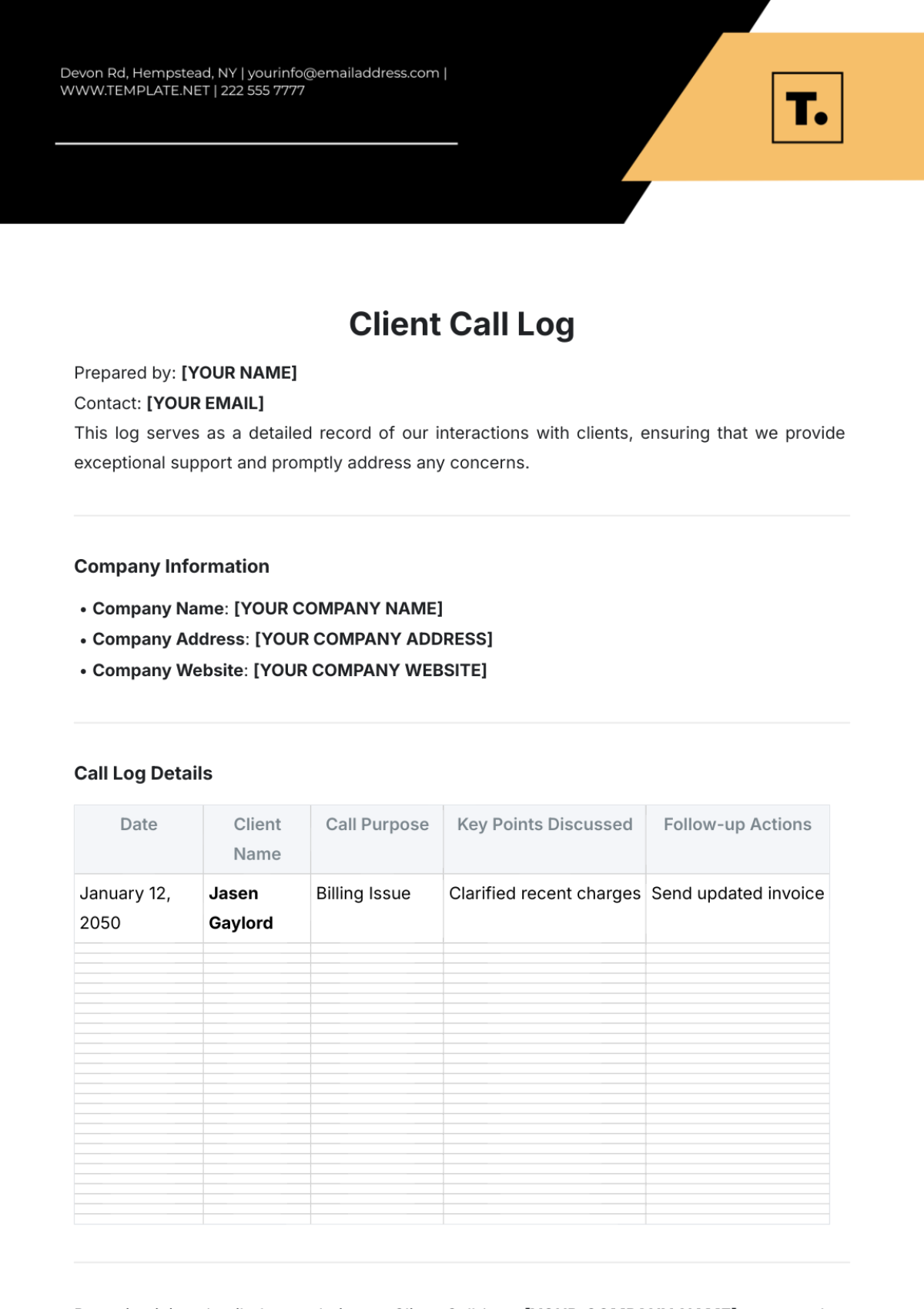
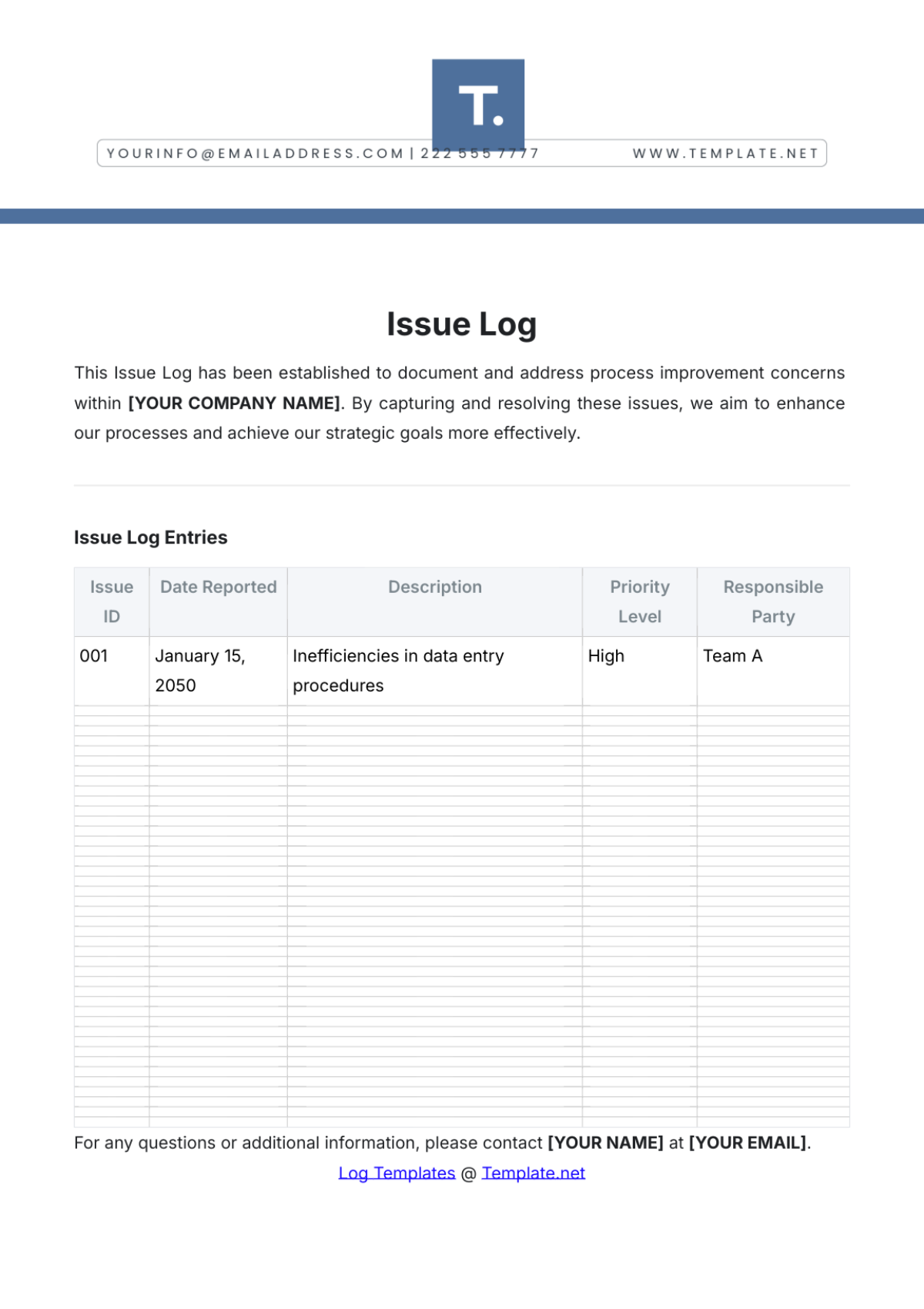
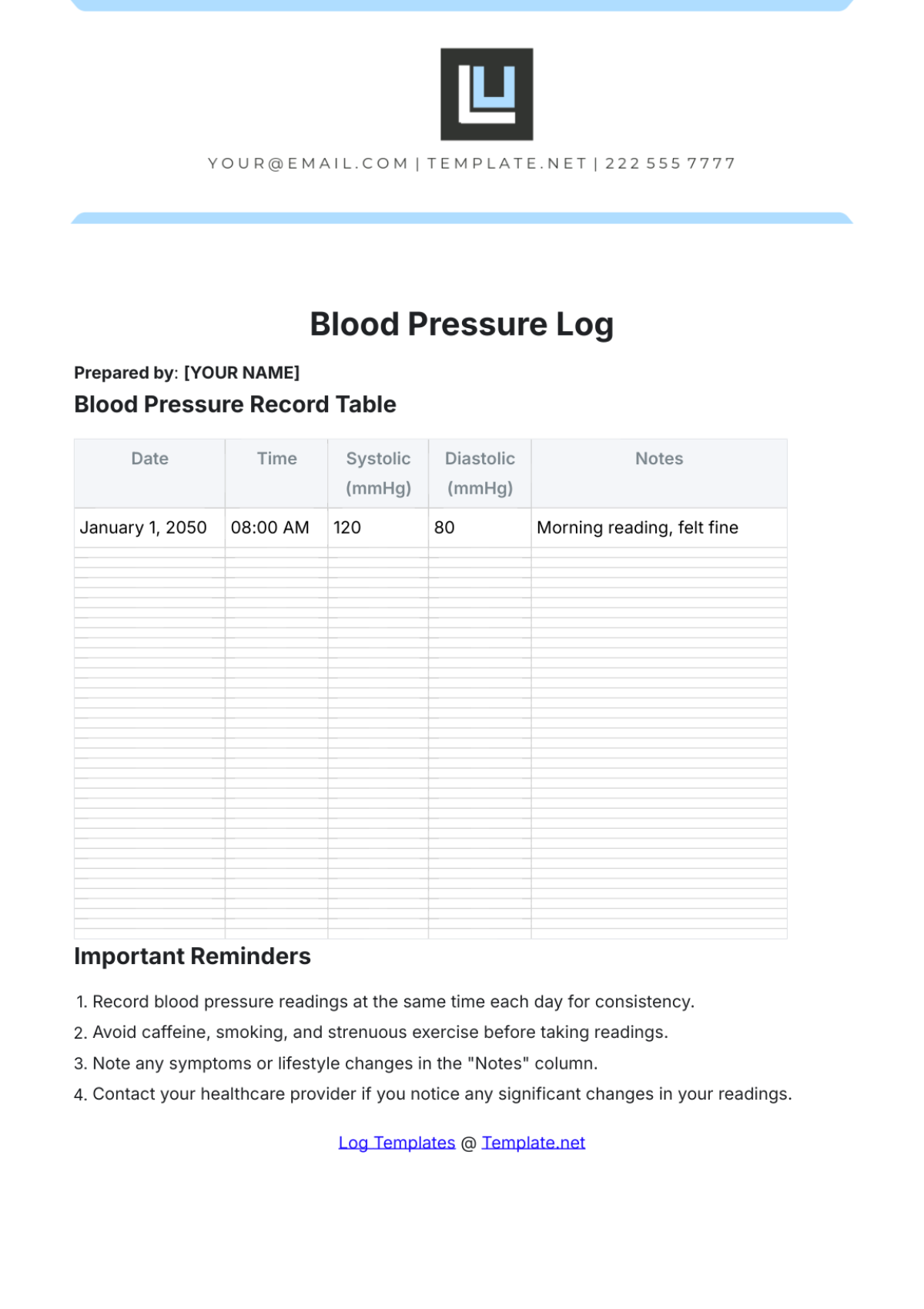
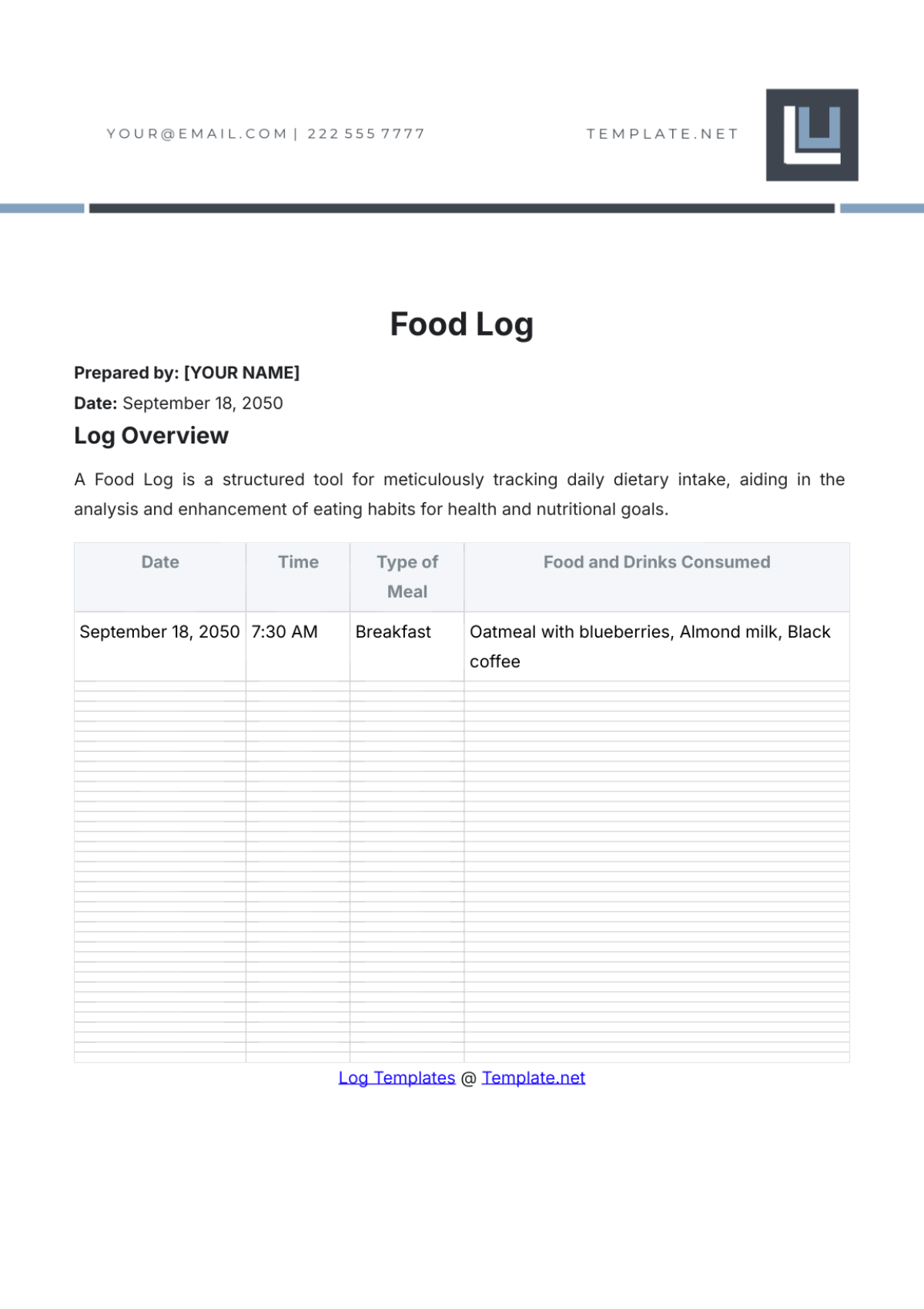
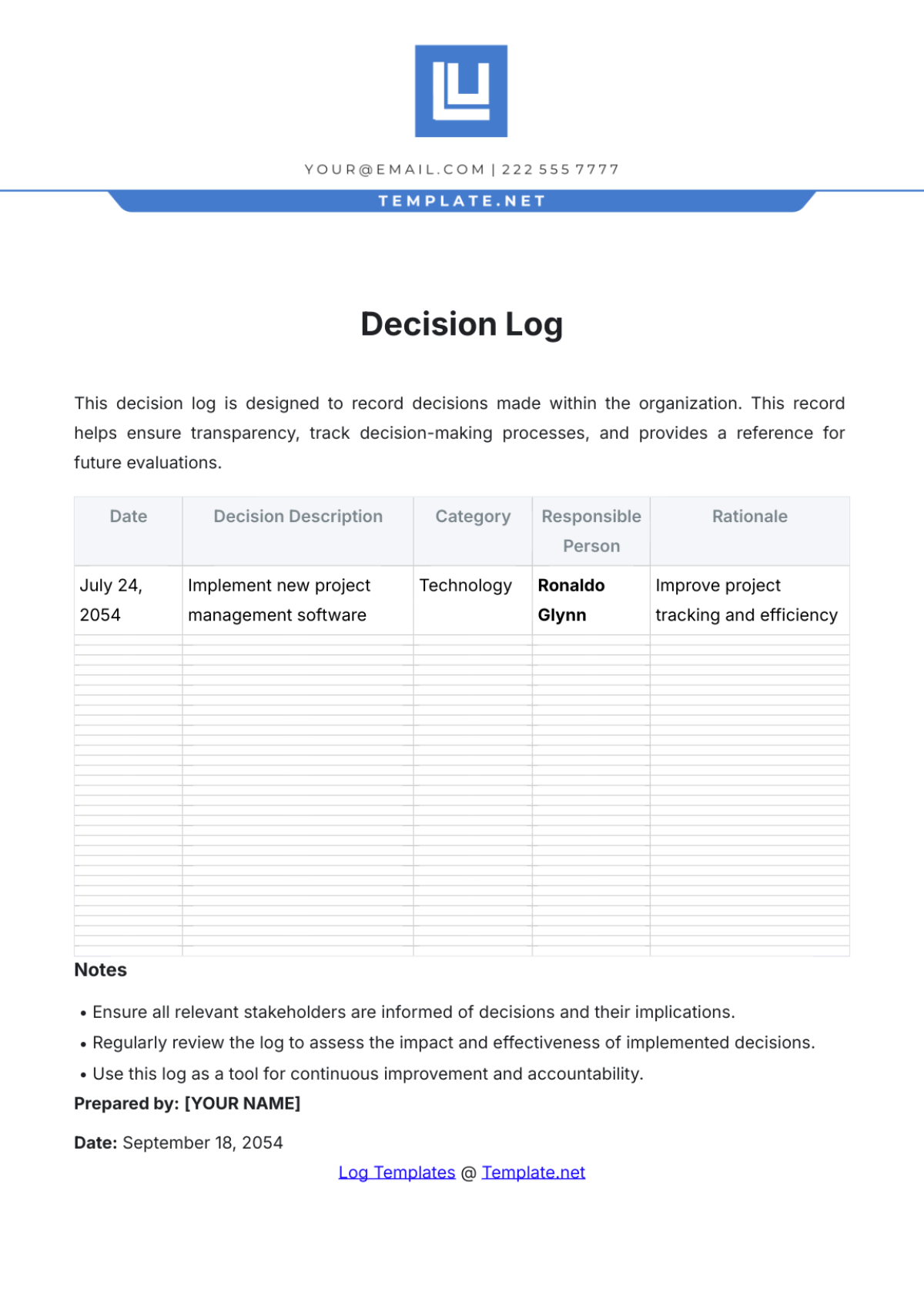
