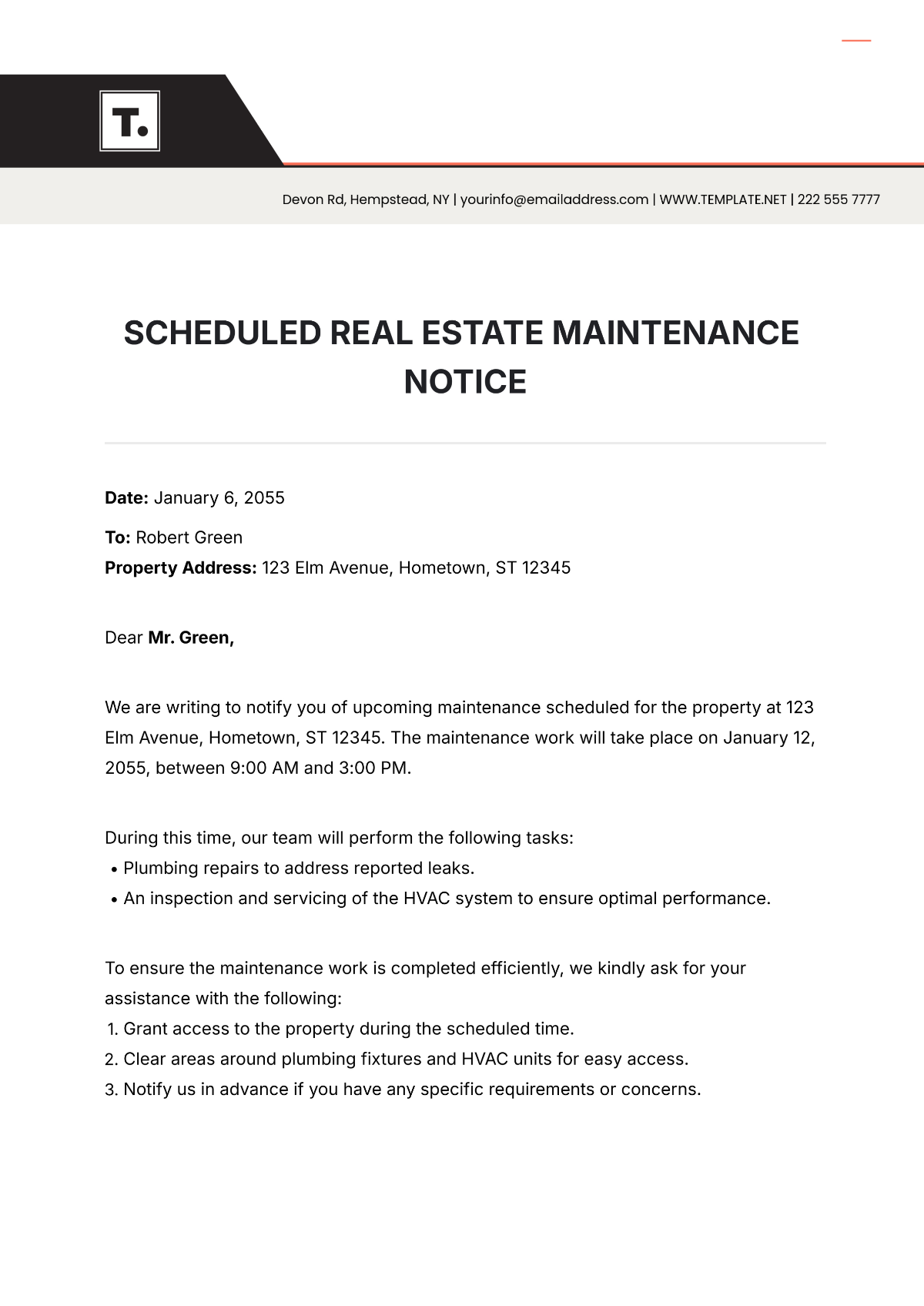
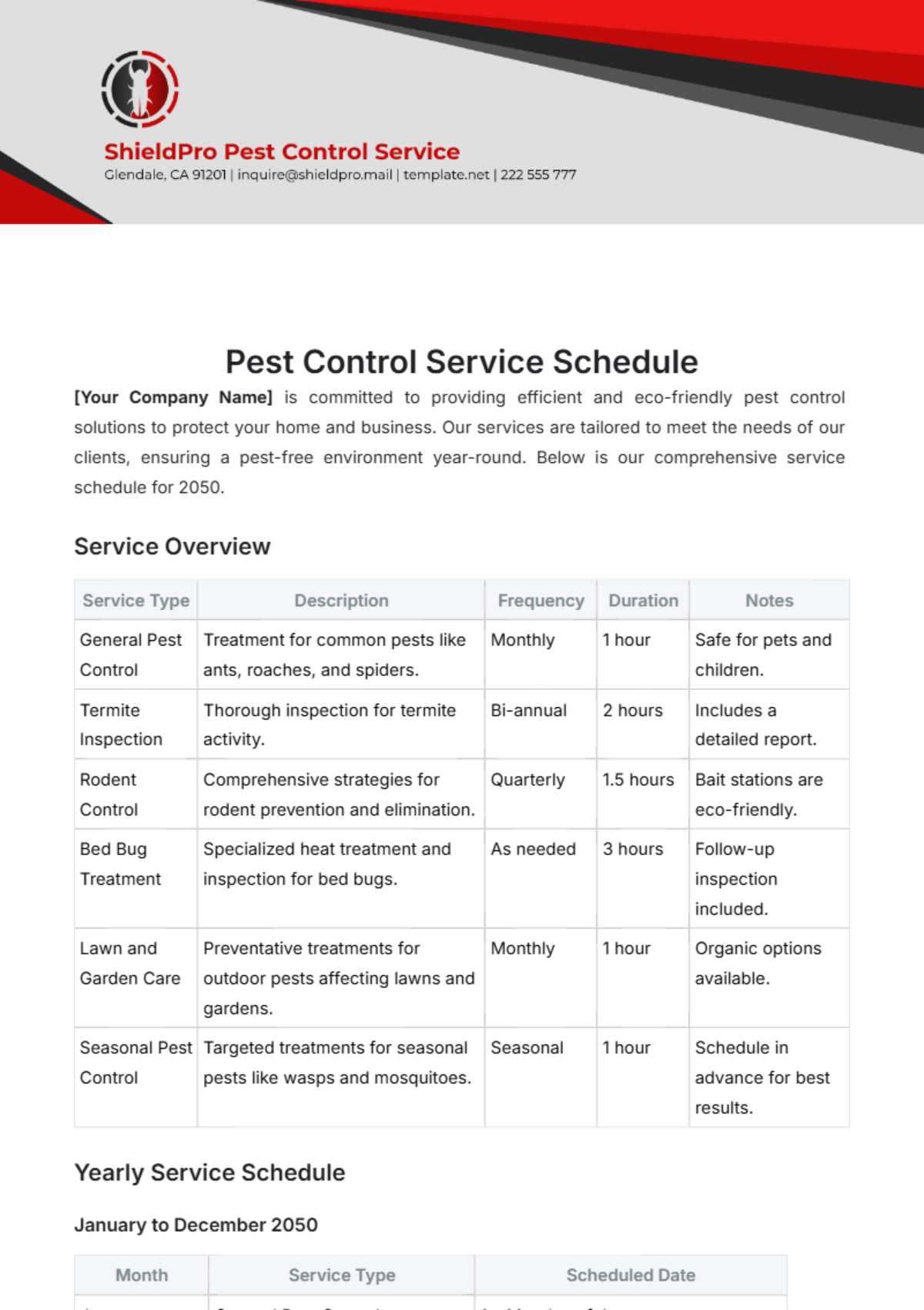
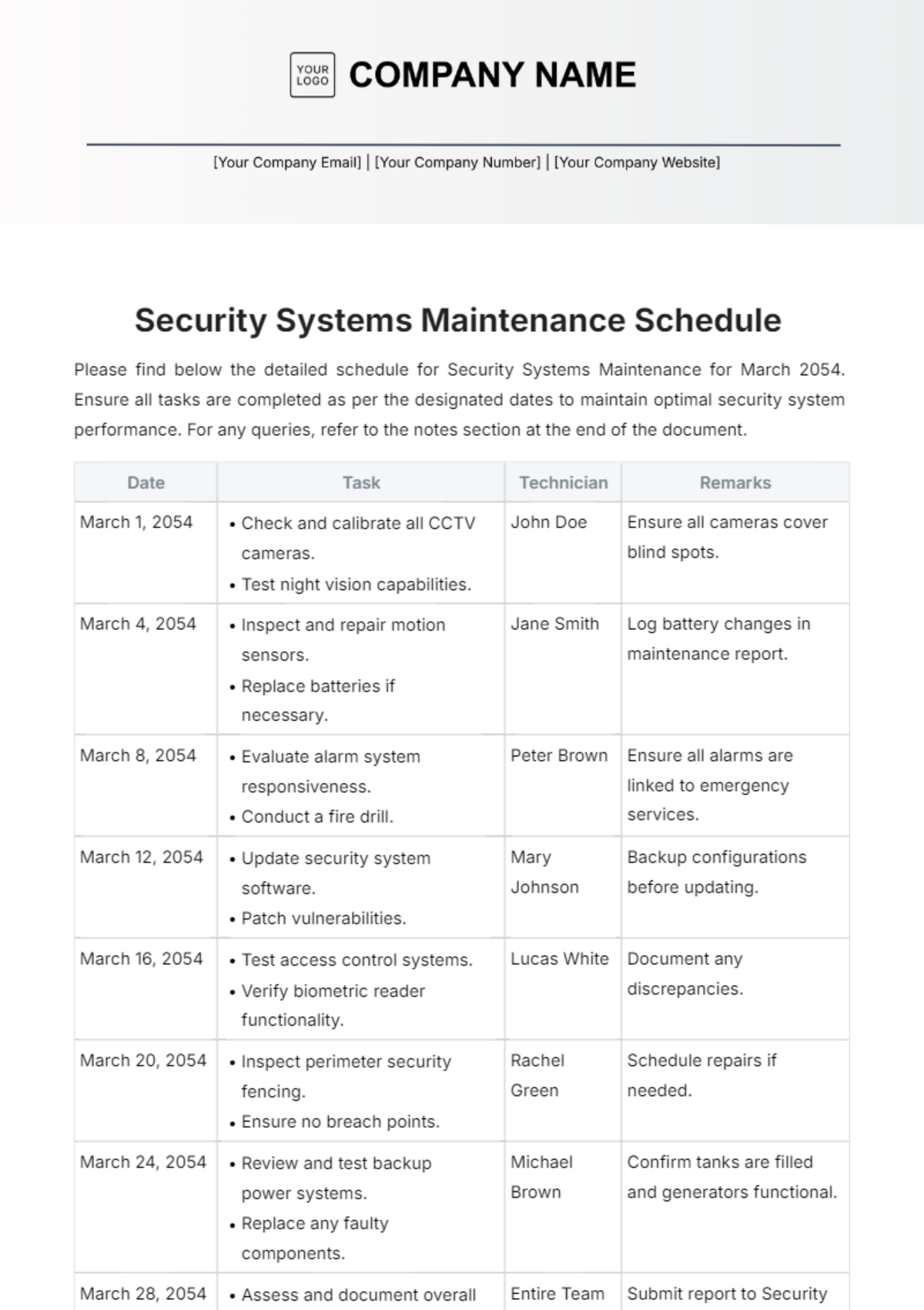
Network Maintenance Schedule
Maintaining the reliability, security, and performance of our network infrastructure is crucial for supporting [Your Company Name]'s operations and safeguarding data integrity. This schedule outlines the planned maintenance activities and tasks required to achieve these objectives.
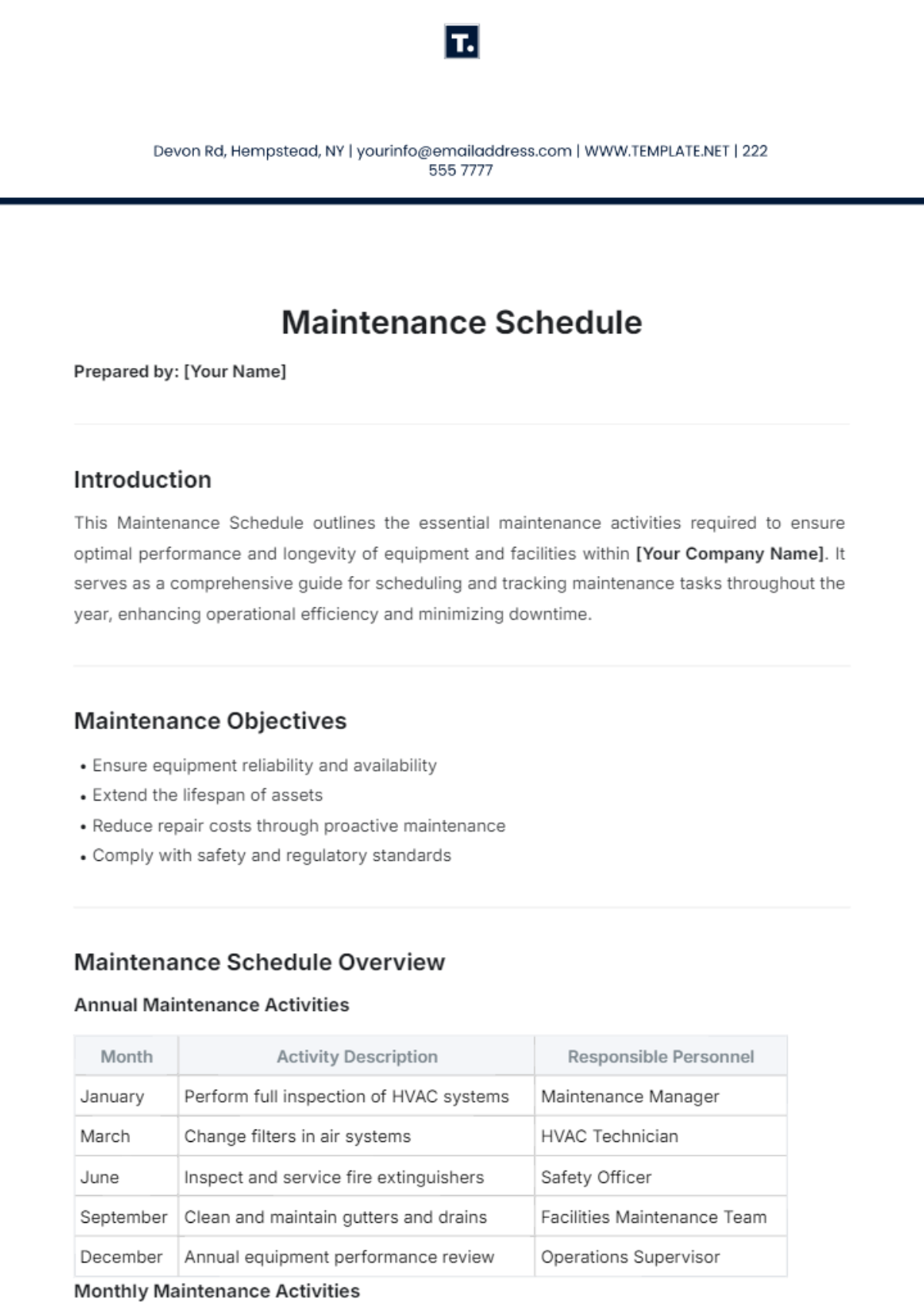
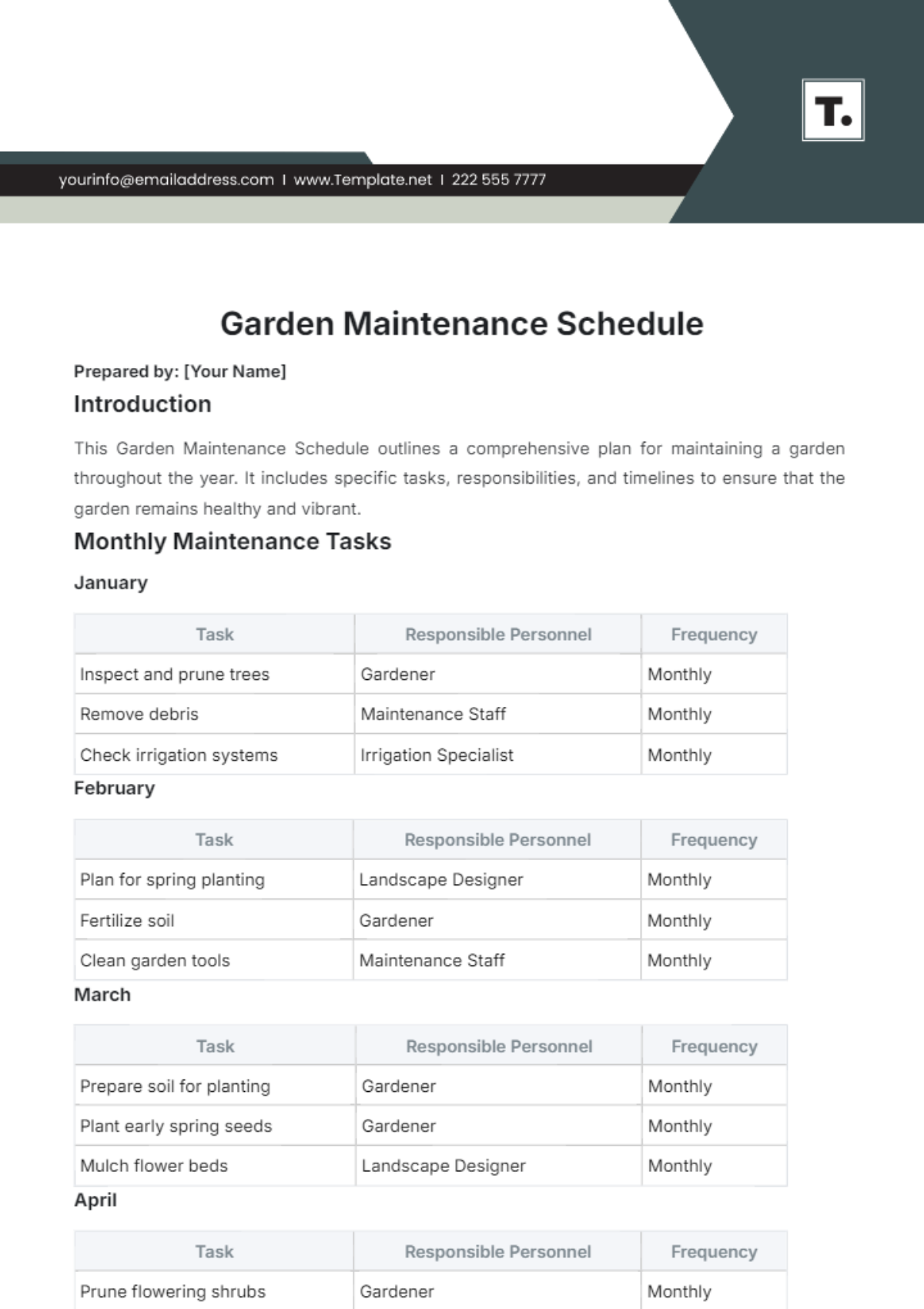
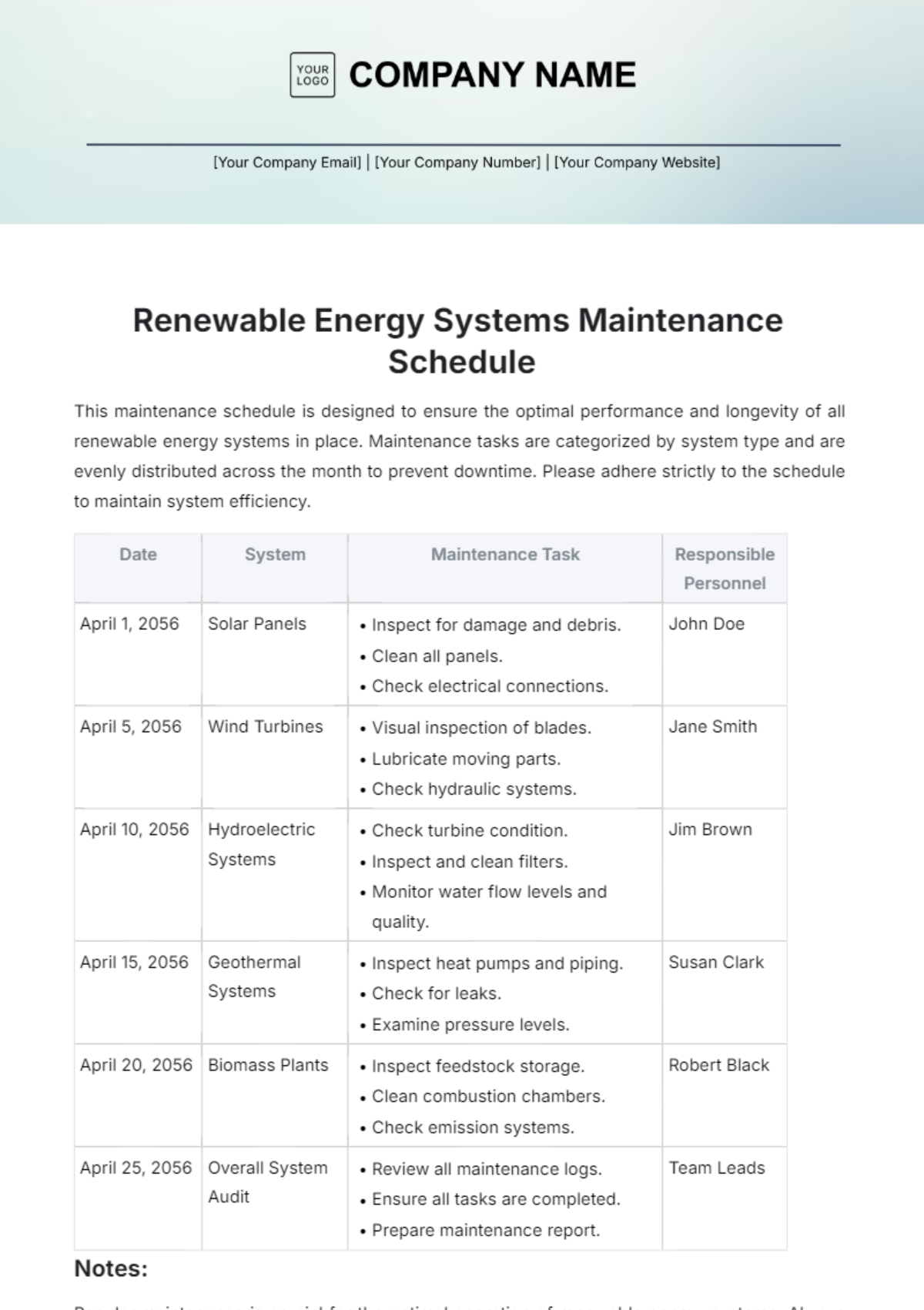
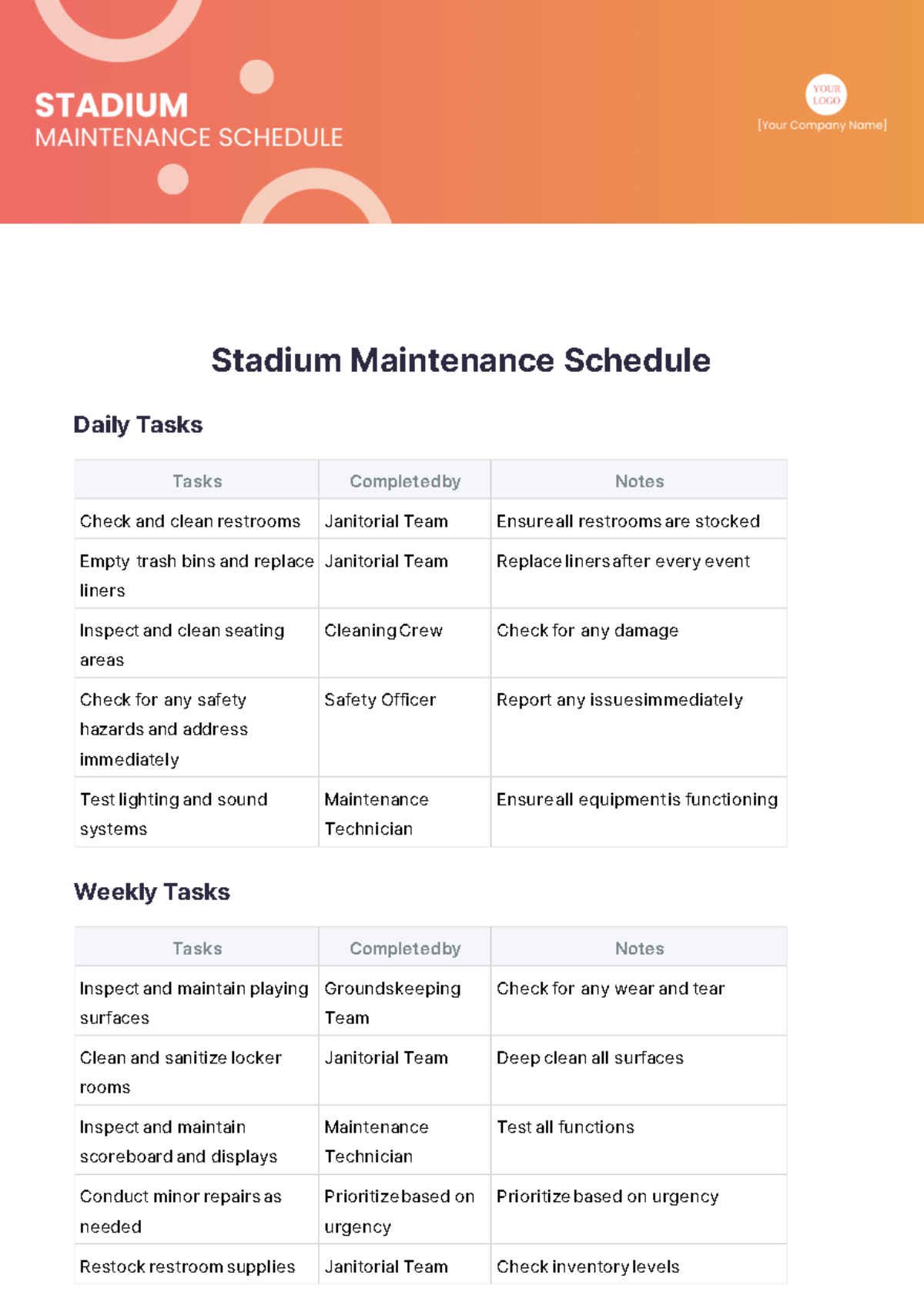
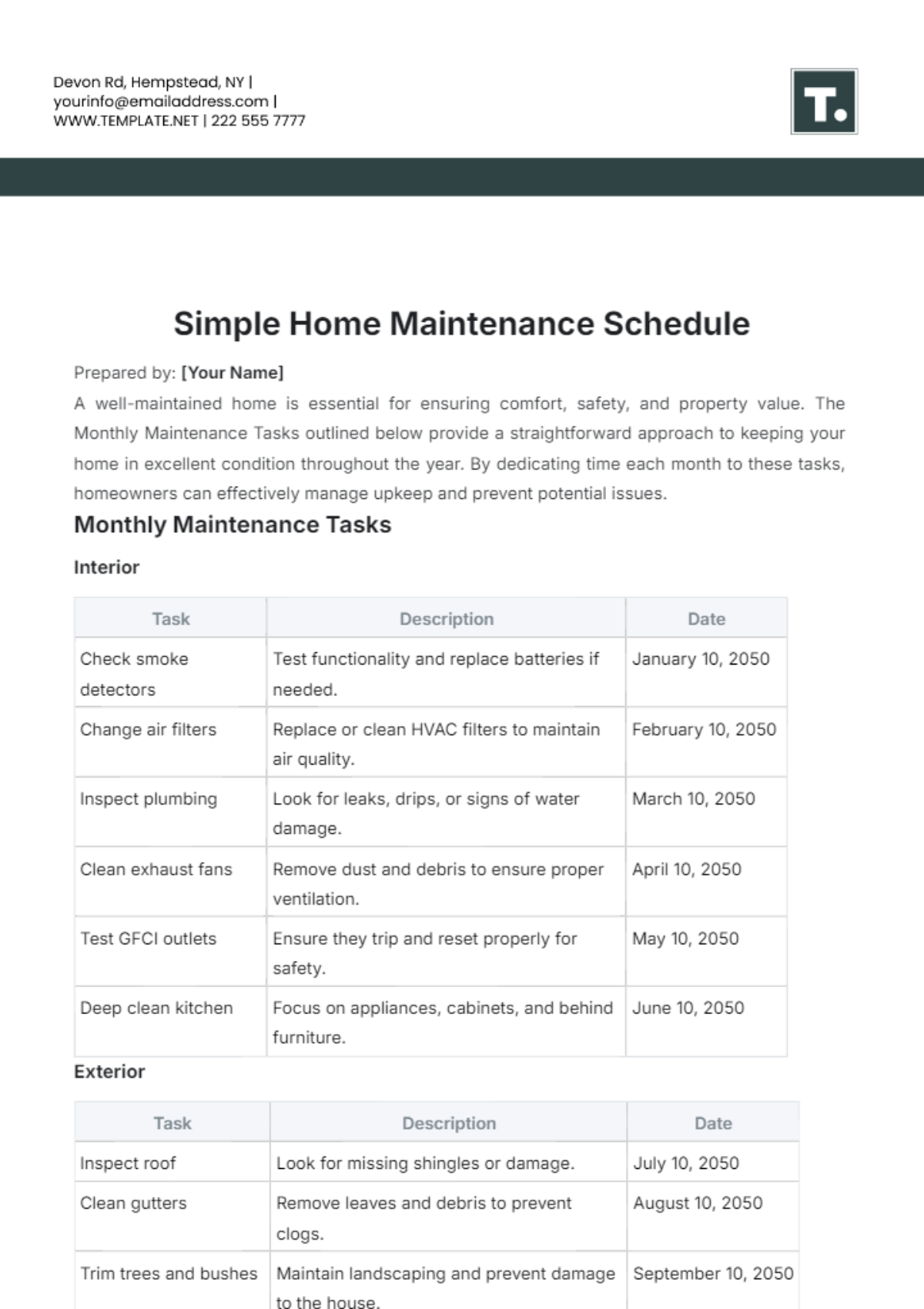
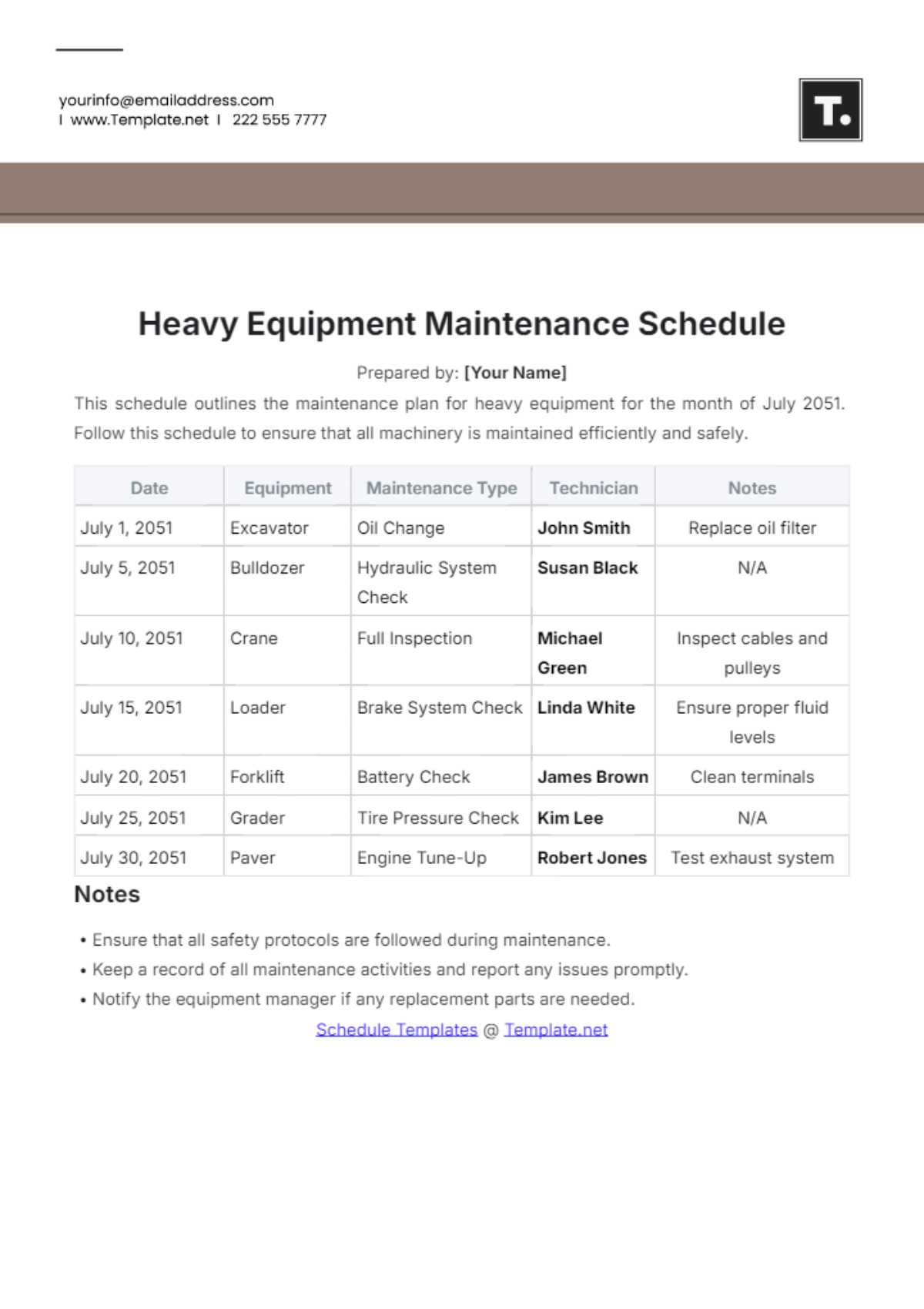
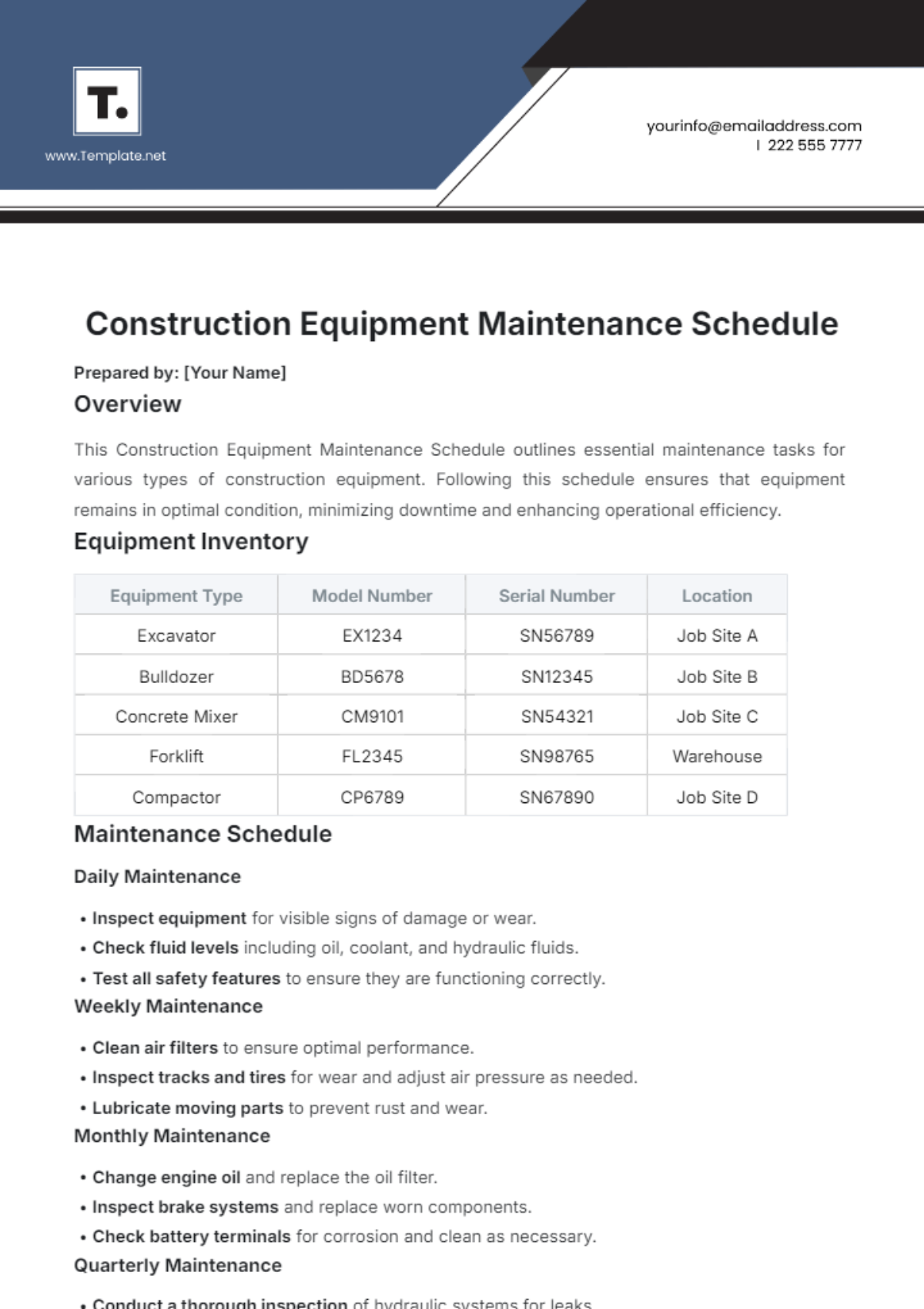
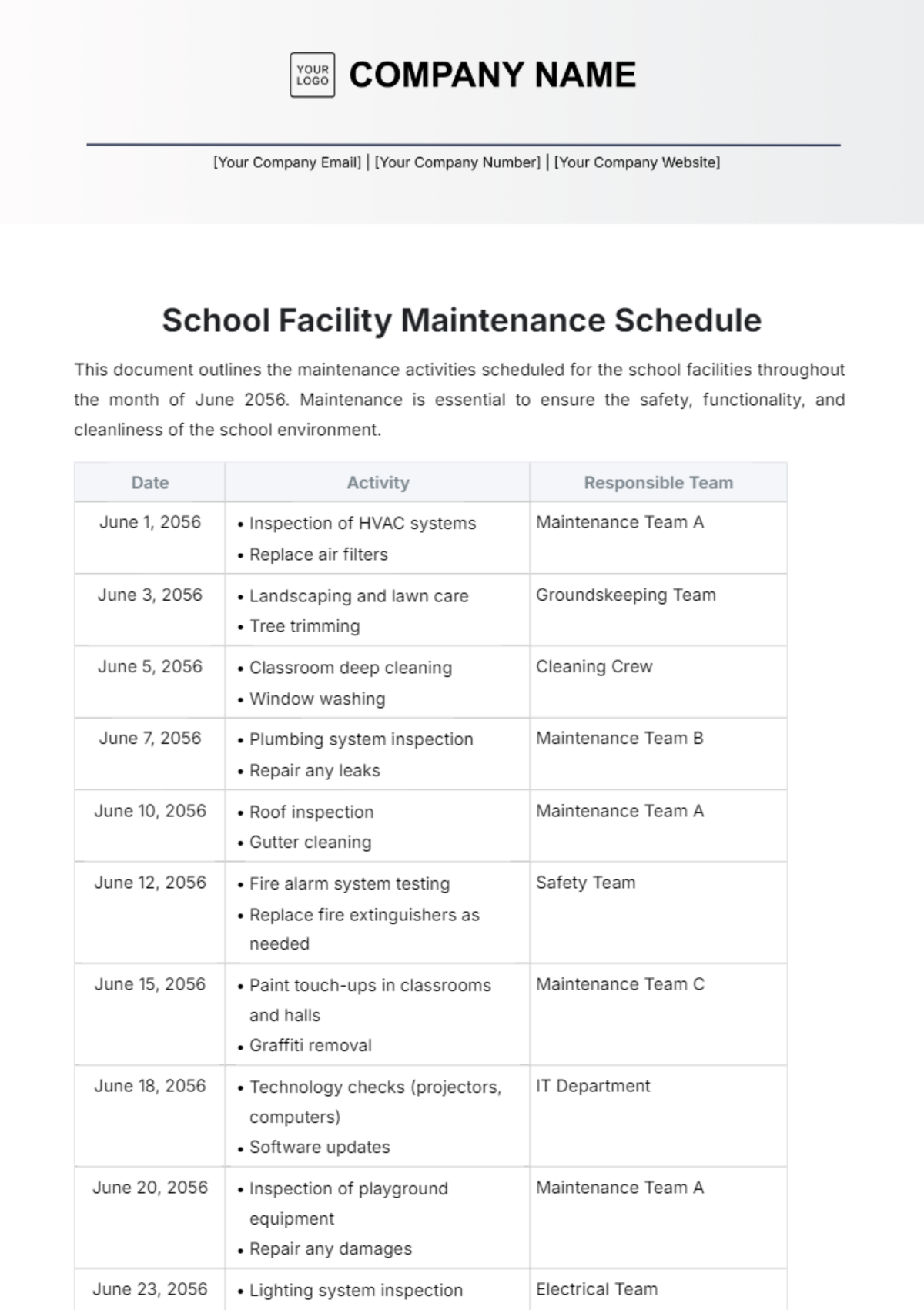
1. Daily Tasks
Section | Tasks | Next Scheduled Maintenance |
|---|---|---|
