BEC Written Communication
I. Introduction to BEC Written Communication
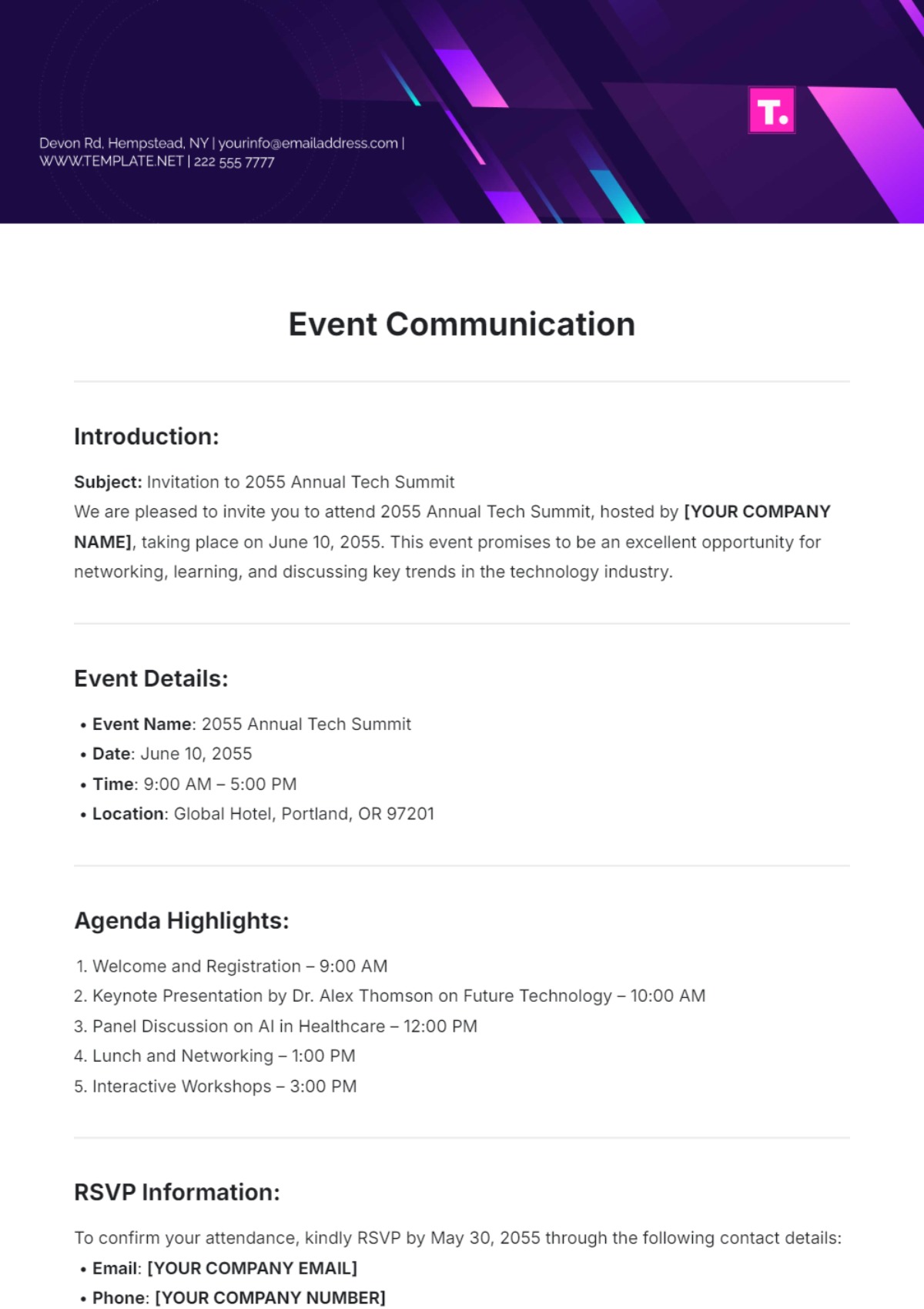
Business Email Compromise (BEC) written communication is a vital component in ensuring secure, clear, and effective exchange of information within and outside [YOUR COMPANY NAME]. This document provides a comprehensive guide on the rules and best practices for BEC-related written communication to enhance security and professionalism.
II. Understanding BEC Risks
BEC scams are sophisticated schemes aimed at executives, finance departments, or any stakeholders with financial authority. Understanding these risks is crucial in formulating an effective communication strategy.
