Firewall Compliance Checklist
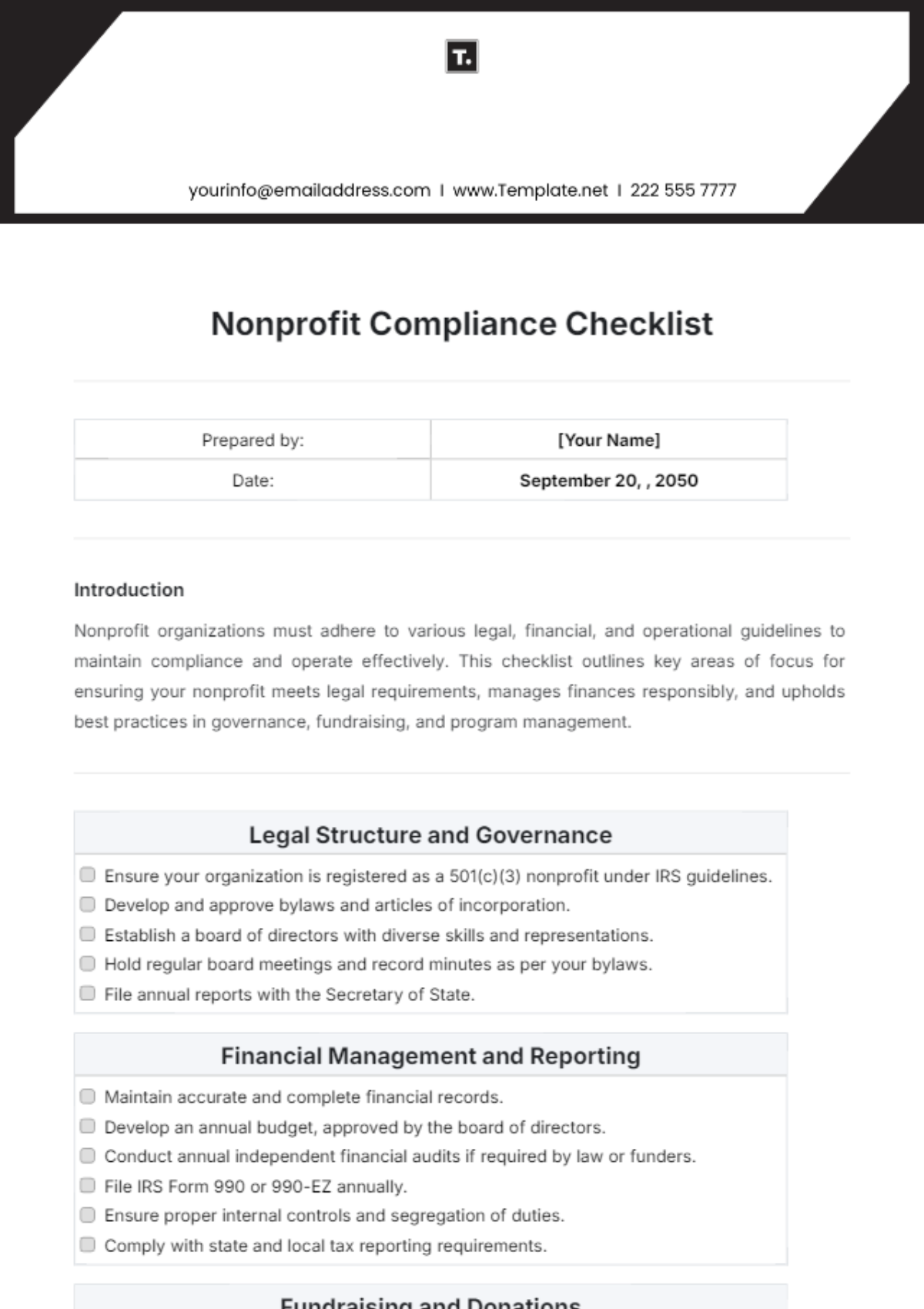
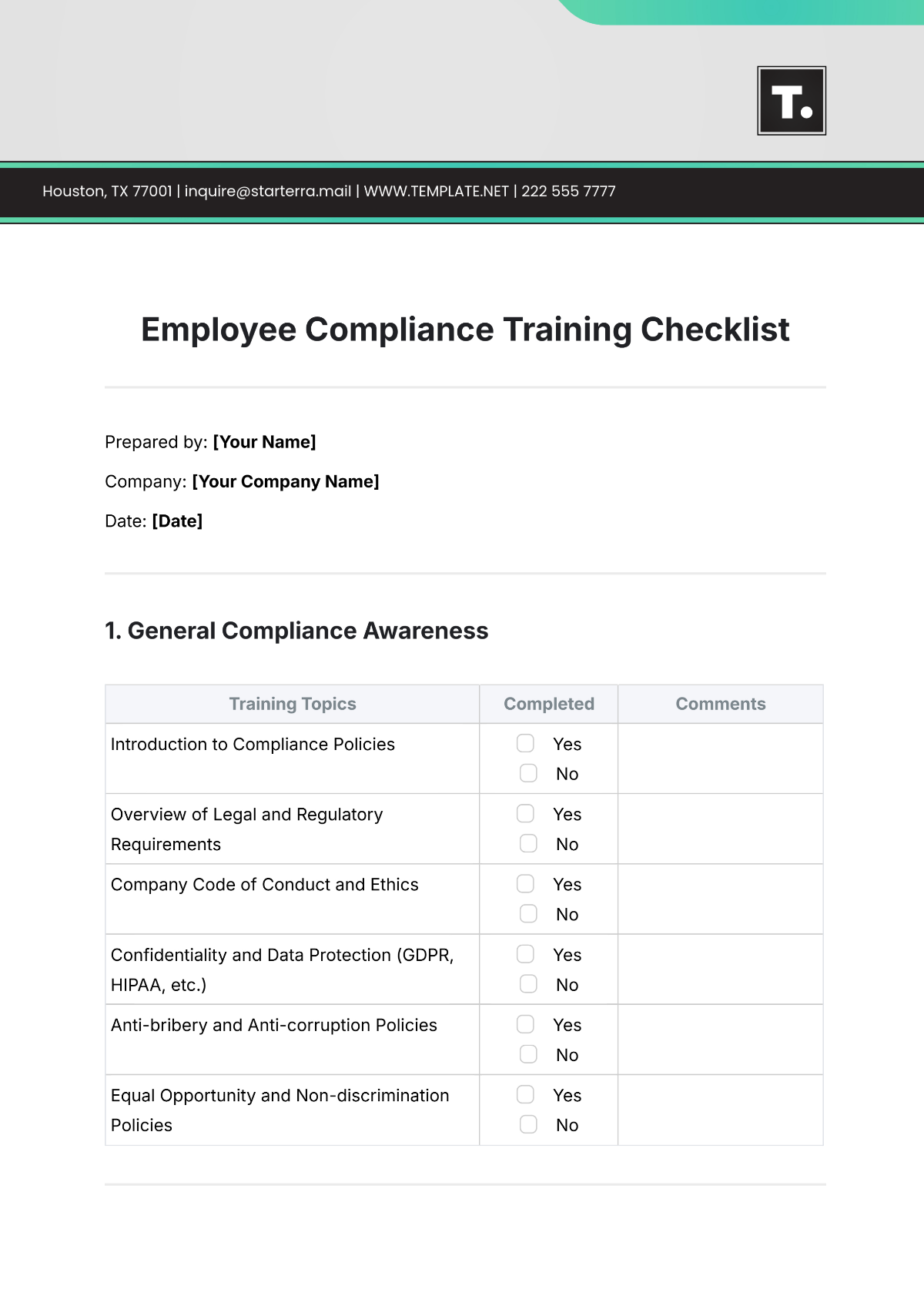
I. Compliance Overview
Objective: Ensure that [YOUR ORGANIZATION NAME]'s firewall configuration adheres to all relevant security standards and best practices.