Routine Monitoring and Health Checks | Monitor network traffic and performance metrics using monitoring tools. | July 12, 2050, |
Identify and troubleshoot connectivity issues proactively. | ||
Review logs and alerts for security breaches or anomalies. |
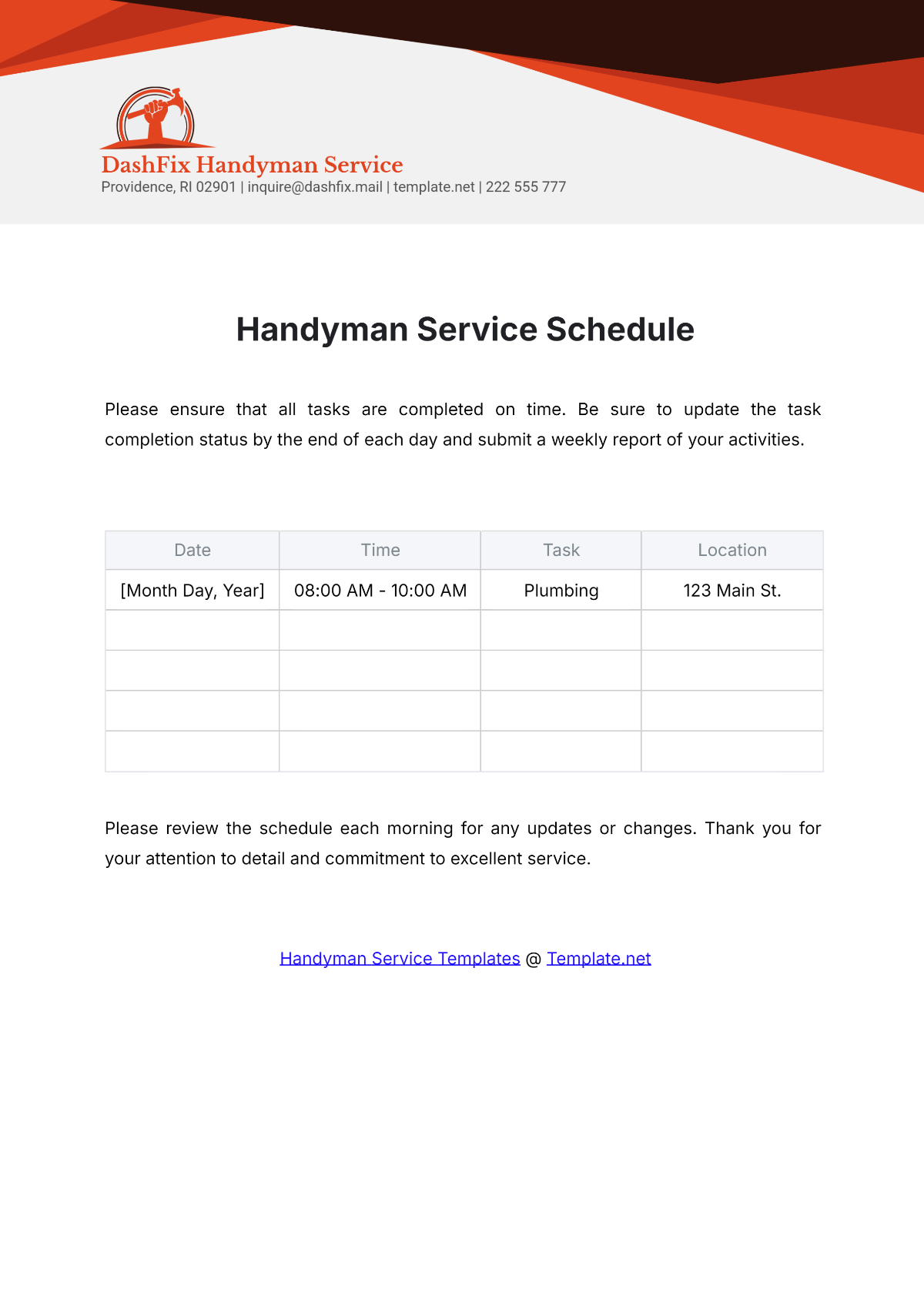
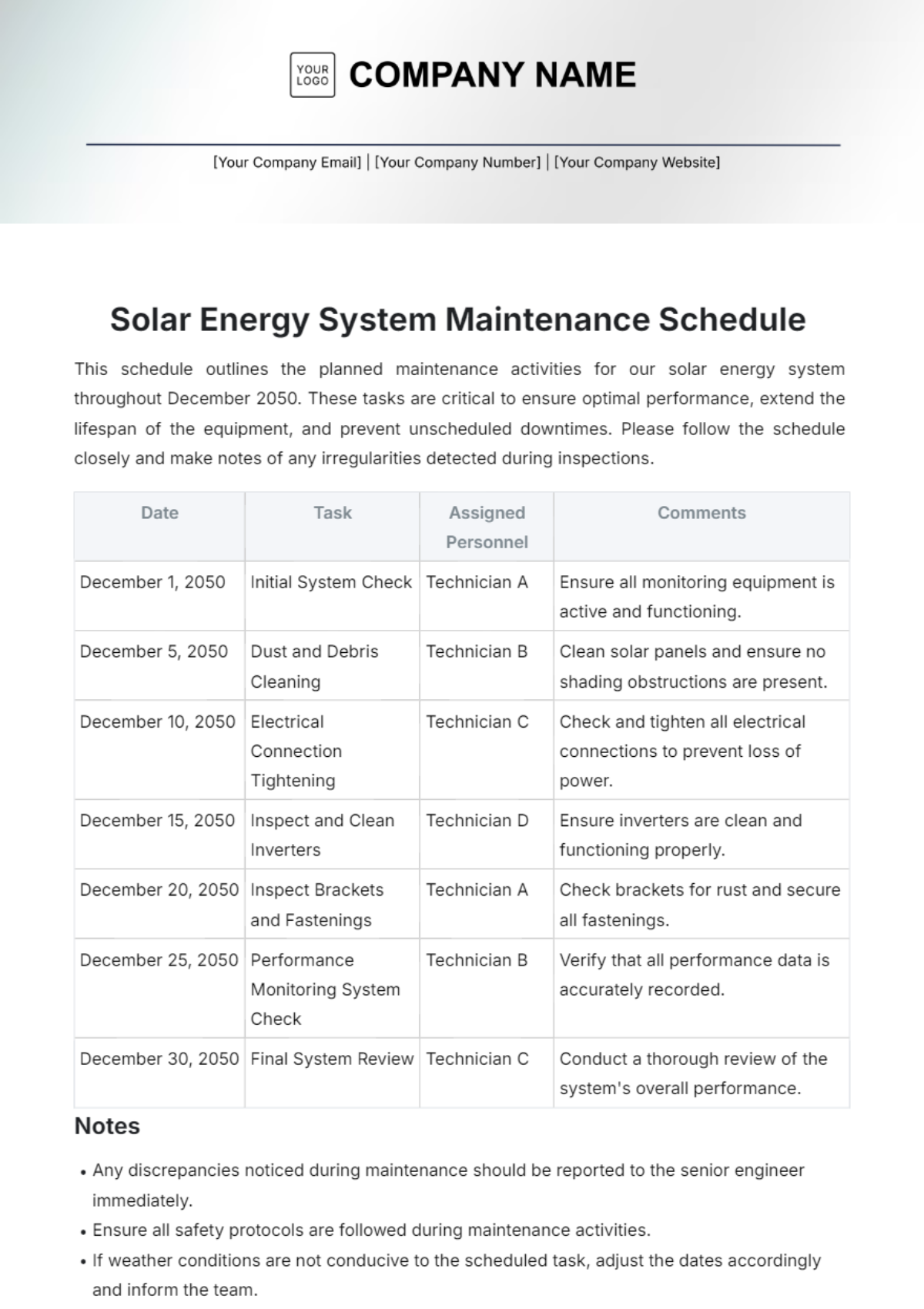
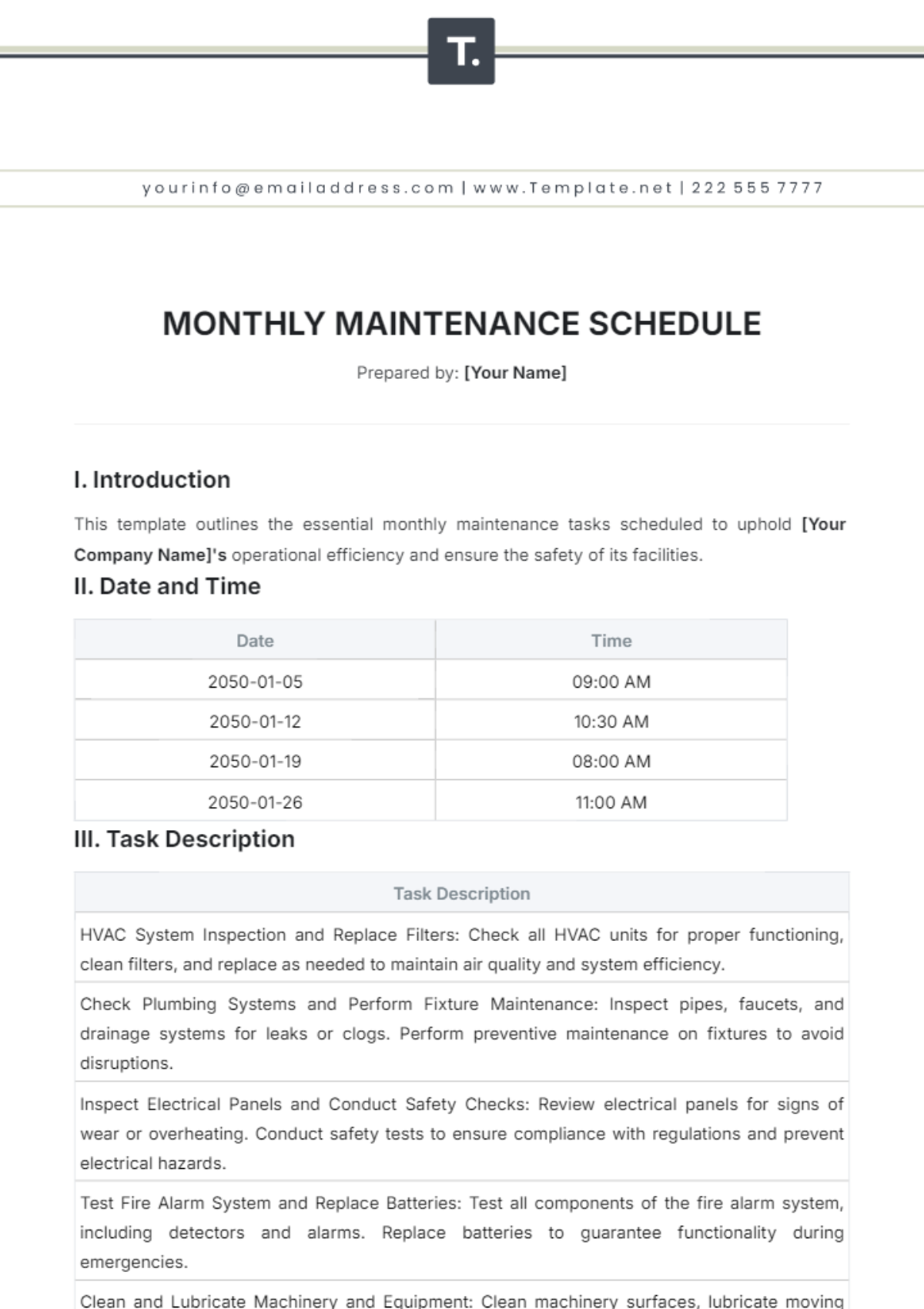
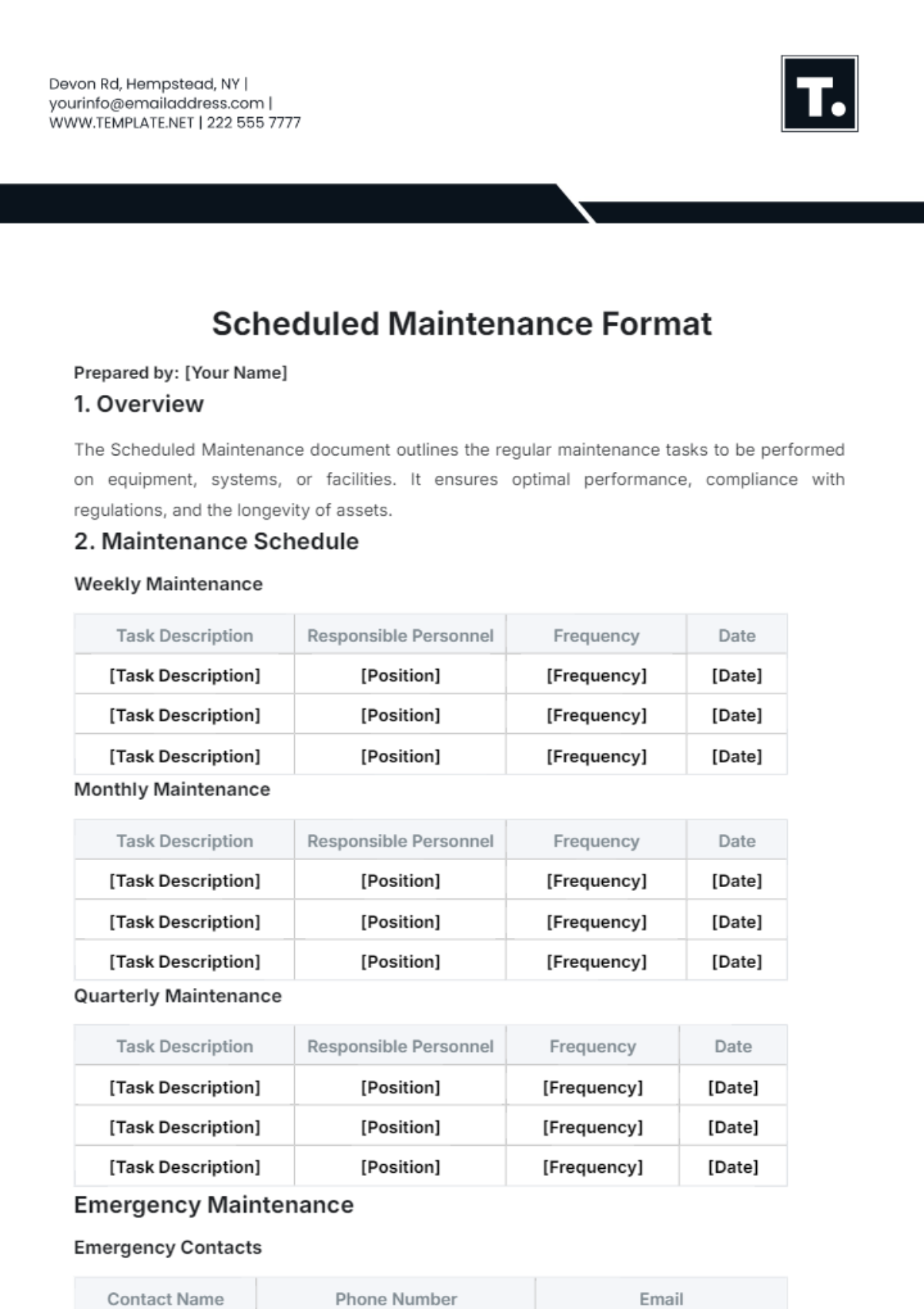
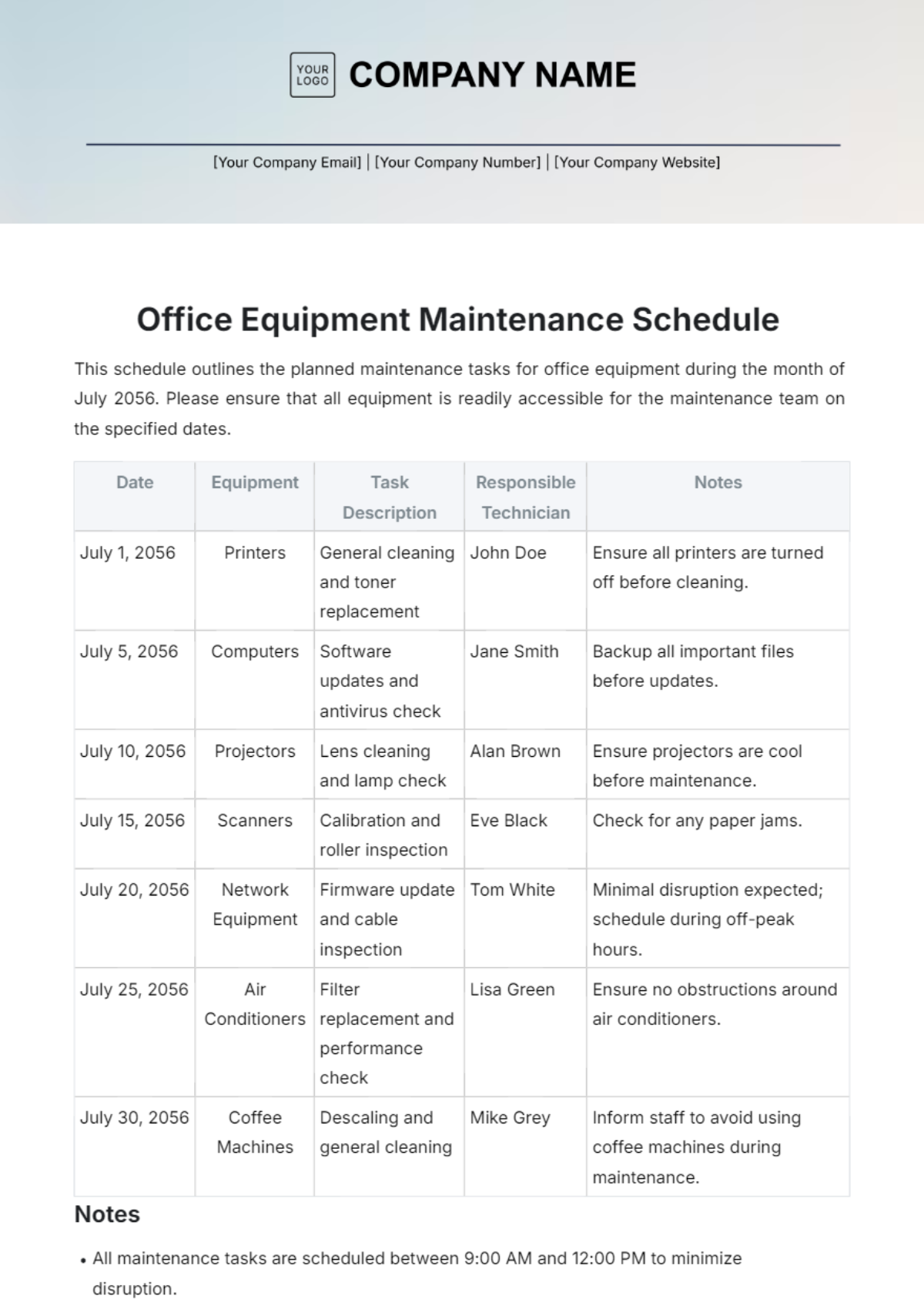