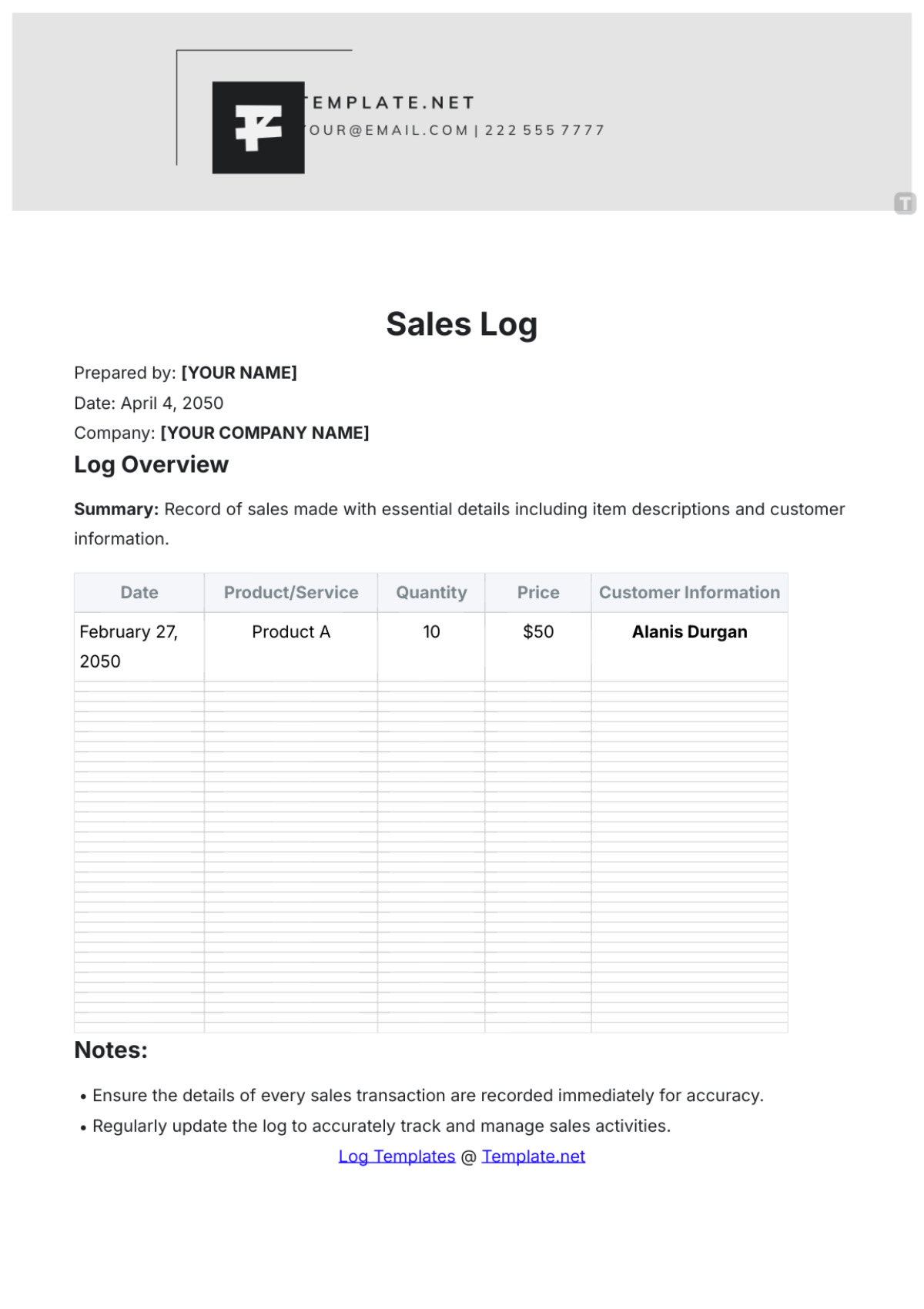
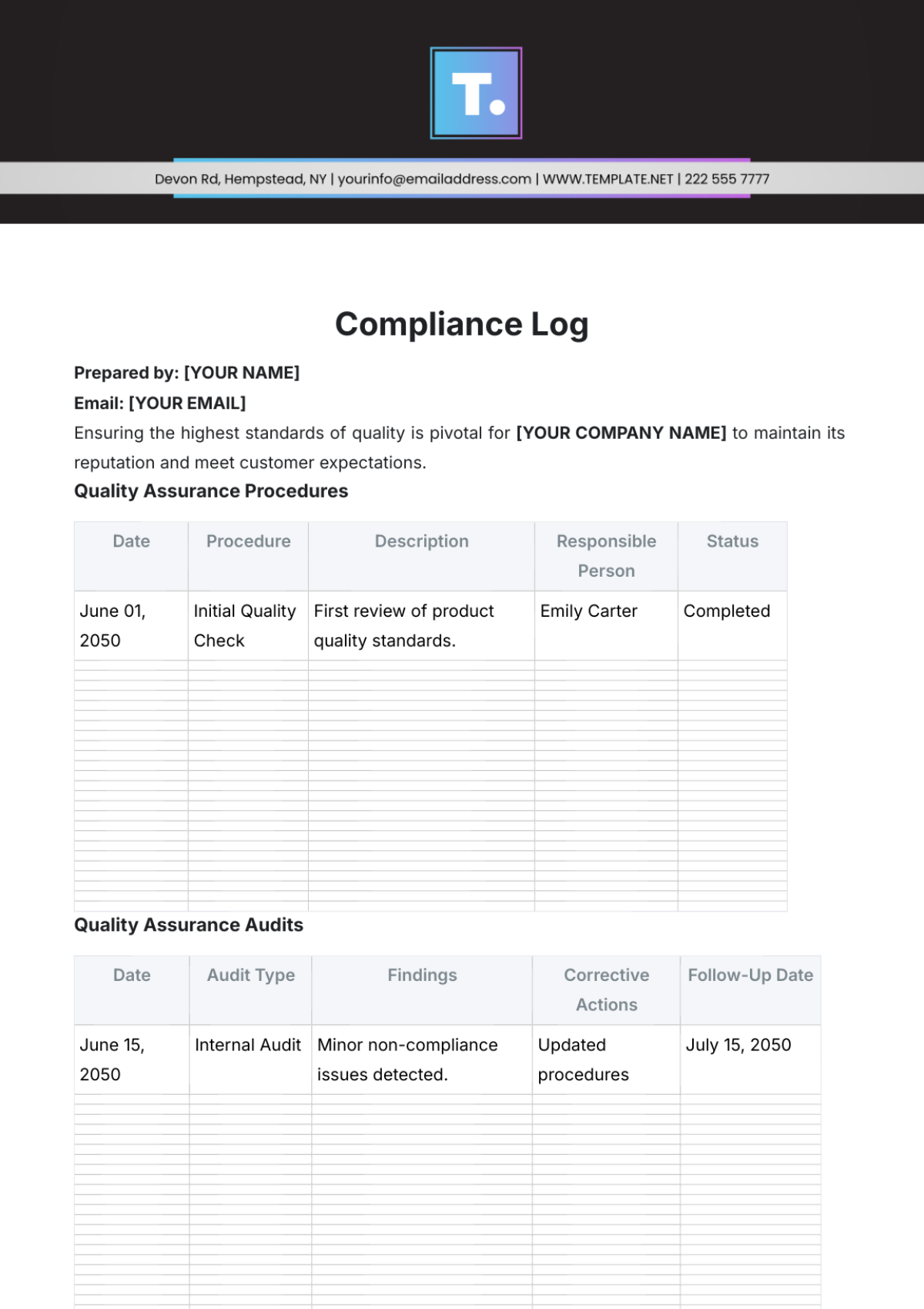
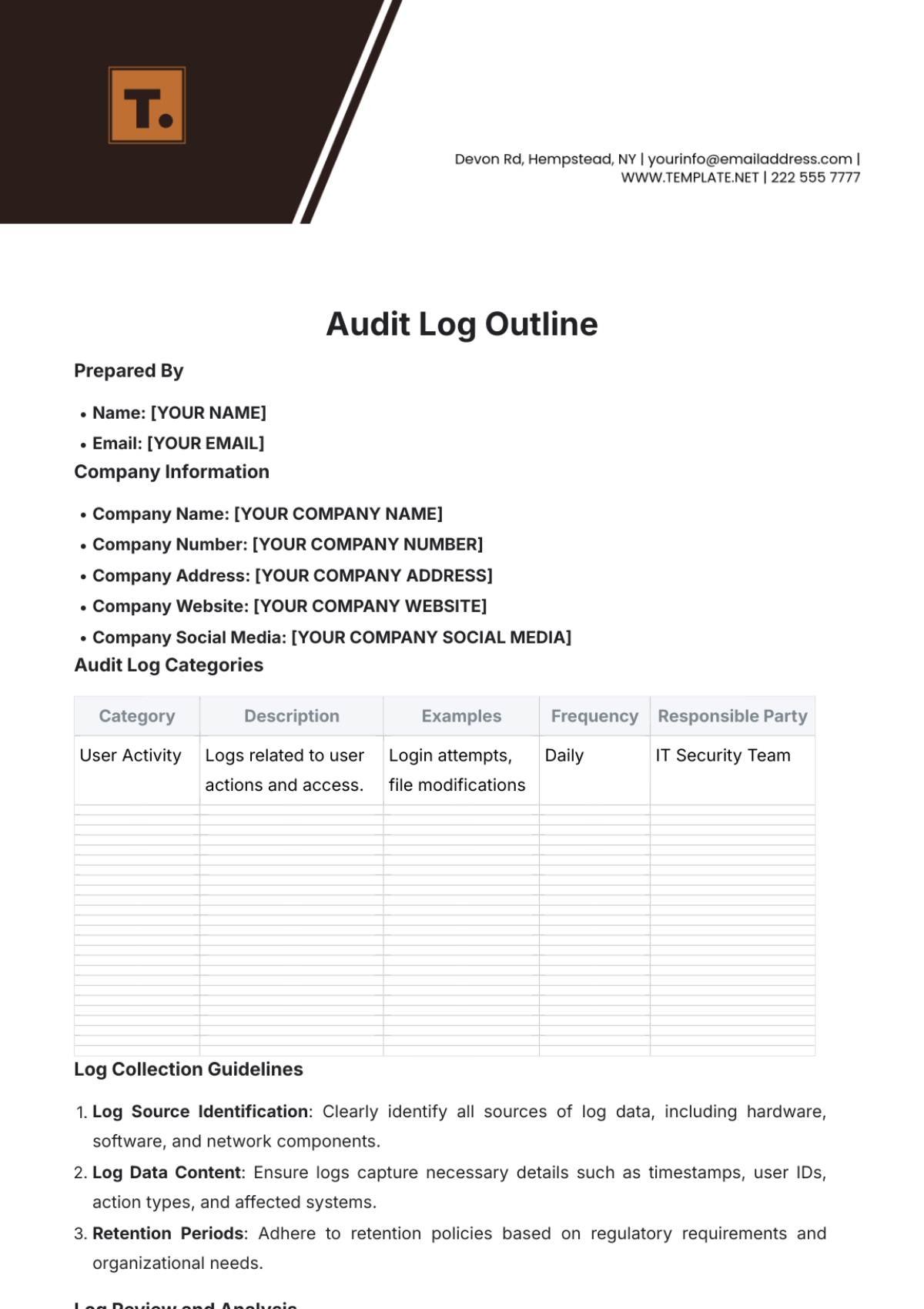
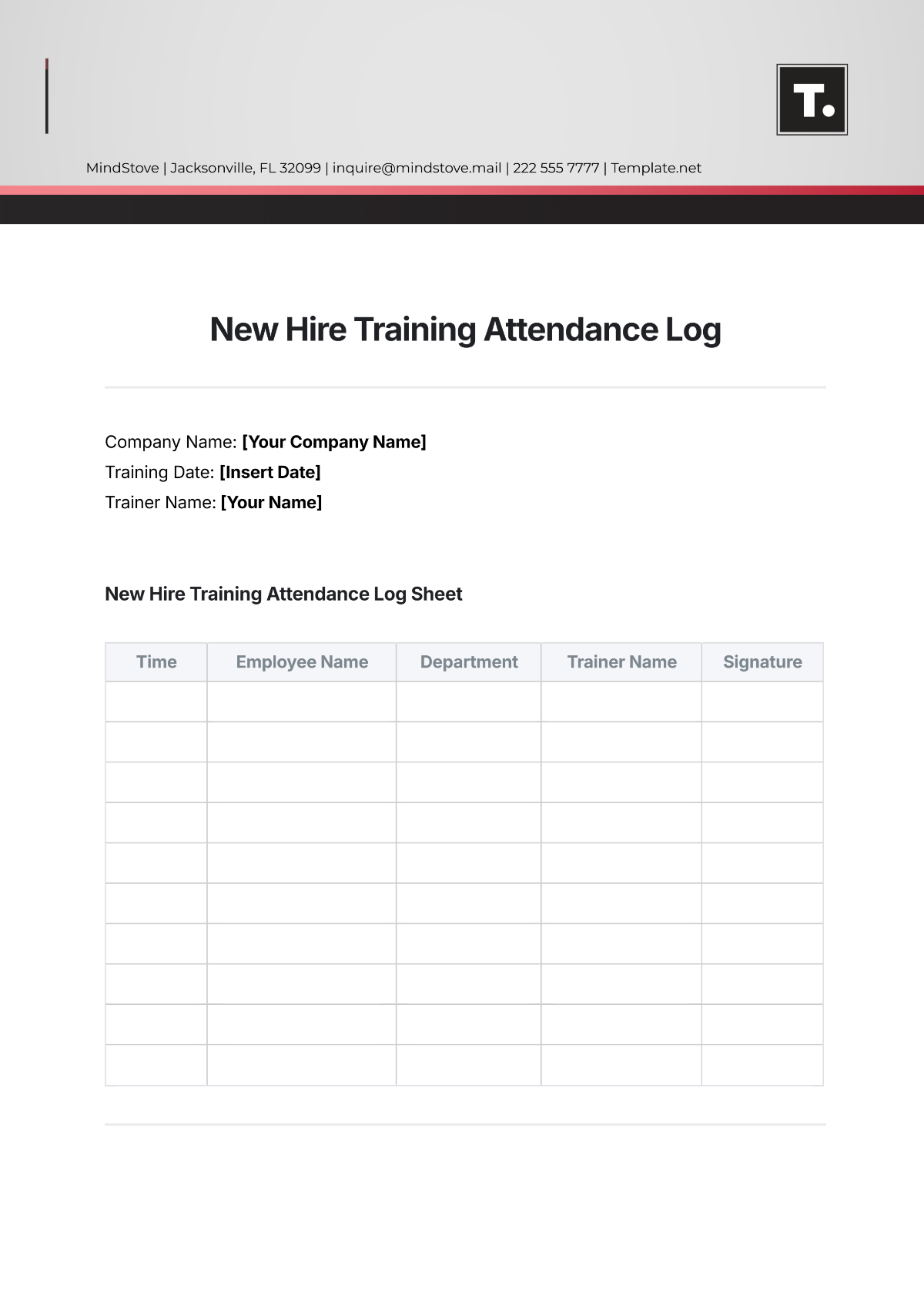
