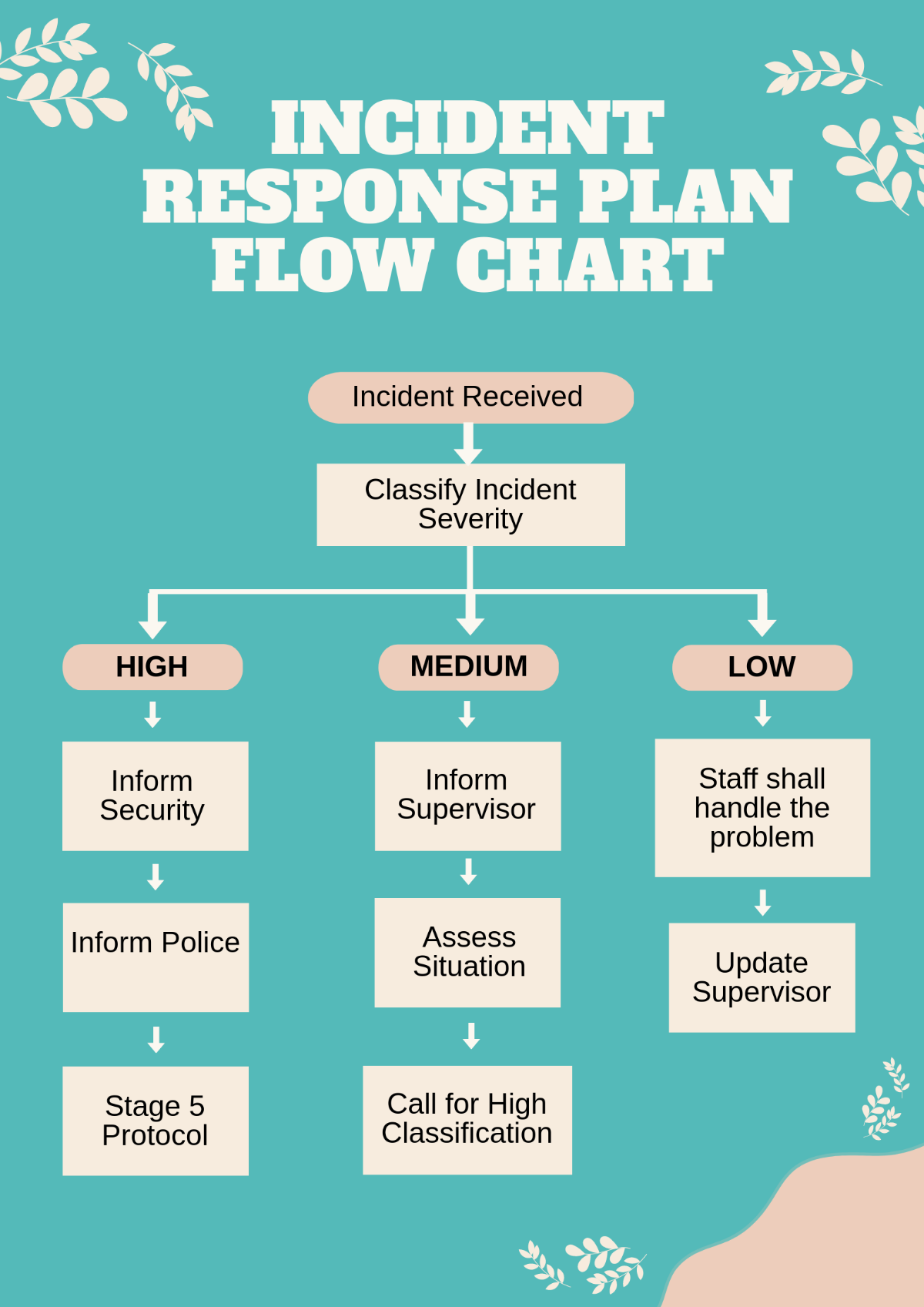
Incident Response Plan
_____________________________________________________________________________________
_____________________________________________________________________________________
I. Introduction
The Incident Response Plan (IRP) for [Your Company Name] facilitates a swift and effective response to security incidents, safeguarding the company's assets and maintaining operational continuity. This plan outlines the roles, responsibilities, procedures, and communication protocols to be followed by the Incident Response Team (IRT) and relevant stakeholders during security incidents.
_____________________________________________________________________________________
II. Incident Response Team (IRT) Roles and Responsibilities
Roles | Responsibilities |
|---|---|
Chief Information Security Officer (CISO) | Helen Ramirez oversees the incident response process and coordinates with executive leadership. |
IT Security Managers and Analysts | John Smith and Emily Johnson are responsible for incident detection, analysis, and containment. |
Legal and Compliance Officers | David Miller ensures incident response actions comply with legal and regulatory requirements. |
Public Relations and Communications Specialists | Sarah Thompson manages external communication and media relations during incidents. |
Business Continuity and Disaster Recovery Planners | Michael Brown and Lisa Chen align incident response efforts with broader organizational resilience strategies. |
_____________________________________________________________________________________
III. Incident Classification
Incidents are classified based on severity and impact to prioritize response efforts. Classification criteria include the extent of data compromise, potential harm to the organization, and regulatory implications.
_____________________________________________________________________________________
IV. Detection and Reporting
Detection Mechanisms
Utilize intrusion detection systems, security information, event management (SIEM) tools, and employee reporting mechanisms to identify security incidents.
Reporting Procedures
Immediately report suspected incidents to the designated point of contact within the IRT or IT Security team.
_____________________________________________________________________________________
V. Incident Response Procedures
Initial Assessment
Assess the nature and scope of the incident, including potential impact on systems, data, and operations.
Containment and Mitigation
Immediately contain the incident and prevent further damage or unauthorized access.
Eradication
Remove or neutralize the threat from affected systems and networks.
Recovery
Restore affected systems and data from backups and implement additional security measures to prevent future incidents.
_____________________________________________________________________________________
VI. Communication Plan
Internal Communication
Establish clear channels of communication within the IRT and across relevant departments.
External Communication
Designate spokespersons for communicating with external stakeholders, such as customers, partners, regulatory agencies, and the media.
Notification Procedures
Develop templates for notifying affected parties about the incident, including instructions for mitigating potential risks.
_____________________________________________________________________________________
VII. Containment, Eradication, and Recovery
Isolation
Isolate affected systems or networks to prevent further spread of the incident.
Forensic Analysis
Conduct forensic analysis to determine the root cause of the incident and gather evidence for investigation.
System Restoration
Restore systems and data from backups to resume normal operations.
Post-Incident Review
Conduct a post-incident review to evaluate the effectiveness of the response and identify areas for improvement.
_____________________________________________________________________________________
VIII. Post-Incident Analysis and Reporting
Documentation
Document all actions taken during the incident response process, including timelines, decisions, and outcomes.
Lessons Learned
Identify lessons learned from the incident and make recommendations for enhancing the organization's security posture.
Reporting
Prepare incident reports for executive leadership, regulatory agencies, and other relevant stakeholders as required by policy or regulation.
_____________________________________________________________________________________
IX. Training and Awareness
Employee Training
Provide regular training and awareness programs to educate employees about security risks, incident response procedures, and their roles and responsibilities.
Simulated Exercises
Conduct simulated incident response exercises to test the effectiveness of the IRP and familiarize stakeholders with their roles during a real incident.
_____________________________________________________________________________________
X. Appendices
Contact Information
Maintain a list of contact information for members of the IRT, key stakeholders, and external partners.
Checklists and Forms
Include checklists, incident reporting forms, and other resources to facilitate incident response activities.
Legal and Regulatory References
Include relevant legal and regulatory references, such as data breach notification requirements and incident reporting obligations.
_____________________________________________________________________________________