2. Weekly Tasks
Section | Tasks | Next Scheduled Maintenance |
|---|---|---|
Software Updates and Patch Management | Apply software updates to network devices and servers following a staged deployment process. | July 19, 2050, 10:00 PM |
Test patches in a controlled environment before full deployment. | ||
Schedule downtime and notify stakeholders for critical updates. |
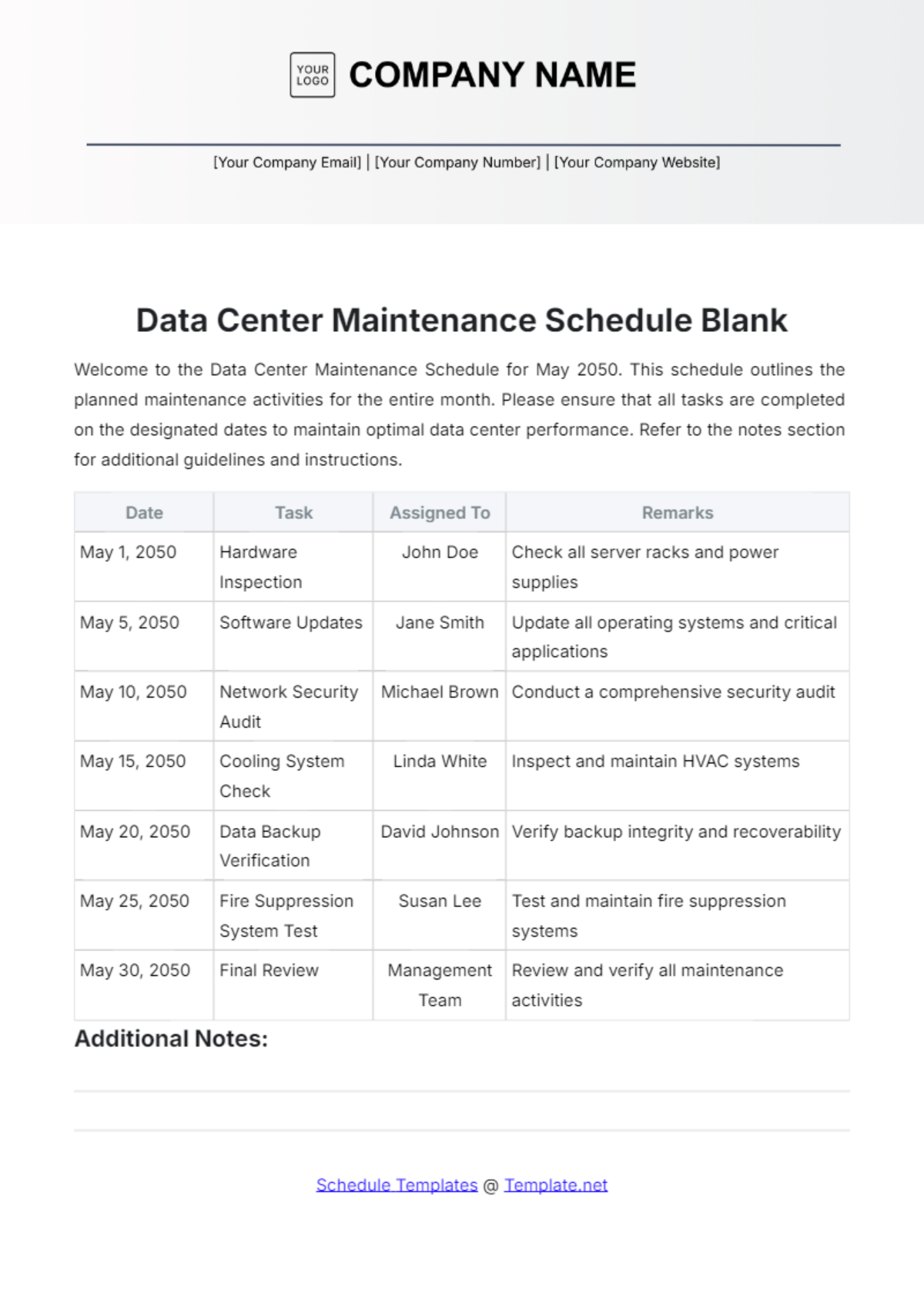
