Third-Party Vendor Security Policy
Prepare by: [Your Name]
Company: [Your Company Name]
1. Objective
The purpose of this policy is to guarantee that every third-party vendor involved in managing our organization's data adheres to our established security standards. By doing so, we seek to safeguard sensitive information and uphold the integrity of our systems.
2. Scope
This policy applies to every third-party vendor that accesses the data or systems of our organization. It encompasses external contractors, service providers, as well as business partners.
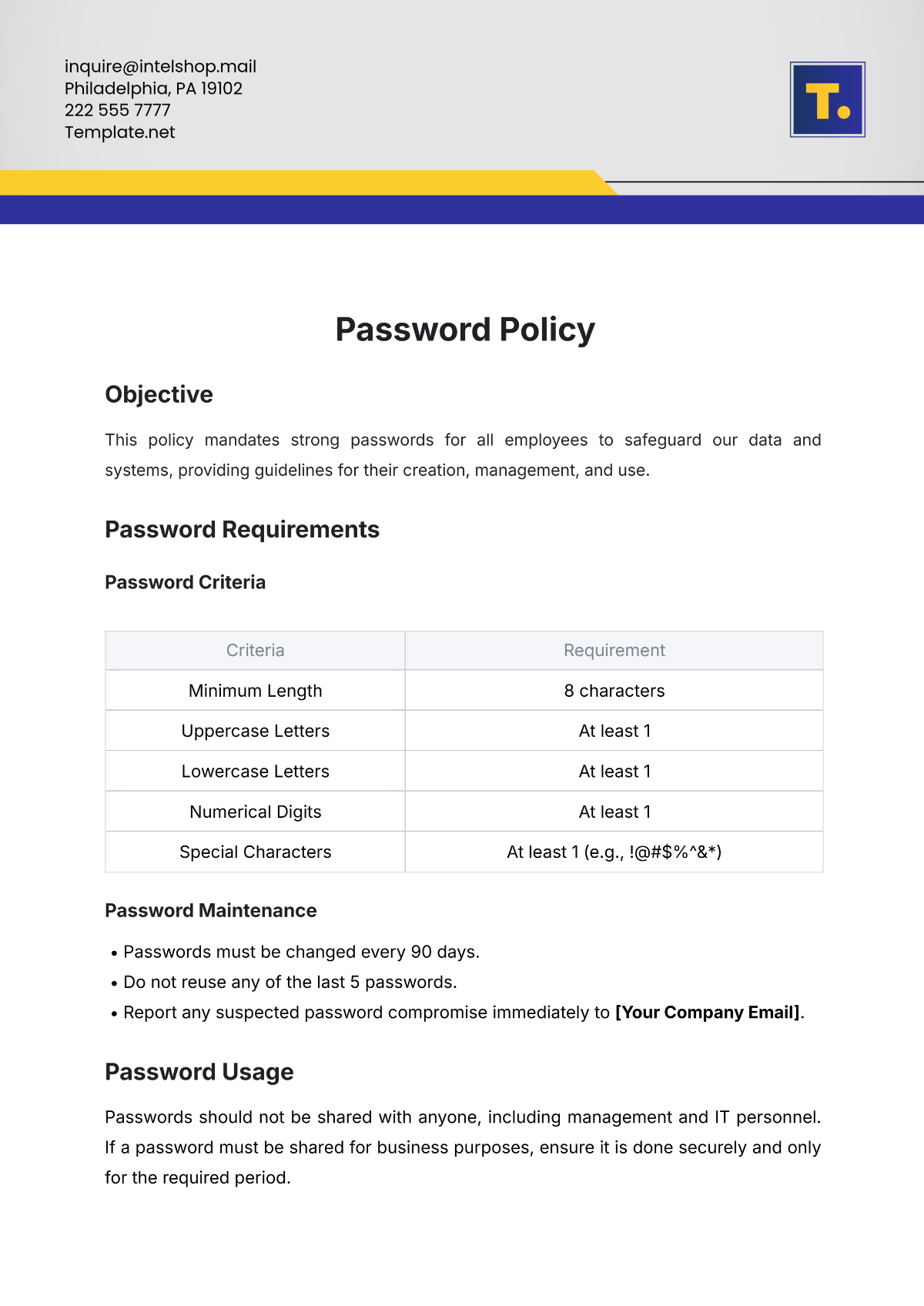
3. Security Requirements
A. Data Protection
Vendors must implement adequate encryption methods for transmitting and storing data.
Access controls must be in place to ensure that only authorized personnel have access to our data.
Data must be backed up regularly with secure and encrypted storage solutions.
B. Access Management
Vendors will use unique user accounts for all staff accessing our systems.
Multi-factor authentication must be implemented wherever possible.
Access logs must be maintained and reviewed periodically for any unauthorized access.
C. Incident Response
Vendors must notify us promptly of any security breach affecting our data.
There should be a clear incident response plan outlining the steps to follow in a security incident.
Vendors should conduct investigation and remediation of security incidents as per the agreed timelines.
D. Compliance Monitoring
Vendors will undergo periodic security assessments and audits to verify compliance with this policy.
Compliance status should be reported to our organization quarterly.
All identified security gaps must be addressed within 30 days of discovery.
4. Terms and Conditions
All third-party vendors must adhere to this security policy and align with our organization’s security standards as outlined in the contract agreements. Non-compliance may result in termination of the contract and potential legal actions.
5. Responsibilities
Role | Responsibilities |
|---|---|
Vendor | Ensure compliance with security policies and implement the necessary measures. |
IT Security Team | Provide vendors with guidelines and support, and monitor compliance. |
Risk Management Department | Conduct periodic risk assessments and reports to leadership. |
6. Review and Updates
This policy will be reviewed annually and updated as necessary to ensure continuous improvement in our third-party vendor security measures.
Approved by:
 [Your Name]
[Your Name]
Chief Security Officer (CSO)