Free Data Breach Incident Report

I. Incident Overview
Date and Time: May 15, 2050, 10:30 PM UTC
Incident ID: (e.g., #DB-2024-001)
Incident Detected By: Security Operations Center (SOC)
Incident Severity Level: (e.g., low, moderate, high)
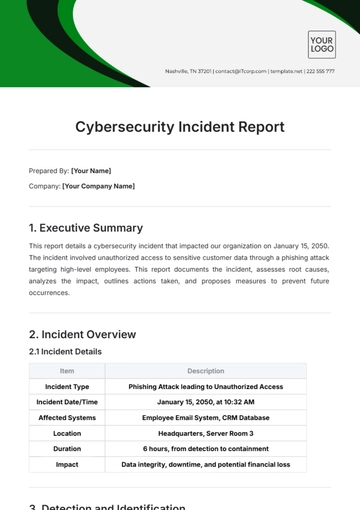
Initial Impact Assessment: The breach compromised sensitive customer data including names, addresses, and credit card information. Approximately 100,000 customer records were accessed.
II. Incident Details
Attack Vector: Phishing email containing malware attachments
Vulnerabilities Exploited: Exploitation of unpatched software vulnerabilities in the email client
Affected Systems/Assets: (e.g., Customer database, Payment processing servers)
Duration of Breach: The breach was active for approximately 72 hours, from May 15, 2050, 10:30 PM UTC to May 18, 2050, 10:30 PM UTC)
III. Data Compromised
Type of Data Compromised: e.g., Personally identifiable information (PII) such as names, addresses, phone numbers, email addresses, and credit card details
The extent of Breach: Approximately 100,000 customer records were compromised
Sensitive Data Exposed: Credit card numbers, expiration dates, and CVV codes were exposed, posing a significant risk of financial fraud and identity theft for affected individuals
IV. Impact Assessment
Financial Impact: Preliminary assessment indicates potential financial losses of $1.5 million due to regulatory fines, legal fees, and customer compensation
Reputational Damage: The breach has resulted in significant damage to the organization's reputation, leading to a loss of customer trust and negative publicity in the media
Regulatory Implications: The breach triggers mandatory reporting requirements under GDPR and PCI DSS. The organization is required to notify affected individuals and regulatory authorities within 72 hours of becoming aware of the breach
V. Response and Mitigation Actions
Immediate Actions Taken: Upon detection, the compromised systems were quickly isolated, and the incident response team assessed the breach, resetting passwords and logging out affected users.
Notification Process: The company informed both internal stakeholders—including senior management, legal counsel, and IT/security teams—and external stakeholders such as affected customers about the breach through email and website announcements, detailing the incident, mitigation efforts, and protective measures for affected individuals.
Forensic Analysis: Forensic experts conducted a detailed investigation of the breach, analyzing logs, network traffic, and malware, while also performing memory and disk forensics to identify the root cause, scope of unauthorized access, and any potential data exfiltration or additional compromises.
VI. Follow-up and Remediation
Remediation Efforts: All identified vulnerable systems and software were promptly patched and updated. Enhanced security measures, including multi-factor authentication and intrusion detection systems, were adopted. Ongoing security audits and penetration tests will continually address and fix remaining vulnerabilities.
Lessons Learned: The incident underscored the need for proactive security, including timely software updates and comprehensive cybersecurity training for employees. Recommendations are to refine incident response, boost employee security awareness, and strengthen access controls to protect sensitive data.
Security Enhancements: Future security improvements will center on enhancing network segmentation, upgrading threat detection with sophisticated analytics, and refining incident response to quickly manage breaches. Moreover, the organization will boost continuous security training for employees to stay alert to emerging cyber threats.
VII. Regulatory Reporting
Regulatory Requirements: The breach mandates reporting under GDPR and PCI DSS. GDPR requires notifying supervisory authorities within 72 hours and affected individuals immediately if there's a high risk to their rights and freedoms.
Timeline for Reporting: The incident response team will draft a comprehensive report on the breach, detailing its impact, cause, and remedies, for submission to the supervisory authority within 72 hours as mandated by GDPR. Affected individuals will be promptly notified via email and other appropriate channels, in line with regulatory requirements.
VIII. Contact Information
Name: | [Your Name] |
Email: | [Your Email] |
Phone: | [Your Phone Number] |
Position: | [Your Position] |
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Protect your organization's data integrity with the Data Breach Incident Report Template from Template.net. Fully customizable and editable, this template is designed to help you systematically document and respond to data breaches. Editable in our Ai Editor Tool, it offers a seamless experience to tailor the report to your specific needs, ensuring comprehensive and clear reporting.
You may also like
- Sales Report
- Daily Report
- Project Report
- Business Report
- Weekly Report
- Incident Report
- Annual Report
- Report Layout
- Report Design
- Progress Report
- Marketing Report
- Company Report
- Monthly Report
- Audit Report
- Status Report
- School Report
- Reports Hr
- Management Report
- Project Status Report
- Handover Report
- Health And Safety Report
- Restaurant Report
- Construction Report
- Research Report
- Evaluation Report
- Investigation Report
- Employee Report
- Advertising Report
- Weekly Status Report
- Project Management Report
- Finance Report
- Service Report
- Technical Report
- Meeting Report
- Quarterly Report
- Inspection Report
- Medical Report
- Test Report
- Summary Report
- Inventory Report
- Valuation Report
- Operations Report
- Payroll Report
- Training Report
- Job Report
- Case Report
- Performance Report
- Board Report
- Internal Audit Report
- Student Report
- Monthly Management Report
- Small Business Report
- Accident Report
- Call Center Report
- Activity Report
- IT and Software Report
- Internship Report
- Visit Report
- Product Report
- Book Report
- Property Report
- Recruitment Report
- University Report
- Event Report
- SEO Report
- Conference Report
- Narrative Report
- Nursing Home Report
- Preschool Report
- Call Report
- Customer Report
- Employee Incident Report
- Accomplishment Report
- Social Media Report
- Work From Home Report
- Security Report
- Damage Report
- Quality Report
- Internal Report
- Nurse Report
- Real Estate Report
- Hotel Report
- Equipment Report
- Credit Report
- Field Report
- Non Profit Report
- Maintenance Report
- News Report
- Survey Report
- Executive Report
- Law Firm Report
- Advertising Agency Report
- Interior Design Report
- Travel Agency Report
- Stock Report
- Salon Report
- Bug Report
- Workplace Report
- Action Report
- Investor Report
- Cleaning Services Report
- Consulting Report
- Freelancer Report
- Site Visit Report
- Trip Report
- Classroom Observation Report
- Vehicle Report
- Final Report
- Software Report