Responsible Party: [YOUR NAME], Firewall Compliance Officer
Date of Last Review: [DATE]
Next Scheduled Review: [NEXT REVIEW DATE]
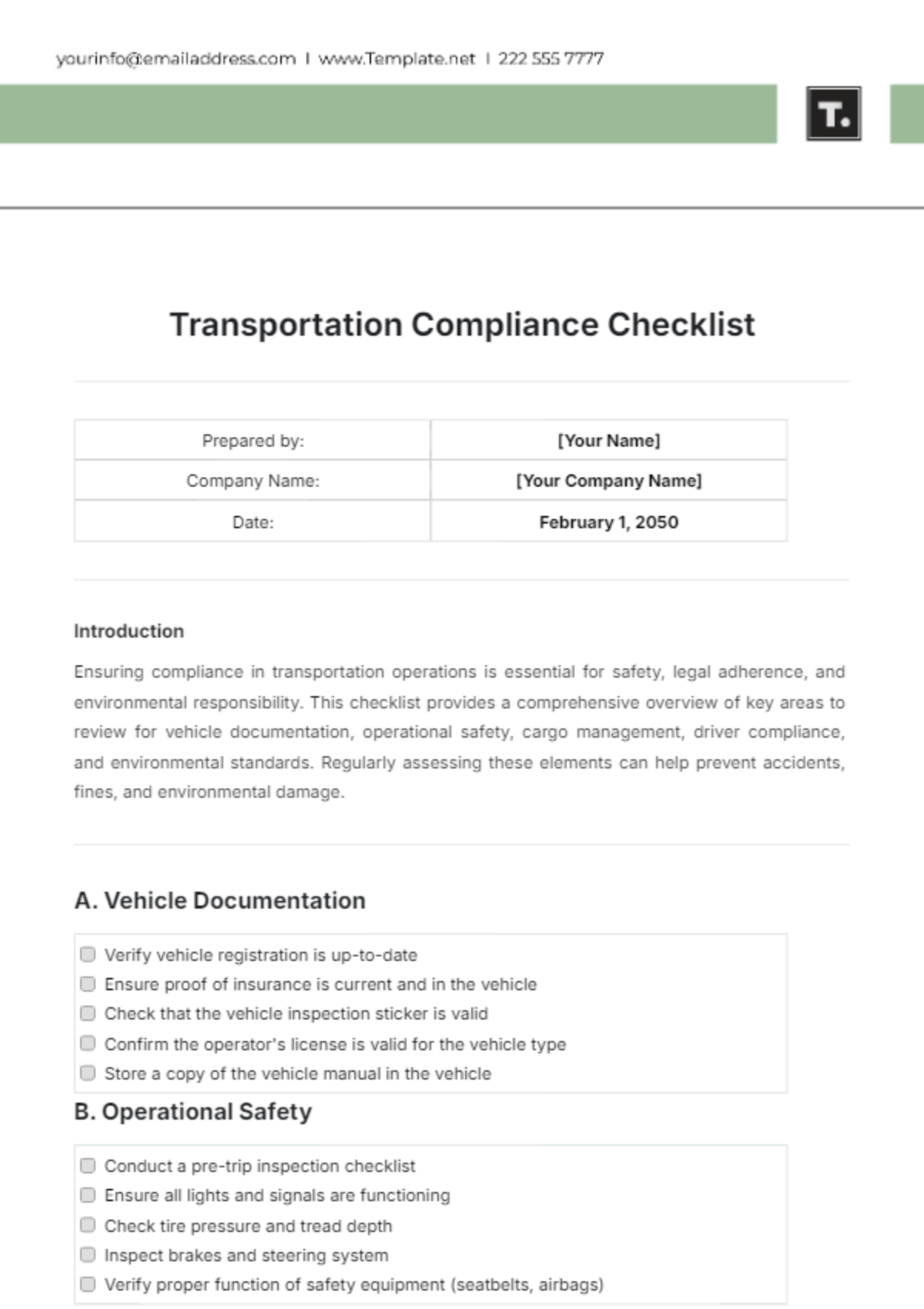
II. Firewall Configuration
1. Rule Base Review
Regularly review and update the firewall rule base to reflect current organizational needs.
Remove outdated or unnecessary rules to reduce potential vulnerabilities.
2. Default Settings
Disable default accounts and settings to prevent unauthorized access.
Implement strong password policies for administrative access.