A. Common BEC Tactics
Impersonation of high-ranking officials to authorize payments
Use of compromised email accounts
Creation of lookalike email domains
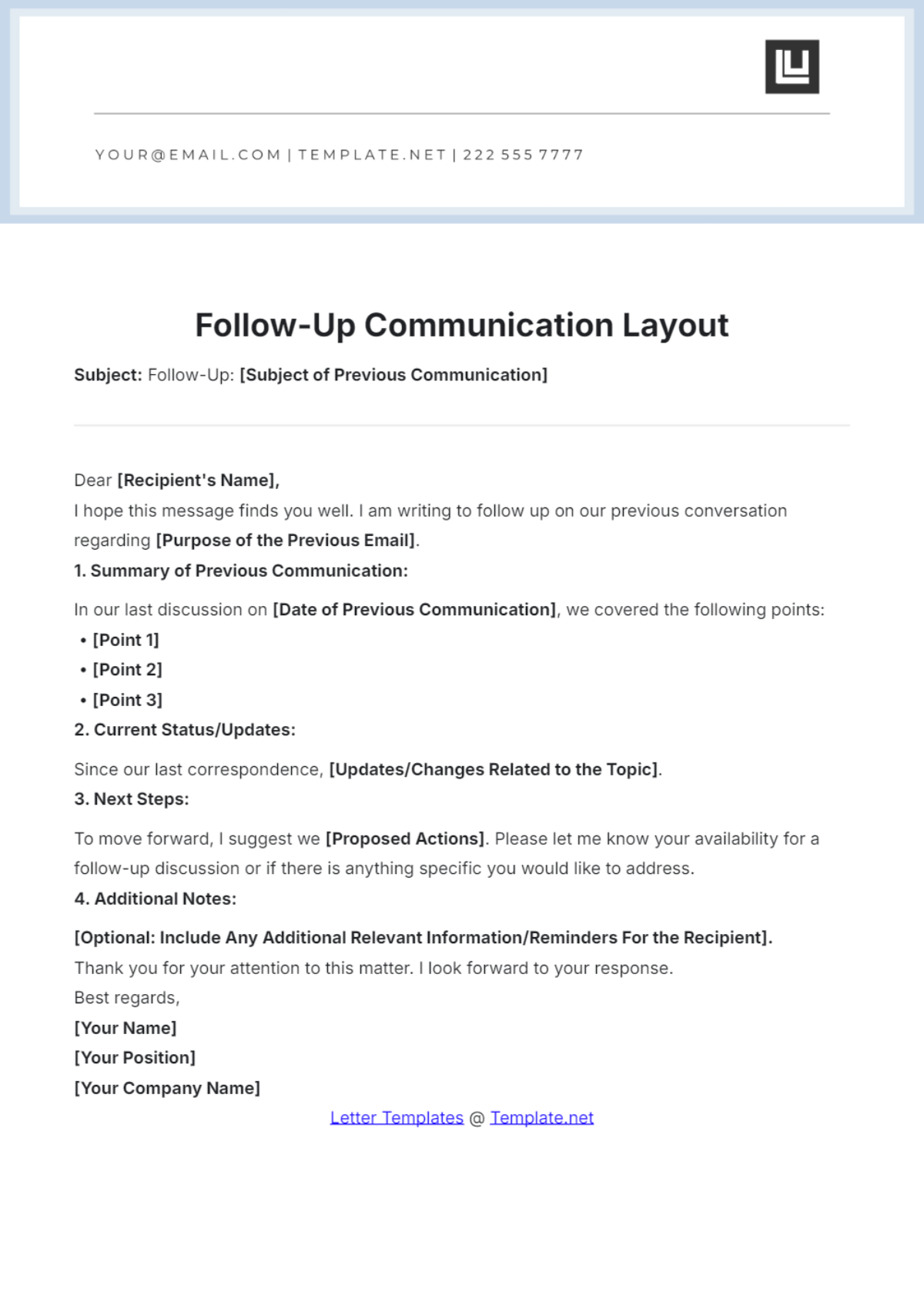
III. Best Practices for Effective Written Communication
To mitigate BEC threats, written communication should adhere to certain standards. These rules aim at enhancing both security and clarity:
A. Verification and Authentication
Always verify the identity of the sender before responding to emails involving sensitive information or financial transactions.
Double-check email addresses for anomalies.
Verify requests through alternate channels.
Implement two-factor authentication (2FA).
B. Clarity and Precision
Ensuring clarity and precision in written communication can prevent misunderstandings and potential exploitation.
