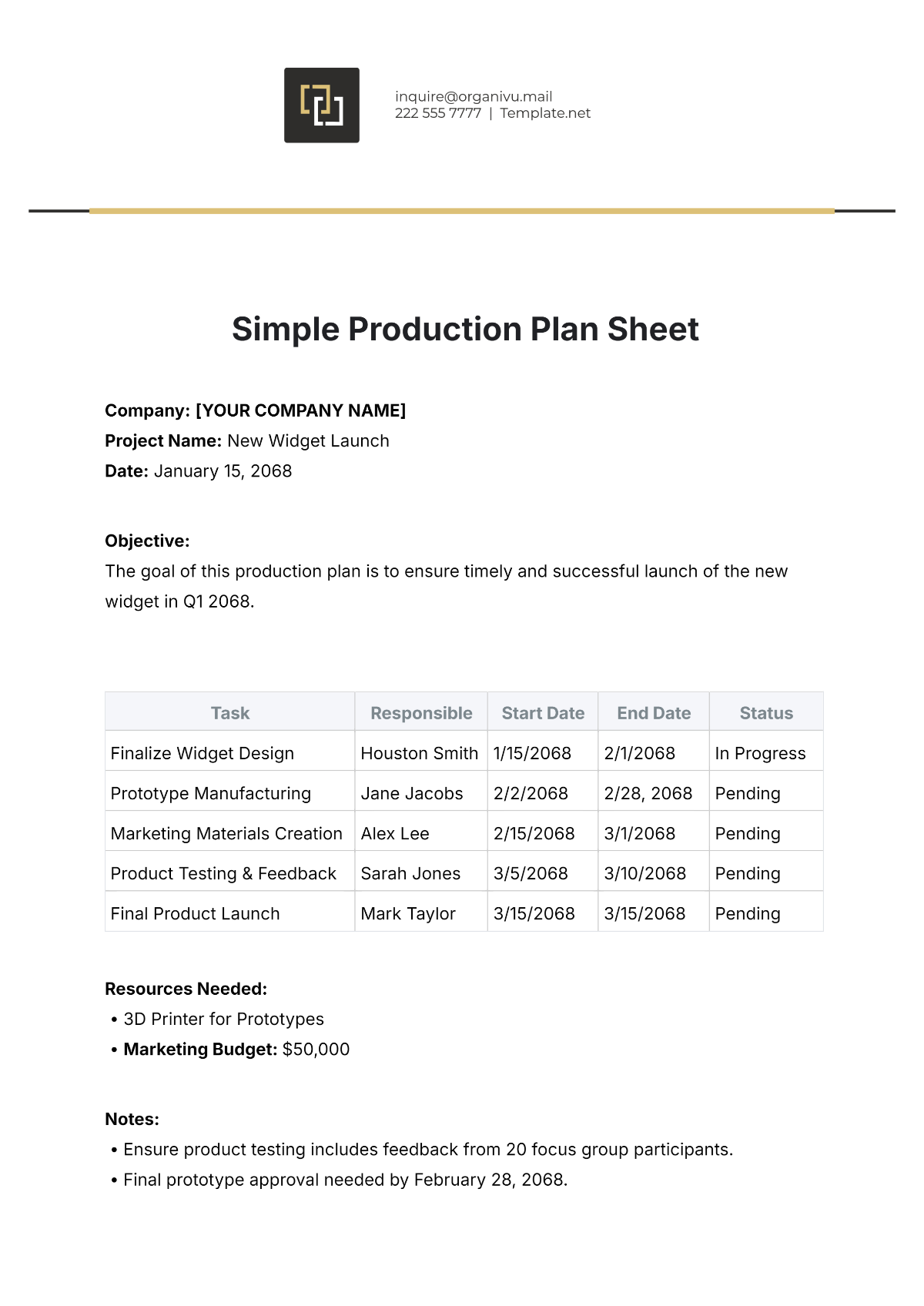
Raid Operation Plan
I. Introduction
The Raid Operation Plan outlines the comprehensive strategy for conducting a Counterterrorism raid to achieve the neutralization of a high-value target. This plan encompasses all aspects of the operation, including pre-mission preparation, execution, and post-operation procedures.
