IT Data Centre Resilience Assessment
This IT Data Centre Audit Checklist aims to provide a holistic and in-depth evaluation of the data center's hardware, software, infrastructure, and security components.
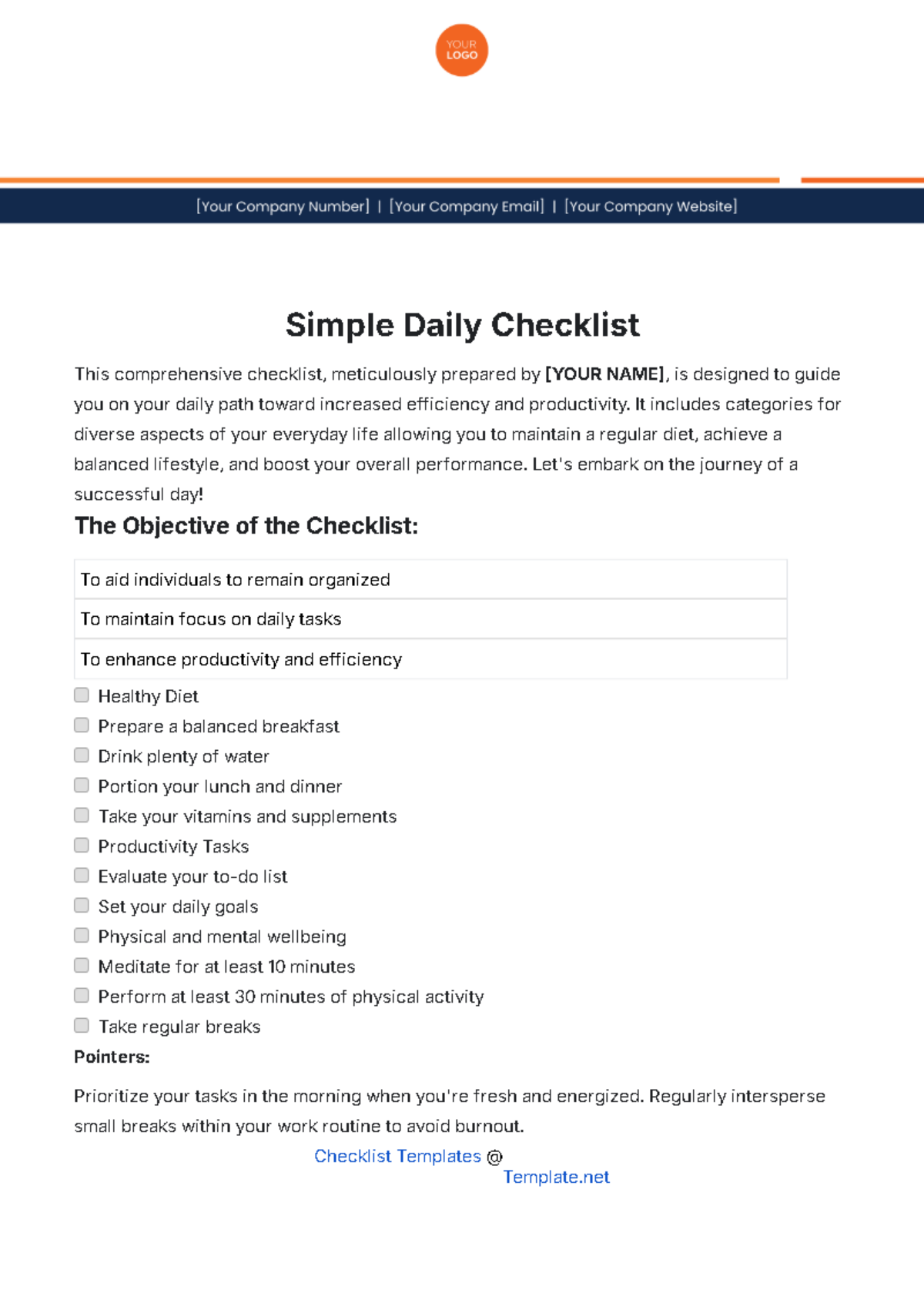
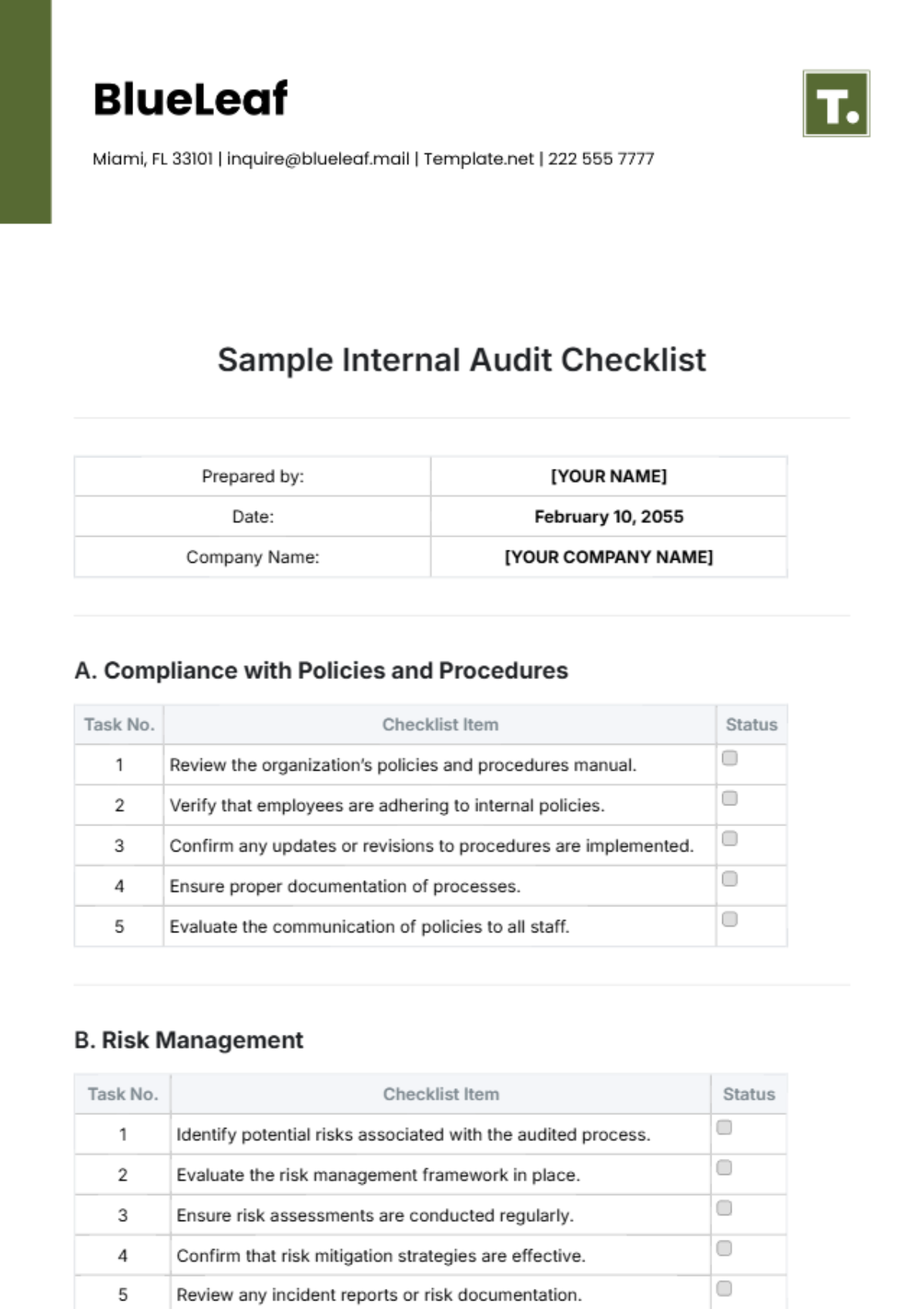
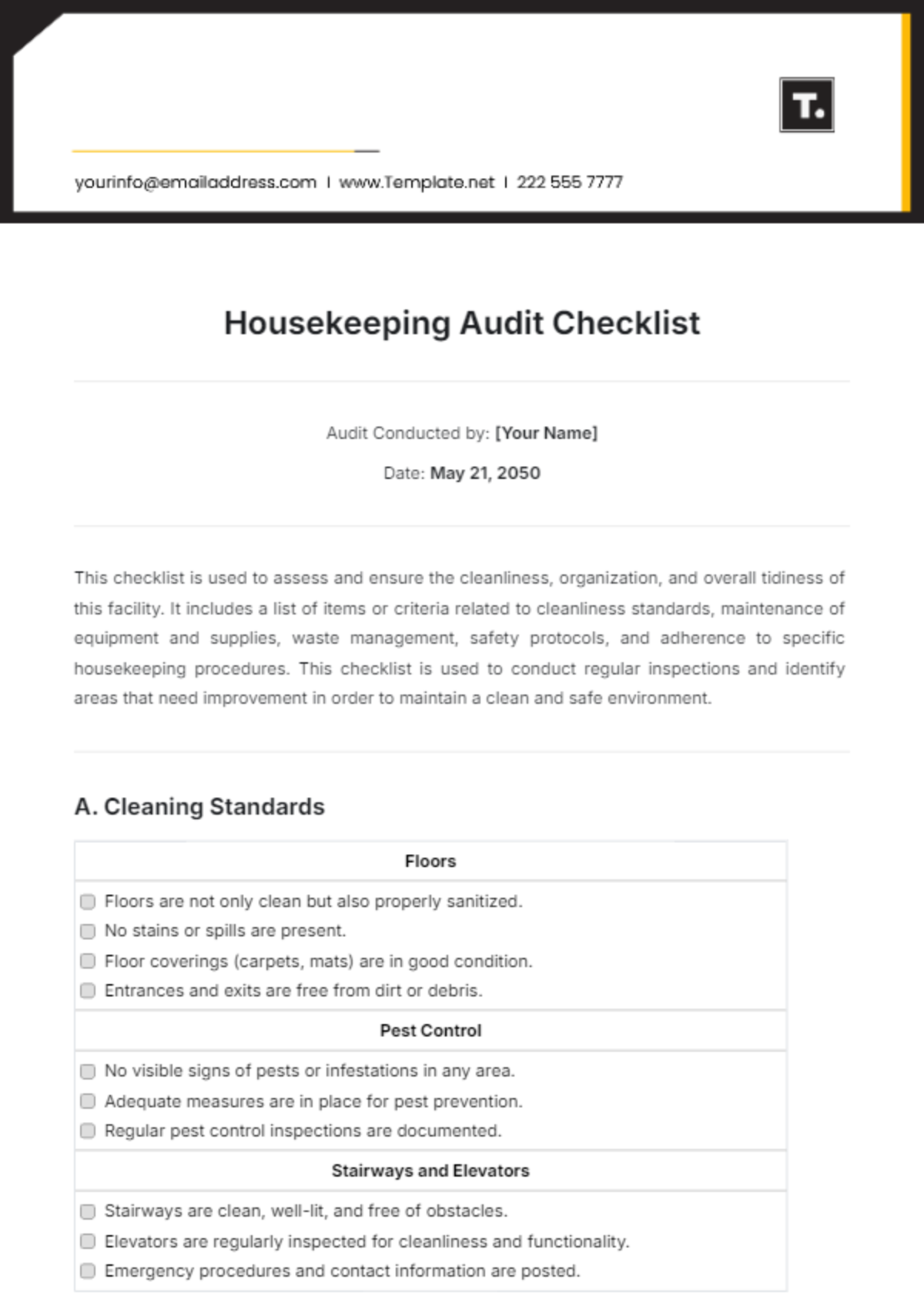
Hardware Audit
|
|
|
|
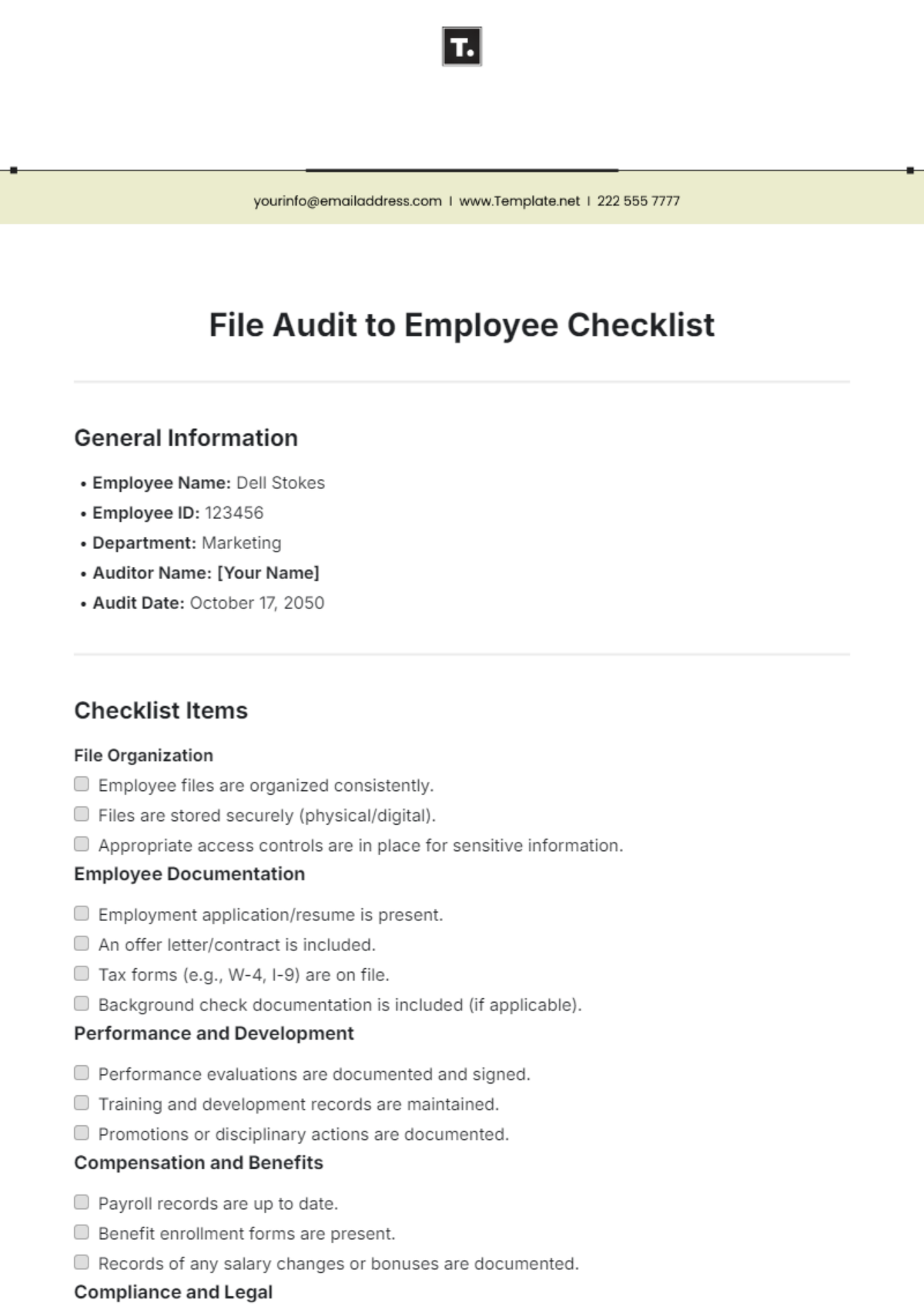
Software Audit
