Free IT Onboarding Checklist Template
Essential Onboarding Protocols
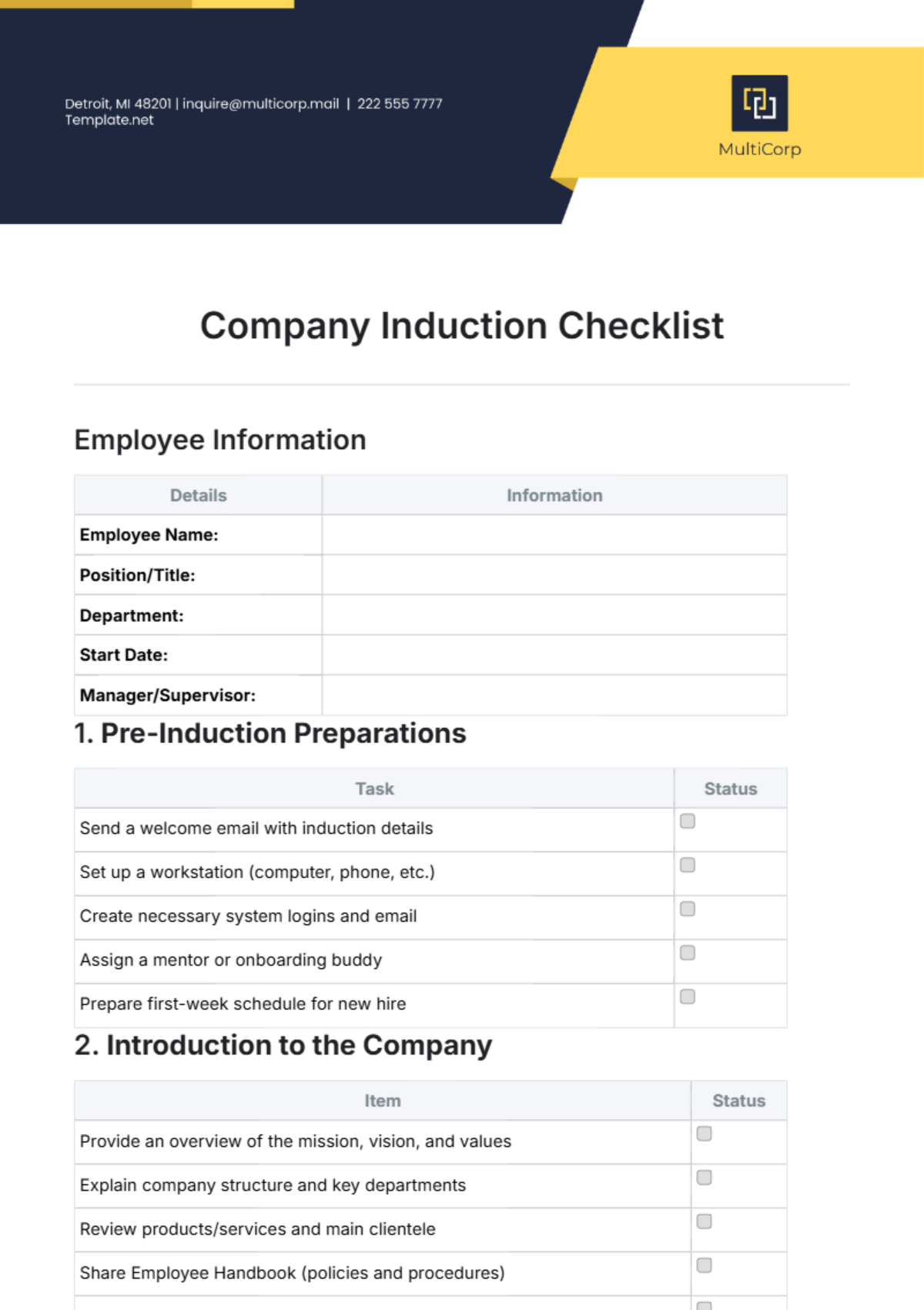
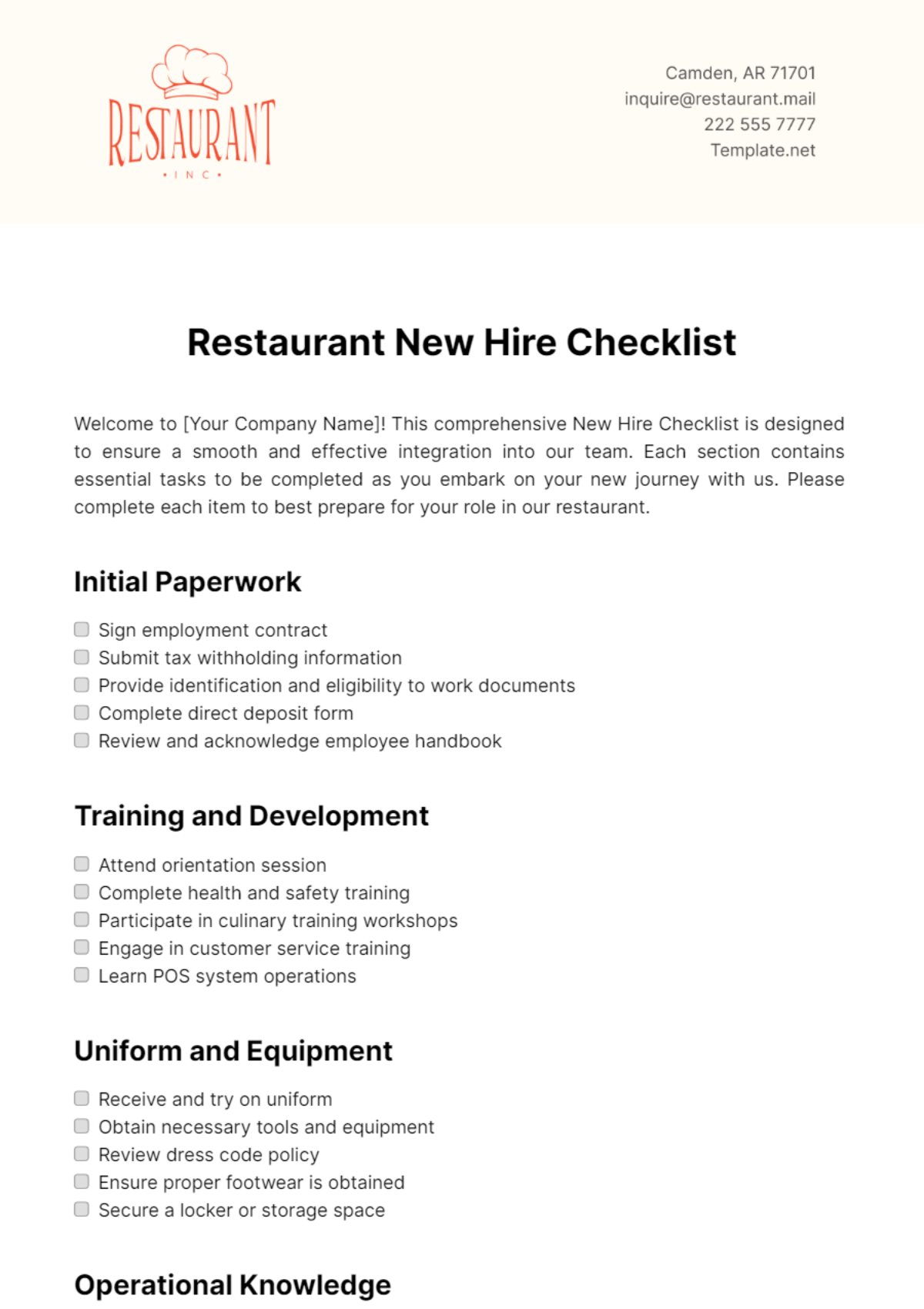
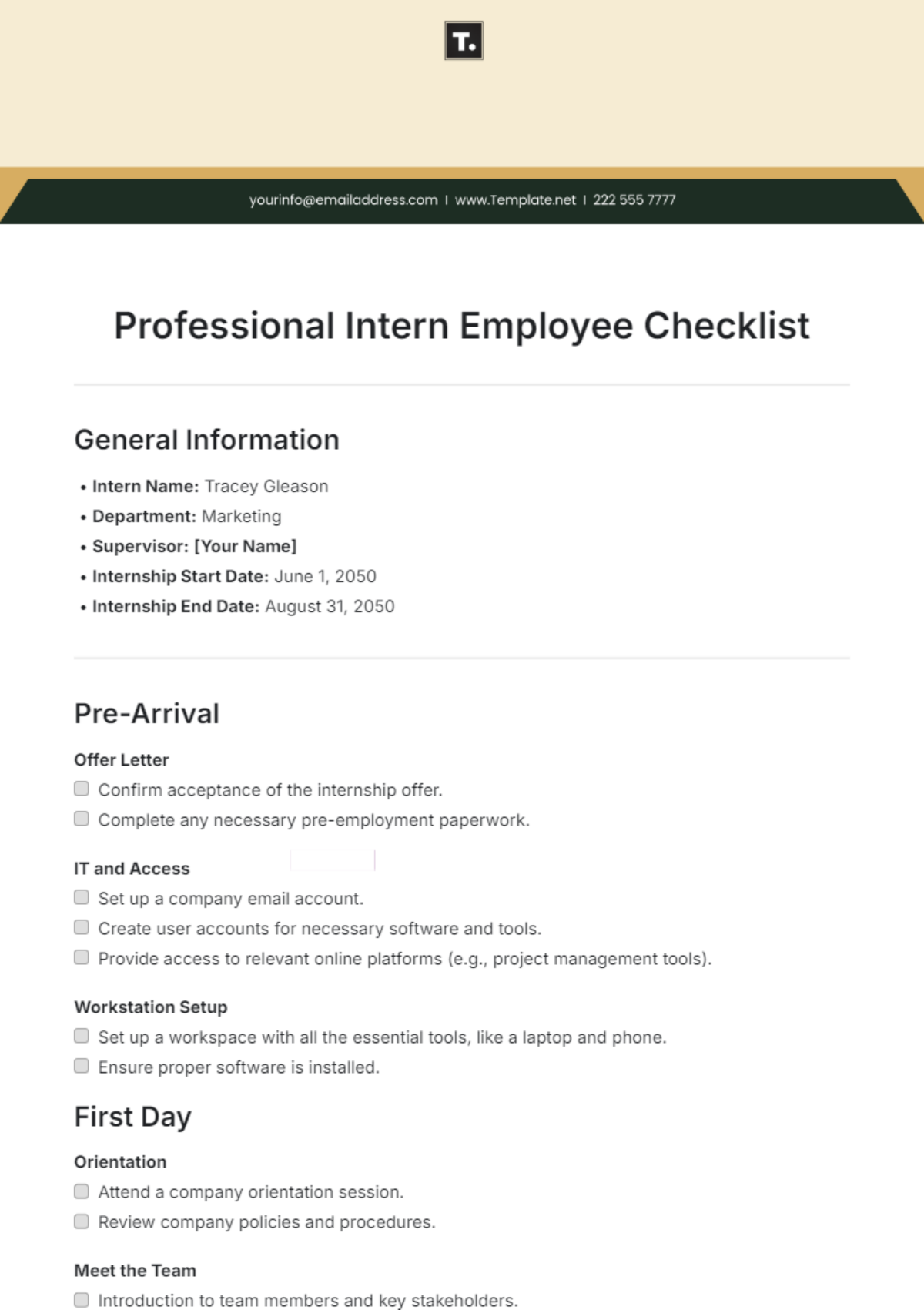
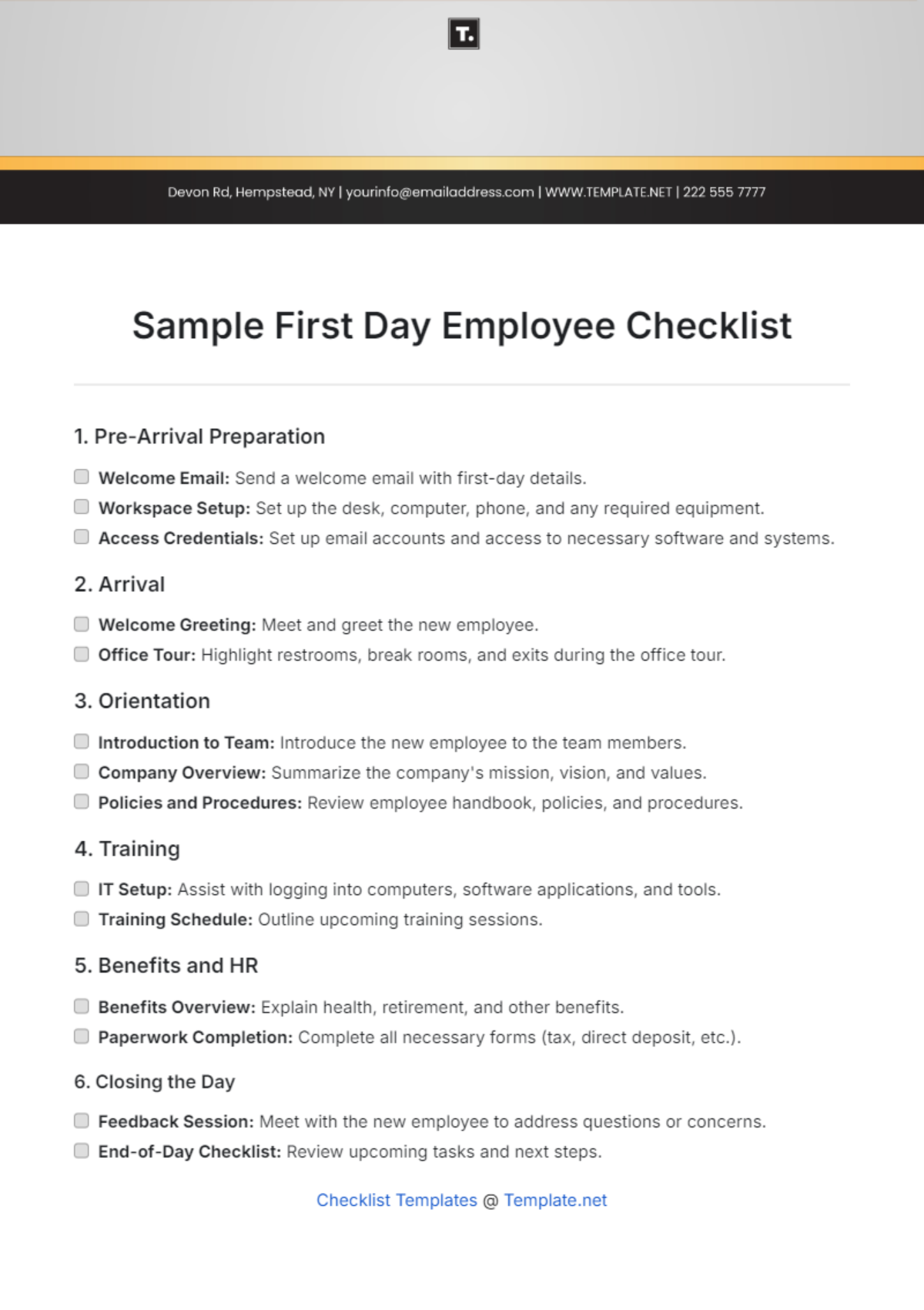
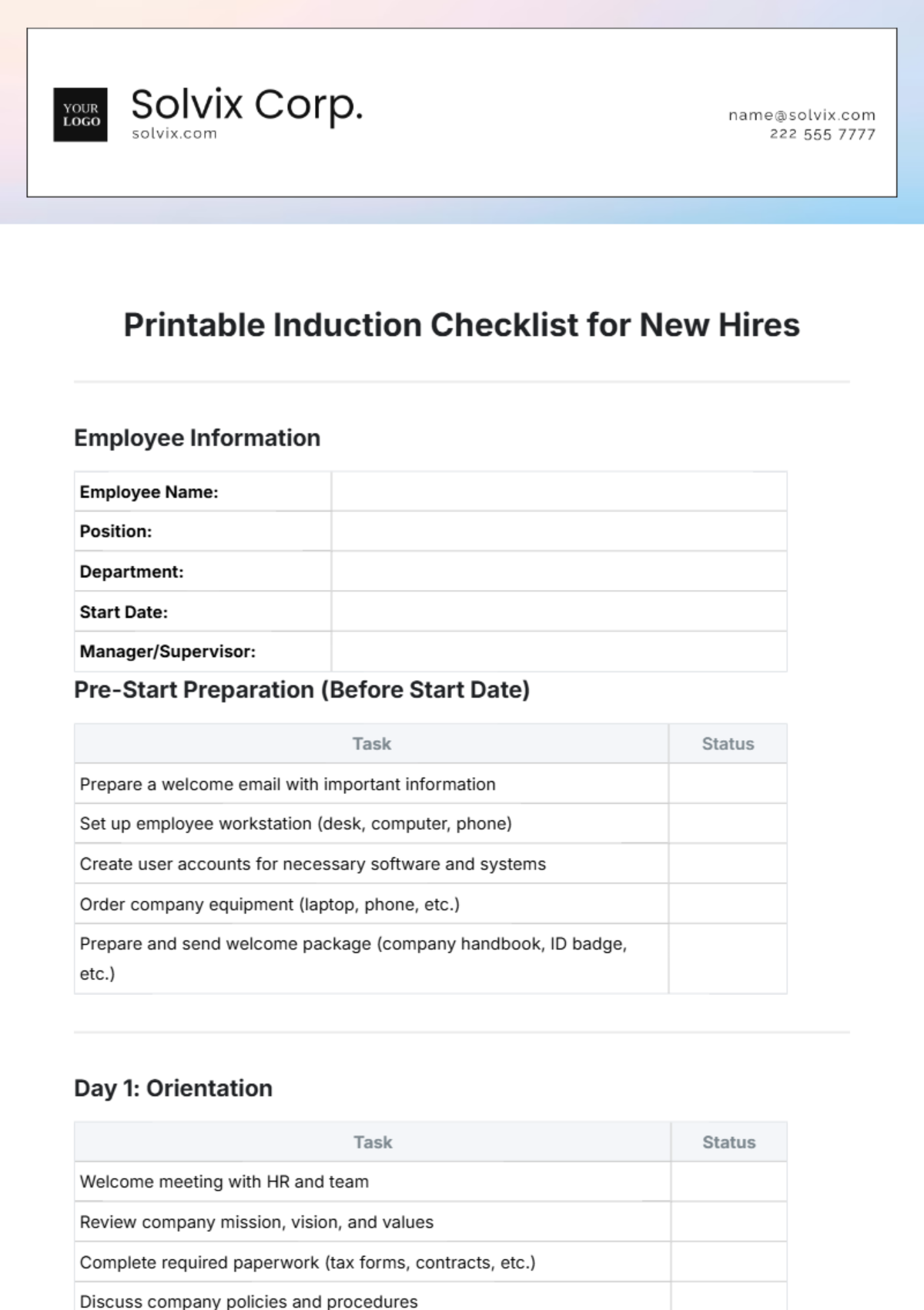
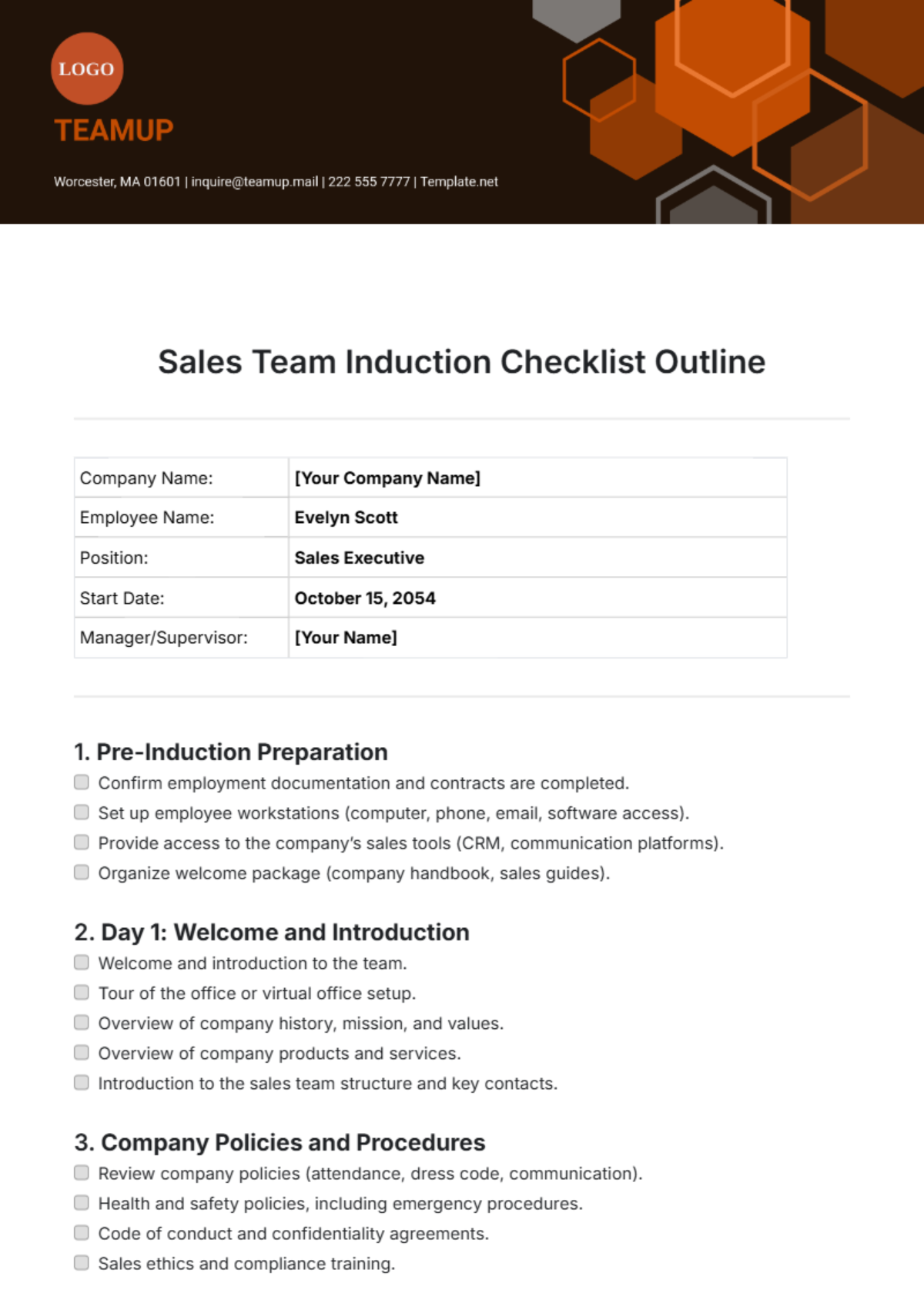
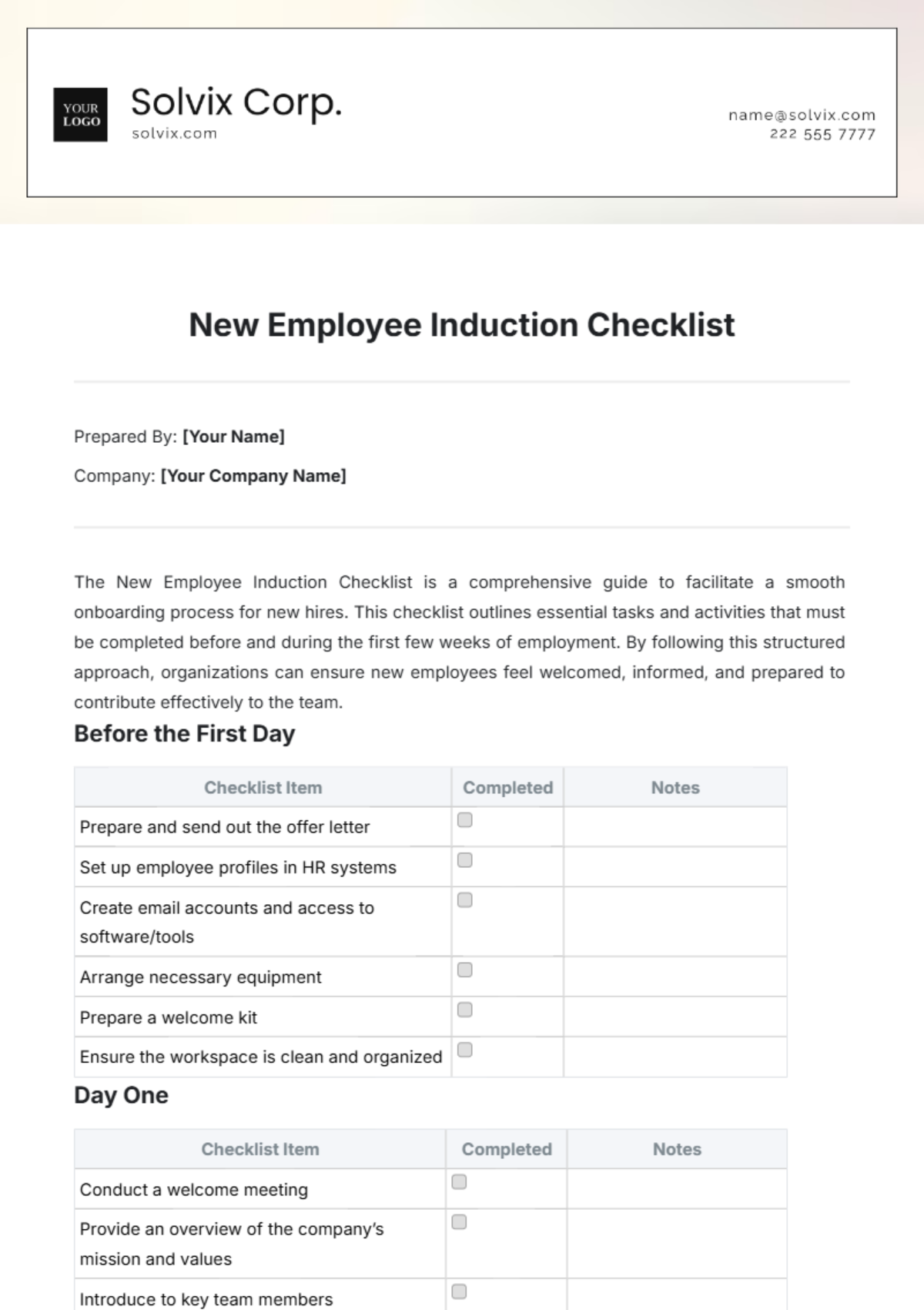
