Free Legal Corporate IT Security Compliance Checklist
This checklist is intended to facilitate comprehensive assessment and maintenance of IT security compliance within [Your Company Name]. Please follow the instructions in each category and ensure that the necessary measures are in place. You may utilize the provided spaces or tick boxes to indicate compliance status.
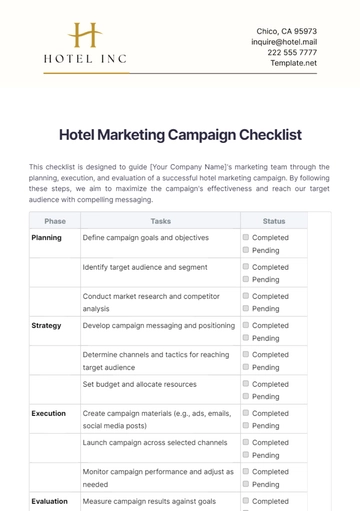
1. Policy and Procedures
Develop and regularly review a comprehensive written organizational security policy.
Clearly define user roles and responsibilities within the organization.
Establish procedures for effectively handling and responding to security incidents.
Implement a robust risk management plan to mitigate potential threats.
Ensure adherence to relevant regulations and standards governing IT security practices.
2. Technical Measures
Regularly update software and hardware.
Conduct regular security audits and vulnerability assessments.
Implement firewalls and intrusion detection systems.
Encrypt sensitive data at rest and in transit.
Maintain backups of all important data.
3. Human Factors
Train staff on security awareness and incident response.
Enforce strong password policies.
Maintain clear lines of communication about security issues.
Implement regular phishing testing for employees.
Incorporate security protocols into onboarding and offboarding processes.
4. Incident Response
Establish incident response team.
Create incident response plan.
Practice incident response scenarios.
Develop post-incident recovery processes.
Report incidents as required by regulations.
5. Physical Security
Secure data centers and server rooms.
Restrict employee access to necessary areas only.
Use locking devices for laptops and mobile devices.
Monitor premises using surveillance cameras.
Dispose of hardware and media securely and responsibly.
Prepared By: [YOUR NAME]
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Ensure the utmost security for your IT infrastructure with Template.net's Legal Corporate IT Security Compliance Checklist Template. Our AI editor empowers you to tailor the checklist to your company's specific needs, ensuring comprehensive coverage of all security aspects. Customize effortlessly, incorporating industry best practices and regulatory requirements. With editable features, streamline compliance efforts and fortify your defenses against cyber threats. Elevate your IT security posture with confidence and ease.
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist