Incident Response Management Plan
Prepared by: [Your Name]
Date: [Date]
I. Introduction
The [Your Company Name] Cybersecurity Incident Response Management Plan outlines procedures and protocols to be followed in the event of cybersecurity incidents, including malware infections, data breaches, and denial-of-service attacks. The plan aims to minimize the impact of such incidents on [Your Company Name]'s operations, assets, and reputation by providing a structured and coordinated approach to incident response.
II. Purpose
The purpose of this plan is to:
Establish clear roles and responsibilities for responding to cybersecurity incidents.
Provide guidelines for identifying, assessing, and containing incidents.
Define procedures for communicating with stakeholders, including employees, customers, regulators, and law enforcement agencies.
Facilitate the timely and effective recovery from cybersecurity incidents.
Promote continuous improvement through post-incident analysis and lessons learned.
III. Scope
This plan applies to all employees, contractors, and third-party vendors who have access to [Your Company Name]'s information systems and data. It covers all cybersecurity incidents that may affect [Your Company Name]'s confidentiality, integrity, or availability, regardless of the source or motive.
IV. Incident Response Team
[Your Company Name] has established an Incident Response Team (IRT) responsible for implementing this plan and coordinating the response to cybersecurity incidents. The IRT is composed of the following roles:
Role | Responsibilities |
|---|---|
Chief Information Security Officer (CISO) | Overall responsibility for incident response efforts and decision-making. |
Incident Response Coordinator | Leads the incident response efforts and serves as the primary point of contact for all communications related to the incident. |
IT Security Analysts | Investigate and analyze security incidents, identify containment measures, and assist with recovery efforts. |
Legal Counsel | Provides legal guidance and ensures compliance with relevant laws and regulations. |
Public Relations Officer | Manages external communications and media relations during cybersecurity incidents. |
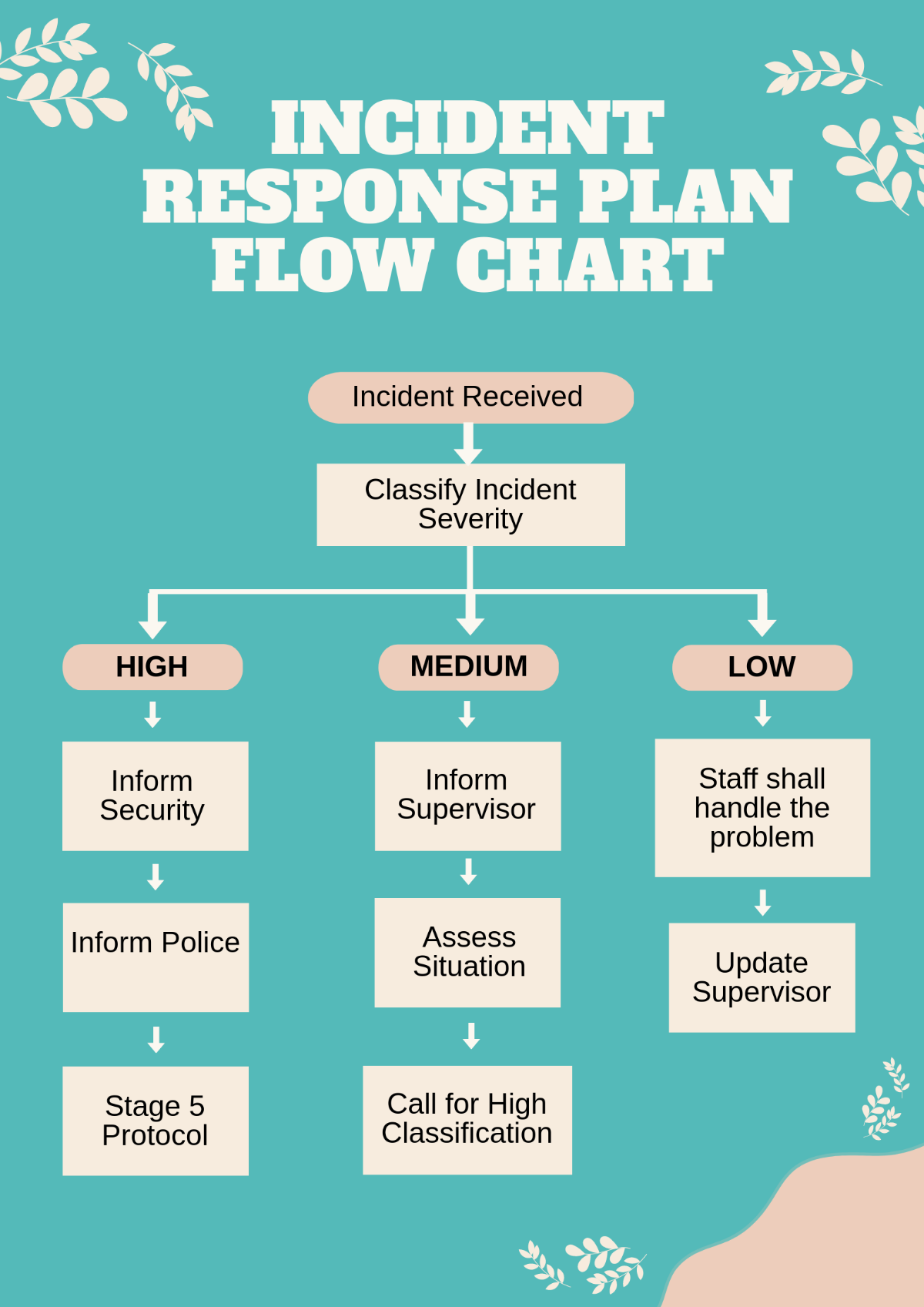
V. Incident Response Procedures
A. Incident Identification and Reporting
All employees are responsible for promptly reporting any suspicious activities or security incidents to the Incident Response Coordinator.
