Security Service Policy
I. Introduction
A. Purpose
The Security Service Policy of [Your Company Name] aims to establish comprehensive guidelines and procedures that govern the protection of our information, systems, and physical resources. In an age where digital threats are continuously evolving, this policy seeks to ensure the confidentiality, integrity, and availability of sensitive data. By implementing robust security measures, we aim to prevent data breaches, safeguard proprietary information, and maintain the trust of our clients, partners, and employees. It is crucial that all stakeholders understand the importance of security in maintaining our reputation and operational efficiency.
B. Scope
This policy is applicable to all employees, contractors, partners, clients, and third-party entities associated with [Your Company Name]. It encompasses various security domains, including but not limited to:
Access control to physical and digital assets, ensuring that only authorized personnel have entry.
Comprehensive data handling procedures that outline how sensitive information should be processed and stored.
Network security measures that protect our systems from unauthorized access and cyber threats.
Incident response and disaster recovery plans that delineate steps to be taken in the event of a security breach.
Security monitoring and management practices to proactively identify vulnerabilities and threats.
C. Objectives
The objectives of this policy are as follows:
To ensure that all assets—be they physical, digital, or intellectual—are safeguarded against unauthorized access and potential breaches.
To create a clear framework for the consistent management of security risks, enabling swift action and mitigation strategies.
To establish a comprehensive incident response plan that details how to handle breaches, cyber-attacks, or natural disasters effectively.
To support regulatory compliance, ensuring adherence to relevant national and international laws, thus minimizing legal risks.
II. Information Security Governance
A. Governance Structure
[Your Company Name] has established a multi-tiered governance structure for effective information security management.
Chief Information Security Officer (CISO): The CISO is accountable for the overall security strategy, budget allocation, and ensuring that security policies align with organizational goals. The CISO plays a critical role in reporting to the executive team and providing updates on security posture.
Information Security Committee: This committee comprises representatives from key departments, including IT, HR, and Operations. They are responsible for setting security policies, reviewing incidents, and ensuring compliance with security regulations. Meetings are held quarterly to assess security posture and propose necessary adjustments. Each member is tasked with bringing insights from their departments to ensure a holistic approach to security.
Security Operations Team: Tasked with daily security management, this team is responsible for monitoring security alerts, conducting vulnerability assessments, and responding to incidents in real-time. They utilize advanced security tools to ensure all systems are fortified against potential threats. This includes continuous surveillance and analysis of security logs to identify unusual patterns of behavior that may indicate security breaches.
Third-party Auditors: Independent auditors are engaged annually to review [Your Company Name]’s security posture. They assess compliance with industry standards such as ISO 27001 and provide actionable insights for improvement. The auditors' findings are shared with management and incorporated into the ongoing security strategy.
B. Roles and Responsibilities
All employees, contractors, and third-party vendors must understand their specific responsibilities in protecting [Your Company Name]’s information assets.
Executive Management: Responsible for endorsing security policies, allocating resources, and ensuring that security measures align with business objectives. They play a critical role in fostering a security-focused culture within the organization. Executive management also collaborates with the CISO to make informed decisions on security investments based on identified risks.
Department Heads: Each department head is tasked with overseeing department-level security measures and ensuring compliance with corporate security policies. They are responsible for disseminating security information and conducting training within their teams. For example, department heads will ensure that their teams participate in mandatory training sessions on security protocols and threat awareness.
Employees: All employees must adhere to security practices, including proper password management, reporting incidents, and following access controls. Regular training sessions will be conducted to reinforce these responsibilities and update employees on emerging threats. Employees are encouraged to report suspicious activities without fear of repercussions, fostering an environment of vigilance and accountability.
C. Security Policy Review
The Security Service Policy will be reviewed at least annually or whenever significant changes occur in the business, technology, or legal landscape. The review process includes evaluating the effectiveness of existing controls and updating the policy to address any new threats or vulnerabilities. All changes will be communicated to stakeholders, and compliance will be ensured through mandatory training and awareness programs. This commitment to regular updates reflects our proactive approach to security.
