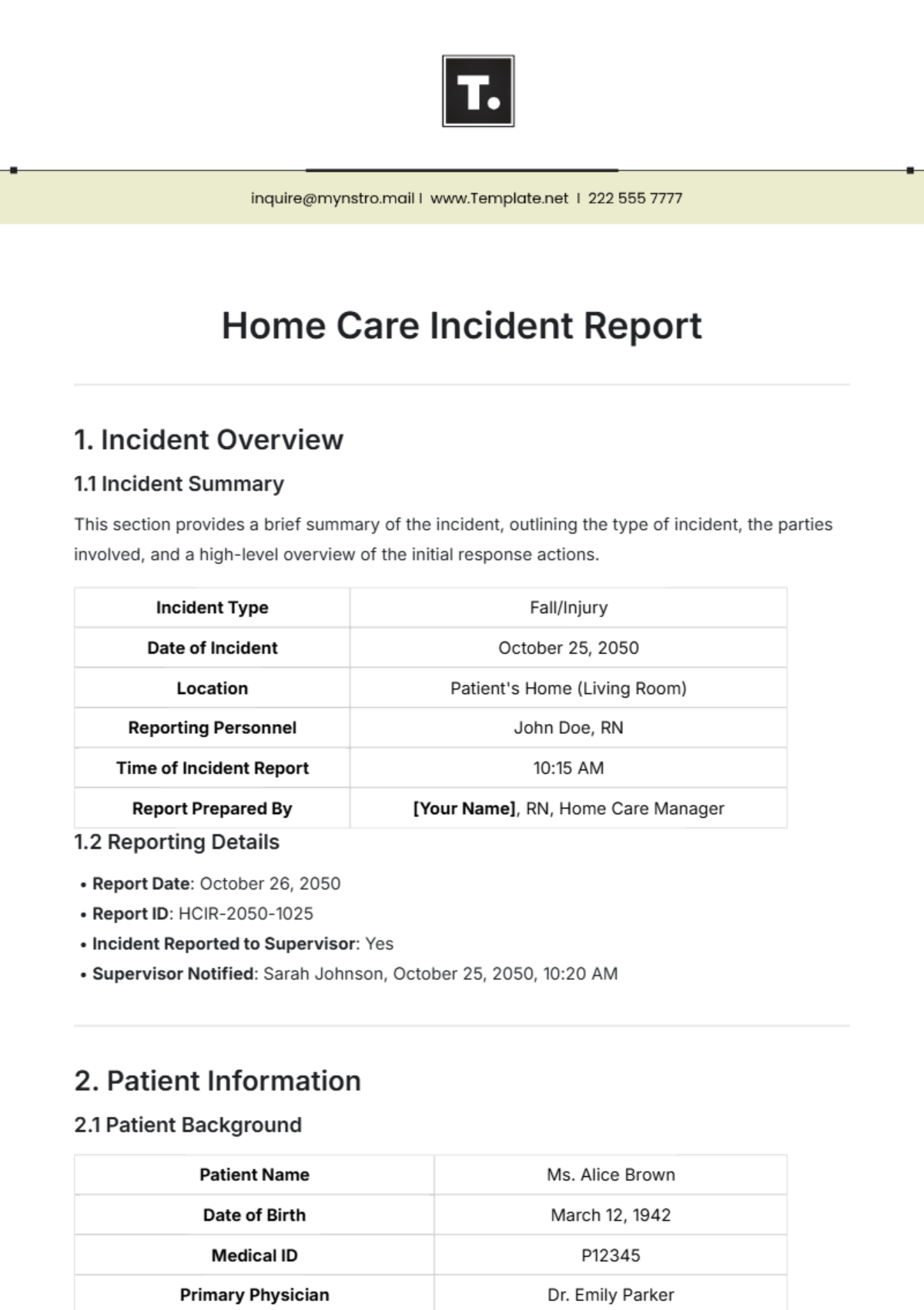
Cyber Intelligence Report
Company: | [YOUR COMPANY NAME] | ||
Prepared by: | [YOUR NAME] | Department: | [YOUR DEPARTMENT] |
I. Introduction
The [YOUR COMPANY NAME] Cyber Intelligence Report provides a comprehensive analysis of the cybersecurity landscape and threats facing [YOUR COMPANY NAME]. This report aims to equip stakeholders with actionable insights to enhance cybersecurity resilience and protect against cyber threats. The introduction sets the stage for the report, outlining its objectives and the importance of cybersecurity in safeguarding [YOUR COMPANY NAME]'s assets and data.
