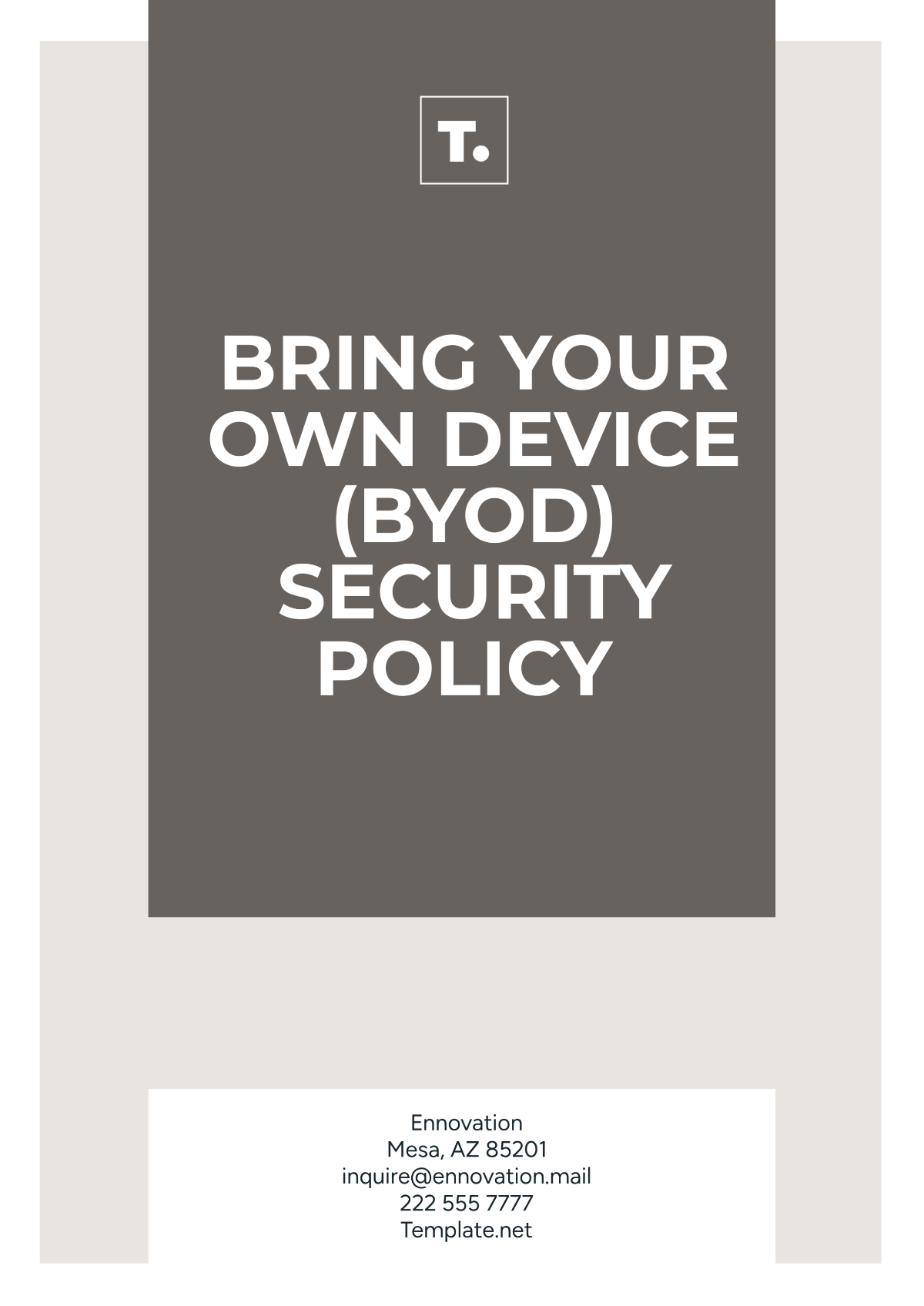
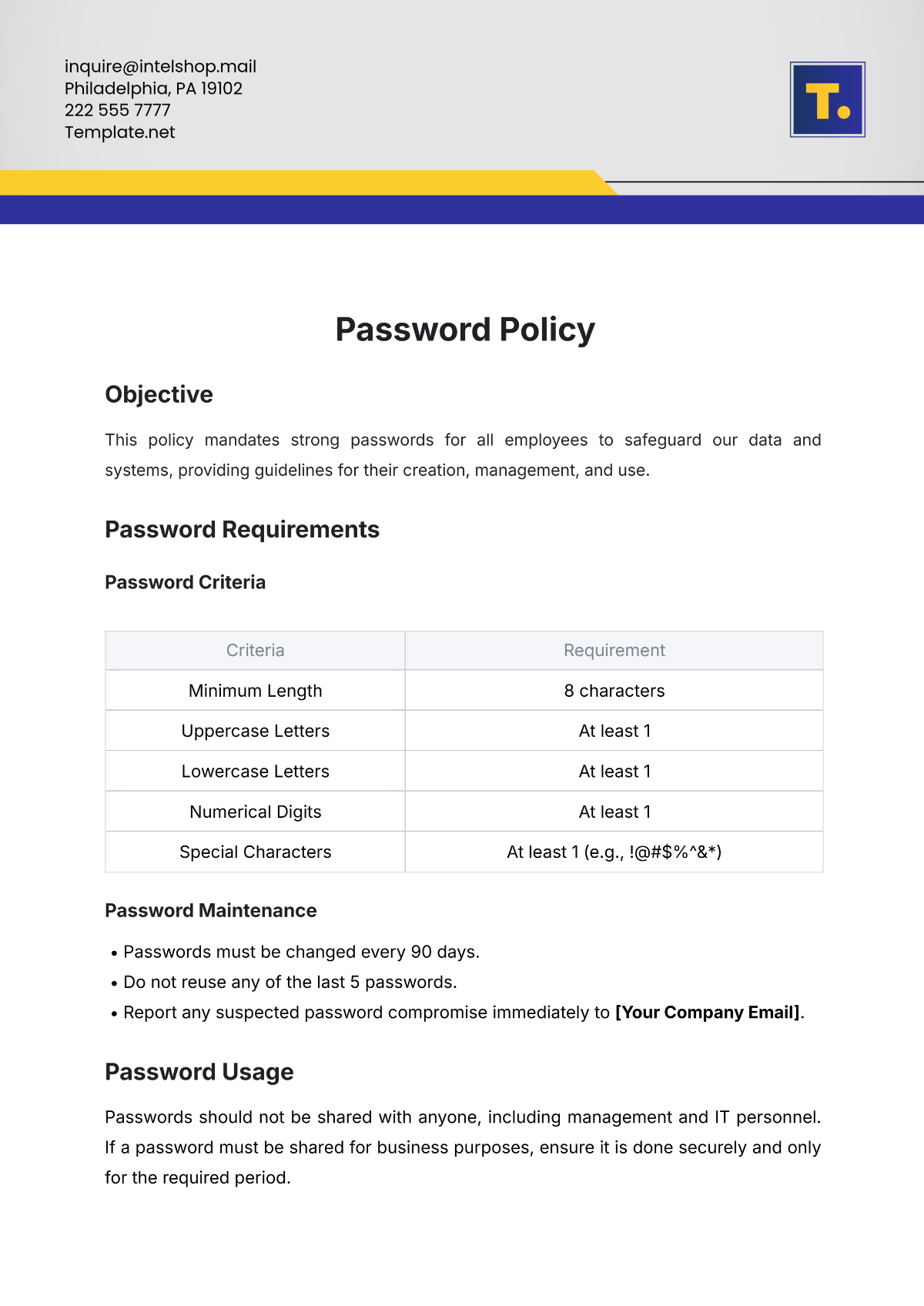
Network Security Policy Format
Effective Date:
The date the policy comes into effect.