III. Asset Management
A. Asset Identification
All assets within [Your Company Name] are categorized based on their criticality and sensitivity. The identification process is crucial in determining the appropriate security measures for each asset.
Data Assets: This includes customer information, intellectual property, financial records, and internal communication records. For instance, sensitive customer information, such as social security numbers and credit card data, is classified as high-risk and requires strict protection measures.
Hardware Assets: This category encompasses all physical devices, including servers, desktops, laptops, mobile devices, and IoT devices. For example, the company currently owns [500] desktops valued at an average of $[1,200] each, totaling approximately $[600,000]. Additionally, we maintain [200] laptops with an average cost of $[1,500] each, amounting to $[300,000].
Software Assets: These include operating systems, applications, and licenses. Software is regularly reviewed, with licenses for applications such as Microsoft Office and security software totaling about $[200,000] annually. This includes costs for updates and maintenance, ensuring that all software is current and secure.
B. Ownership of Assets
Every asset within [Your Company Name] must have a designated owner who is responsible for its lifecycle from acquisition to disposal. The asset owner is accountable for ensuring that appropriate security measures are in place, regularly updated, and compliant with company policies. Asset ownership also includes periodic audits of the asset to ensure continued security and operational integrity. For example, asset owners must conduct semi-annual reviews to verify that all devices and software are accounted for and that security measures are effective.
C. Acceptable Use
The use of company assets is strictly for business purposes. Personal use of company devices or data is prohibited unless specifically approved by the department head. The Acceptable Use Policy explicitly outlines restrictions on accessing non-work-related websites, sharing sensitive information, and installing unauthorized software. For example, employees found accessing social media sites during work hours may be subject to disciplinary action. Regular training will ensure that employees are aware of these policies and the consequences of non-compliance.
Acceptable Use Guidelines | Description |
|---|---|
Business Use Only | Company assets must be used solely for work-related tasks. |
Personal Use | Limited personal use may be allowed with prior approval. |
Prohibited Activities | Accessing inappropriate websites or downloading unauthorized software is strictly forbidden. |
IV. Data Protection and Privacy
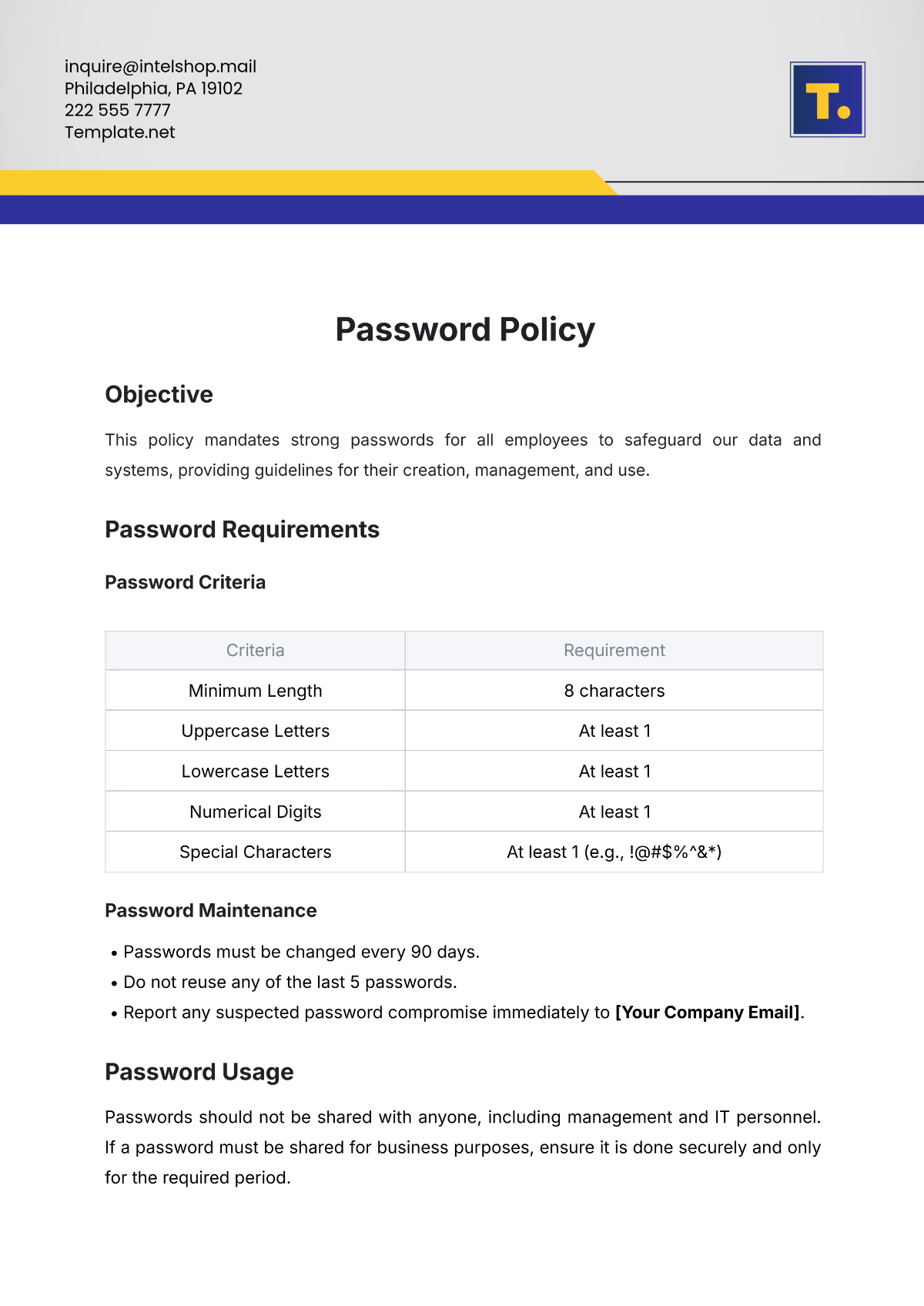
A. Data Classification
Data handled by [Your Company Name] is classified into three categories to ensure the appropriate level of protection, allowing the organization to allocate resources efficiently and mitigate risks effectively:
Confidential Data: This category includes customer data, intellectual property, and internal business strategies, such as financial projections and market analysis reports. This data is highly sensitive and requires the strongest level of protection to prevent unauthorized access. Access to this data is restricted to authorized personnel only.
Restricted Data: Employee records, payroll information, and certain financial reports fall into this category. Access to this data is limited to authorized personnel only, such as HR representatives and department heads. A breach of this data could result in significant legal ramifications and reputational damage.
Public Data: Data that can be freely shared without risk, such as press releases, marketing materials, and publicly available company information. Employees must ensure that sensitive data is not accidentally shared in public forums.
B. Data Encryption
All confidential and restricted data must be encrypted both at rest and in transit. Data encryption ensures that even if an unauthorized entity gains access, they will not be able to read or exploit the information. [Your Company Name] uses industry-standard encryption protocols such as AES-256 for data at rest and TLS 1.3 for data in transit. For example, all emails containing sensitive information are encrypted, which adds an additional layer of security to communications. This process helps to prevent data breaches, particularly during transmission over potentially insecure networks.
C. Data Retention and Disposal
Data must be retained only for as long as it is necessary to fulfill business needs or comply with legal and regulatory requirements. For instance, financial records must be kept for a minimum of [7] years, while employee records are retained for [5] years post-termination. Upon the expiration of the retention period, data must be securely deleted. This includes purging electronic files using secure deletion methods and physically destroying paper records through shredding or incineration. Regular audits will ensure compliance with the data retention policy.
Data Retention Schedule | Retention Period |
|---|---|
Financial Records | [7] years after end of fiscal year |
Employee Records | [5] years post-termination |
Customer Data | [5] years after customer relationship ends |
Marketing Materials | Indefinitely, unless deemed obsolete |
V. Incident Response
A. Incident Definition
An incident is any event that threatens the integrity, confidentiality, or availability of information. This includes, but is not limited to, data breaches, unauthorized access, malware infections, and natural disasters. Identifying an incident quickly is crucial in mitigating potential damage and initiating the appropriate response. For example, a phishing attack targeting employees could lead to compromised accounts, requiring immediate action to prevent further unauthorized access.