II. Methodology
The methodology section details the approach and techniques used to gather and analyze cyber intelligence data. It includes:
Data Sources: Identification of sources of cyber intelligence, including threat feeds, security tools, and internal logs.
Data Collection: Description of the data collection process, including automated tools, manual assessments, and threat intelligence feeds.
Analysis Techniques: Explanation of analytical methods used to interpret and derive insights from the collected data, such as threat modeling, data correlation, and statistical analysis.
Limitations: Disclosure of any limitations or constraints encountered during the data collection and analysis process, including data quality issues and resource constraints.
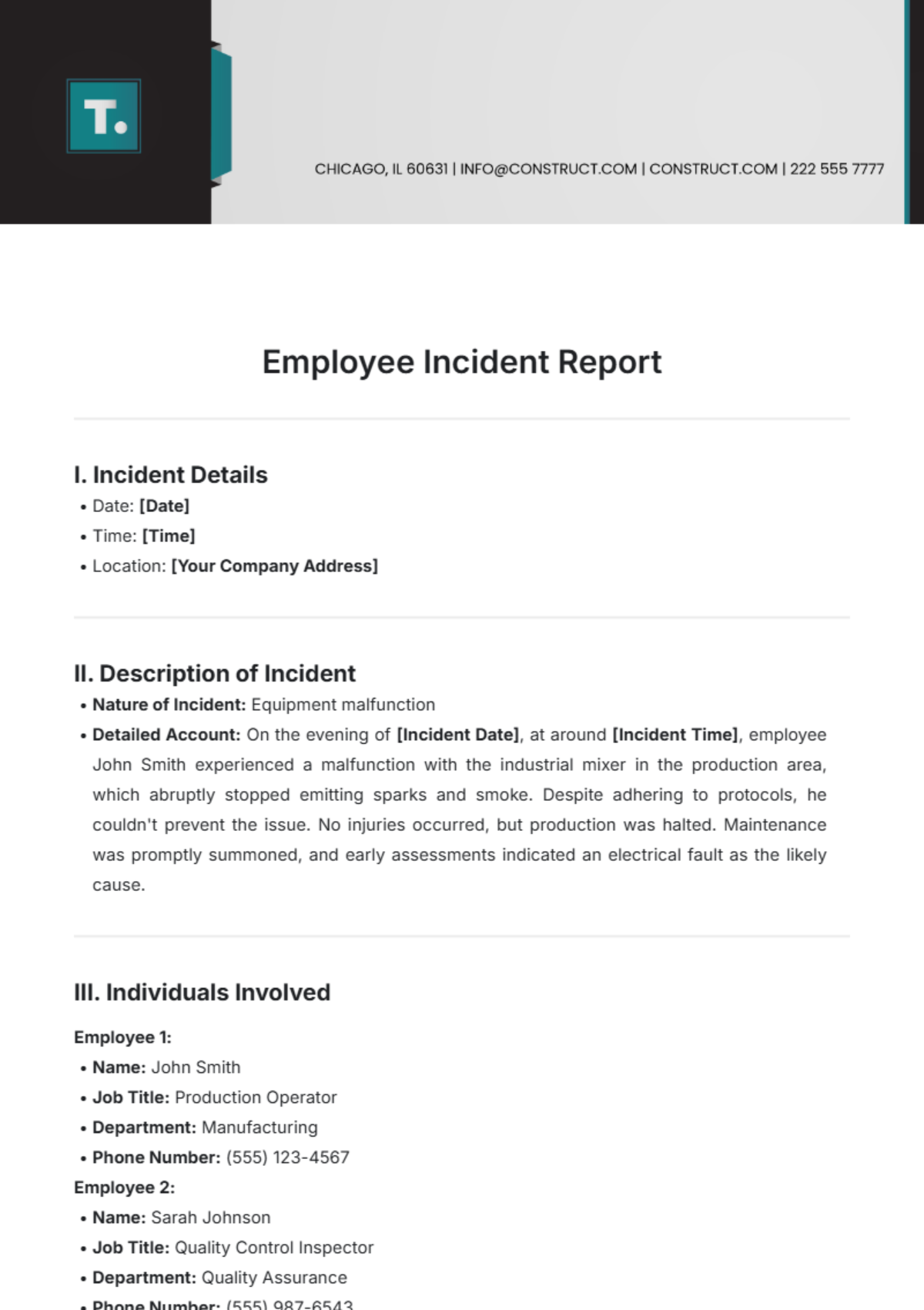
III. Findings
The findings section presents the key findings derived from the analysis of cyber intelligence data. It includes:
Common Threats: Identification of prevalent cyber threats targeting [YOUR COMPANY NAME], including malware, phishing, ransomware, and insider threats.
