Endpoint Security Policy
Prepared By: [Your Name]
Company: [Your Company Name]
1. Purpose
The purpose of this Endpoint Security Policy is to define the security requirements for all endpoints (devices such as laptops, desktops, smartphones, tablets, and any other devices that access company data) to ensure the protection of [Your Company Name]'s network and sensitive data from unauthorized access, misuse, or damage.
2. Scope
This policy applies to all employees, contractors, consultants, temporary workers, and other individuals who have access to [Your Company Name]'s network and endpoints, whether the devices are owned by the company or personal devices used for work (BYOD - Bring Your Own Device).
3. Definitions
Endpoint: Any device that connects to the corporate network (e.g., laptops, smartphones, tablets).
Antivirus: Software used to detect and protect against malicious software (malware) on endpoints.
Encryption: The process of converting data into a secure format that is unreadable without an encryption key.
MFA (Multi-Factor Authentication): A security system that requires more than one method of authentication from independent categories of credentials.
4. Responsibilities
IT Department: The IT department is responsible for implementing, maintaining, and monitoring security measures for all endpoints.
Employees and Users: Users are responsible for adhering to the requirements outlined in this policy to ensure their devices are secure.
5. Security Requirements
5.1 Device Configuration
All endpoints must be configured with the latest version of operating systems, applications, and security patches.
Firewalls and endpoint protection software (e.g., antivirus) must be enabled on all endpoints.
Automatic updates for operating systems and critical software should be enabled where possible.
5.2 Encryption
All endpoints must use full disk encryption to protect data in case of device theft or loss.
Sensitive data (such as passwords, personal data, and financial information) must be encrypted during transmission and at rest.
5.3 Access Control
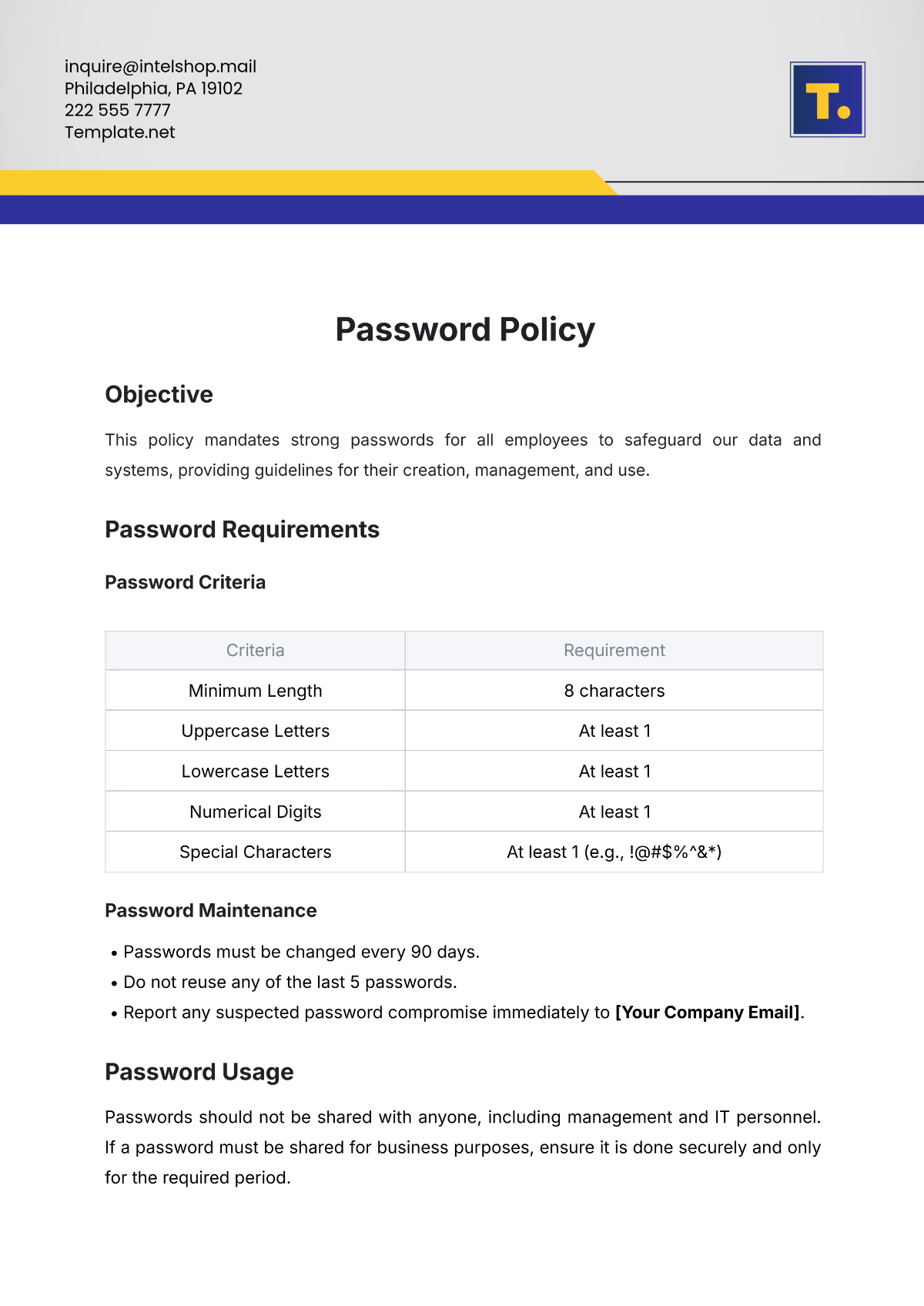
Strong, unique passwords must be used for each endpoint device, and password complexity requirements should be enforced (e.g., minimum length, special characters).
Multi-factor authentication (MFA) must be enabled to access company systems remotely.
5.4 Antivirus and Endpoint Protection
Endpoint devices must have up-to-date antivirus software installed and configured to scan for malware automatically.
Antivirus software should include the ability to detect and block viruses, spyware, ransomware, and other forms of malware.
5.5 Remote Access
Remote access to the company network should be limited to approved VPNs (Virtual Private Networks) or remote desktop solutions.
All remote connections should use encrypted channels to ensure data confidentiality and integrity.
5.6 Mobile Devices
Mobile devices used for work must be secured with a PIN or password and require automatic locking after inactivity.
Mobile device management (MDM) solutions must be used to enforce security policies on smartphones and tablets.
Devices that are lost or stolen should be reported immediately, and remote wipe capabilities should be enabled.
5.7 Data Protection
Sensitive and personal data should not be stored on endpoint devices unless necessary. If stored, it must be encrypted.
Endpoints must be configured to back up important data regularly to prevent data loss.
6. Monitoring and Reporting
All endpoint devices may be subject to monitoring for compliance with security policies.
Any suspicious activities or security incidents must be reported immediately to the IT department for investigation.
7. Compliance
Failure to comply with this Endpoint Security Policy may result in disciplinary action, including termination, and legal consequences where applicable.
8. Review and Updates
This policy will be reviewed annually and updated as needed to address new threats, vulnerabilities, or regulatory requirements.
Acknowledgment
I have read and understood the [Company Name] Endpoint Security Policy and agree to comply with all guidelines and practices outlined within.
Signature: ____________________________
Name: ________________________________
Date: ________________________________