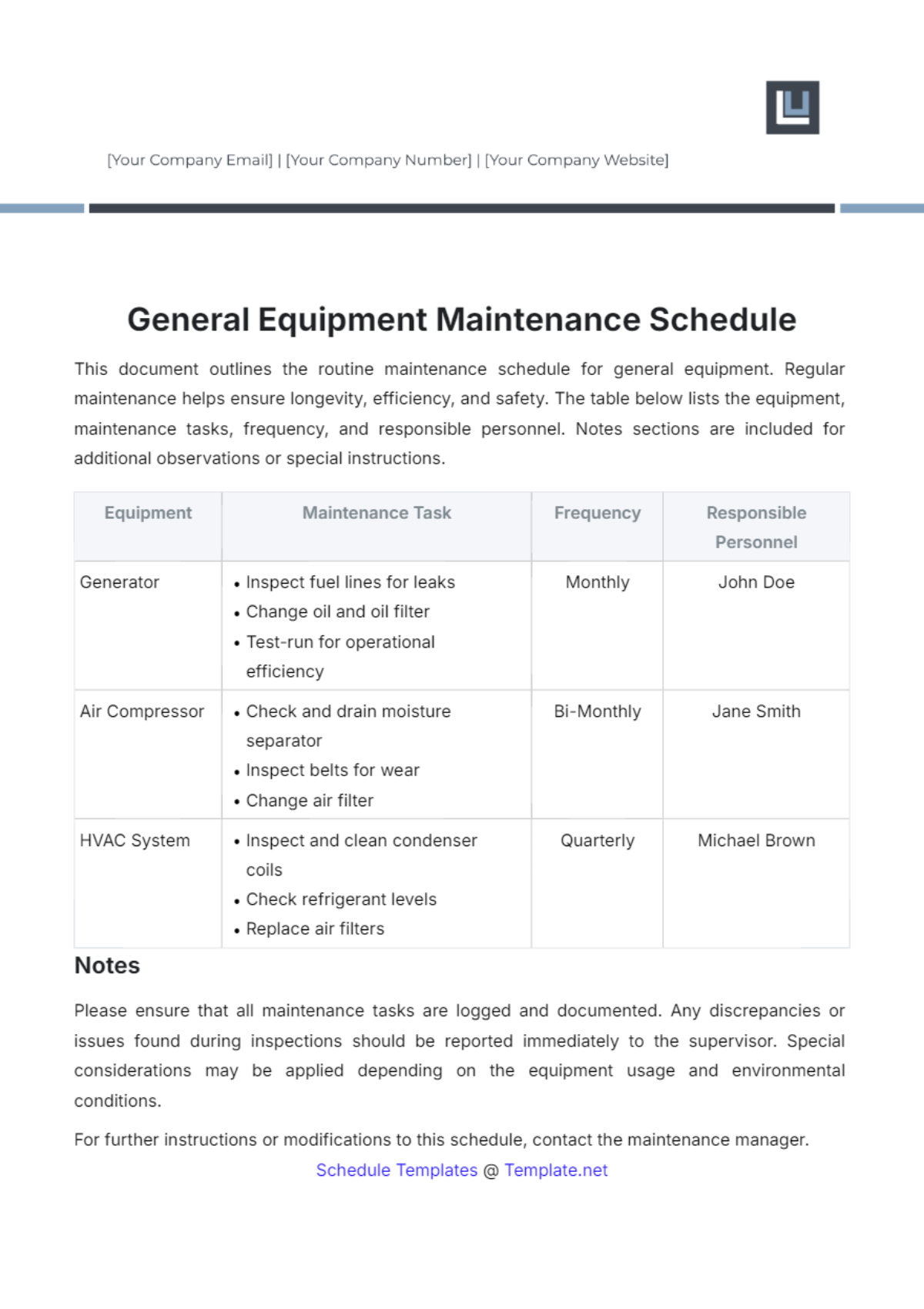
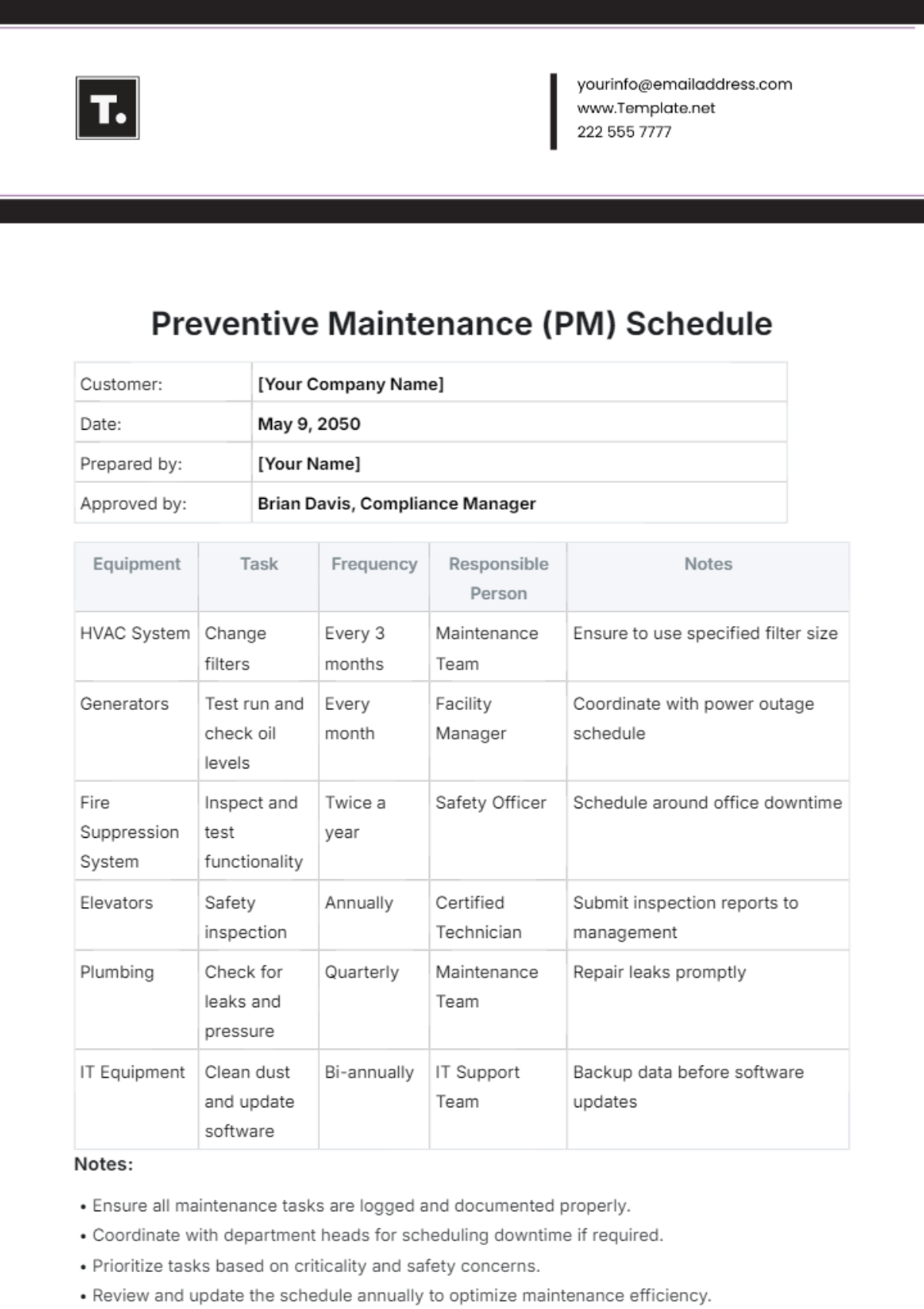
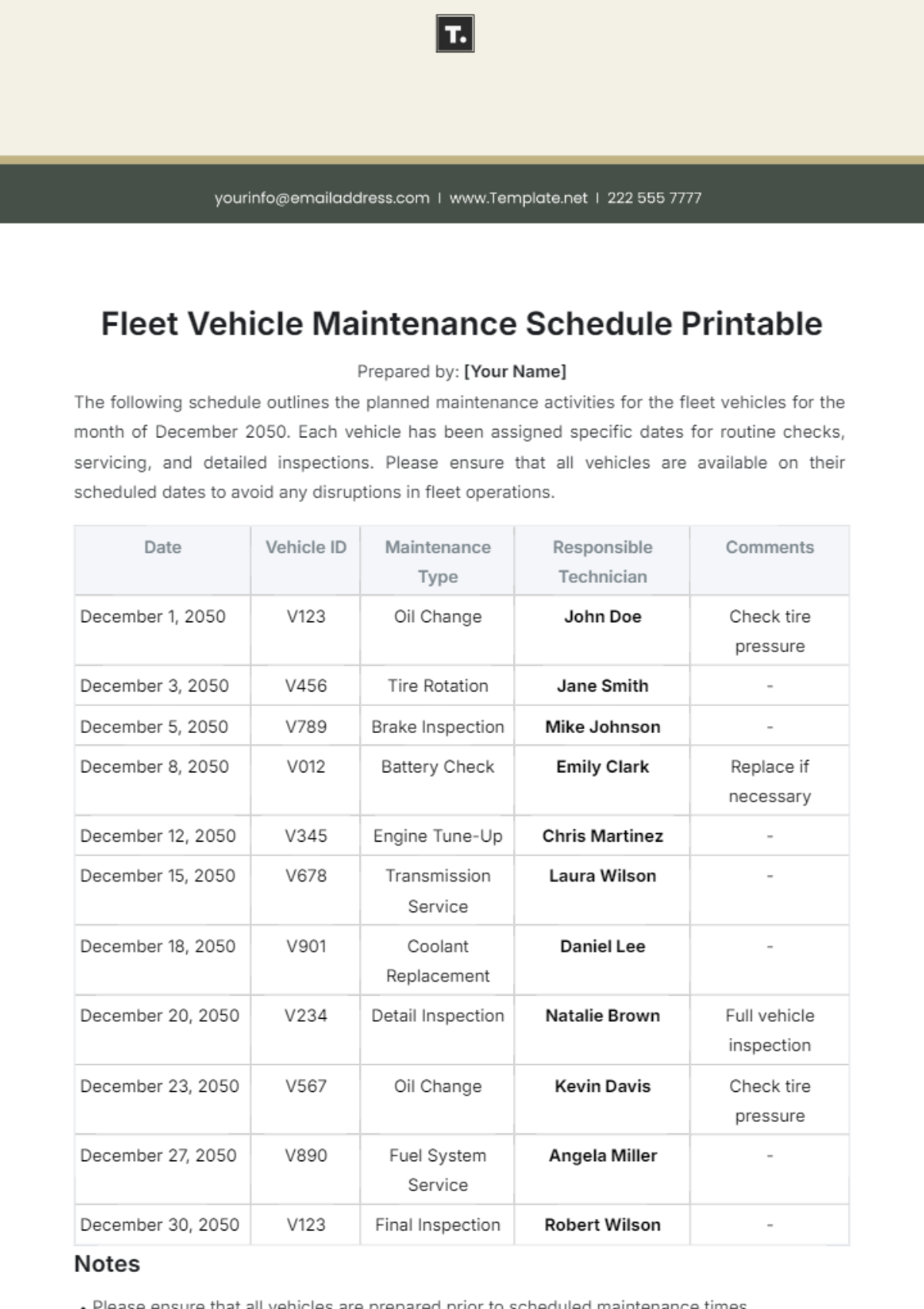
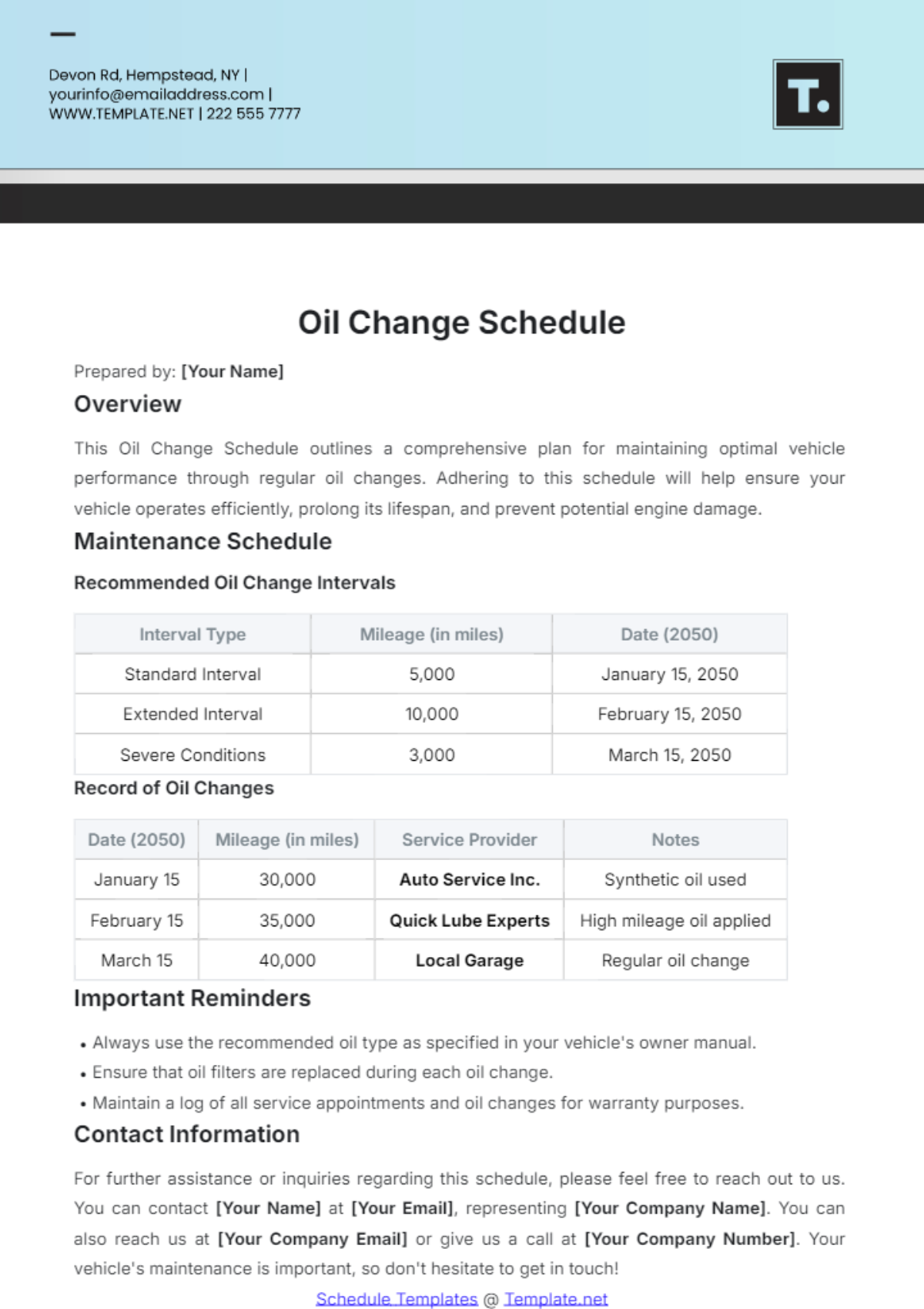
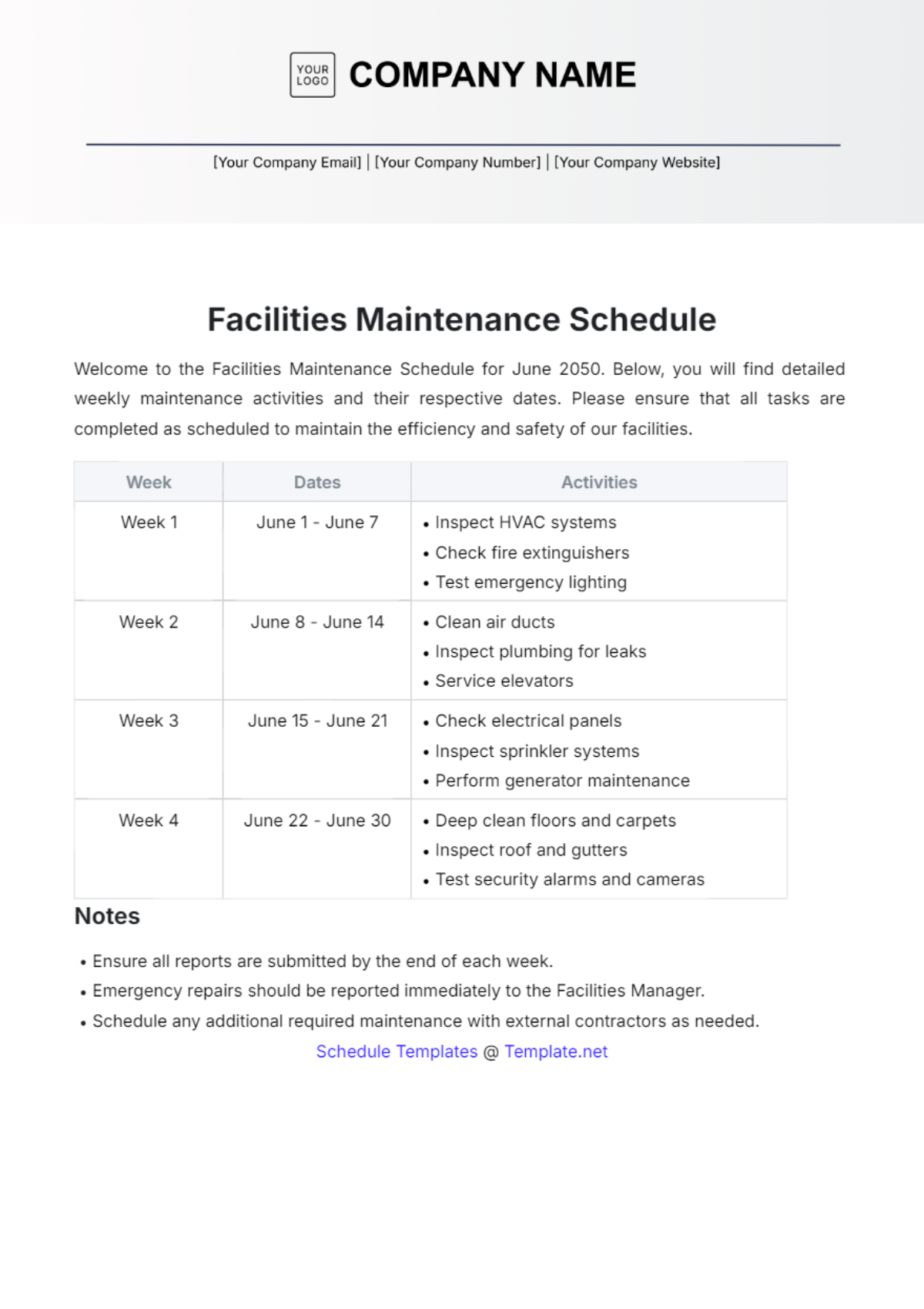
3. Monthly Tasks
Section | Tasks | Next Scheduled Maintenance |
|---|---|---|
Backup and Disaster Recovery | Perform regular backups of network configurations, data, and critical systems. | August 1, 2050, 12:00 AM |