B. Incident Response Team
An Incident Response Team (IRT) will be established to manage and respond to security incidents. The IRT will comprise representatives from IT, legal, HR, and public relations, ensuring a well-rounded approach to incident management. The team will be responsible for:
Identifying and classifying the incident.
Containing and eradicating the threat.
Assessing the impact and implementing recovery procedures.
Communicating with stakeholders and regulatory bodies if necessary.
C. Incident Reporting Procedures
All employees must report any suspected security incidents immediately to their supervisor or the IT department. A detailed reporting procedure will be provided to ensure consistent communication. Reports should include the nature of the incident, the affected systems, and any actions taken prior to reporting. For example, if an employee receives a suspicious email, they should document the sender, content, and their response before escalating the issue. Failure to report incidents promptly may result in disciplinary action.
D. Post-Incident Review
Following the resolution of any incident, a post-incident review will be conducted to evaluate the response, identify lessons learned, and implement improvements to prevent future occurrences. The review will include:
A detailed timeline of events.
Analysis of the effectiveness of the incident response plan.
Recommendations for policy updates or additional training.
Documentation of the review findings will be maintained for future reference.
VI. Training and Awareness
A. Security Awareness Training
All employees are required to undergo mandatory security awareness training upon hiring and annually thereafter. The training program will cover the following topics:
Recognizing phishing attempts and social engineering tactics.
Safe handling of sensitive information.
Understanding the consequences of non-compliance with security policies.
Familiarization with incident reporting procedures.
B. Specialized Training
Certain roles may require additional training based on specific responsibilities. For example:
IT Staff: Advanced training on incident response and vulnerability assessment tools.
HR Staff: Training on handling sensitive employee information and data privacy regulations.
All Staff: Regular updates on emerging threats and security trends through newsletters or workshops.
C. Training Evaluation
Training effectiveness will be assessed through periodic quizzes and feedback sessions. Employees who fail to complete training or demonstrate inadequate understanding may be subject to remedial training or disciplinary action. For instance, employees will be required to achieve a score of [85]% or higher on assessments to pass the training program. This ensures that the staff is equipped with the necessary knowledge to maintain security protocols.
VII. Compliance and Auditing
A. Compliance Requirements
[Your Company Name] is committed to adhering to all relevant laws, regulations, and industry standards regarding information security. This includes:
GDPR (General Data Protection Regulation) for handling personal data of EU citizens.
HIPAA (Health Insurance Portability and Accountability Act) for protecting health information.
PCI DSS (Payment Card Industry Data Security Standard) for securing payment card information.
B. Internal Audits
Regular internal audits will be conducted to evaluate compliance with the Security Service Policy. Audits will assess the effectiveness of security controls, identify vulnerabilities, and ensure that all employees are following established protocols. Audit results will be reported to the Information Security Committee for review and action. For example, audits will be scheduled semi-annually, focusing on critical areas such as access controls, data handling, and incident response practices.
C. External Audits
Independent third-party audits will be performed annually to validate compliance with security standards and regulations. The audit report will be shared with executive management, and recommendations will be incorporated into the continuous improvement process. These audits provide an objective assessment of our security posture and help identify any gaps that need to be addressed.
VIII. Conclusion
A. Policy Review and Updates
This Security Service Policy will be reviewed and updated at least annually or as needed to address emerging threats, regulatory changes, and technological advancements. Stakeholders will be notified of any significant updates, and training will be provided to ensure compliance. Regular feedback from employees will also be solicited to improve the policy continuously.
B. Policy Acknowledgment
All employees are required to acknowledge their understanding and acceptance of the Security Service Policy upon hiring and during subsequent policy updates. A record of acknowledgment will be maintained by the HR department to ensure compliance. Employees who fail to acknowledge the policy may face disciplinary action, highlighting the importance of understanding and adhering to security measures.