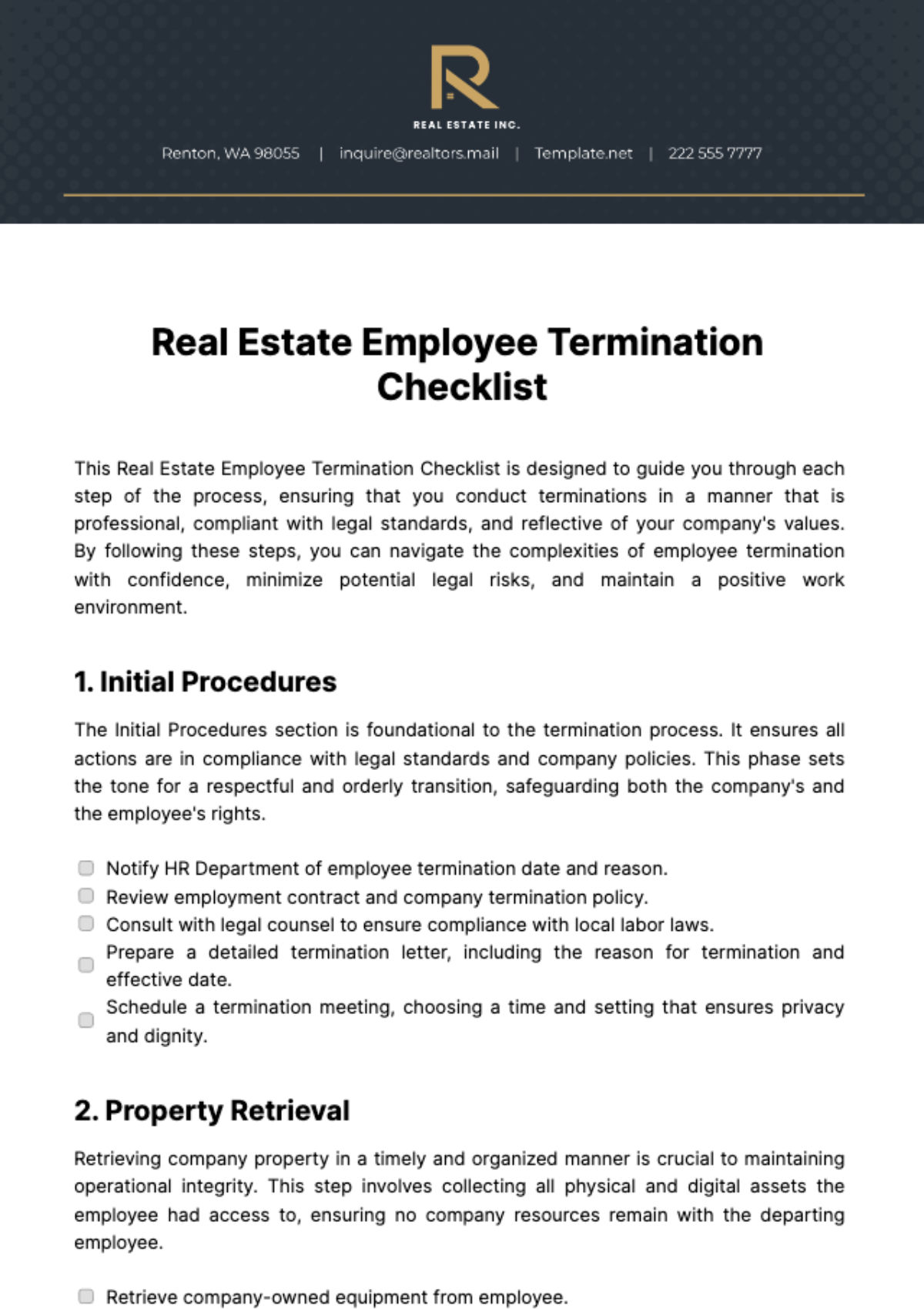
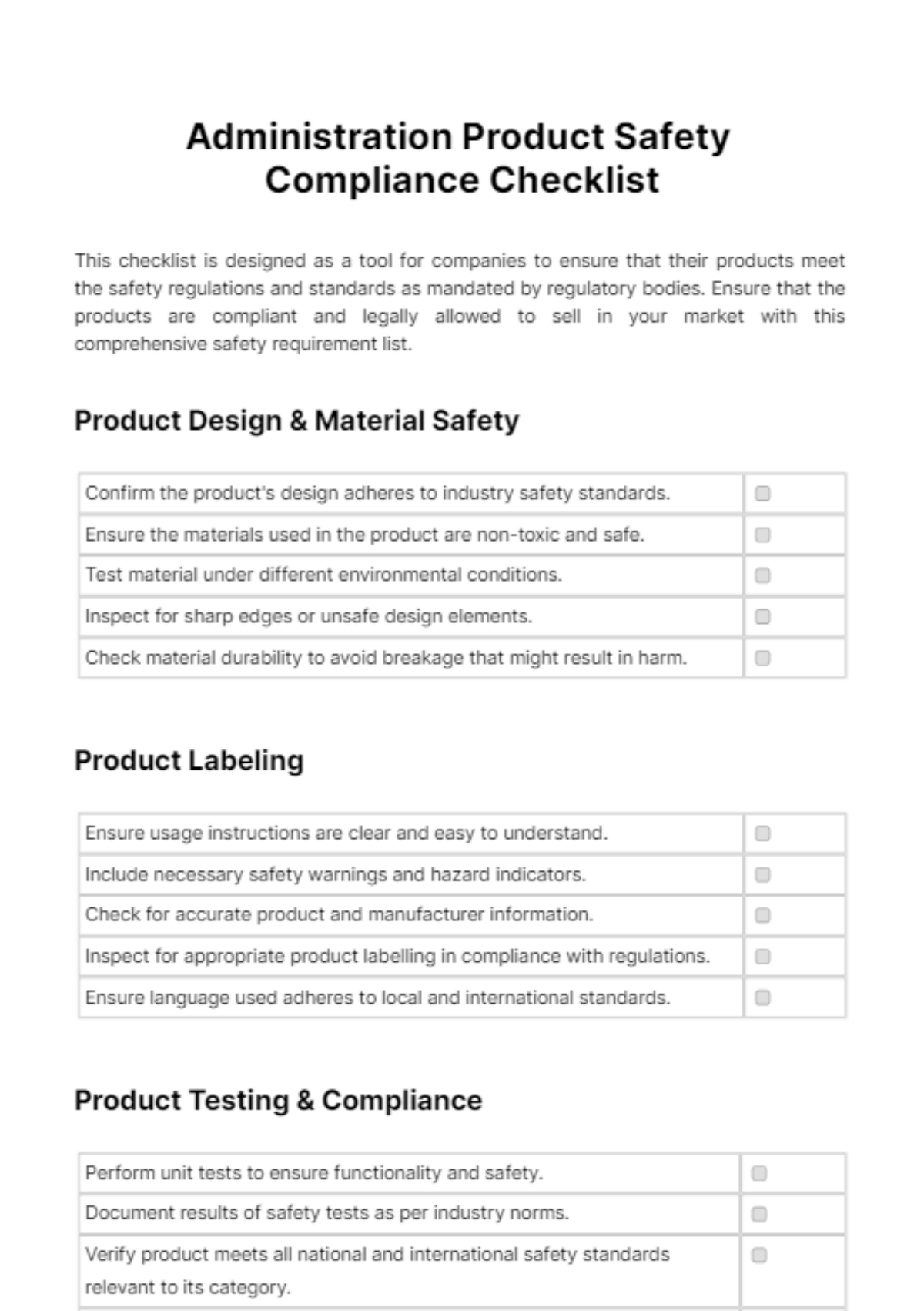
This comprehensive IT onboarding checklist aims to ensure a thorough integration of new employees into the organization's digital environment. By addressing hardware setup, software access, security protocols, and specialized training modules, the objective is to foster a secure, efficient, and knowledgeable workforce ready to contribute effectively from day one.
Hardware Setup
1. Check Physical Workstation:
Inspect cables for wear and tear.
Ensure proper ventilation for computer components.
Verify the functionality of peripherals (keyboard, mouse, etc.).
Confirm adequate desk space for comfortable working.
2. Setup Monitors and Screen Displays:
Adjust screen resolution for optimal clarity.
Configure multiple monitors, if applicable.
Test display settings to prevent eye strain.
Confirm the correct alignment of dual monitors.
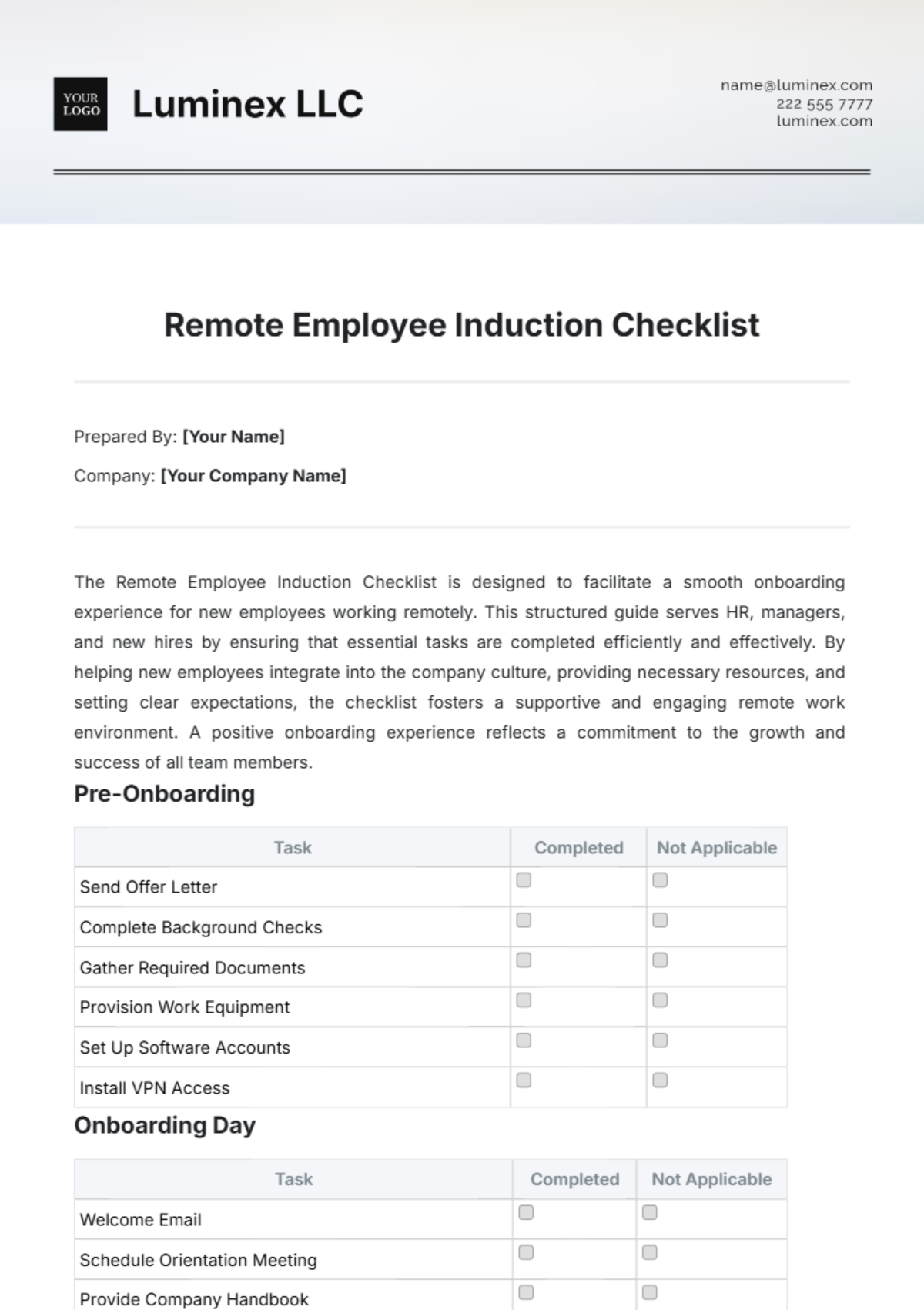
Software Access
1. Grant Access to Necessary Applications:
Assign specific roles and permissions based on job requirements.
Verify access to collaboration tools (email, messaging apps).
Ensure compatibility with industry-specific software.
Set up remote access tools, if applicable.
2. Install Essential Software:
Deploy standard office applications.
Install antivirus and security software.
Implement project management tools as needed.
Configure automatic updates for software maintenance.
