IT Declaration
I. Declaration Purpose
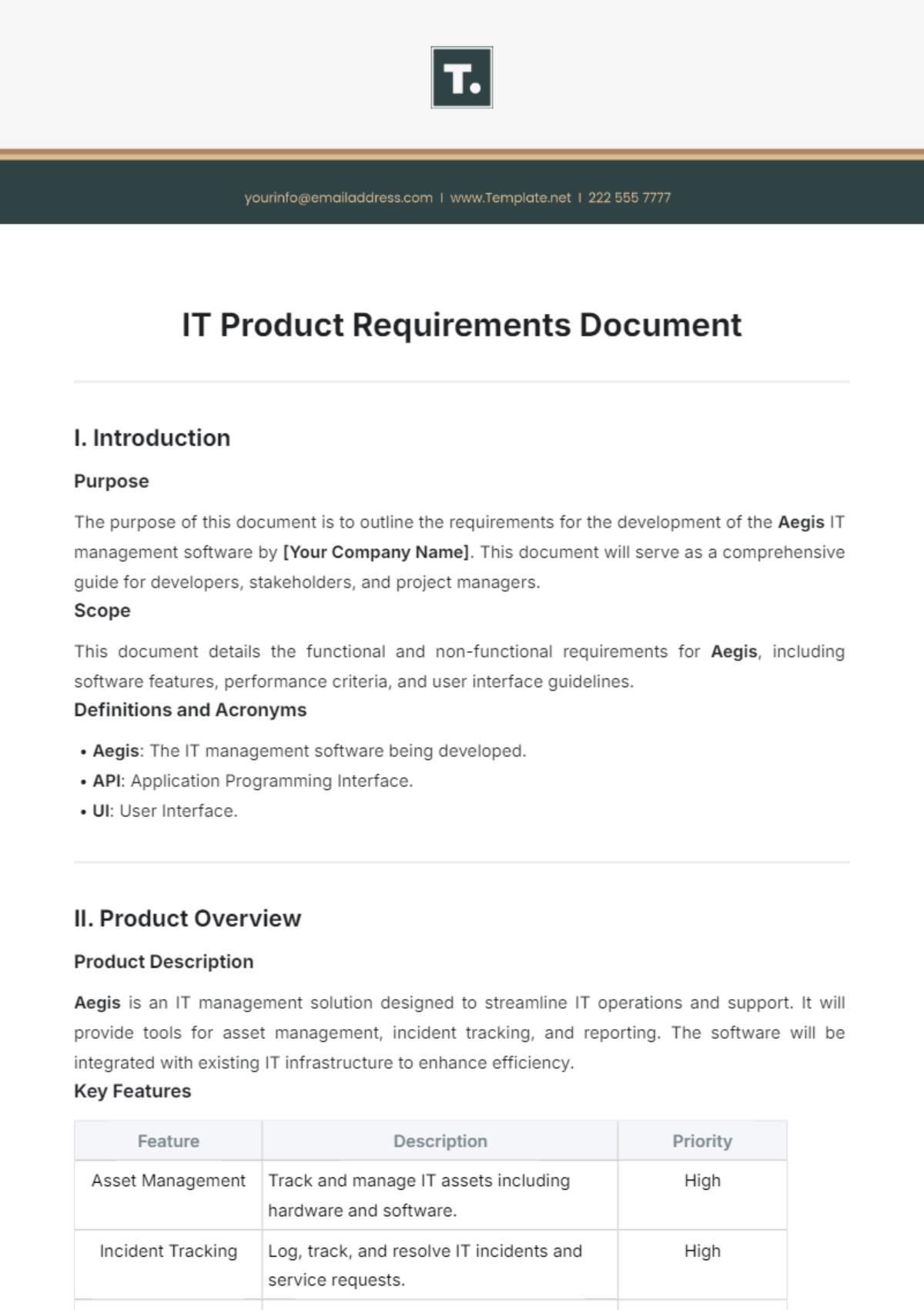
This IT Declaration serves as a formal affirmation by [YOUR NAME], holding the position of [YOUR POSITION] at [YOUR DEPARTMENT] of [YOUR COMPANY NAME]. The purpose of this document is to certify that all IT policies and procedures have been complied with concerning the management, security, and use of information technology resources within the organisation. This declaration covers data integrity, confidentiality, and availability of the IT systems deployed by [YOUR COMPANY NAME].
II. Compliance with IT Policies
I, [YOUR NAME], hereby declare that I have reviewed the current Information Technology policies as outlined by [YOUR COMPANY NAME]. I confirm that these policies have been fully implemented and adhered to during the period of TIME PERIOD, e.g., 'the last fiscal year'. This includes, but is not limited to, compliance with:
Data protection and privacy laws,
Internal cybersecurity protocols,
Use of licensed software,
Regular system and security updates.
III. System Integrity and Security
[YOUR COMPANY NAME] has taken all necessary steps to ensure that the IT systems are secure from unauthorised access, data breaches, and other cyber threats. This includes the deployment of:
Firewall protections,
Antivirus and anti-malware software,
Regular security audits and vulnerability assessments,
Encryption of sensitive data.
IV. Employee Training and Awareness
[YOUR NAME] further certifies that all employees at [YOUR COMPANY NAME] have received adequate training regarding IT policy and data security best practices. This training aims to equip staff with the necessary knowledge to recognize and prevent potential IT security threats effectively.
V. Software Licensing and Compliance
I declare that all software used within [YOUR COMPANY NAME] is fully licensed, and all terms of use are adhered to according to the respective software license agreements. Regular audits are conducted to ensure compliance and to prevent any legal or operational risks associated with unlicensed software use.
VI. Data Privacy Compliance
[YOUR COMPANY NAME] strictly adheres to applicable data protection regulations, ensuring that all personal and sensitive information is handled in compliance with regional and international privacy laws. All data is collected, processed, stored, and disposed of in a manner that respects privacy and prevents data leakage.
VII. Incident Reporting and Response
I confirm that [YOUR COMPANY NAME] has an effective incident response plan in place. This plan has been activated promptly in response to any IT security incidents during the reporting period, with all such incidents documented and reported in accordance with legal and regulatory requirements.
VIII. Signature
This IT Declaration is signed on [DATE] by [YOUR NAME], affirming the accuracy and completeness of the information provided herein regarding the IT practices of [YOUR COMPANY NAME].

[YOUR PRINTED NAME]
[DATE]