Use clear and direct language.
Avoid jargon or ambiguous terms.
Provide context and background information when necessary.
C. Formal Communication Protocols
Implementing a formalized communication protocol within [YOUR COMPANY NAME] aids in maintaining consistency and security.
Standardize email formats and signatures.
Create templates for frequent communication types.
Regularly update contact lists to include verified emails.
IV. Tools and Resources for Secure Communication
Utilizing the right tools can significantly enhance the security and efficiency of written communications within [YOUR COMPANY NAME].
Email filtering and anti-spoofing tools
Secure communication platforms
Encryption services for sensitive emails
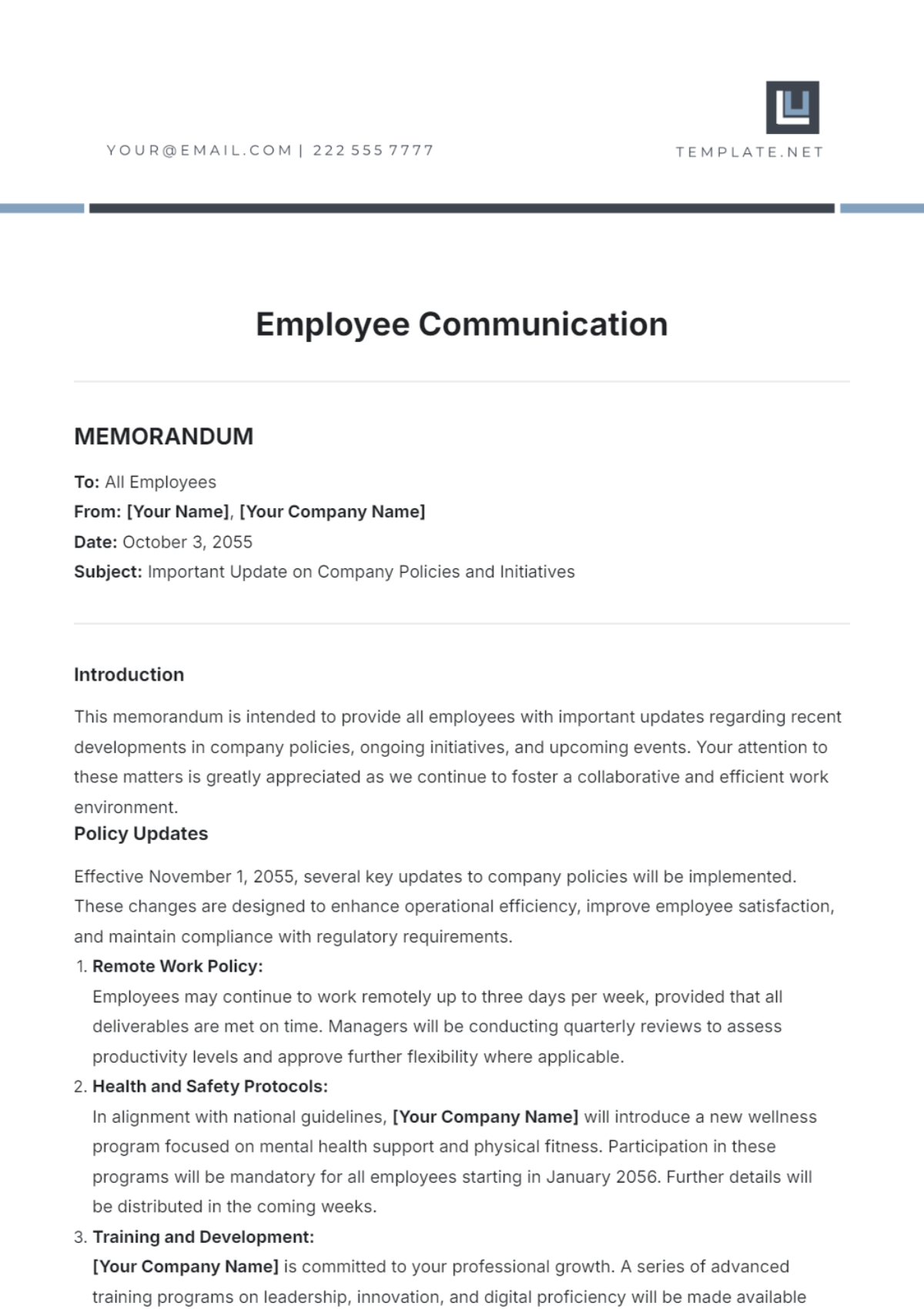
V. Training and Awareness
Employee training and constant awareness are key elements in preventing BEC threats. Regular training sessions should be conducted to educate our staff on spotting and handling potential threats.