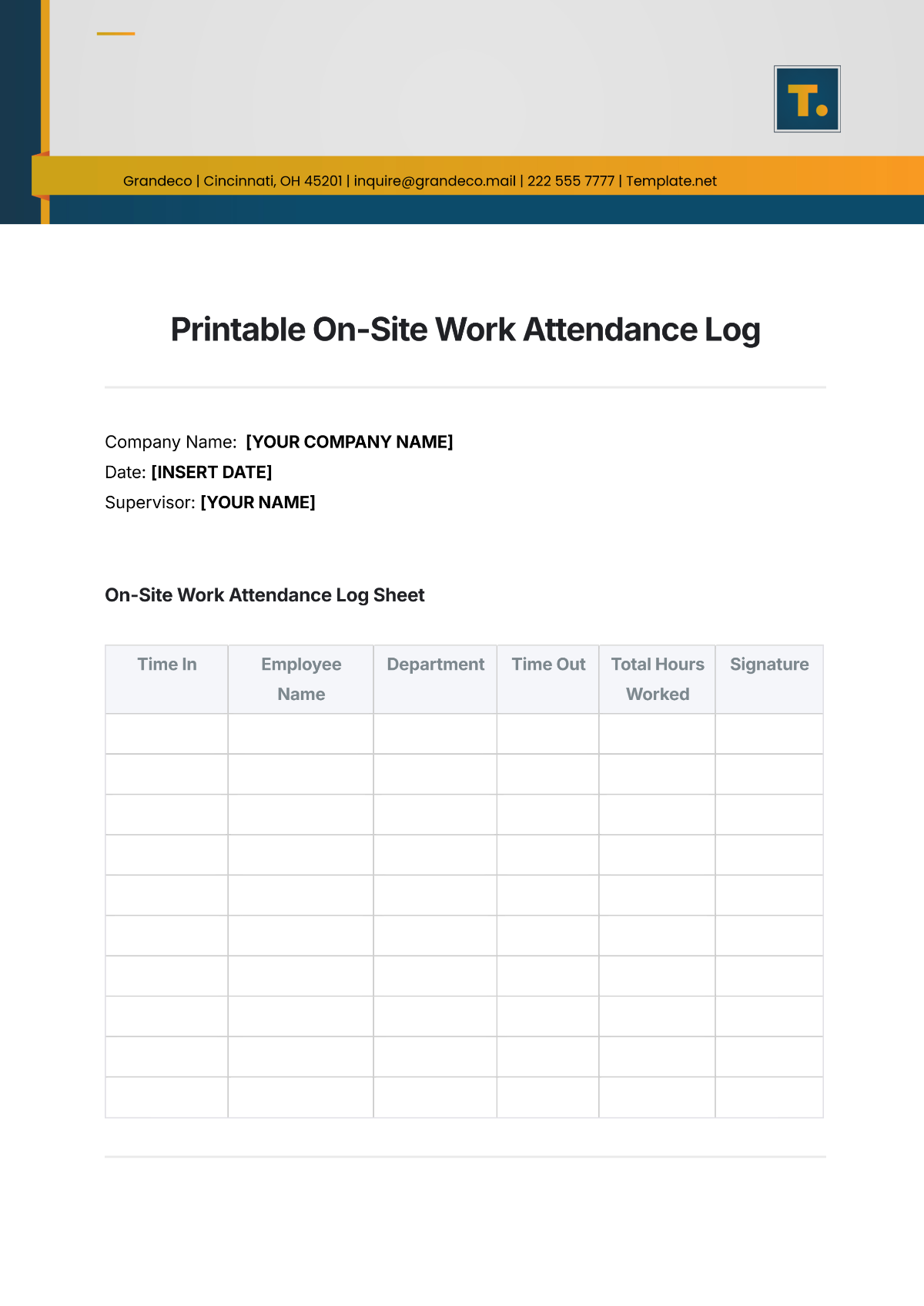
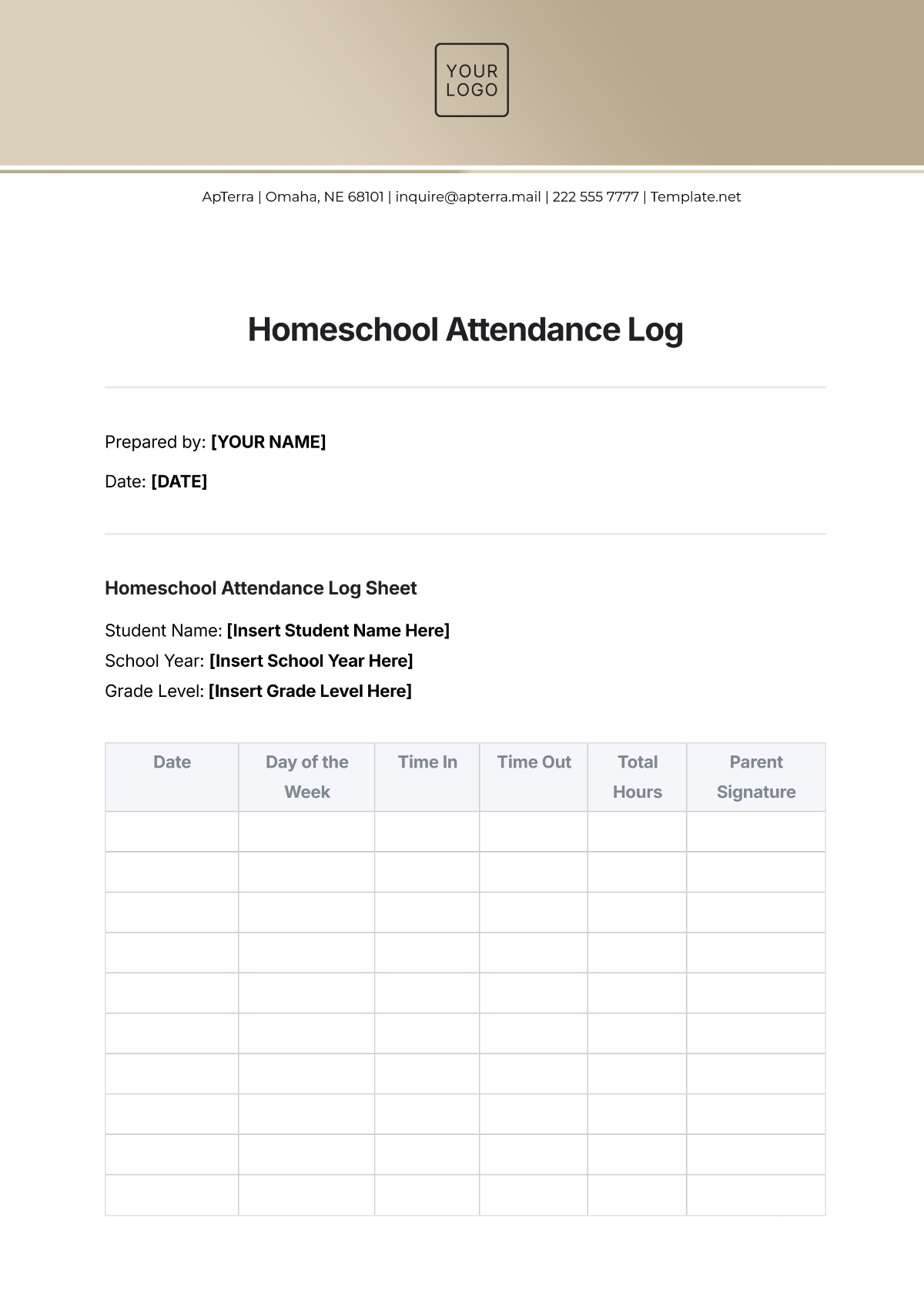
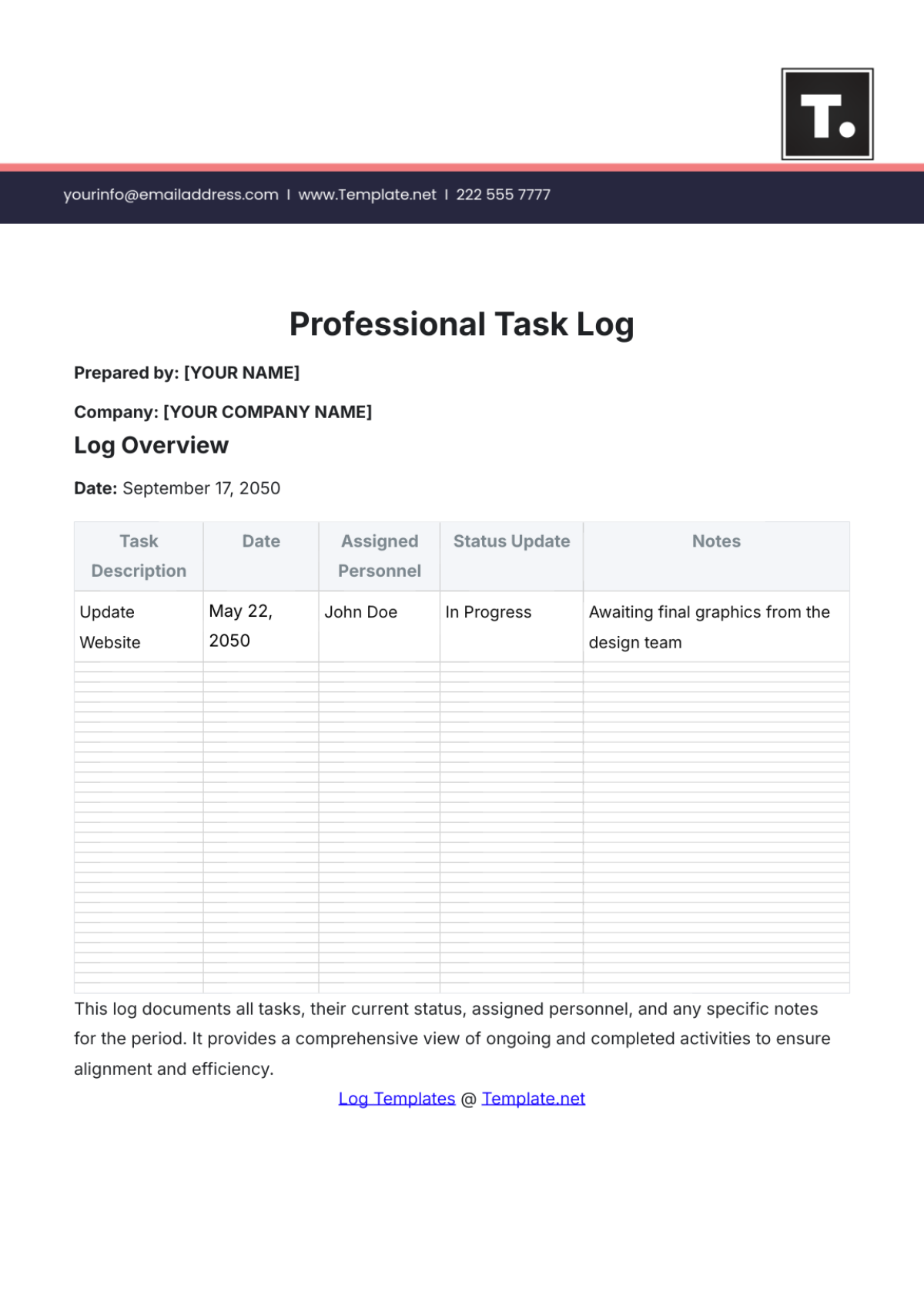
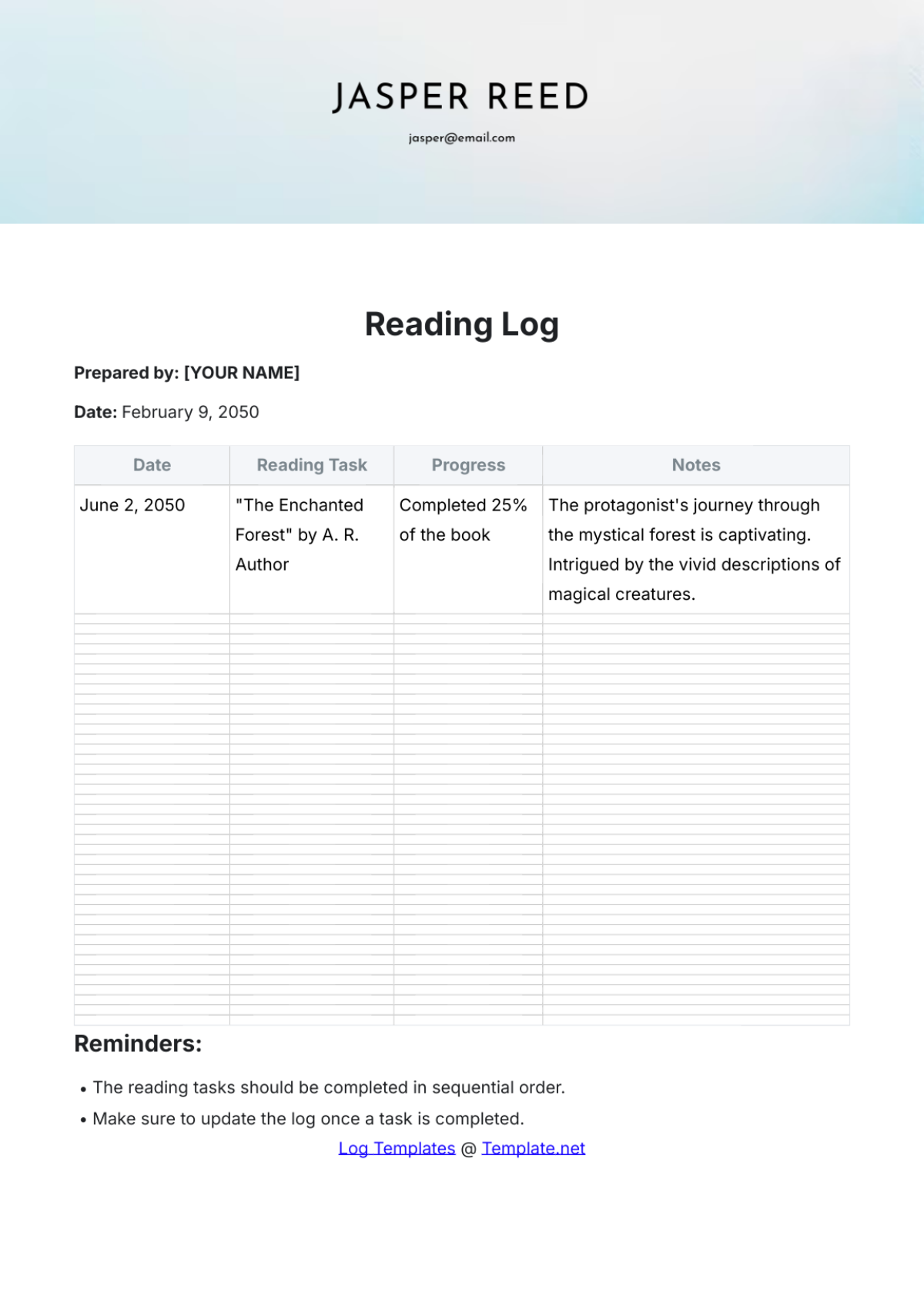
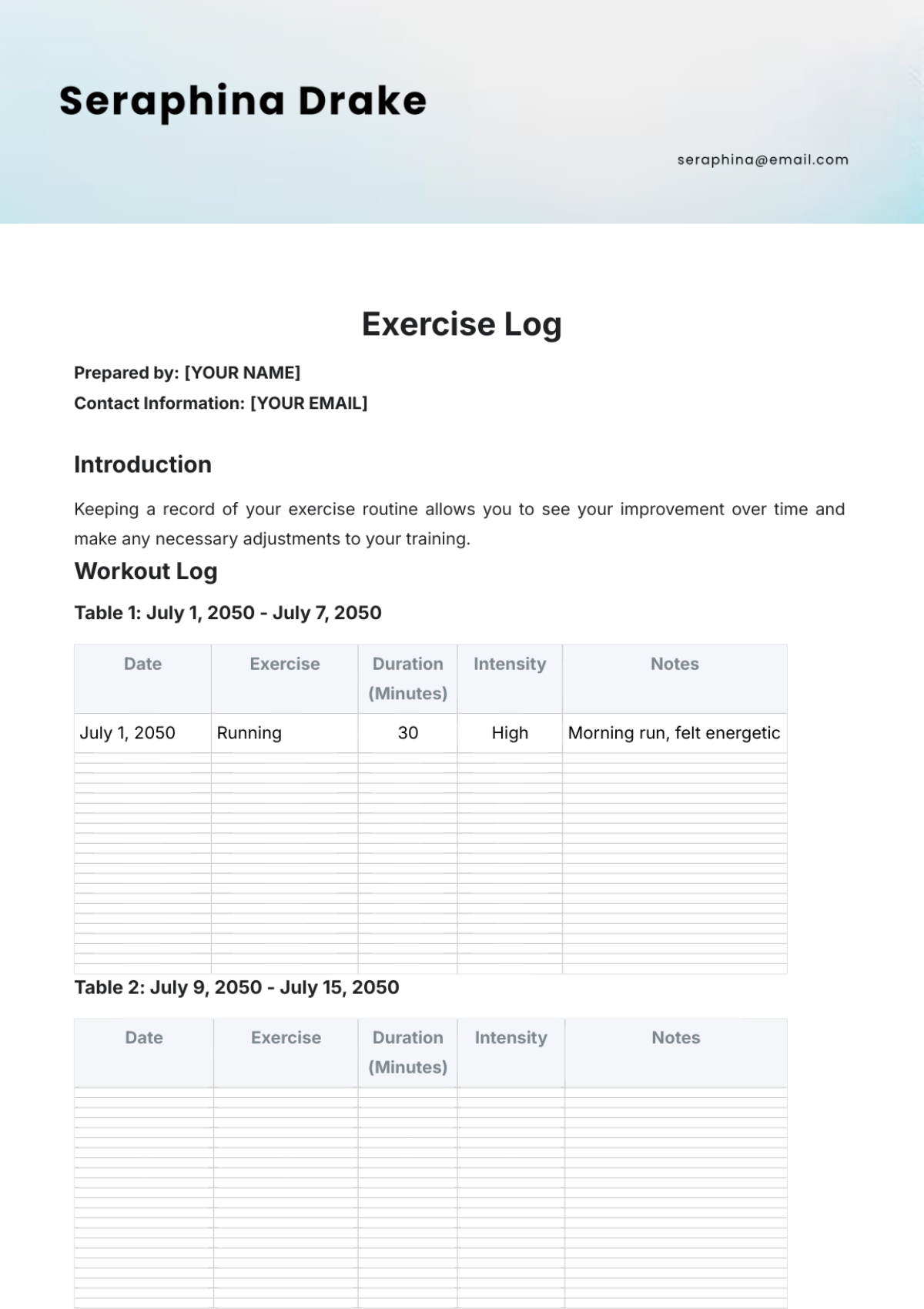
