IT Infrastructure, Security, and Process Assessment
This comprehensive IT assessment aims to ensure the robustness of infrastructure, security protocols, and operational processes. By expanding the checklist items, the objective is to provide a thorough examination of critical IT components, enhancing overall system reliability and resilience against potential threats.
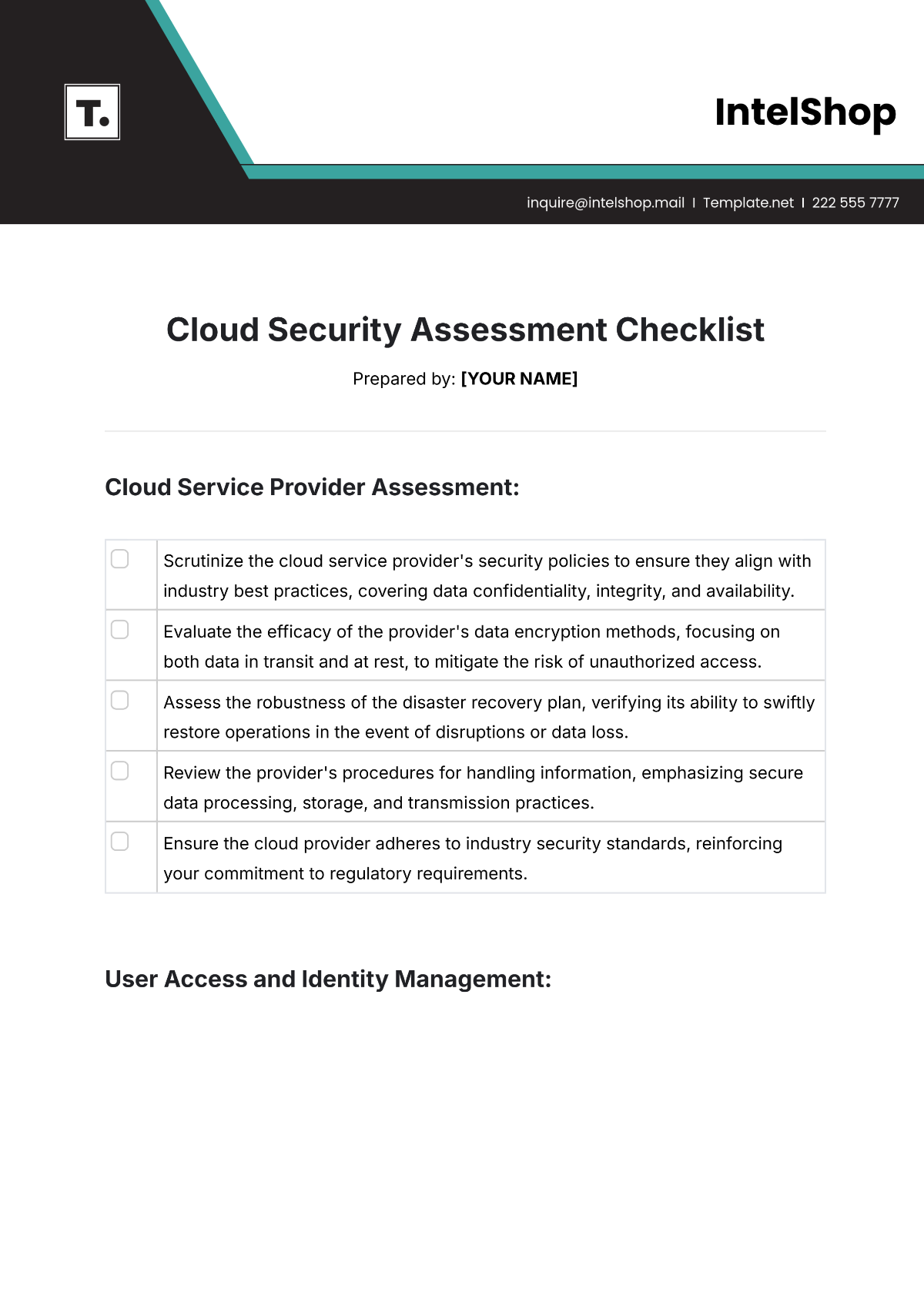
Infrastructure
Verify system integration by assessing the seamless interaction of software applications and hardware components.
Check data backup systems for effectiveness, ensuring data recovery capabilities in case of system failures.
Assess network connectivity to identify potential bottlenecks and optimize data transfer speeds.
Evaluate hardware conditions by conducting a comprehensive review of servers, computers, and other devices for performance and maintenance needs.
Security
Analyze firewall protection to confirm its ability to block unauthorized access and prevent cyber threats.
Test vulnerability to threats by simulating potential security breaches and assessing the system's resistance.
Review password protocols to ensure the implementation of strong, regularly updated passwords for user accounts.
Examine encryption measures to safeguard sensitive data and communications from unauthorized access.
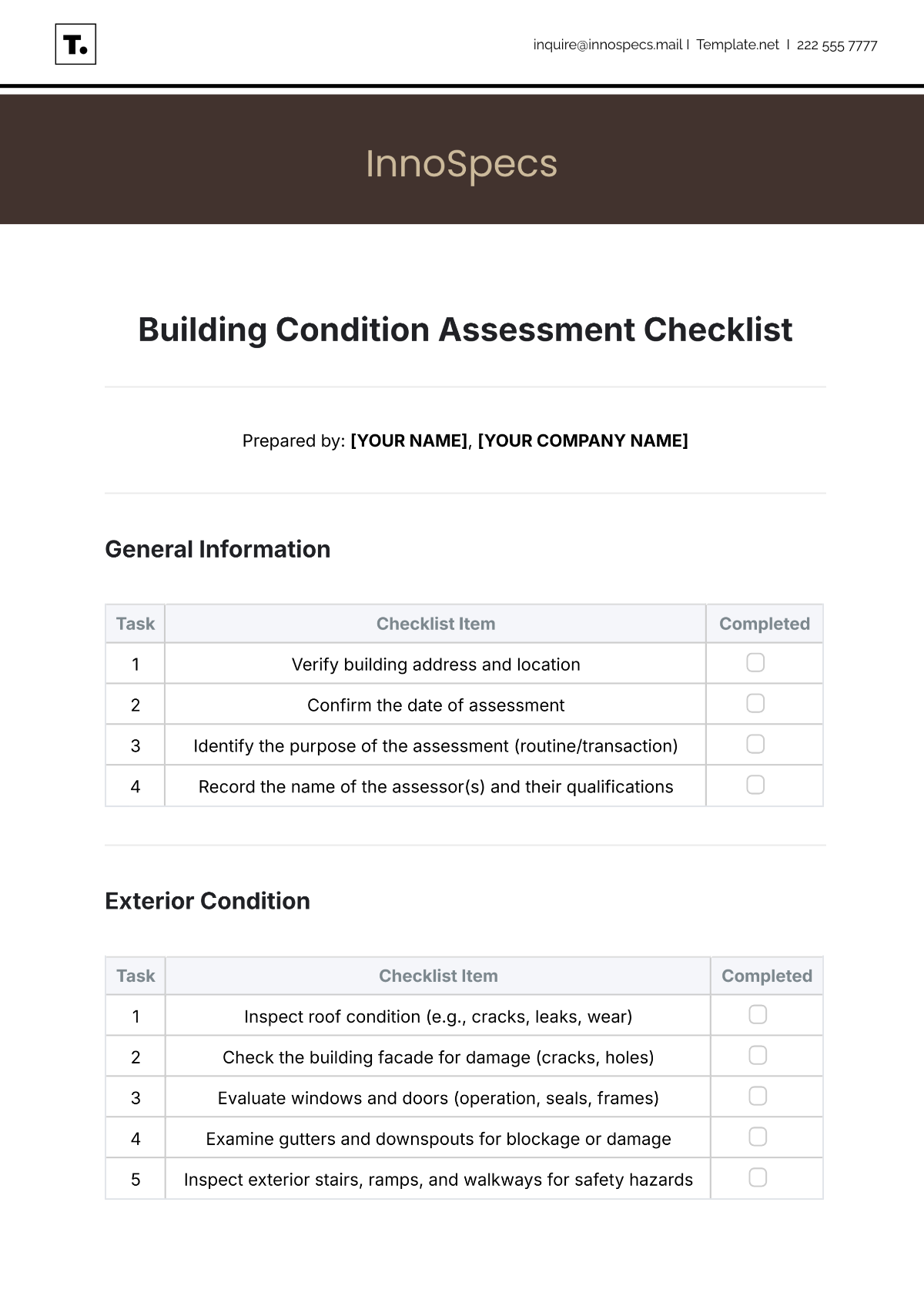
Process
Conduct software audits to verify license compliance and assess the efficiency of installed applications.
Review update schedules to ensure timely application of patches and security updates.
Scrutinize helpdesk processes, focusing on responsiveness and issue resolution times.
Inspect the equipment upgrade process to determine its alignment with organizational needs and technological advancements.
[Your Company Name]
Checked by: [Your Name]