Last Reviewed:
The date when the policy was last reviewed or updated.
Approved By:
The name of the authority or committee who approved the policy.
1. Purpose
Guideline: Clearly define the purpose of the policy.
Example: "The purpose of this policy is to ensure the protection of the organization’s network infrastructure, sensitive data, and systems from unauthorized access, breaches, and potential cyber threats. It establishes rules for securing network access, data transmission, and system configuration."
2. Scope
Guideline: Specify who and what is covered by the policy.
Example: "This policy applies to all employees, contractors, and third-party service providers who access the organization's network resources. It encompasses all network devices, infrastructure, and software tools used within the corporate environment."
3. Network Security Responsibilities
Guideline: Detail the roles and responsibilities of each group or individual involved in network security.
Example:
IT Department: "Responsible for the configuration and ongoing maintenance of network security controls, including firewalls, intrusion detection/prevention systems, and VPNs."
Employees: "Must adhere to password management, use encryption where required, and report any suspicious activities."
Network Administrators: "Monitor network traffic, ensure timely software updates, and enforce network security best practices."
4. Security Measures
Guideline: Outline the key security measures to be implemented and their configurations.
Example:
4.1. Firewalls and Intrusion Prevention Systems (IPS): "Deploy firewalls at the network perimeter and internal segmentation points. Use intrusion prevention systems to analyze traffic for malicious behavior."
4.2. Access Control: "Implement Role-Based Access Control (RBAC) to restrict access based on job responsibilities. Ensure multi-factor authentication (MFA) is required for access to sensitive areas."
4.3. Network Segmentation: "Divide the network into segments to limit access between different areas, minimizing the scope of any potential compromise."
4.4. Encryption: "Encrypt sensitive data in transit (e.g., via SSL/TLS) and at rest (e.g., using AES-256) to protect data confidentiality."
5. Monitoring and Logging
Guideline: Emphasize the need for continuous monitoring and logging of network activity to detect security threats.
Example: "Monitor all network traffic for unusual patterns, unauthorized access attempts, and potential vulnerabilities. Store and analyze logs from network devices, servers, and applications for early detection of malicious activity."
6. Incident Response
Guideline: Define the steps to take in the event of a security incident.
Example: "The Incident Response Team (IRT) should be activated immediately in the event of a security breach. The team will follow an established procedure to identify, contain, and mitigate the threat, followed by an incident report for future prevention measures."
7. Remote Access
Guideline: Specify the rules for remote access to the organization’s network.
Example: "Remote access must be granted only via secure VPN connections with multi-factor authentication. Employees working remotely must adhere to the same security protocols as those working on-site."
8. Software Updates and Patch Management
Guideline: Implement a robust system for regular updates and patches.
Example: "All network-connected devices must be kept up-to-date with the latest security patches. Critical patches must be applied within 48 hours of release. A patch management system should be used to automate the process where possible."
9. Training and Awareness
Guideline: Establish a continuous training program to ensure awareness of network security.
Example: "Employees must complete annual security awareness training, which covers topics such as phishing, secure password practices, and data protection. Regular refresher courses should be conducted to keep up with evolving security threats."
10. Enforcement
Guideline: Clearly state the consequences for violating the policy.
Example: "Failure to adhere to the Network Security Policy may result in disciplinary action, up to and including termination of access privileges, employment, or legal action. Serious violations will be reported to the relevant authorities."
11. Review and Updates
Guideline: Ensure the policy is regularly reviewed and updated to reflect new threats and organizational changes.
Example: "This policy will be reviewed annually or sooner if necessary, to accommodate changes in network infrastructure, emerging security threats, or compliance regulations. All updates will be communicated to staff immediately."
12. Approval
Guideline: Confirm the policy's approval by an authorized entity.