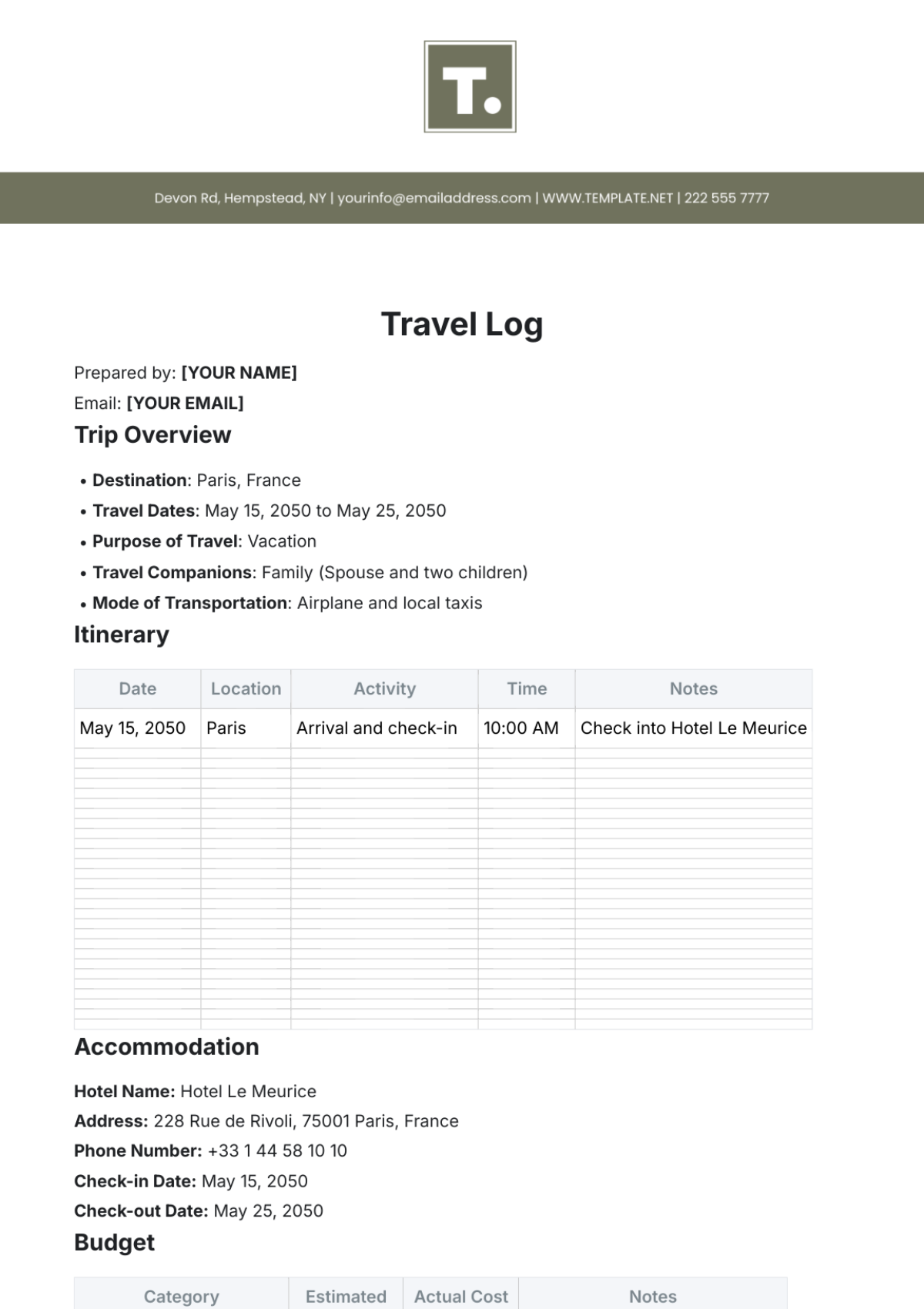
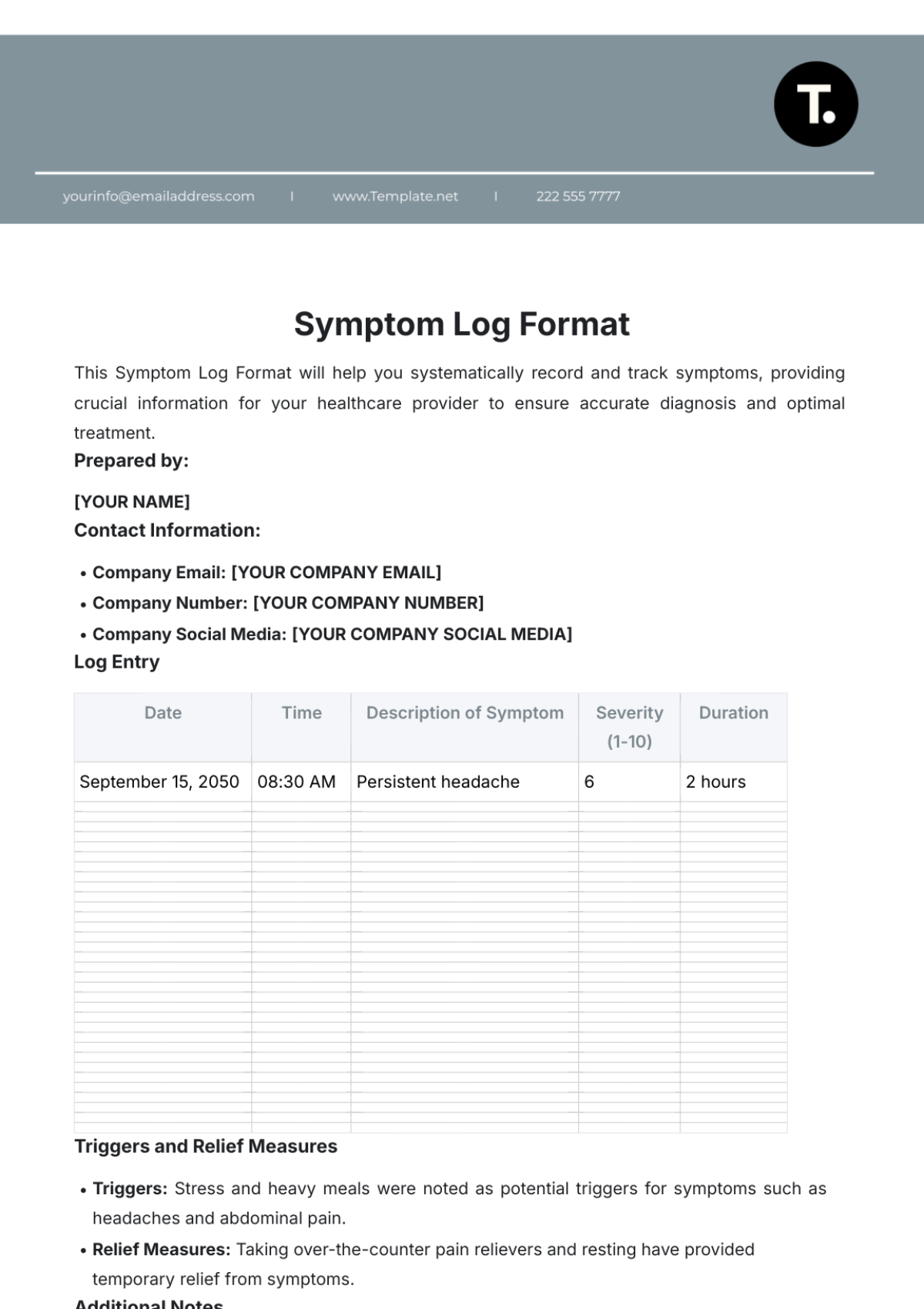
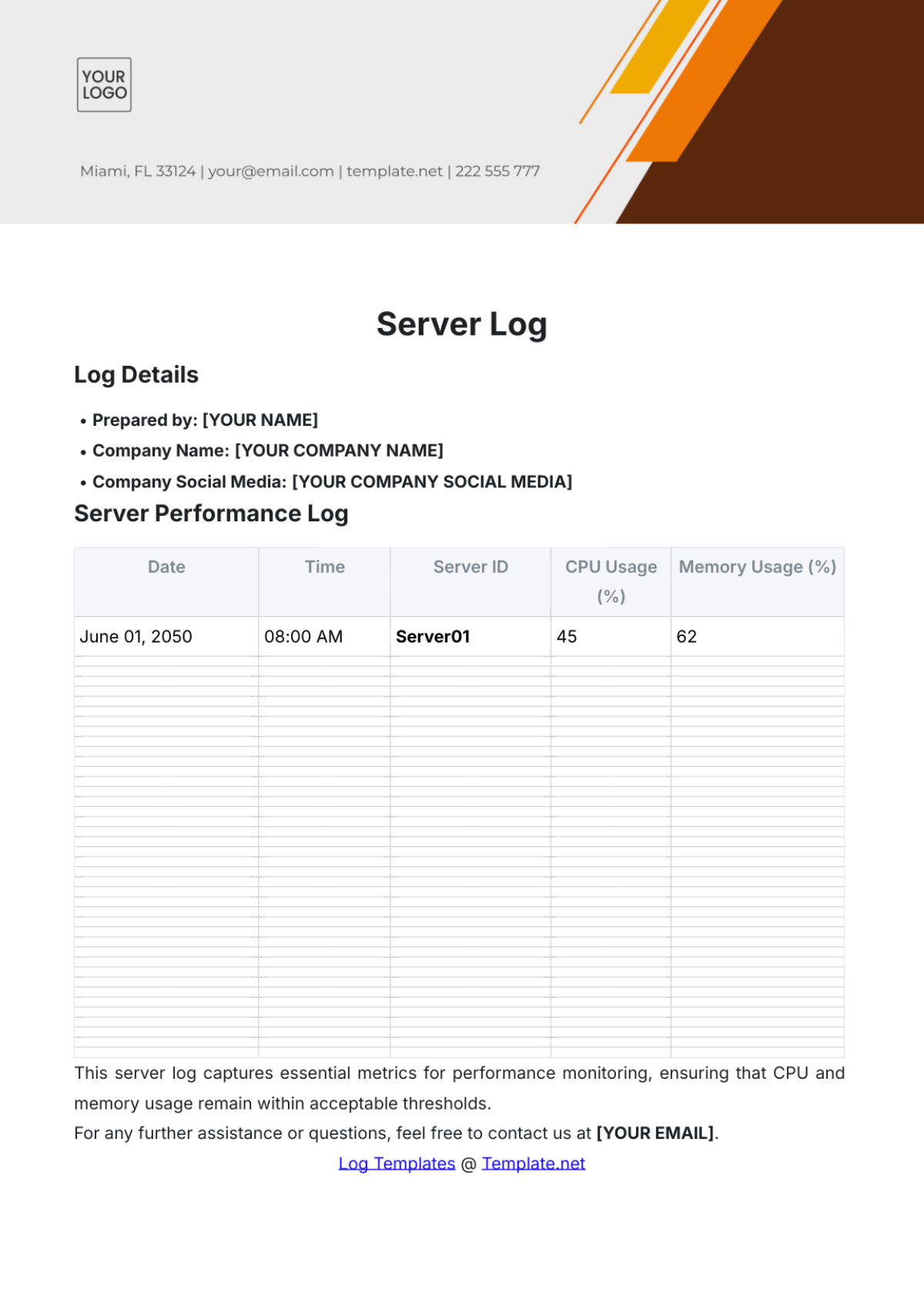
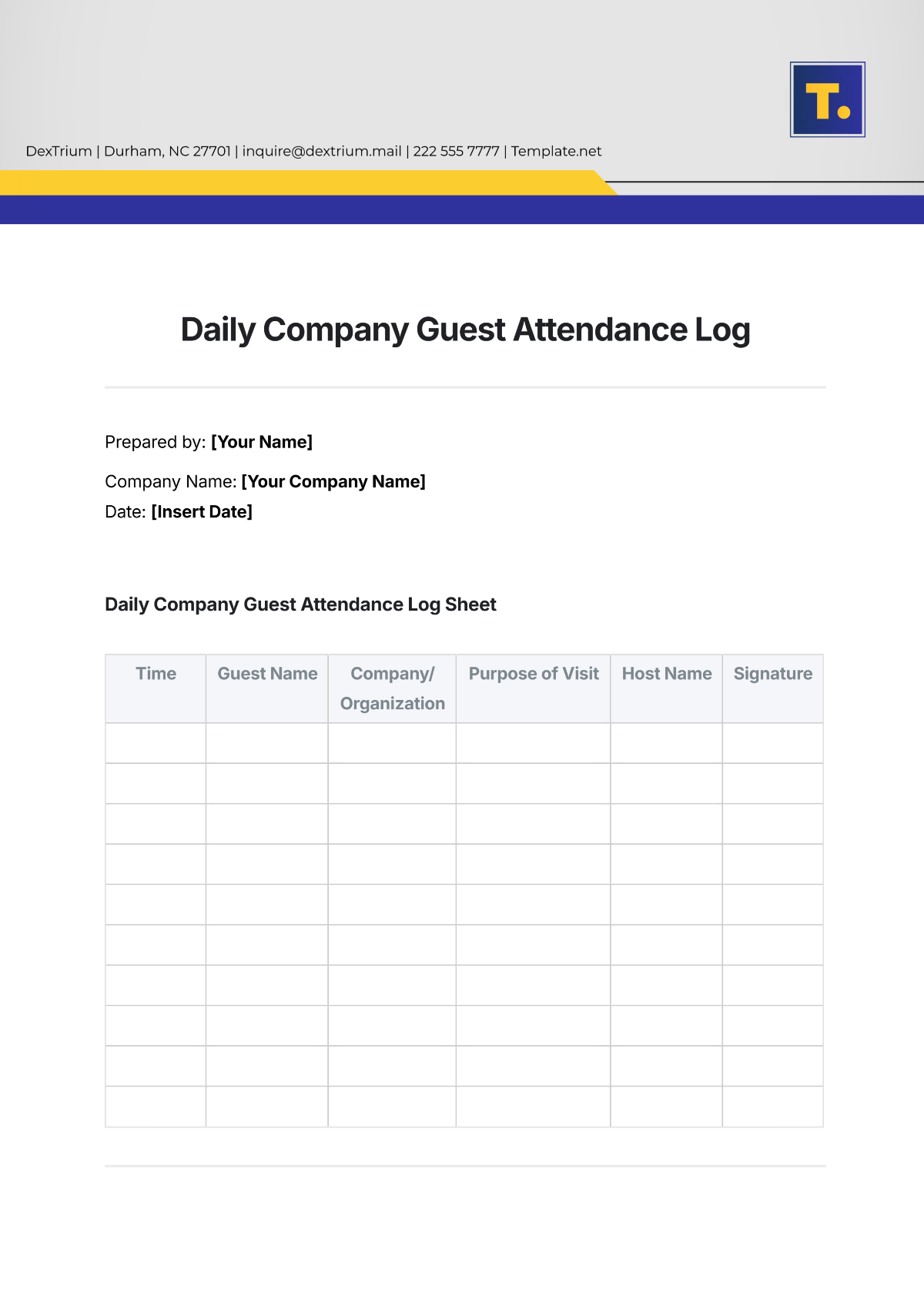
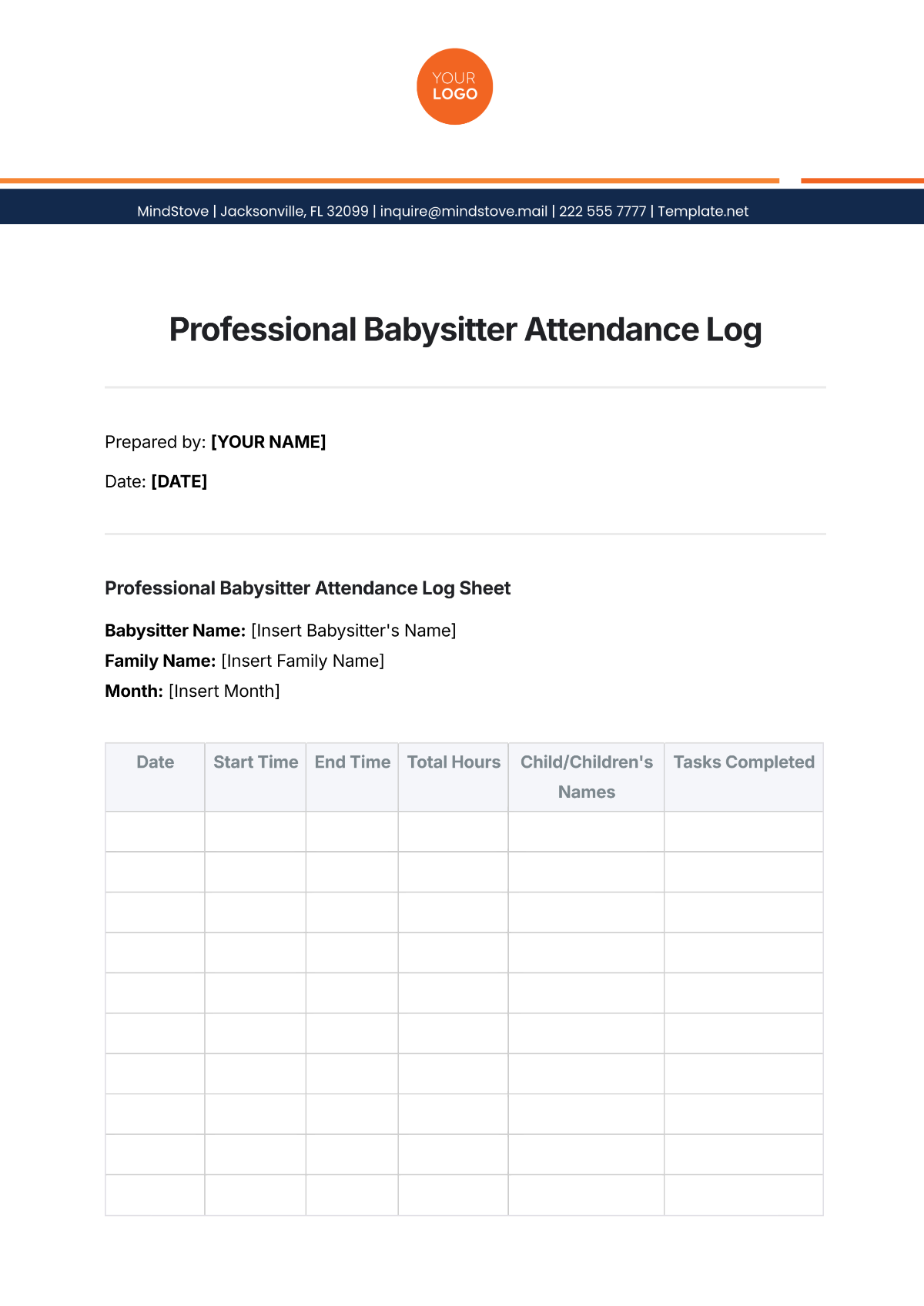
Key Log
The Key Log is designed to keep a comprehensive record of access to secured areas by documenting who has been issued keys and when. This log enhances security measures, helps in identifying any unauthorized access, and ensures accountability for the distribution and usage of keys within a specified environment.
Prepared by: [YOUR NAME]
Date: March 2, 2050
Company: [YOUR COMPANY NAME]
Name | Time In | Time Out | Location | Signature |
|---|---|---|---|---|
John Doe | 9:00 am | 10:00 am | Conference 1 | [Date Signed] |
Mary Peter | 11:00 am | 12:00 am | Conference 2 | [Date Signed] |
James Sullivan | 3:00 pm | 5:00 pm | Conference 3 | [Date Signed] |
Notes/Reminders:
Ensure to update the log regularly
Maintain the log for accurate task management