The Incident Response Coordinator will assess the reported incident and determine the appropriate response actions.
B. Incident Triage and Assessment
The Incident Response Team will triage the incident to determine its severity, impact, and scope.
Depending on the nature of the incident, the team will activate the appropriate response procedures and escalate as necessary.
C. Incident Containment and Mitigation
The Incident Response Team will work to contain the incident and prevent further damage or unauthorized access.
Containment measures may include isolating affected systems, blocking malicious traffic, and implementing temporary security controls.
D. Incident Investigation and Analysis
IT Security Analysts will conduct a thorough investigation to determine the root cause of the incident and identify any vulnerabilities or weaknesses in [Your Company Name]'s systems or procedures.
The Incident Response Coordinator will document all findings and maintain a chain of custody for evidence collected during the investigation.
E. Incident Recovery and Restoration
Once the incident is contained and mitigated, the Incident Response Team will focus on restoring affected systems and services to normal operations.
Recovery efforts may include restoring from backups, applying security patches, and implementing additional security measures to prevent future incidents.
F. Post-Incident Review and Lessons Learned
Following the resolution of the incident, the Incident Response Team will conduct a post-incident review to evaluate the effectiveness of the response efforts and identify areas for improvement.
Lessons learned from the incident will be documented and incorporated into future incident response procedures and training programs.
VI. Communication and Notification
A. Internal Communication
The Incident Response Coordinator will communicate regularly with key stakeholders within [Your Company Name], including executive management, IT teams, and relevant business units, to provide updates on the incident response efforts.
B. External Communication
The Public Relations Officer will manage external communications with customers, partners, regulators, and the media, following established communication protocols and guidelines.
Legal Counsel will guide the disclosure of information to external parties and ensure compliance with legal and regulatory requirements.
VII. Training and Awareness
[Your Company Name] will provide regular training and awareness programs to educate employees about cybersecurity best practices, incident reporting procedures, and their roles and responsibilities during incident response efforts.
VIII. Plan Maintenance and Testing
This plan will be reviewed and updated annually or as needed to reflect changes in technology, regulations, or business operations. [Your Company Name] will conduct regular tabletop exercises and simulated incident scenarios to test the effectiveness of the plan and ensure readiness to respond to cybersecurity incidents.
IX. Plan Approval and Acknowledgement
This Cybersecurity Incident Response Management Plan has been reviewed and approved by executive management. All employees, contractors, and third-party vendors are required to familiarize themselves with this plan and acknowledge their understanding and compliance with its provisions.
X. Plan Revision History
Version 1.0: May 15, 2050 - Initial release.
Version 2.0: August 22, 2053 - Comprehensive update.
Version 3.0: April 10, 2057 - Major revision for emerging threats.
XI. Glossary of Terms
Incident: Any event that compromises the confidentiality, integrity, or availability of [Your Company Name]'s information systems or data.
Malware: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems or data.
Data Breach: Unauthorized access, disclosure, or acquisition of sensitive information, such as customer data or intellectual property.
Denial-of-Service (DoS) Attack: An attempt to disrupt the normal functioning of a computer network or system by overwhelming it with a flood of traffic or requests.
For questions or assistance regarding this plan, please contact the [Your Company Name] Incident Response Coordinator at [Your Company Number] or [Your Company Email].