Cyber Security Compliance Checklist
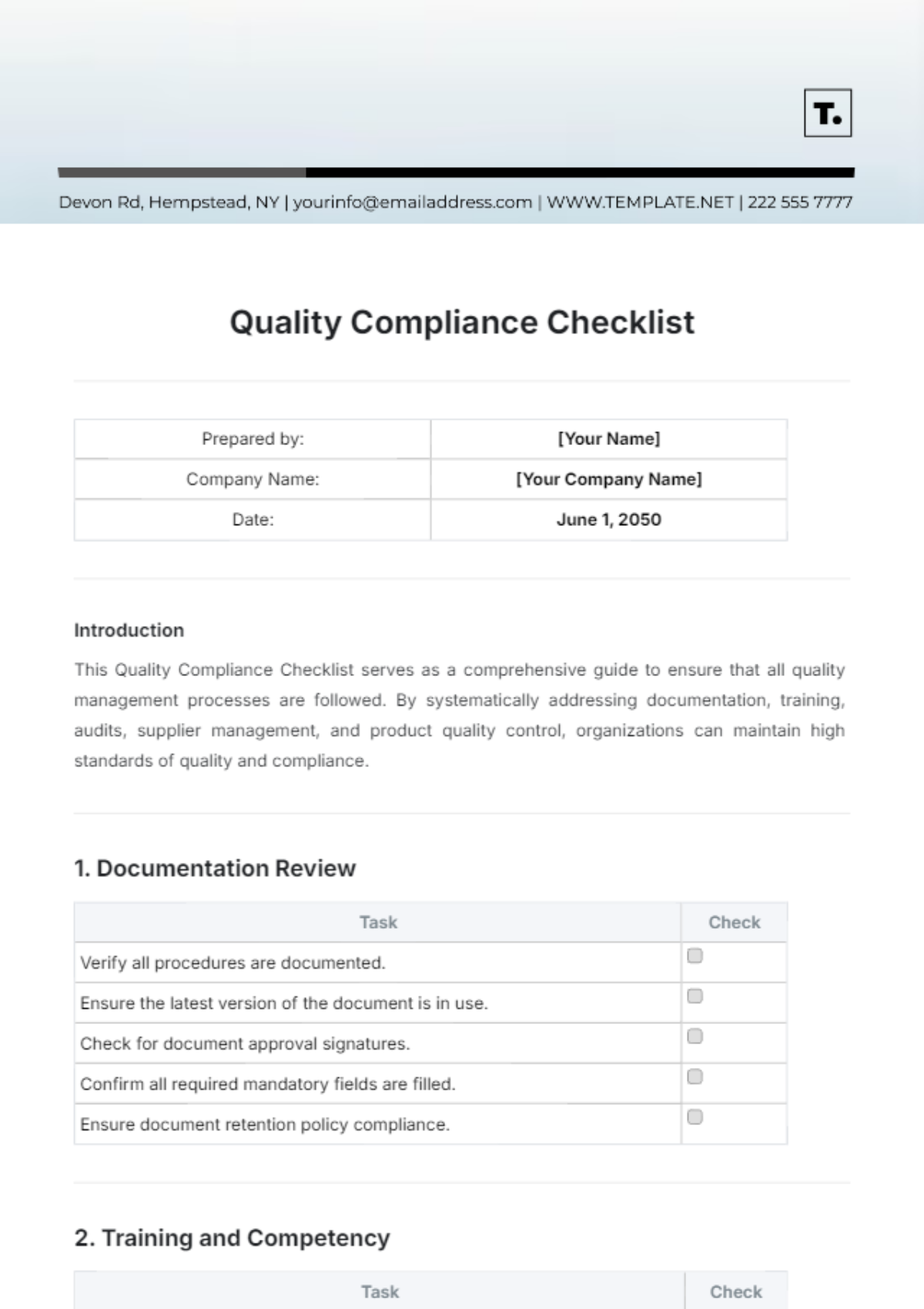
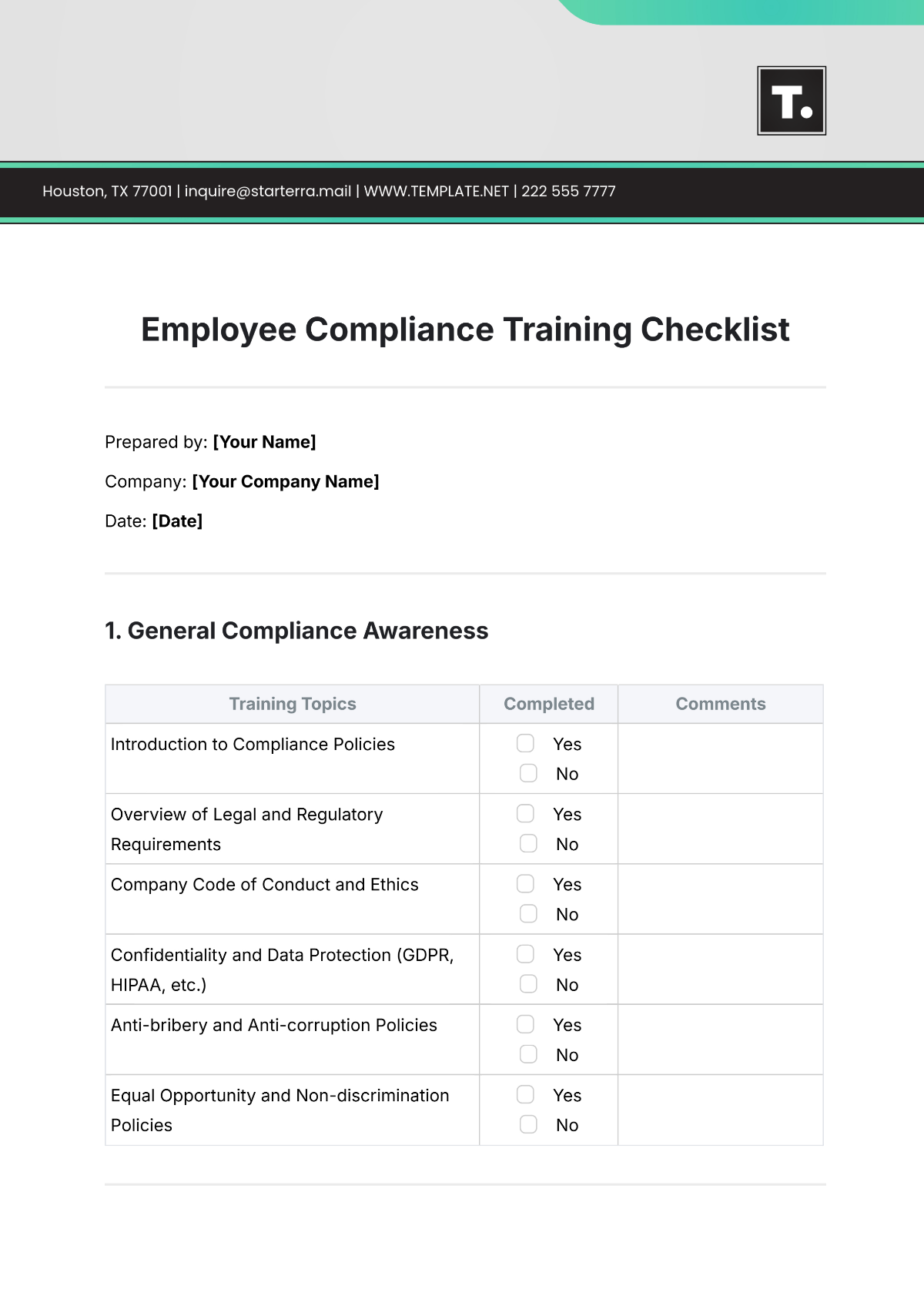
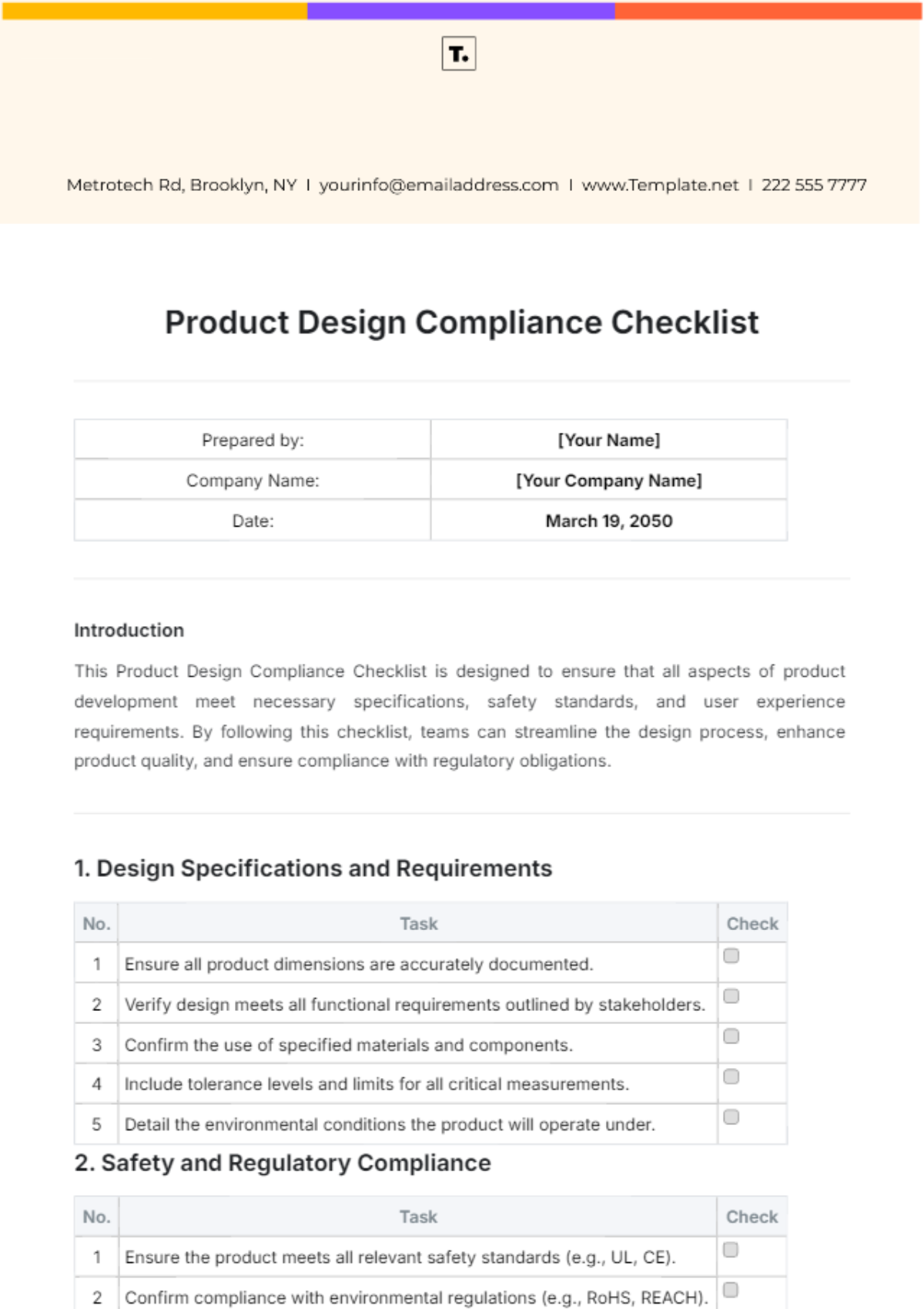
1. Compliance Overview
Objective: Ensure that [YOUR COMPANY NAME] complies with all relevant cyber security standards and best practices to protect sensitive information and mitigate cyber threats.
Responsible Party: [YOUR COMPANY NAME], [YOUR DEPARTMENT]
Date of Last Review: [DATE]
Next Scheduled Review: [DATE]
2. Access Control
A. User Access Management
Implement role-based access control (RBAC) to restrict unauthorized access.
Regularly review and update user access permissions based on job roles.
Enforce strong password policies and multi-factor authentication (MFA).
B. Privileged Access
Limit access to critical systems and data to authorized personnel only.
Monitor and audit privileged user activities for suspicious behavior.
Implement least privilege principle to minimize the risk of insider threats.