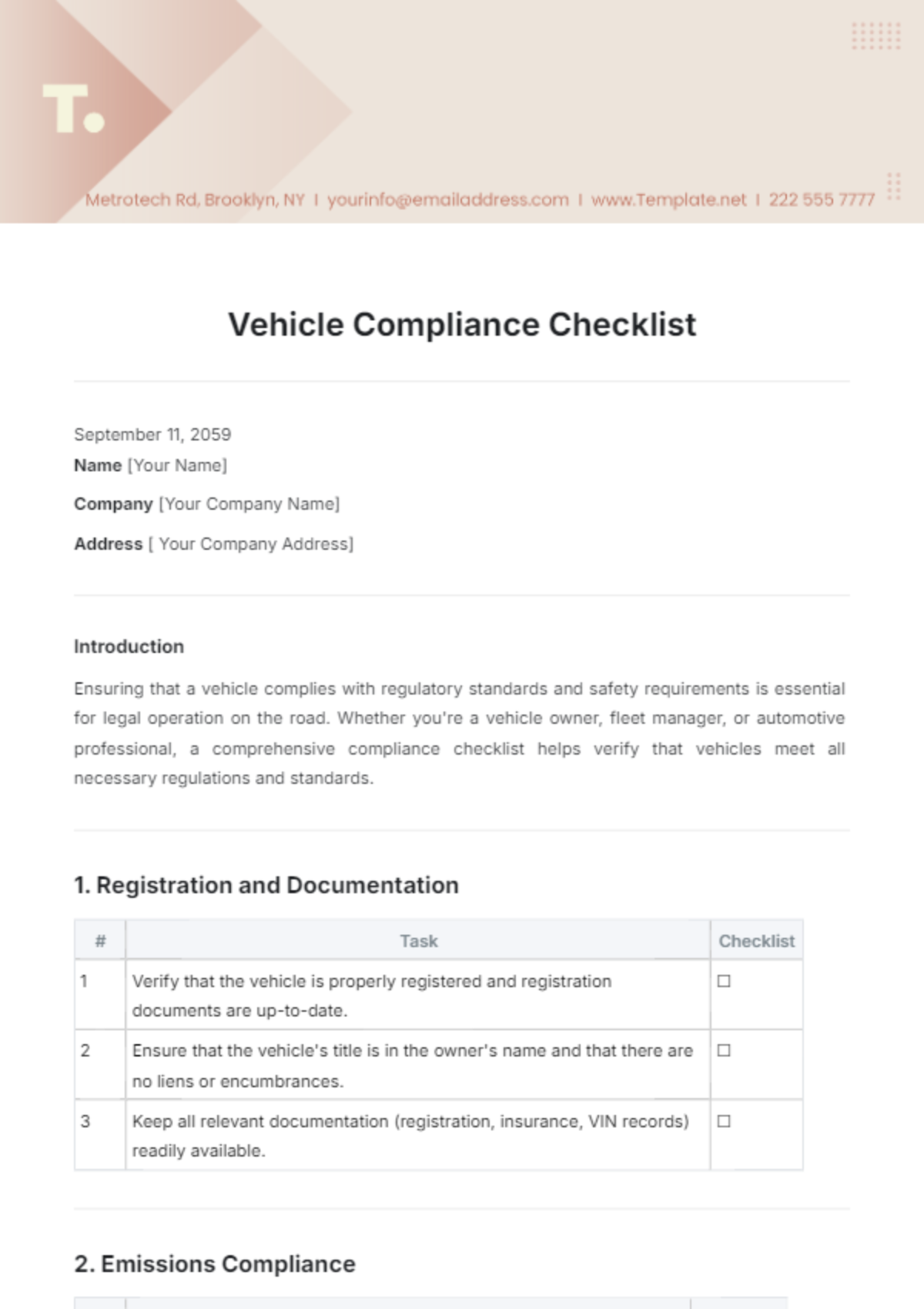
III. Access Control
1. User Authentication
Implement multi-factor authentication (MFA) for accessing the firewall management interface.
Assign roles and permissions based on job responsibilities to limit access.
2. Remote Access
Secure remote access to the firewall through VPNs or secure channels.
Monitor and log remote access activities for auditing and compliance purposes.
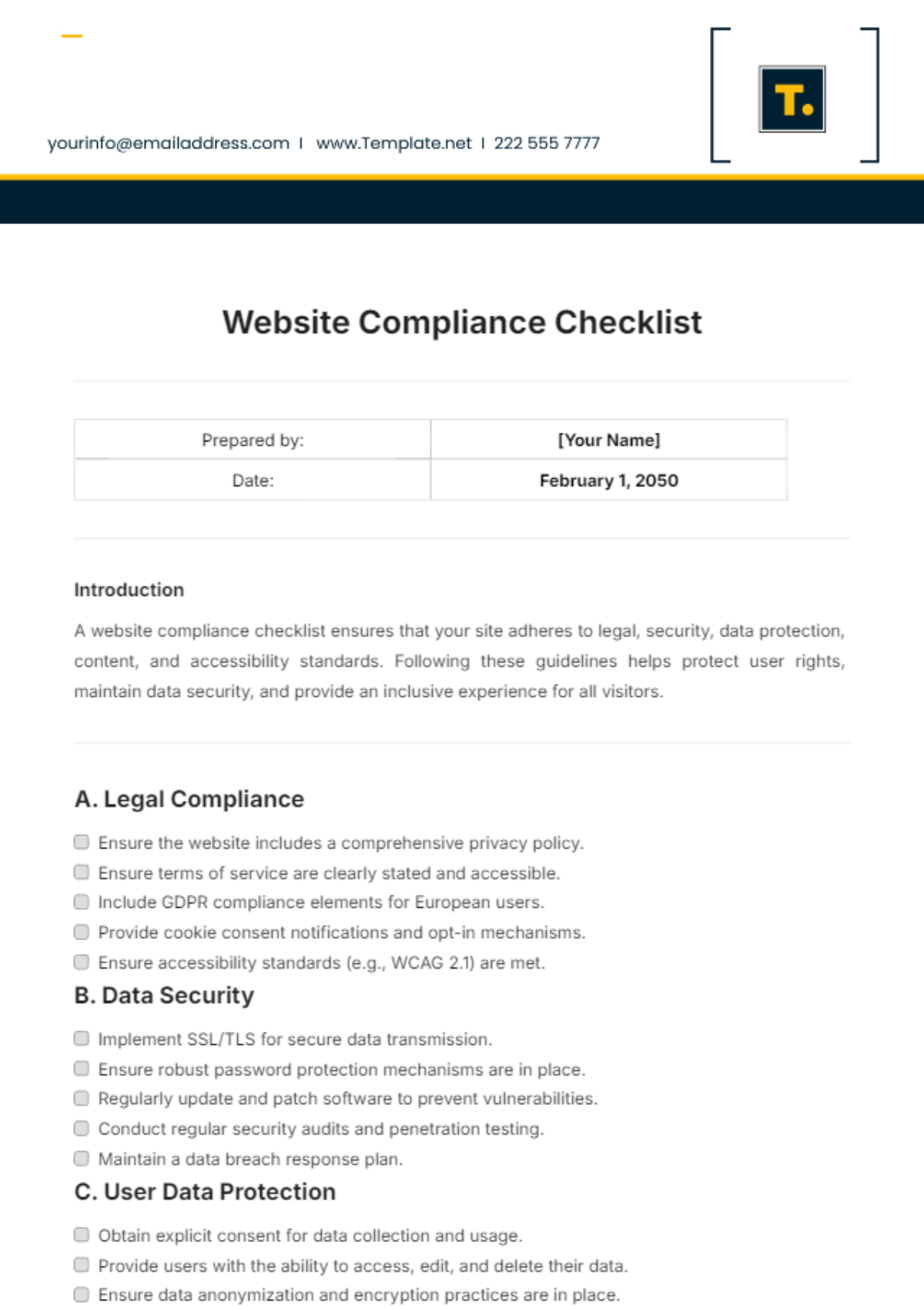
IV. Security Policies
1. Intrusion Prevention System (IPS)
Enable and configure the IPS to detect and block malicious activities.
Regularly update IPS signatures and rules to protect against new threats.
2. Application Control
Implement application control policies to manage and monitor application usage.
Block unauthorized or risky applications that pose security risks.
V. Logging and Monitoring
1. Logging Configuration
Configure firewall logging to capture relevant security events and activities.
Store logs securely and retain them for the required retention period.
2. Real-Time Monitoring
Implement real-time monitoring of firewall activities to detect suspicious or unauthorized access attempts.
Set up alerts for potential security incidents requiring immediate attention.
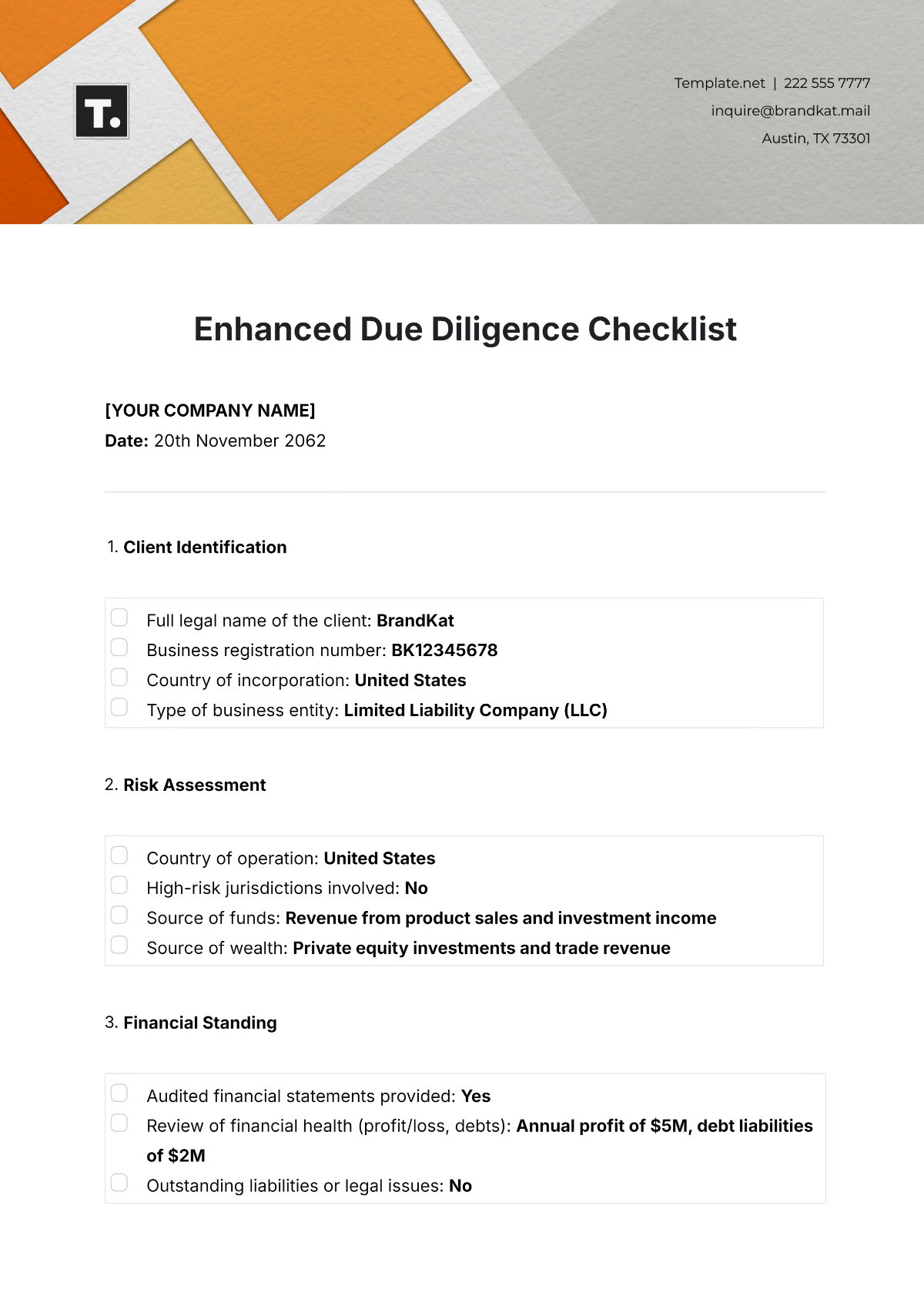
VI. Regular Audits and Assessments
1. Internal Audits
Conduct regular internal audits to assess firewall compliance and effectiveness.
Document findings and implement corrective actions as necessary.
2. Third-Party Audits
Engage external auditors to validate firewall compliance annually or as required.
Review and act on recommendations from external audits.
VII. Non-Compliance Response Plan
Establish procedures for addressing firewall non-compliance issues.
Document and report any instances of non-compliance, along with corrective actions taken.
Remember to regularly review and update this checklist to ensure ongoing compliance with all relevant firewall security standards and requirements. Compliance is an evolving process, and staying informed is key to protecting [YOUR ORGANIZATION NAME].
VIII. Signature
By signing below, you acknowledge that you have reviewed and understand the contents of this Firewall compliance checklist.

Firewall Compliance Officer
[YOUR ORGANIZATION NAME]
Date: [DATE]