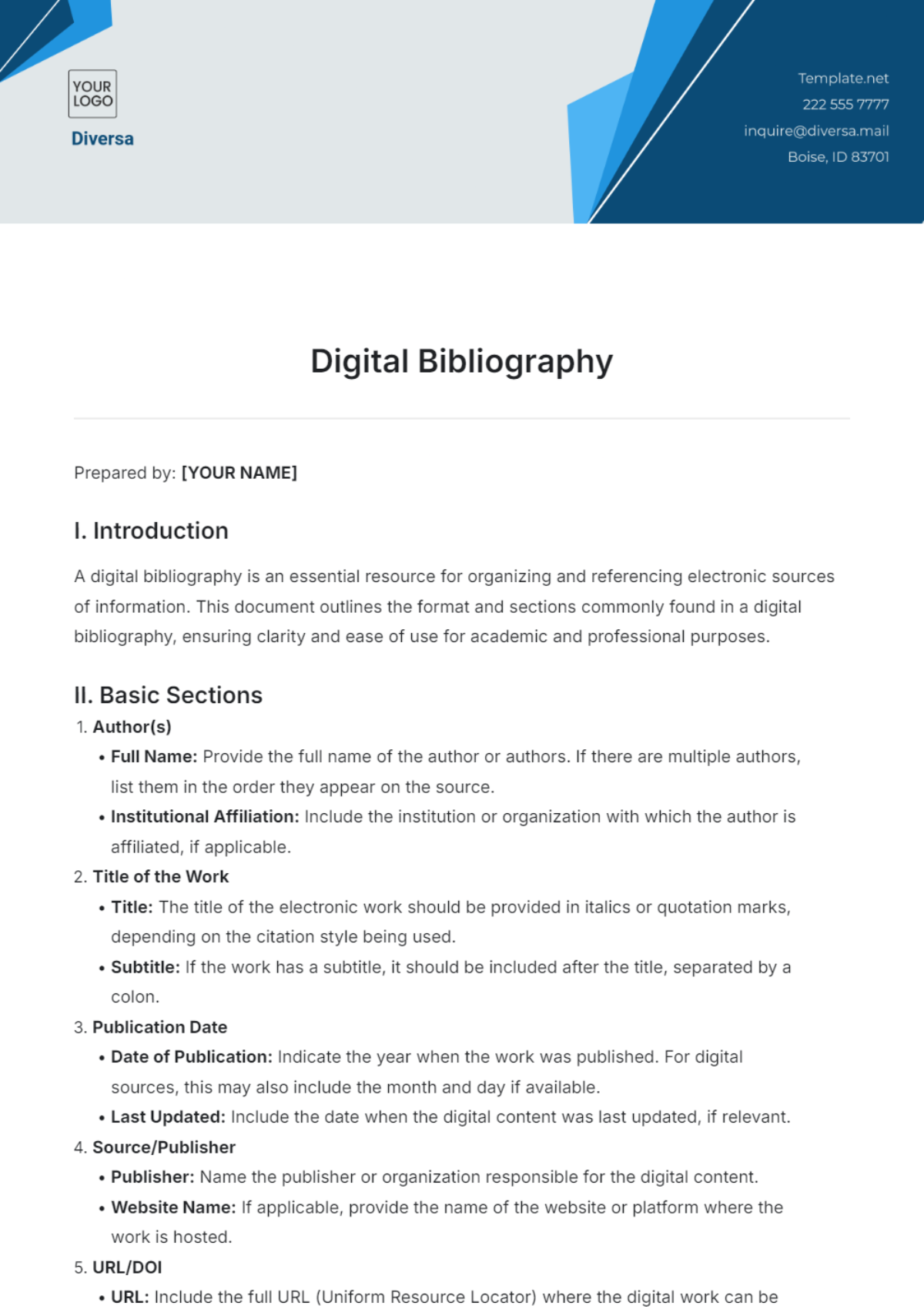
Ongoing support and maintenance are critical for the effectiveness of this protocol:
Date | Action | Responsible Party | Description | Status |
|---|---|---|---|---|
January 15, 2050 | Review Encryption Standards | [YOUR NAME] | Assess and update encryption methods | Scheduled |
March 22, 2050 | User Feedback Survey | [YOUR COMPANY NAME] | Collect user experiences and suggestions | Planned |
April 10, 2050 | Security Audit | [YOUR COMPANY NAME] | Conduct a comprehensive security evaluation | Pending |
June 5, 2050 | Update Privacy Policy | [YOUR NAME] | Revise policy based on recent changes | In Progress |
August 30, 2050 | Performance Review | [YOUR COMPANY NAME] | Analyze VPN speed and reliability | Scheduled |
October 12, 2050 | Implement User Training | [YOUR NAME] | Educate users on best practices for data privacy | Planned |
November 25, 2050 | Upgrade Server Infrastructure | [YOUR COMPANY NAME] | Enhance server capacity and performance | Not Started |
December 15, 2050 | Annual Compliance Review | [YOUR COMPANY NAME] | Ensure adherence to legal and regulatory standards | Planned |
December 31, 2050 | End-of-Year Summary | [YOUR NAME] | Document achievements and areas for improvement | Pending |
VII. Conclusion
This VPN Protocol serves as a vital framework for individuals and organizations aiming to enhance data privacy in the digital landscape of 2050 and beyond. By following the outlined guidelines and maintenance strategies, users can ensure that their online activities remain secure, private, and free from unwanted surveillance. Protecting personal data is not just a necessity; it is an essential right in today’s digital age.
Prepared by: [YOUR NAME]
Email: [YOUR EMAIL]