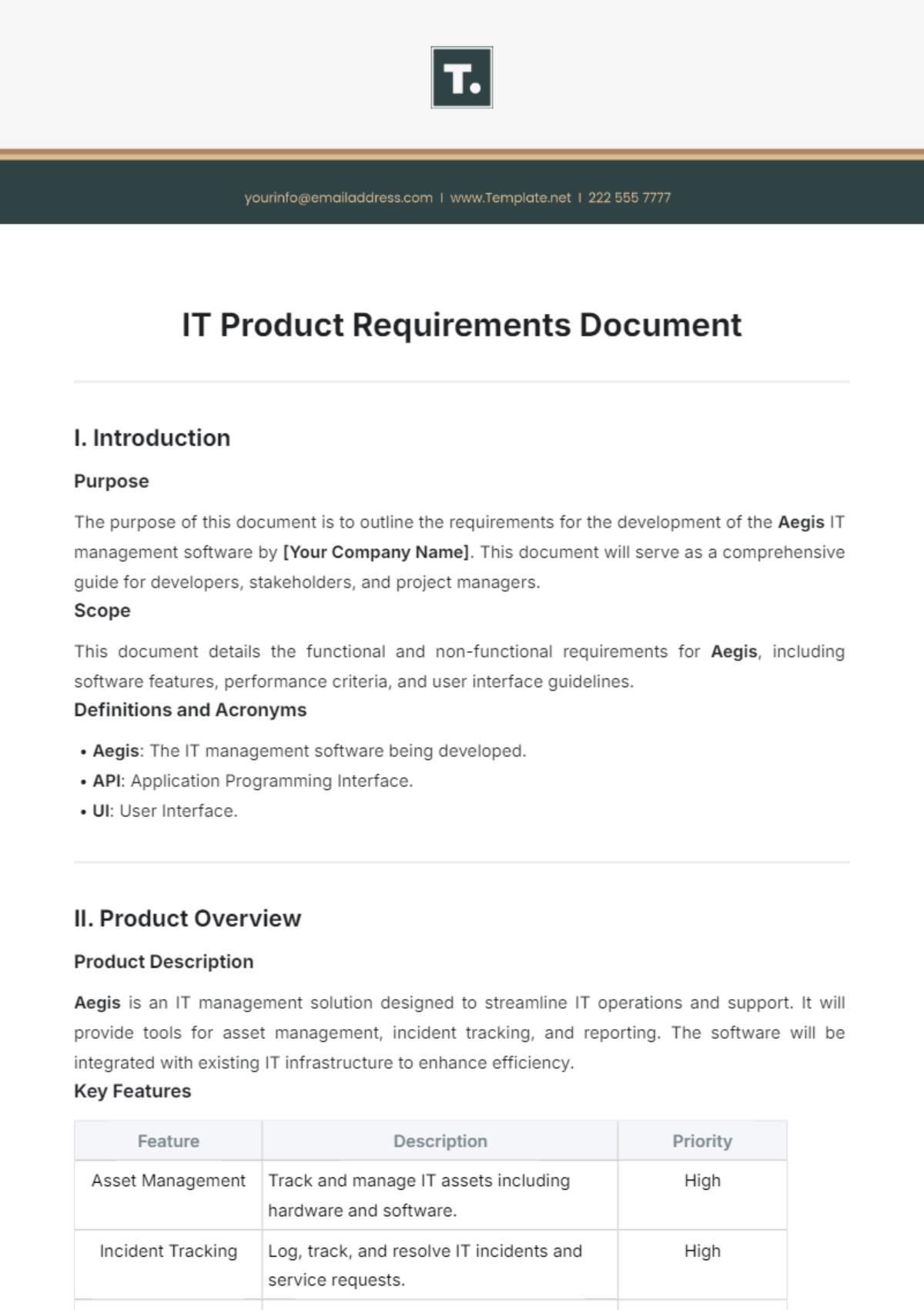
IT Incident Response Protocol
1. Purpose
The purpose of this protocol is to establish a standardized procedure for responding to IT incidents to minimize impact, ensure timely resolution, and maintain the security and integrity of [Your Company Name]'s IT systems.
2. Scope
This protocol applies to all IT incidents, including but not limited to system outages, data breaches, malware infections, and unauthorized access.
3. Incident Classification
Incidents are classified based on their severity and impact:
Critical: Major disruptions causing severe impact on business operations or sensitive data exposure.
High: Significant impact on business operations but not critical.
Medium: Moderate impact that can be contained with standard procedures.
Low: Minimal impact with manageable issues.
4. Incident Response Team (IRT)
The Incident Response Team is responsible for managing and resolving IT incidents. The team includes:
Incident Response Manager: Oversees the response process.
IT Security Specialist: Handles security-related aspects.
IT Support Staff: Provides technical support and remediation.
Communications Officer: Manages internal and external communications.
5. Incident Response Procedure
5.1 Detection and Identification
Detection: Monitor systems and networks for potential incidents using security tools and user reports.
Identification: Verify the incident by assessing the nature and scope. Classify the incident based on predefined categories.
5.2 Containment
Short-Term Containment: Implement immediate actions to limit the spread of the incident (e.g., isolating affected systems).
Long-Term Containment: Apply more comprehensive measures to prevent recurrence while the root cause is investigated.
5.3 Eradication
Root Cause Analysis: Identify and eliminate the root cause of the incident.
System Cleanup: Remove any malicious software or unauthorized access points.
5.4 Recovery
System Restoration: Restore affected systems to normal operations, ensuring they are free from threats.
Monitoring: Continuously monitor systems for signs of residual issues or reinfection.
5.5 Post-Incident Review
Debriefing: Conduct a review meeting with the Incident Response Team to discuss the incident, response effectiveness, and lessons learned.
Documentation: Document the incident details, response actions, and outcomes for future reference.
Improvement: Update incident response procedures based on lessons learned and implement any necessary improvements.
6. Communication
Internal Communication: Inform relevant stakeholders and team members about the incident and its status.
External Communication: Coordinate with legal and public relations teams to manage communication with external parties, including customers and regulators if required.
7. Training and Awareness
Employee Training: Conduct regular training for employees on incident detection and reporting.
Incident Response Drills: Perform periodic drills to test the effectiveness of the incident response protocol and improve team readiness.
8. Review and Updates
Protocol Review: Regularly review and update the incident response protocol to reflect changes in the IT environment and emerging threats.
Compliance: Ensure the protocol complies with relevant regulations and industry standards.
9. Contact Information
Role | Name | |
|---|---|---|
Incident Response Manager | [Your Name] | [Your Email] |
IT Security Specialist | [Security Specialist Name] | [Security Specialist Email] |
IT Support | [IT Support Name] | [IT Support Email] |
Communications Officer | [Communications Officer Name] | [Communications Officer Email] |