Vulnerabilities: Assessment of vulnerabilities in [YOUR COMPANY NAME]'s systems, applications, and infrastructure, along with potential attack vectors and exploitation methods.
Incident Trends: Analysis of recent cyber incidents and trends affecting [YOUR COMPANY NAME], including incident types, frequency, and impact.
Emerging Risks: Exploration of emerging cyber risks and trends, such as cloud security challenges, IoT vulnerabilities, and supply chain risks.
IV. Analysis
The analysis section delves deeper into the findings presented in the previous section, providing insights and interpretations to contextualize the data. It includes:
Root Cause Analysis: Examination of the root causes contributing to cybersecurity vulnerabilities and incidents within [YOUR COMPANY NAME].
Impact Assessment: Evaluation of the potential impact of cyber threats and incidents on [YOUR COMPANY NAME]'s operations, reputation, and financials.
Trends Analysis: Identification of trends and patterns in cyber threat activity, including changes over time and seasonal variations.
Comparative Analysis: Benchmarking [YOUR COMPANY NAME]'s cybersecurity posture against industry standards and peers to identify areas for improvement.
V. Recommendations
The recommendations section offers actionable strategies and measures to mitigate cyber risks and enhance cybersecurity resilience. It includes:
Security Controls: Implementation of security controls and best practices to protect against common cyber threats, such as endpoint protection, network segmentation, and access controls.
Training and Awareness: Development of cybersecurity training and awareness programs to educate employees about cybersecurity risks and best practices.
Incident Response: Enhancement of incident response capabilities, including incident detection, containment, eradication, and recovery procedures.
Continuous Monitoring: Implementation of continuous monitoring and threat detection mechanisms to detect and respond to cyber threats in real-time.
VI. Security Posture Review
The Security Posture Review section evaluates the overall cybersecurity posture of [YOUR COMPANY NAME]. It includes:
Infrastructure Security: Assessment of network architecture, firewalls, intrusion detection/prevention systems, and other security controls to identify weaknesses and gaps.
Endpoint Security: Evaluation of endpoint protection measures, including antivirus software, endpoint detection and response (EDR) solutions, and device management policies.
Data Protection: Review of data encryption, access controls, data loss prevention (DLP) mechanisms, and backup/recovery processes to safeguard sensitive information.
Identity and Access Management (IAM): Analysis of user authentication methods, role-based access controls (RBAC), and privileged access management (PAM) to ensure secure access to resources.
Security Awareness: Assessment of employee awareness and training programs to mitigate insider threats and improve cybersecurity hygiene.
Incident Response Readiness: Evaluation of incident response plans, procedures, and resources to effectively detect, respond to, and recover from cyber incidents.
VII. Threat Assessment
The Threat Assessment section provides an analysis of current and emerging cyber threats targeting [YOUR COMPANY NAME]. It includes:
Threat Actors: Identification of threat actors, including cybercriminal organizations, nation-state adversaries, and insider threats, targeting [YOUR COMPANY NAME].
Attack Vectors: Analysis of common attack vectors, such as phishing, malware, ransomware, and supply chain attacks, used by threat actors to compromise systems and data.
Targeted Industries: Examination of industries and sectors commonly targeted by cyber threats, along with specific threats and tactics observed within these sectors.
Geographic Trends: Assessment of regional and geopolitical factors influencing cyber threats and attack trends targeting [YOUR COMPANY NAME].
Emerging Threats: Exploration of emerging cyber threats, including zero-day exploits, advanced persistent threats (APTs), and threats related to emerging technologies such as IoT and cloud computing.
These sections provide a comprehensive review of [YOUR COMPANY NAME]'s security posture and the evolving threat landscape, enabling stakeholders to make informed decisions and prioritize cybersecurity initiatives to mitigate risks effectively.
VIII. Conclusion
In conclusion, the Cyber Intelligence Report provides valuable insights into the cybersecurity landscape and threats facing [YOUR COMPANY NAME]. By leveraging the findings and recommendations presented in this report, stakeholders can strengthen [YOUR COMPANY NAME]'s cybersecurity defenses, enhance incident response capabilities, and mitigate the risk of cyber attacks. This report serves as a valuable resource for guiding cybersecurity strategy and decision-making to protect [YOUR COMPANY NAME]'s assets, data, and reputation.