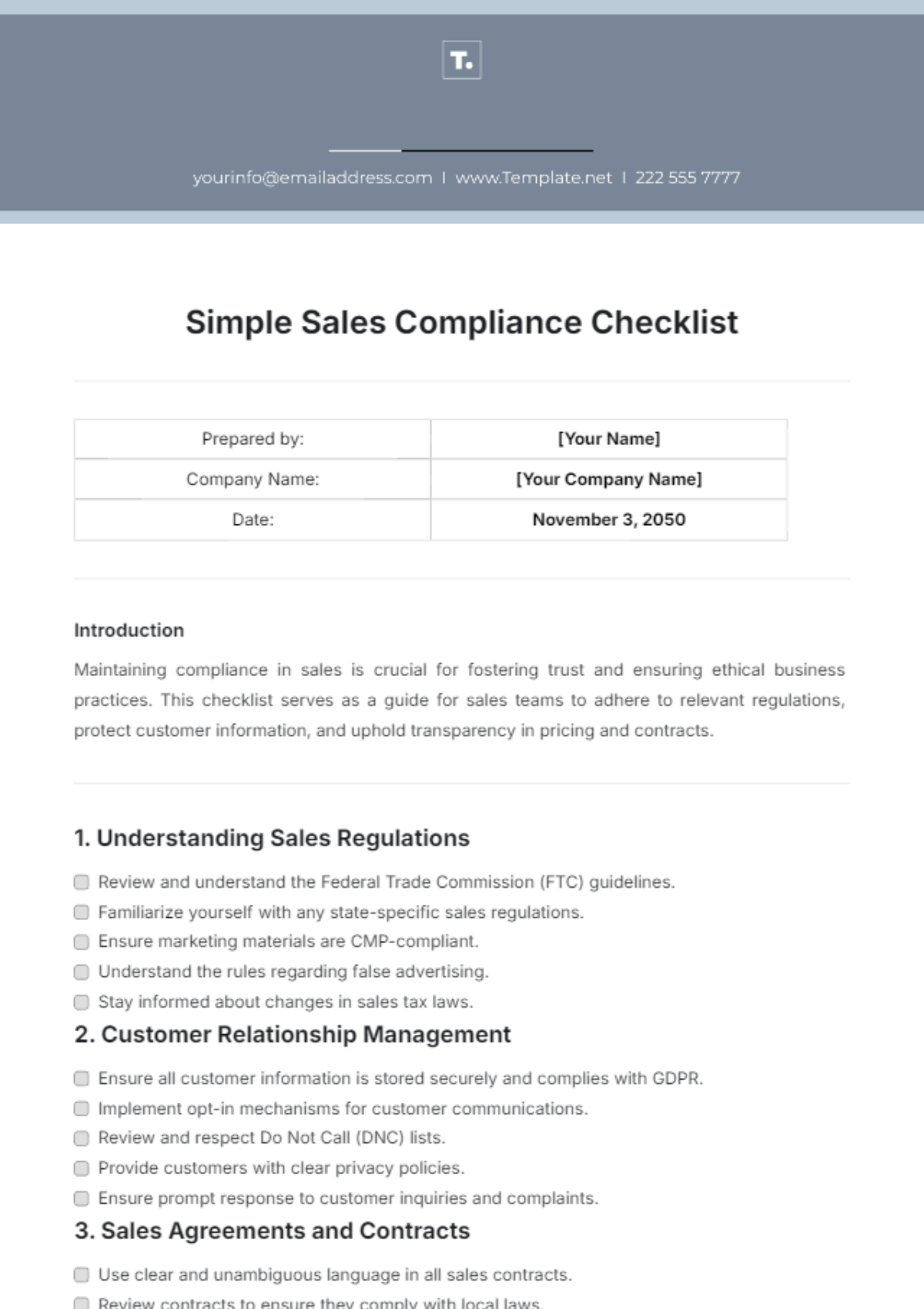
3. Network Security
A. Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS)
Deploy firewalls to monitor and control incoming and outgoing network traffic.
Implement IDS/IPS to detect and prevent malicious activities on the network.
Regularly update firewall and IDS/IPS rules to address emerging threats.
B. Secure Configuration
Configure network devices, such as routers and switches, with secure settings.
Disable unnecessary services and ports to reduce the attack surface.
Conduct regular vulnerability scans and penetration tests to identify and address security gaps.