Conduct regular security awareness workshops.
Update staff on recent BEC incidents and tactics.
Encourage reporting of suspicious communications promptly.
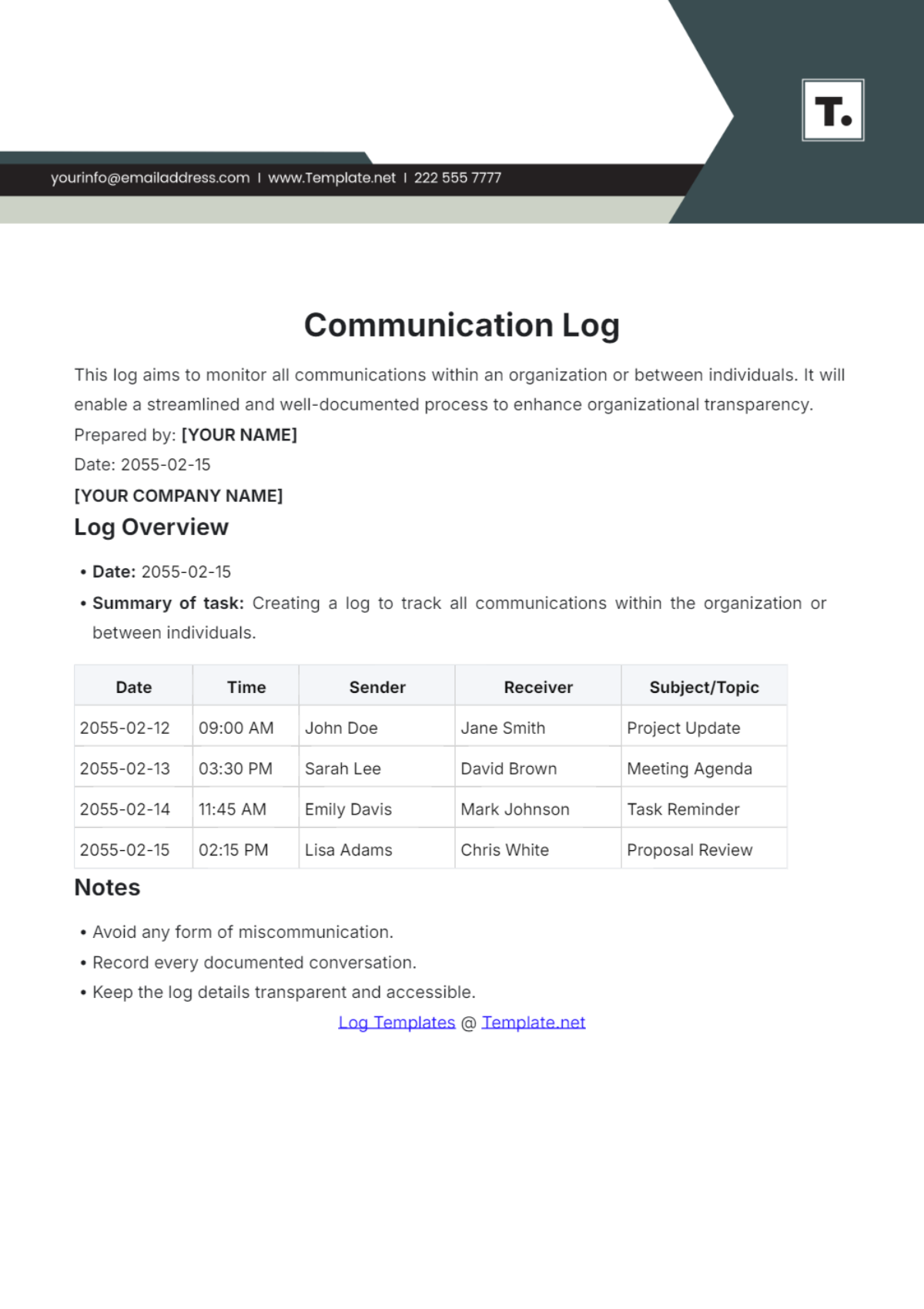
VI. Incident Response and Management
Having a well-defined incident response plan minimizes the damage in the event of a BEC breach.