|
|
|
|
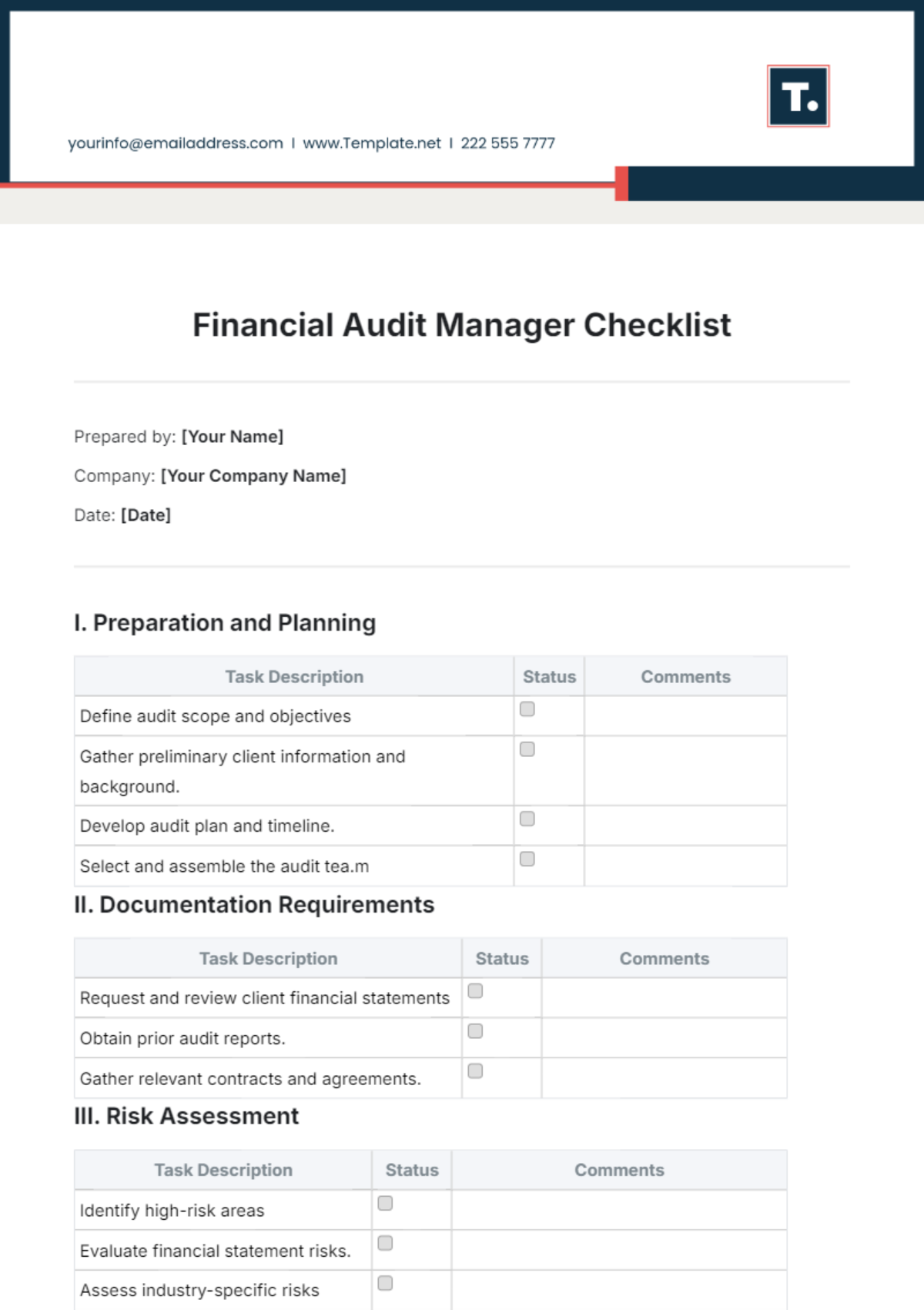
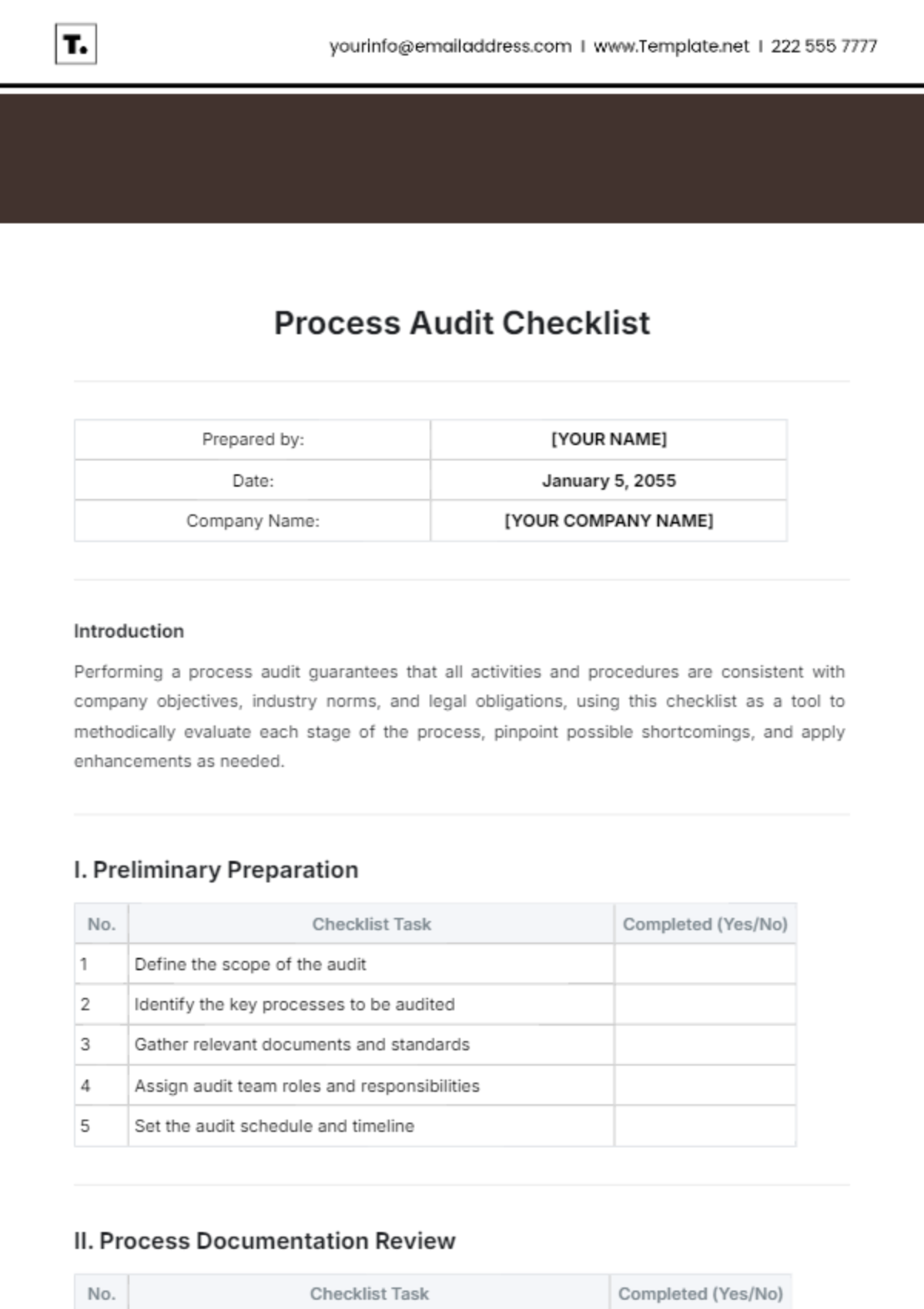
Infrastructure Audit
|
|
|
|
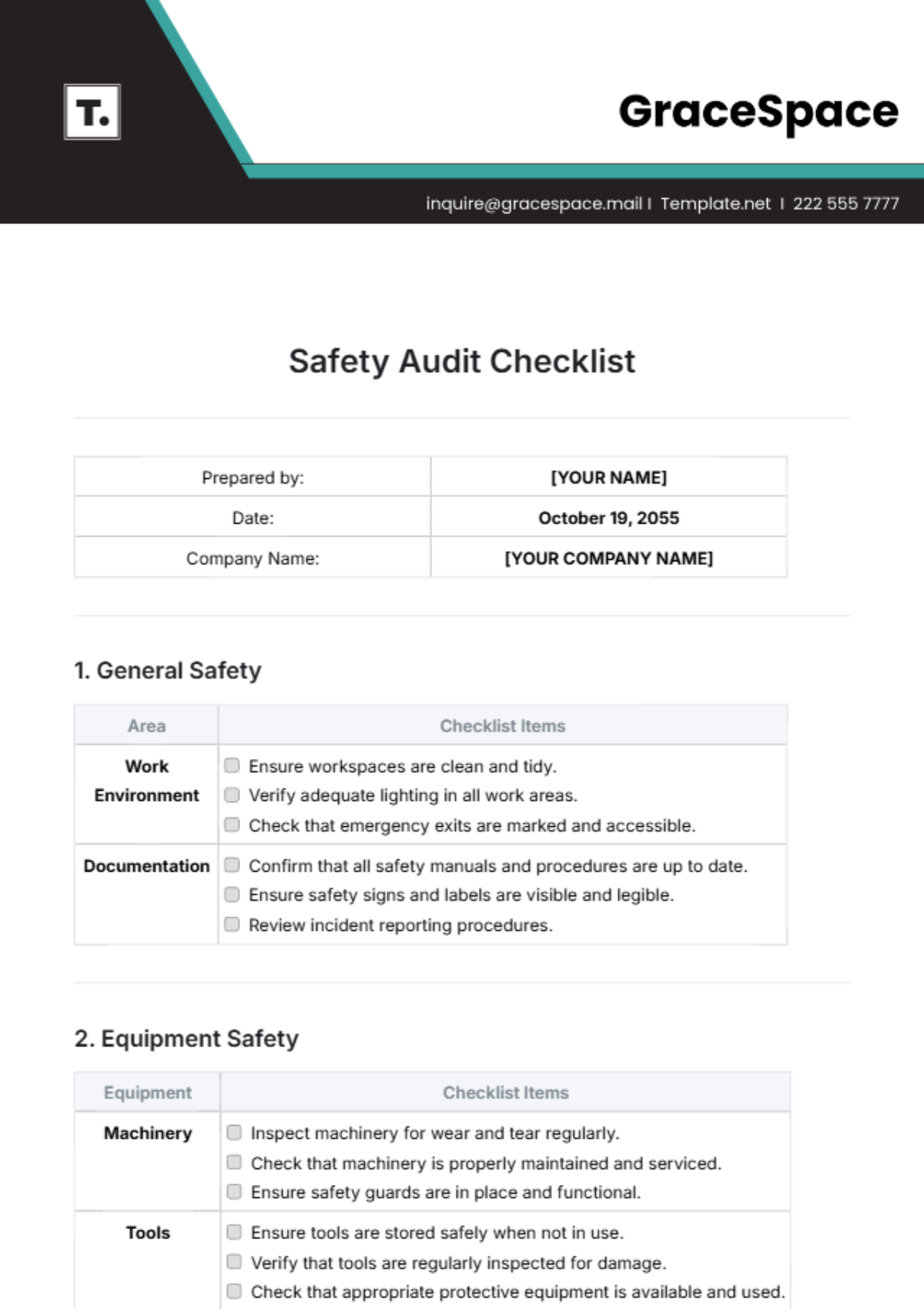
Security and Protocols Audit
|
|
|
|
Checked by: | Company | Date Checked: |
|---|---|---|
[Your Name] | [Your Company Name] | [Date] |