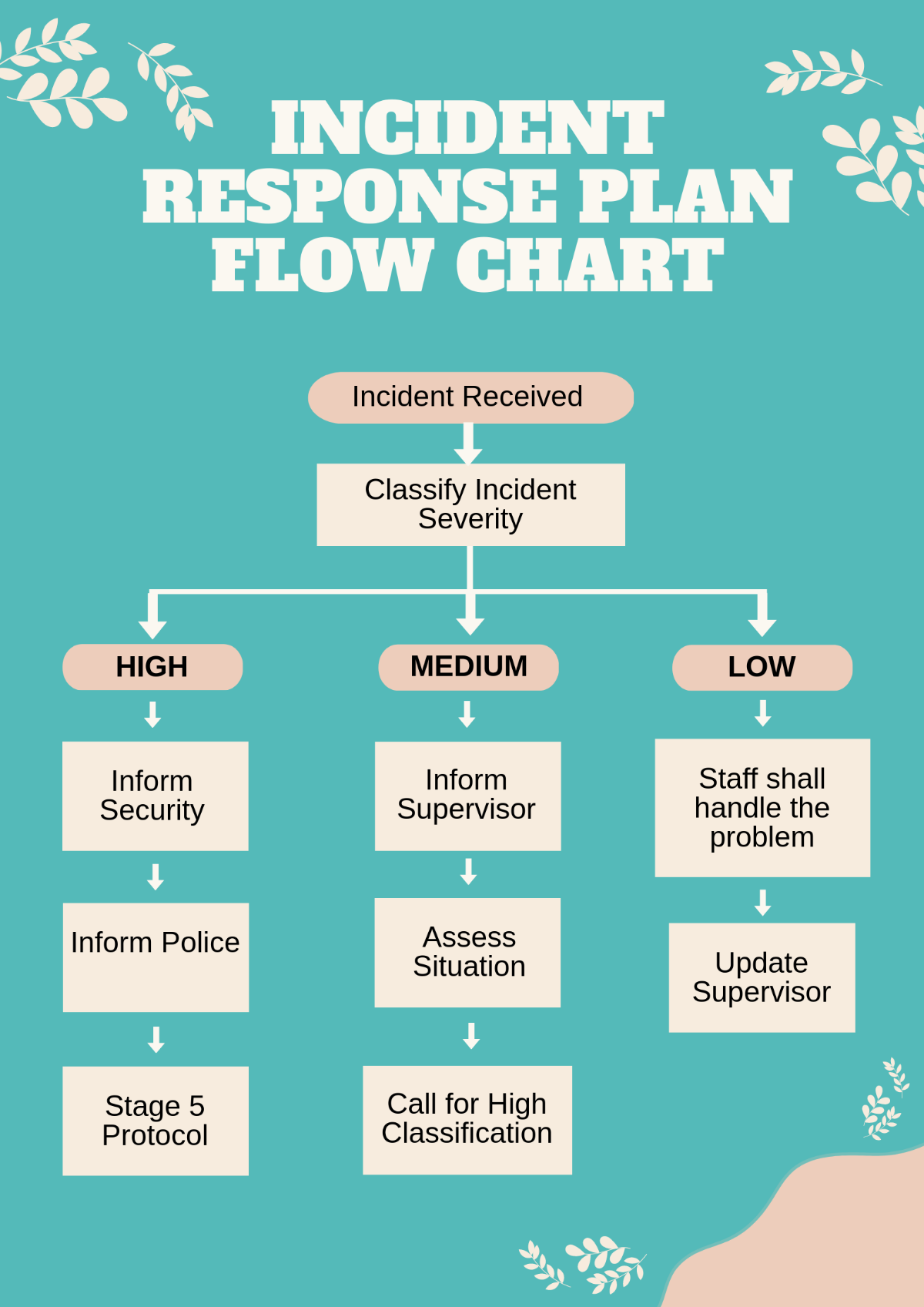
INCIDENT RESPONSE PLAN
This Incident Response Plan (IRP) is developed to provide structured guidance on handling security incidents within [Your Company Name]. The purpose of this document is to outline procedures for detecting, responding to, and recovering from information security incidents to minimize impact and ensure swift restoration of services.
I. Introduction
The IRP is essential for maintaining the integrity, confidentiality, and availability of information assets. It ensures a coordinated response to security incidents, aiming to minimize damage and recover operations as quickly as possible.
A. Purpose
The purpose of the Incident Response Plan is to:
Provide an organized approach for responding to and managing incidents.
Protect and preserve evidence for potential legal or disciplinary action.
Ensure compliance with regulatory and legal obligations.
B. Scope
This plan applies to all staff, systems, and networks owned or operated by .
II. Team Structure
The Incident Response Team (IRT) is responsible for managing the IRP activities.
A. Roles and Responsibilities
Team Leader: Oversees the incident response process, ensures communication, and coordinates with external parties.
IT Security Manager: Leads technical response activities, analyzes incidents, and implements containment strategies.
Legal Advisor: Consults on legal implications and ensures regulatory compliance.
Communications Officer: Manages external and internal communications.
B. Contact Information
Contact | Role | Phone | |
|---|---|---|---|
[Your Name] | Team Leader | [Your Email] | [Your Company Number] |
III. Incident Response Phases
The incident response process is divided into phases to ensure a comprehensive approach to handling incidents.
A. Preparation
Develop and update the Incident Response Plan regularly.
Conduct training sessions for the Incident Response Team.
Establish communication protocols.
B. Detection and Analysis
Monitor networks and systems for signs of incidents.
Analyze alerts and security data to identify potential incidents.
Confirm the occurrence, scope, and nature of the incident.
C. Containment, Eradication, and Recovery
Implement measures to contain the spread of the incident.
Locate and eradicate the root cause.
Restore systems to normal operations.
D. Post-Incident Activity
Conduct a post-incident review to assess response effectiveness.
Document findings and lessons learned.
IV. Communication Plan
Communication is crucial during and after an incident. This section outlines how to effectively communicate with stakeholders.
A. Internal Communication
Notify team members and relevant departments promptly.
Provide regular updates regarding the incident status.
B. External Communication
Engage with affected customers and partners through [Company Email] and [Company Website].
Utilize [Company Social Media] for public announcements, if necessary.
V. Conclusion
By adhering to the structured framework outlined in this Incident Response Plan, can effectively manage and mitigate the impact of information security incidents, ensuring the continued protection of company assets and data.