II. Mission Statement
The primary objective of this raid is to apprehend or eliminate the terrorist leader responsible for orchestrating recent attacks in the region. The success of the operation will be measured by the safe extraction of hostages, elimination of hostile threats, and the capture of key intelligence assets.
III. Intelligence and Reconnaissance
A. Target Location
Location: Abandoned warehouse at [Address], downtown.
Description: Large, multi-story building with limited points of entry and potential hiding spots.
Security Measures: Limited external security, possible internal traps, or surveillance devices.
B. Threat Assessment
Enemy Forces: Approximately 15 armed militants with automatic weapons and explosives.
Weapons: AK-47s, grenades, and improvised explosive devices (IEDs).
Potential Threats: Booby traps, hostages used as human shields.
C. Reconnaissance
Surveillance: Drone reconnaissance and ground surveillance teams.
Intel Gathering: Informants, intercepted communications, and satellite imagery.
IV. Operational Planning
A. Strategy
Approach: Covert approach under cover of darkness.
Entry Points: Front entrance and side door identified for breach.
Routes: The team will enter from multiple points to disorient enemy forces.
B. Tactics
Breach: Explosive breach for the main entrance, manual breach for the side door.
Clearing: Dynamic room-clearing tactics with emphasis on speed and surprise.
Securing: Restraining and searching all individuals encountered.
C. Logistics and Support
Equipment: Night vision goggles, body armor, breaching charges.
Personnel: 20 operators divided into assault, support, and command elements.
Transportation: Armored vehicles for insertion and extraction.
V. Rules of Engagement
Use of Force: Lethal force authorized against armed hostiles.
Engagement Protocol: Verbal warnings followed by immediate action if non-compliance.
Civilians: Minimize civilian casualties, and prioritize the safety of hostages.
VI. Execution
A. Deployment
Team Composition: Assault teams, sniper teams, explosive ordnance disposal (EOD) teams.
Briefing: Detailed briefing conducted two hours before insertion.
B. Breach and Entry
Breach Point: Simultaneous breach of the main entrance and side door.
Entry Procedure: Rapid entry, neutralize immediate threats, secure entry points.
C. Clearing and Securing
Room Clearance: Methodical room clearing with support from sniper overwatch.
Securing Tactics: Flexi-cuffs and thorough searches of all rooms and individuals.
VII. Post-Operation Procedures
A. Debriefing
After-Action Review: Conducted immediately upon return to base.
Lessons Learned: Documented for future training and operations.
B. Evidence Collection
Evidence Handling: Chain of custody maintained for all captured weapons and documents.
Documentation: Detailed reports filed by team leaders.
C. Follow-Up Actions
Medical Care: Immediate medical attention for wounded personnel and civilians.
Legal Procedures: Detainees are processed according to local laws and international conventions.
VIII. Command and Control
Command Structure: Unified command structure led by mission commander.
Communication: Secure radio communications between teams and the command center.
IX. Appendices
Maps: Detailed maps of the target area and surrounding environs.
Diagrams: Floor plans of target building and entry points.
Risk Assessments: Identified risks and mitigation strategies.
X. Financial Projections
Year | Revenue ($M) | Expenses ($M) | Net Income ($M) |
|---|---|---|---|
2050 | 50 | 30 | 20 |
2051 | 55 | 32 | 23 |
2052 | 60 | 35 | 25 |
XI. SWOT Analysis
Strengths | Weaknesses | |
|---|---|---|
Opportunities | Collaboration with international partners. | Advanced training opportunities for personnel. |
Threats | Potential for collateral damage. | Escalation of conflict with enemy forces. |