Free Bank Incident Response Plan

_____________________________________________________________________________________
_____________________________________________________________________________________
I. Introduction
The Bank Incident Response Plan (BIRP) serves as a comprehensive framework to guide [Your Company Name]'s response to security incidents, breaches, and emergencies. This plan outlines the procedures and protocols necessary to mitigate the impact of incidents, safeguard sensitive information, maintain operational continuity, and ensure compliance with regulatory requirements.
_____________________________________________________________________________________
II. Roles and Responsibilities
Roles | Responsibilities |
|---|---|
Incident Response Team (IRT) | Comprised of individuals from Information Security, IT, Risk Management, Compliance, and Legal departments, responsible for coordinating and executing the response to incidents. |
Management | Provides oversight, support, and resource allocation during incident response efforts. |
IT Department | Provides technical expertise and assistance in identifying, containing, and remedying incidents. |
Legal Advisors | Offer guidance on legal and regulatory implications and requirements throughout the incident response process. |
_____________________________________________________________________________________
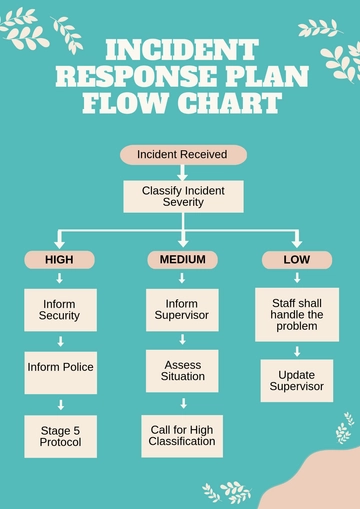
III. Incident Identification and Classification
Incidents are identified through various means, including intrusion detection systems, monitoring tools, reports from employees or customers, and regulatory notifications. Incidents are classified based on severity, impact, and type to determine the appropriate response level.
_____________________________________________________________________________________
IV. Incident Response Procedures
Initial Response
Upon identification, the Incident Response Team is notified, and initial containment measures are implemented to limit the incident's spread.
Investigation
The incident is thoroughly investigated to determine the root cause, the extent of the impact, and potentially compromised assets.
Containment and Eradication
Efforts are made to contain the incident to prevent further damage, followed by the removal of malicious entities from the network.
Recovery
Systems and data affected by the incident are restored to a secure state using backups and remediation measures.
Post-Incident Analysis
After the incident is resolved, a comprehensive analysis is conducted to identify lessons learned, areas for improvement, and potential regulatory implications.
_____________________________________________________________________________________
V. Communication Plan
Internal Communication
Clear and timely communication is maintained among the Incident Response Team, management, and relevant stakeholders throughout the incident lifecycle.
External Communication
Communication with regulatory authorities, law enforcement, customers, and other external parties is coordinated to meet reporting requirements and manage reputational risk.
_____________________________________________________________________________________
VI. Recovery Procedures
Efficient recovery procedures are implemented to restore affected systems, services, and data to normal operations. This includes prioritizing critical functions, testing backups, and verifying the integrity of restored systems.
_____________________________________________________________________________________
VII. Post-Incident Analysis
A post-incident analysis is conducted to assess the effectiveness of the response efforts, identify areas for improvement, and update the Incident Response Plan accordingly. Lessons learned are documented to enhance future incident response capabilities.
_____________________________________________________________________________________
VIII. Training and Awareness
Regular training and awareness programs are conducted to educate employees on their roles and responsibilities during an incident, familiarize them with incident response procedures, and enhance overall cybersecurity awareness.
_____________________________________________________________________________________
IX. Regulatory Compliance
The Bank Incident Response Plan ensures compliance with relevant laws, regulations, and industry standards governing incident response and data protection. This includes maintaining incident documentation, reporting requirements, and cooperation with regulatory authorities.
_____________________________________________________________________________________
X. Appendices
Appendices contain supporting documents such as contact lists, incident response forms, templates, and other resources to facilitate efficient incident response and management.
_____________________________________________________________________________________
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Ensure your bank's readiness with the Bank Incident Response Plan Template from Template.net. This fully customizable and editable document is designed for seamless integration. Effortlessly tailor it to your needs using our Ai Editor Tool, ensuring comprehensive incident management. Stay prepared and secure with a professional, adaptable response plan at your fingertips.
You may also like
- Finance Plan
- Construction Plan
- Sales Plan
- Development Plan
- Career Plan
- Budget Plan
- HR Plan
- Education Plan
- Transition Plan
- Work Plan
- Training Plan
- Communication Plan
- Operation Plan
- Health And Safety Plan
- Strategy Plan
- Professional Development Plan
- Advertising Plan
- Risk Management Plan
- Restaurant Plan
- School Plan
- Nursing Home Patient Care Plan
- Nursing Care Plan
- Plan Event
- Startup Plan
- Social Media Plan
- Staffing Plan
- Annual Plan
- Content Plan
- Payment Plan
- Implementation Plan
- Hotel Plan
- Workout Plan
- Accounting Plan
- Campaign Plan
- Essay Plan
- 30 60 90 Day Plan
- Research Plan
- Recruitment Plan
- 90 Day Plan
- Quarterly Plan
- Emergency Plan
- 5 Year Plan
- Gym Plan
- Personal Plan
- IT and Software Plan
- Treatment Plan
- Real Estate Plan
- Law Firm Plan
- Healthcare Plan
- Improvement Plan
- Media Plan
- 5 Year Business Plan
- Learning Plan
- Marketing Campaign Plan
- Travel Agency Plan
- Cleaning Services Plan
- Interior Design Plan
- Performance Plan
- PR Plan
- Birth Plan
- Life Plan
- SEO Plan
- Disaster Recovery Plan
- Continuity Plan
- Launch Plan
- Legal Plan
- Behavior Plan
- Performance Improvement Plan
- Salon Plan
- Security Plan
- Security Management Plan
- Employee Development Plan
- Quality Plan
- Service Improvement Plan
- Growth Plan
- Incident Response Plan
- Basketball Plan
- Emergency Action Plan
- Product Launch Plan
- Spa Plan
- Employee Training Plan
- Data Analysis Plan
- Employee Action Plan
- Territory Plan
- Audit Plan
- Classroom Plan
- Activity Plan
- Parenting Plan
- Care Plan
- Project Execution Plan
- Exercise Plan
- Internship Plan
- Software Development Plan
- Continuous Improvement Plan
- Leave Plan
- 90 Day Sales Plan
- Advertising Agency Plan
- Employee Transition Plan
- Smart Action Plan
- Workplace Safety Plan
- Behavior Change Plan
- Contingency Plan
- Continuity of Operations Plan
- Health Plan
- Quality Control Plan
- Self Plan
- Sports Development Plan
- Change Management Plan
- Ecommerce Plan
- Personal Financial Plan
- Process Improvement Plan
- 30-60-90 Day Sales Plan
- Crisis Management Plan
- Engagement Plan
- Execution Plan
- Pandemic Plan
- Quality Assurance Plan
- Service Continuity Plan
- Agile Project Plan
- Fundraising Plan
- Job Transition Plan
- Asset Maintenance Plan
- Maintenance Plan
- Software Test Plan
- Staff Training and Development Plan
- 3 Year Plan
- Brand Activation Plan
- Release Plan
- Resource Plan
- Risk Mitigation Plan
- Teacher Plan
- 30 60 90 Day Plan for New Manager
- Food Safety Plan
- Food Truck Plan
- Hiring Plan
- Quality Management Plan
- Wellness Plan
- Behavior Intervention Plan
- Bonus Plan
- Investment Plan
- Maternity Leave Plan
- Pandemic Response Plan
- Succession Planning
- Coaching Plan
- Configuration Management Plan
- Remote Work Plan
- Self Care Plan
- Teaching Plan
- 100-Day Plan
- HACCP Plan
- Student Plan
- Sustainability Plan
- 30 60 90 Day Plan for Interview
- Access Plan
- Site Specific Safety Plan