Test backup integrity and restoration procedures to ensure reliability. | ||
Update disaster recovery plans based on testing results and evolving threats. |
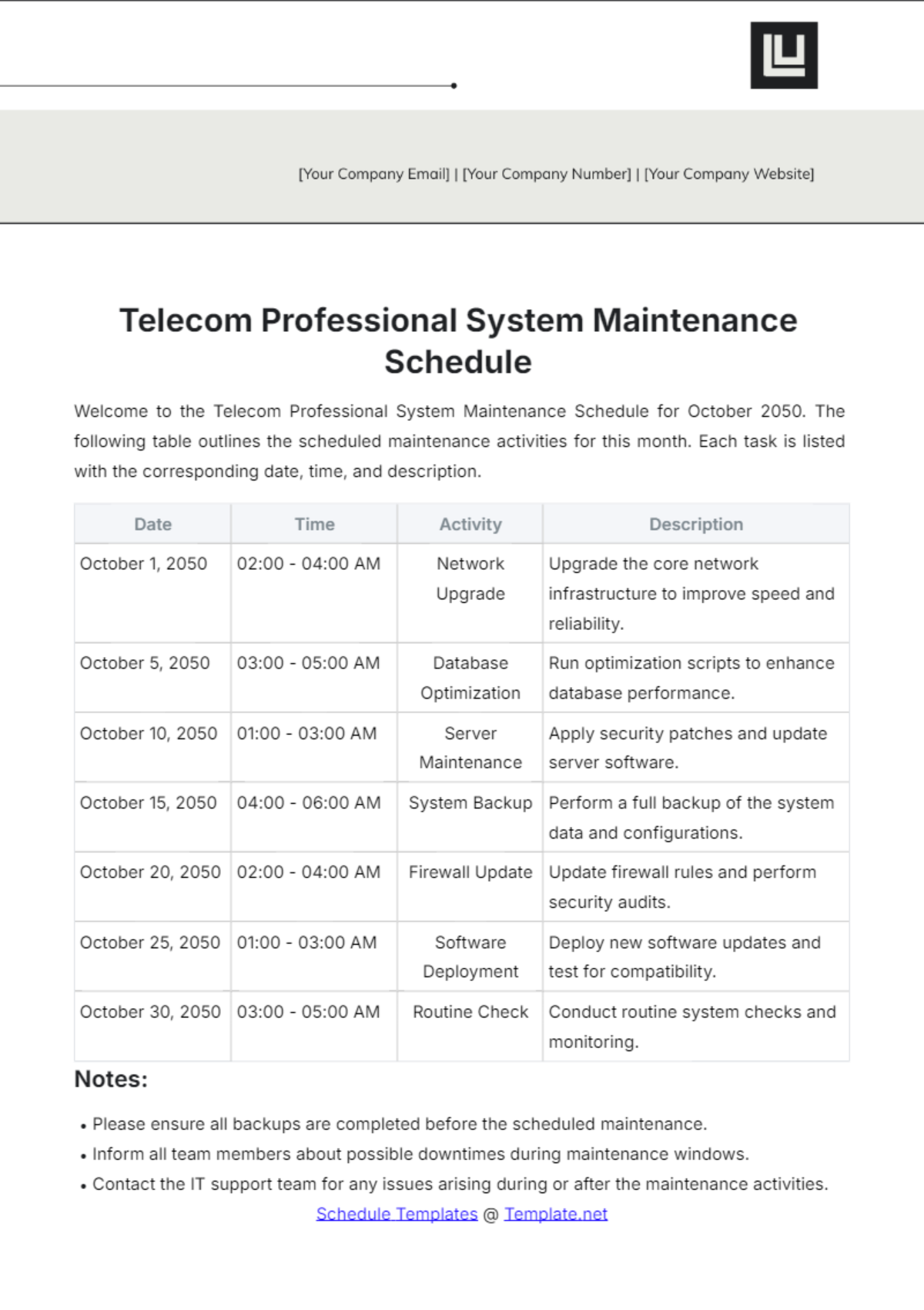
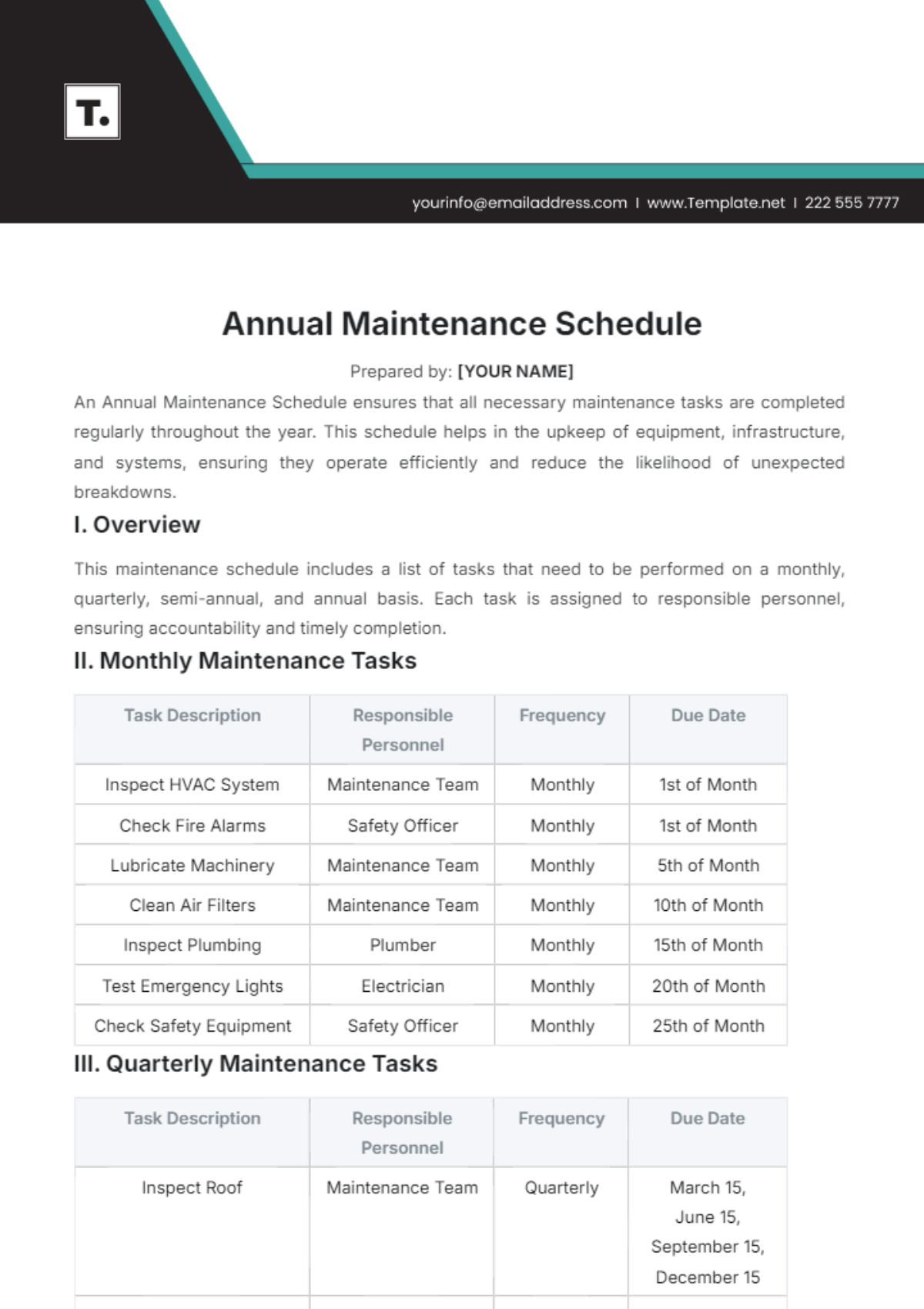
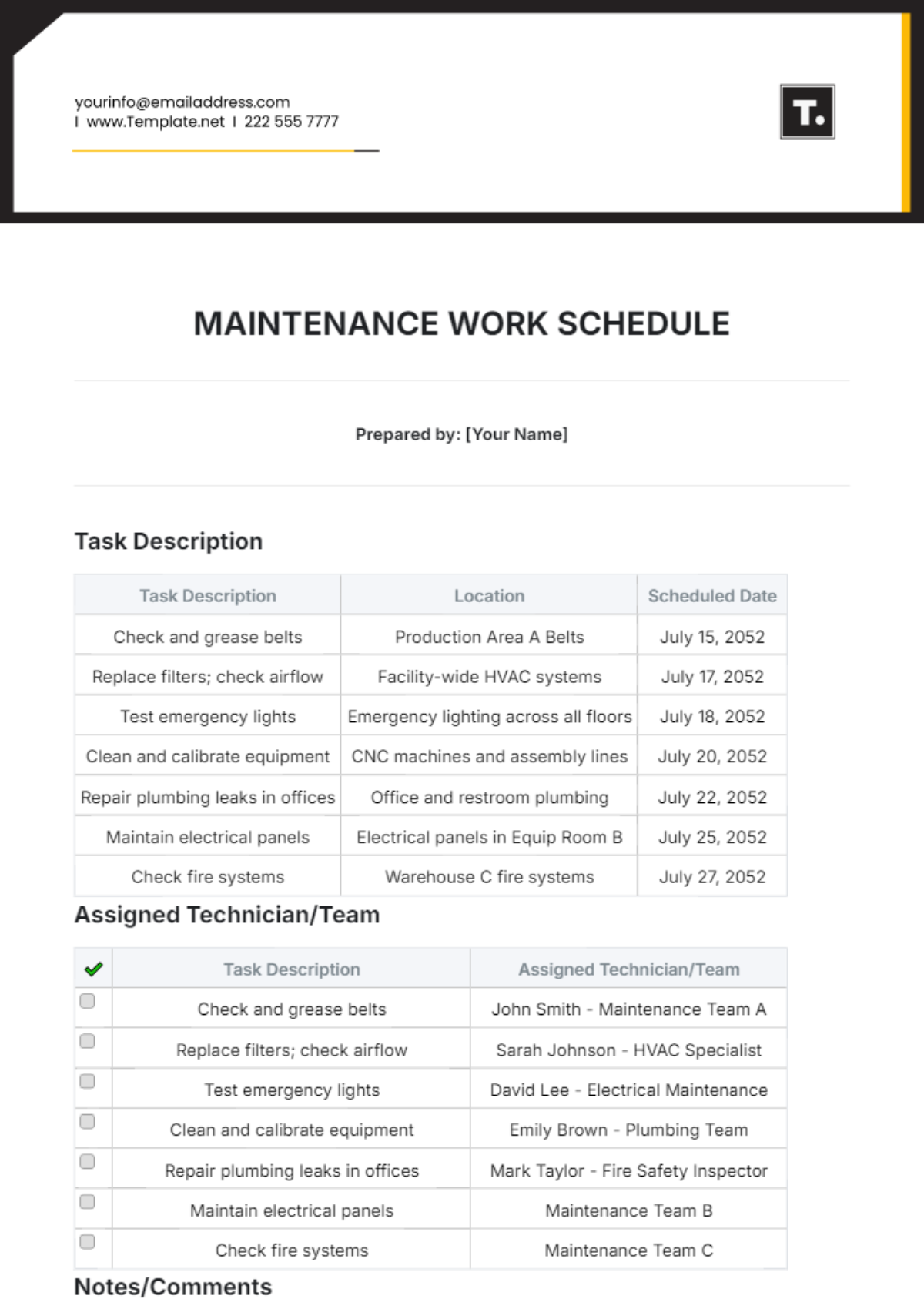
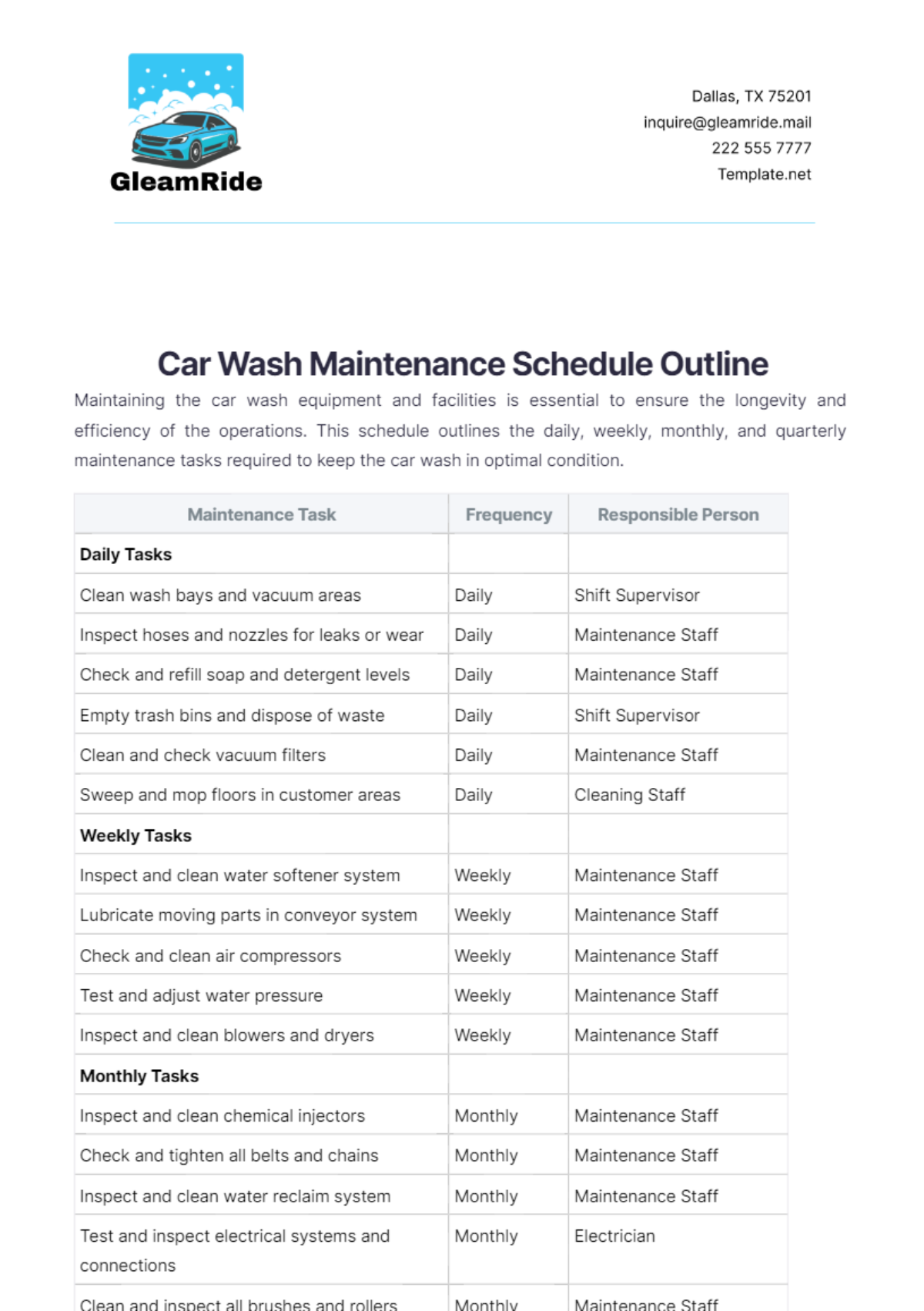
4. Quarterly Tasks
Section | Tasks | Next Scheduled Maintenance |
|---|---|---|
Security Audits and Compliance | Conduct comprehensive security audits to assess network vulnerabilities. | October 1, 2050, 9:00 AM |
Implement security patches and policy updates based on audit findings. | ||
Ensure compliance with industry standards and regulations. |
5. Additional Notes
Maintain detailed documentation of network configurations, changes, and maintenance activities for audit and reference purposes.
Conduct regular training sessions to educate staff on network security best practices and emerging threats.
Regularly review and refine network maintenance processes and procedures to enhance efficiency and effectiveness.
Maintain open communication and strong relationships with vendors to ensure timely support and service delivery.
Perform regular risk assessments to identify potential vulnerabilities and implement proactive mitigation strategies.