Step | Action | Purpose |
|---|---|---|
1 | Immediate Reporting | Ensure quick response to limit potential damage. |
2 | Investigation | Analyze the breach to understand vulnerabilities. |
3 | Communication | Inform affected parties and send out alerts. |
4 | Remediation | Fix vulnerabilities and prevent future recurrences. |
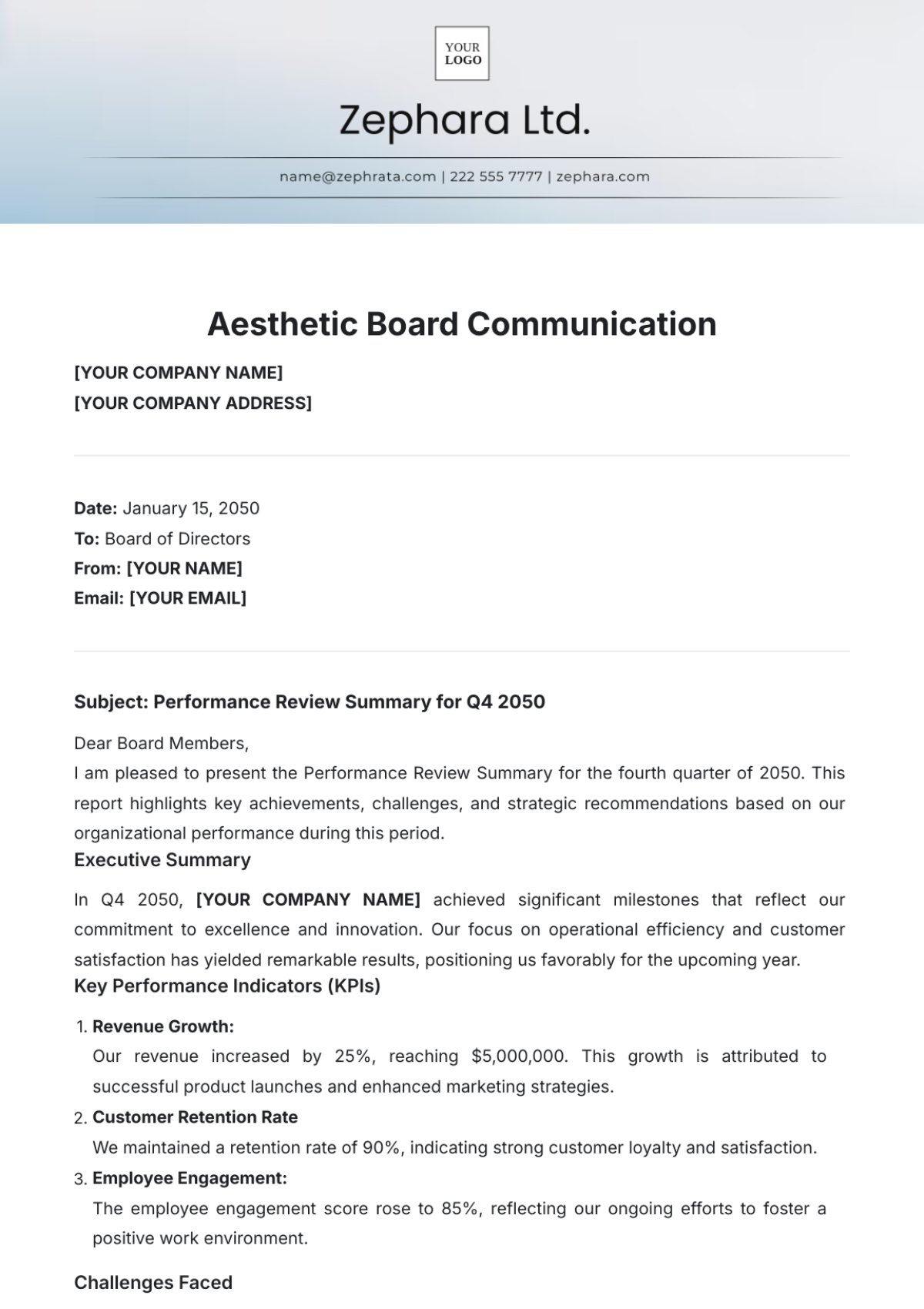
VII. Conclusion
Adhering to the guidelines outlined in this document will greatly enhance [YOUR COMPANY NAME]'s BEC written communication effectiveness and security. It is essential for [YOUR COMPANY NAME] to continuously evaluate and update our communication practices in response to emerging threats and technological advancements.