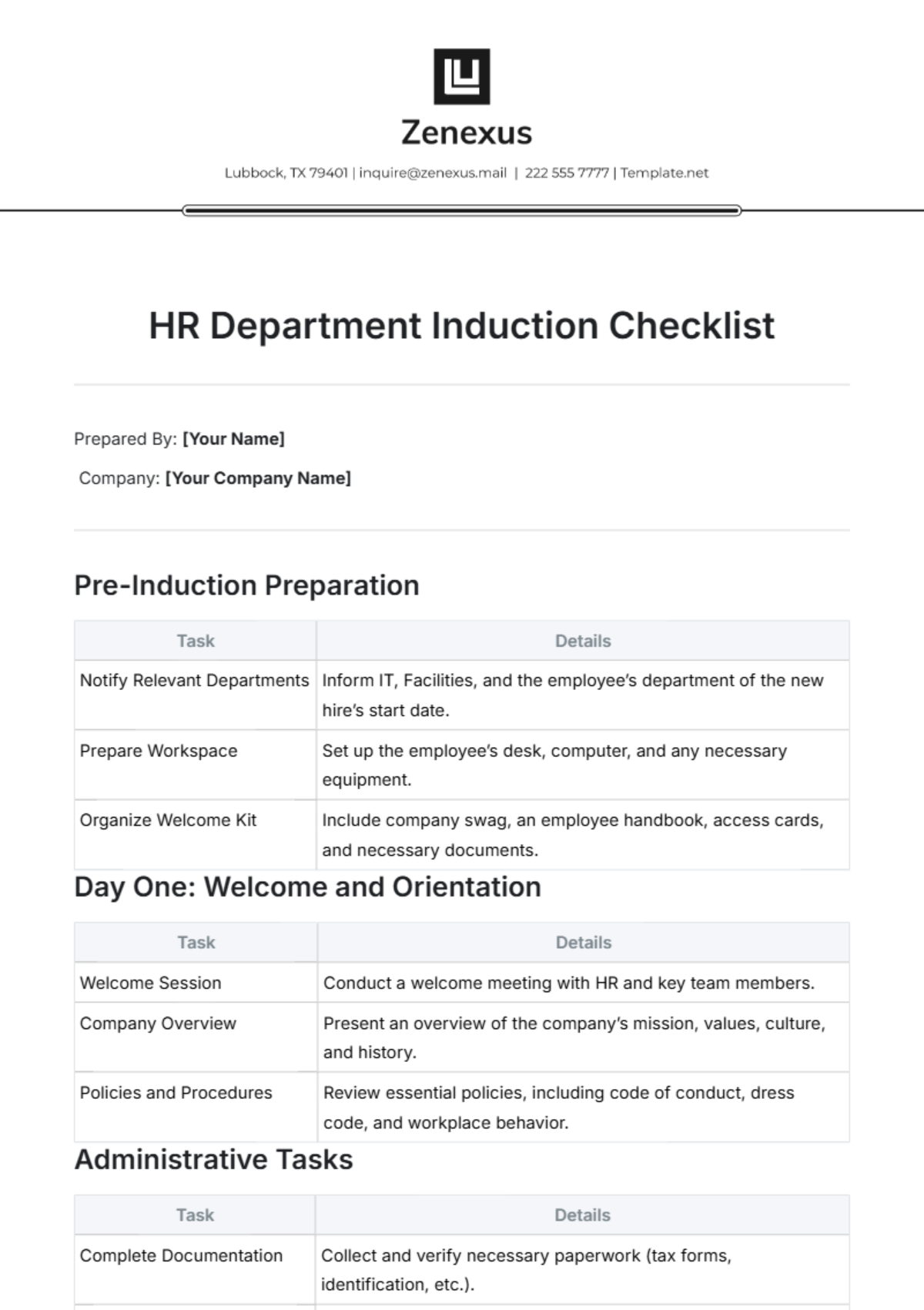
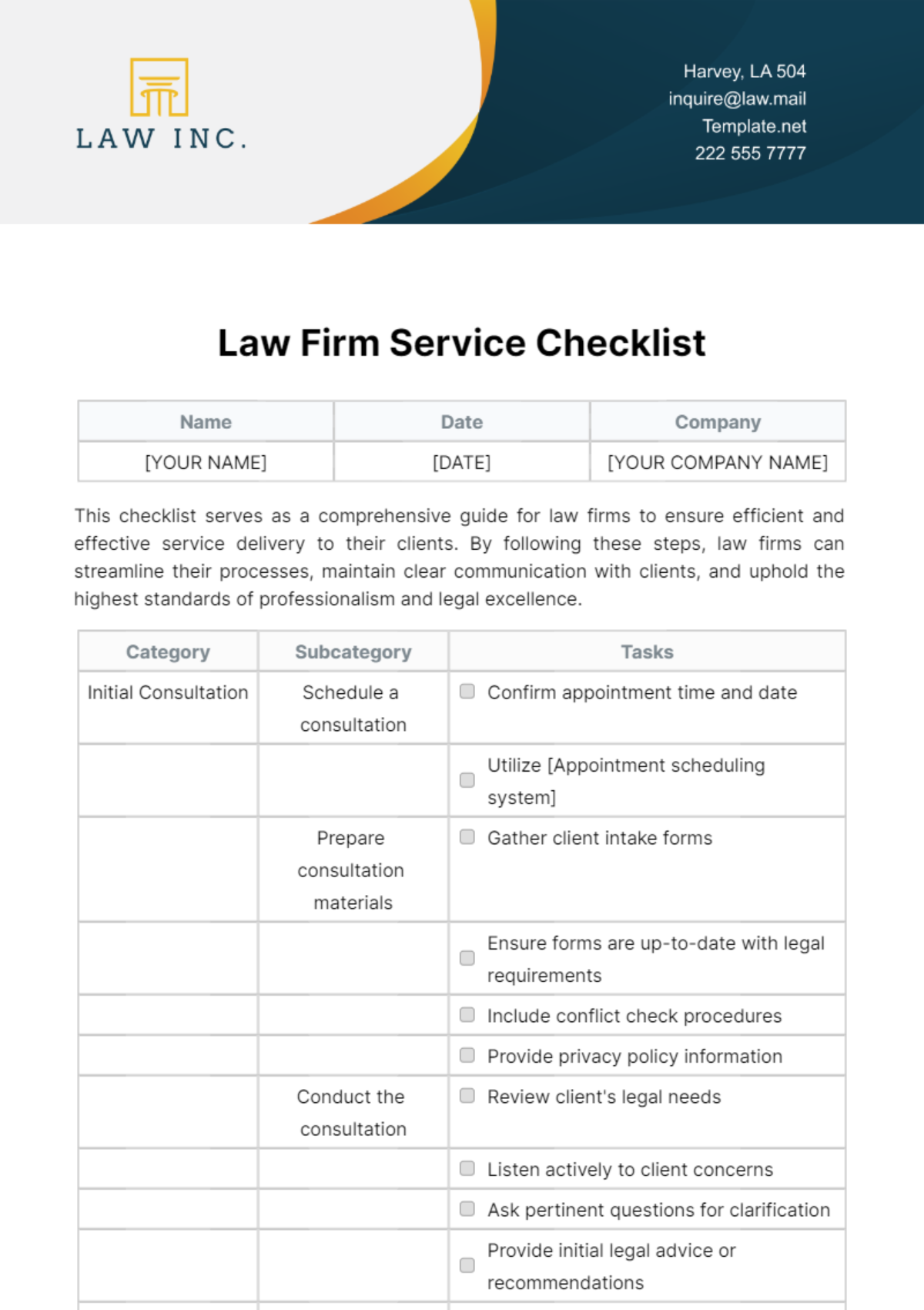
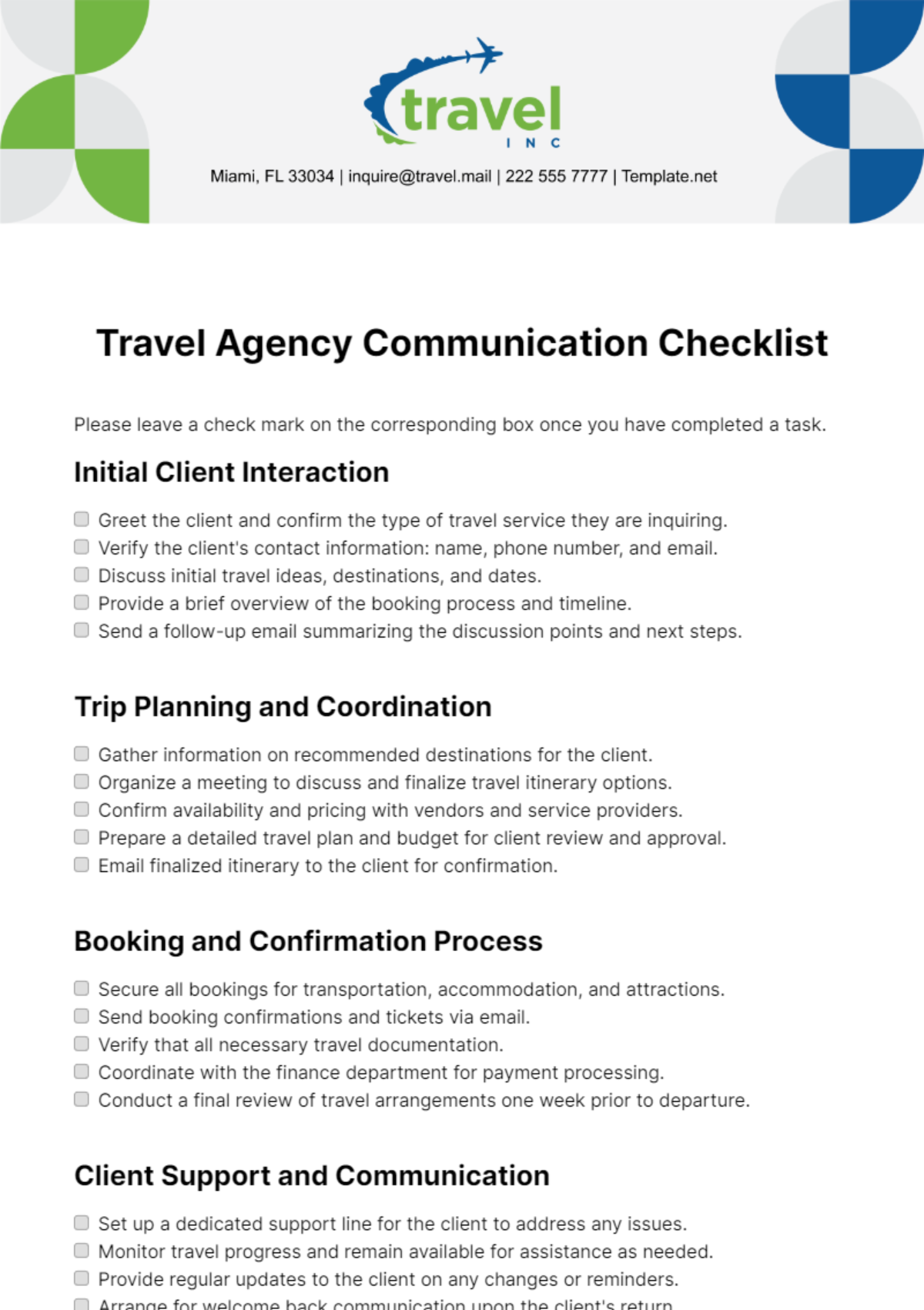
Security Protocols
1. Setup User Account:
Enforce a strong password policy.
Implement multi-factor authentication for enhanced security.
Define access restrictions based on job responsibilities.
Provide guidelines on reporting security incidents.
2. Data Encryption and Backup:
Enable disk encryption for sensitive data.
Establish regular automated backups.
Test data recovery procedures periodically.
Educate users on the importance of data protection.
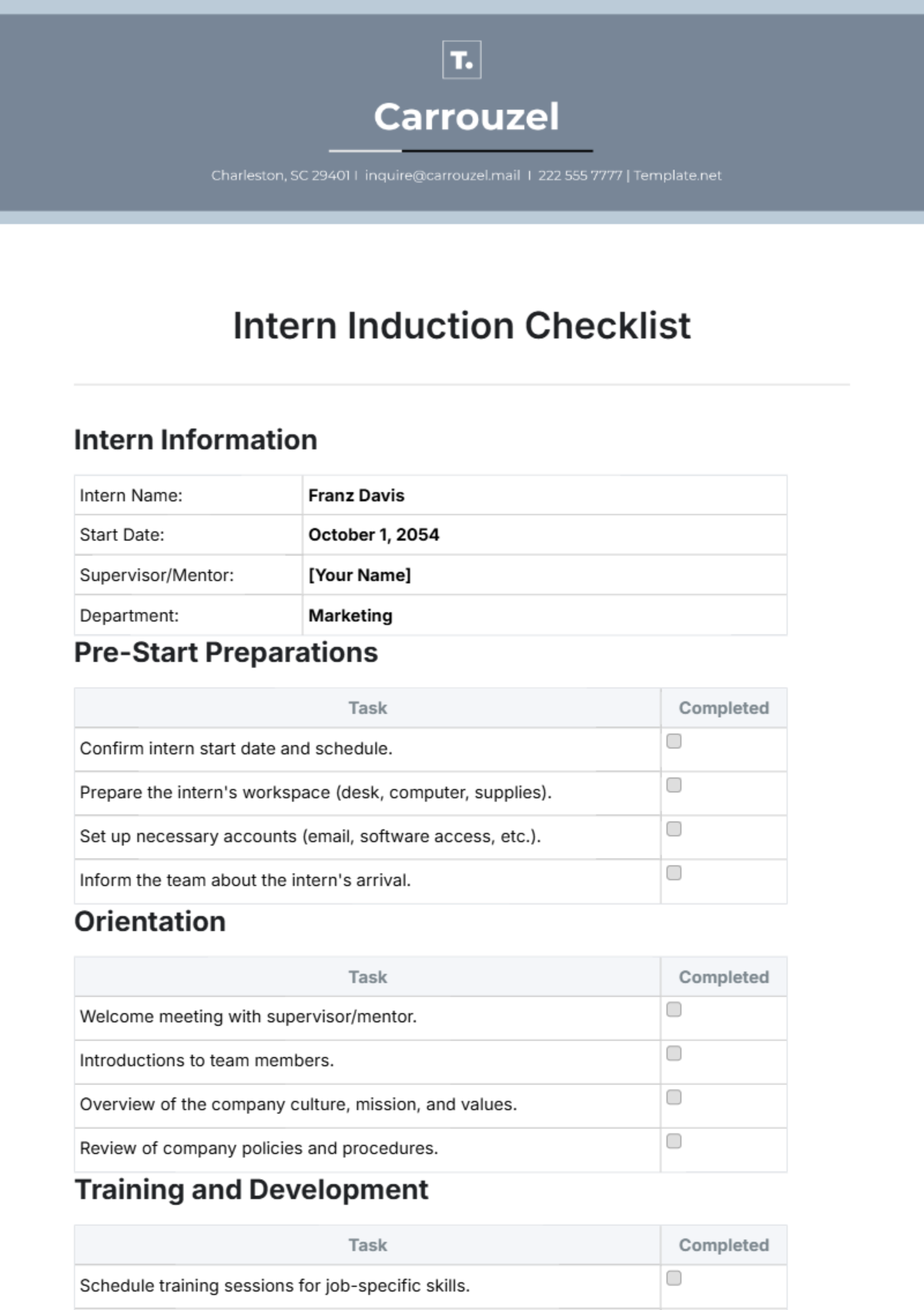
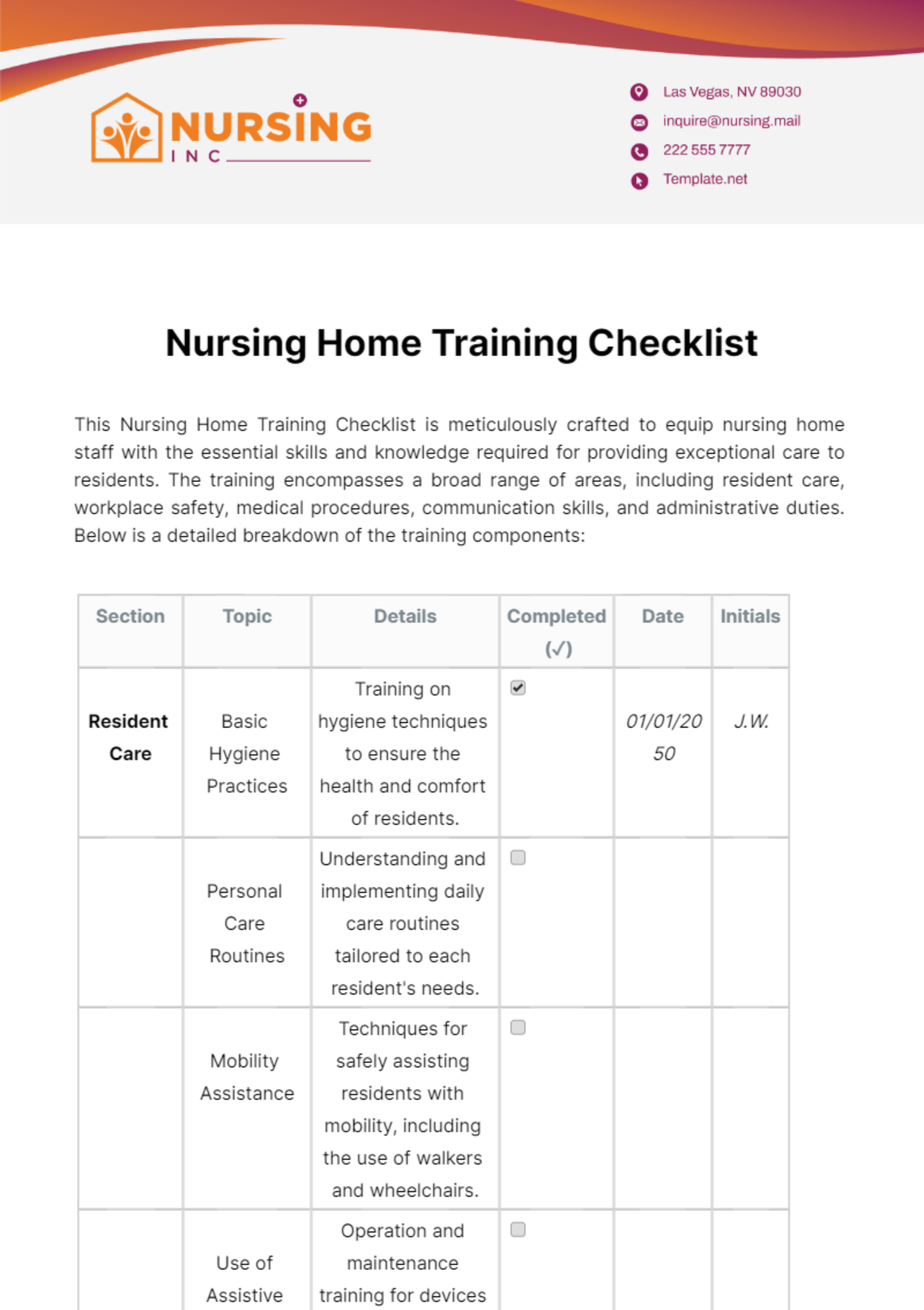
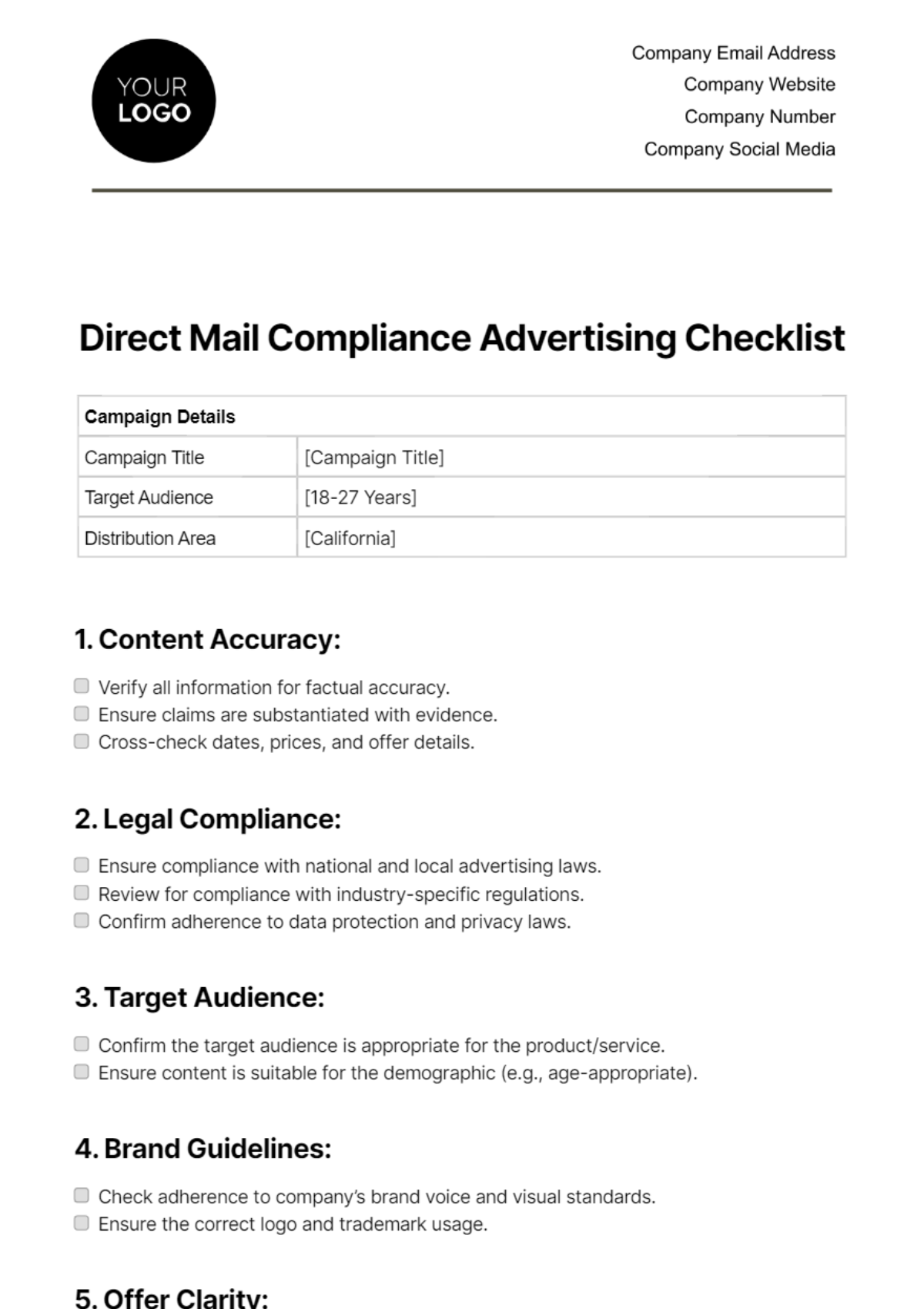
Training Modules
1. Cybersecurity Awareness Training:
Conduct phishing awareness sessions.
Instruct on recognizing and reporting security threats.
Provide guidelines for secure online behavior.
Test employee knowledge with simulated security scenarios.
2. Customized Software Training:
Offer specialized training for industry-specific software.
Provide resources for self-paced learning.
Conduct hands-on workshops for practical application.
Establish a support system for software-related queries.
Prepared by: [Your Name]
Company: [Your Company Name]
Date: [Date]