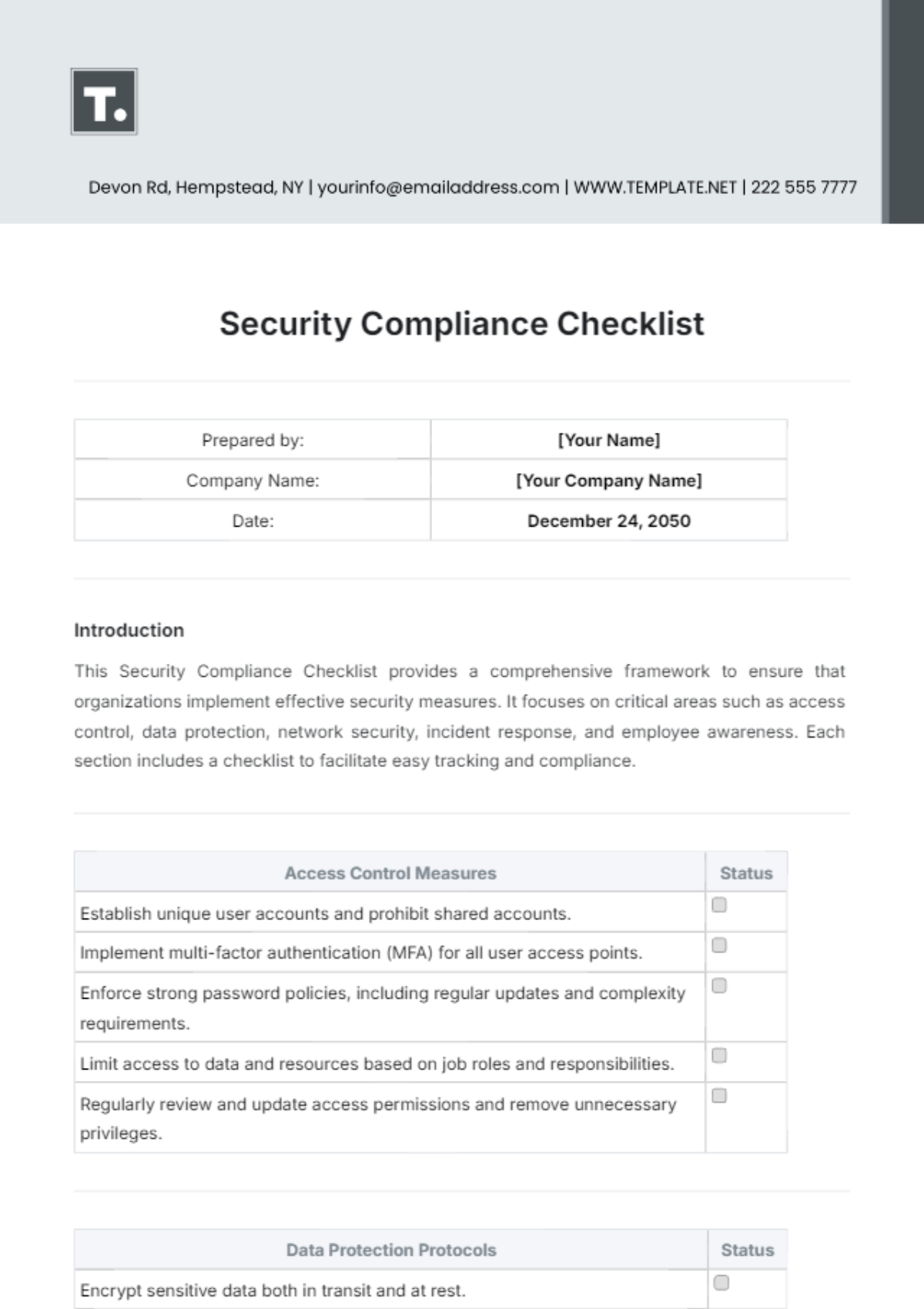
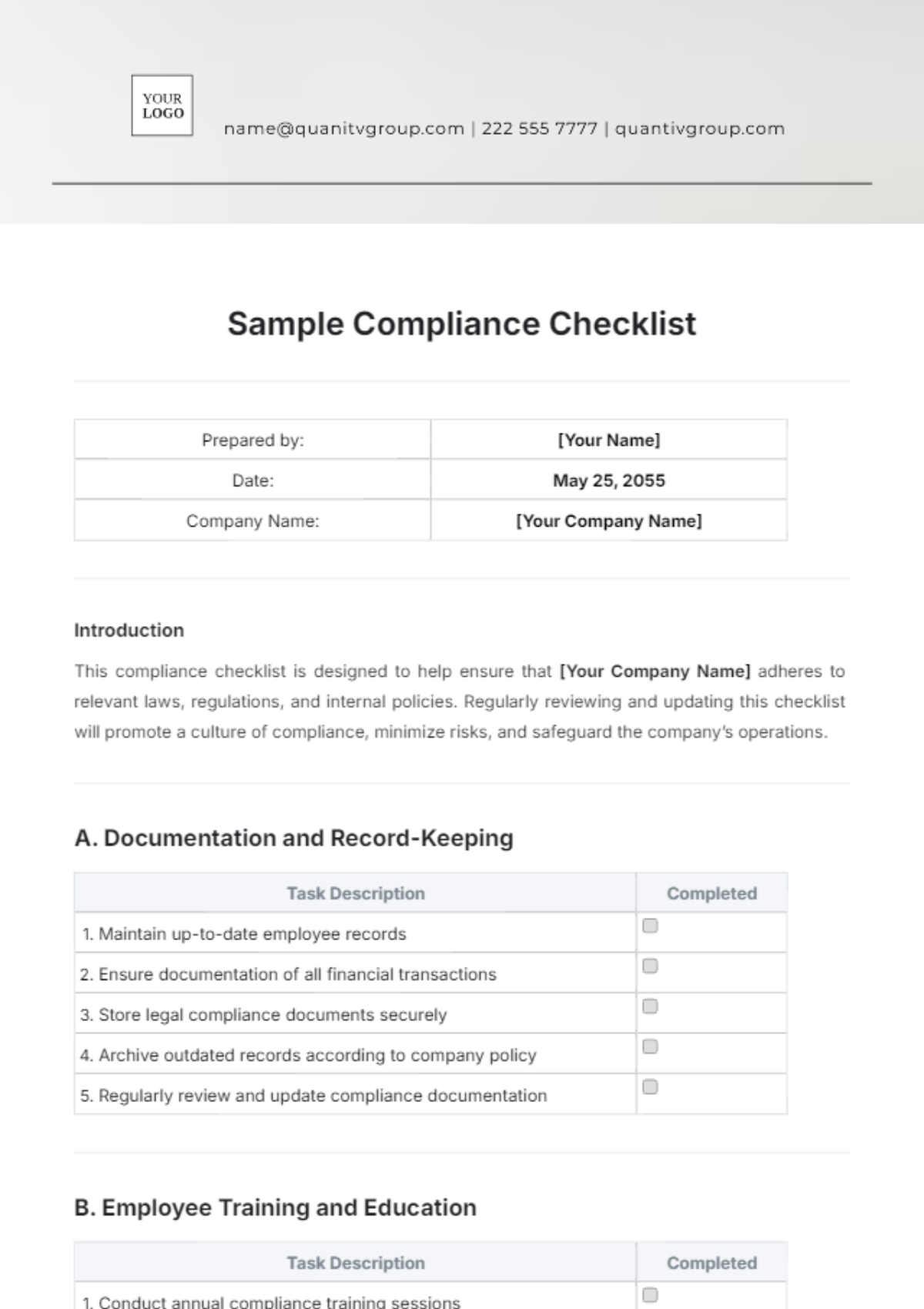
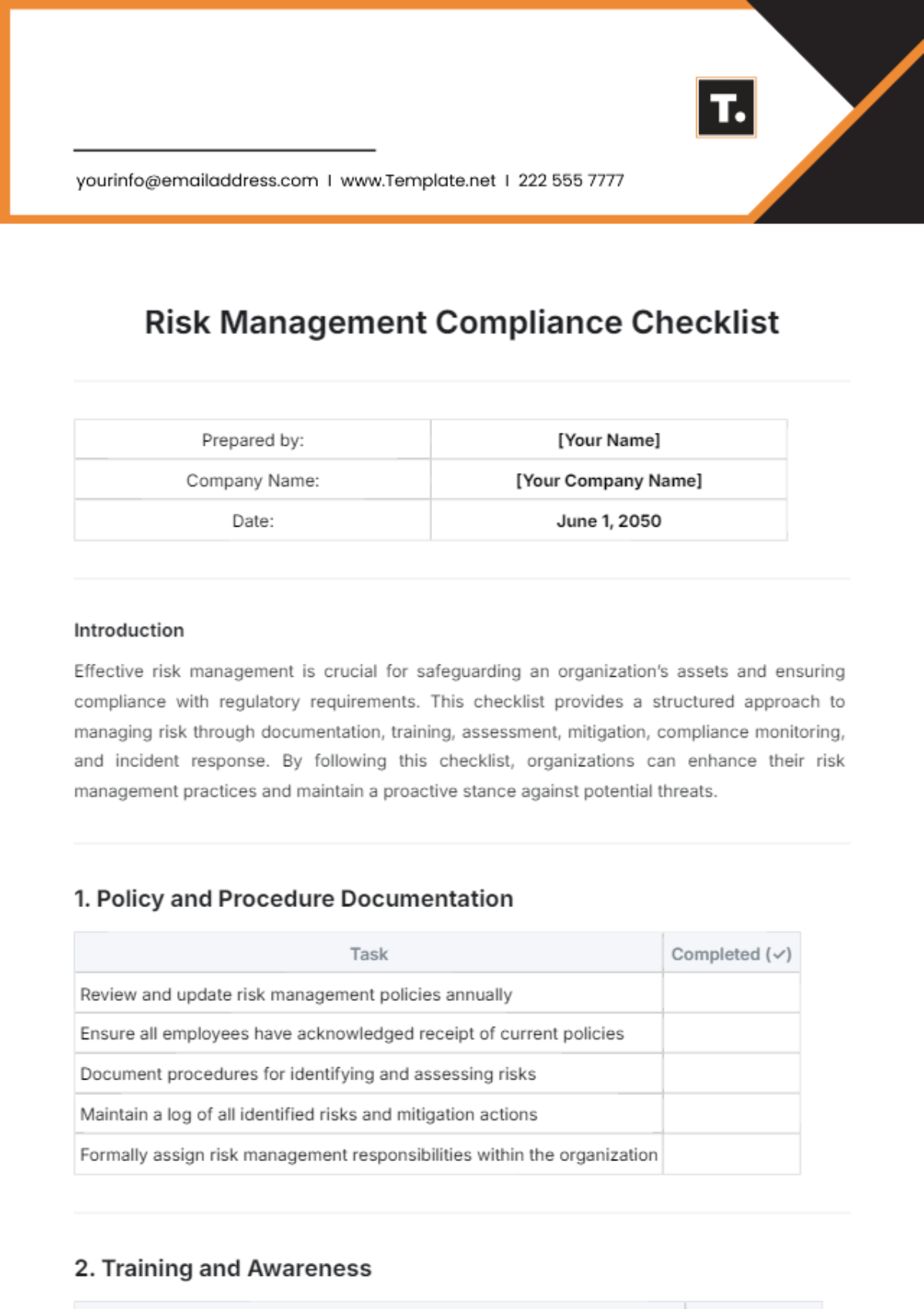
4. Data Protection
A. Data Encryption
Encrypt sensitive data both in transit and at rest using strong encryption algorithms.
Implement encryption protocols such as SSL/TLS for secure communication channels.
Securely manage encryption keys and certificates to prevent unauthorized access.
B. Data Backup and Recovery
Regularly back up critical data and systems to secure and offsite locations.
Test data backup and recovery procedures to ensure data integrity and availability.
Develop and maintain a comprehensive data retention policy.
C. Data Loss Prevention (DLP)
Deploy DLP solutions to monitor and prevent unauthorized data exfiltration.
Define and enforce policies to classify and protect sensitive data.
Monitor and analyze data access and usage patterns for suspicious activities.
5. Infrastructure Audit
A. Hardware Inventory
Maintain an inventory of all hardware assets, including servers, routers, and endpoints.
Conduct regular audits to verify the presence and integrity of hardware assets.
Update hardware inventory records to reflect changes in the infrastructure.
B. Software Inventory
Maintain an inventory of all software applications and versions deployed in the infrastructure.
Conduct regular audits to identify unauthorized or unapproved software installations.
Ensure that software licenses are valid and up-to-date.
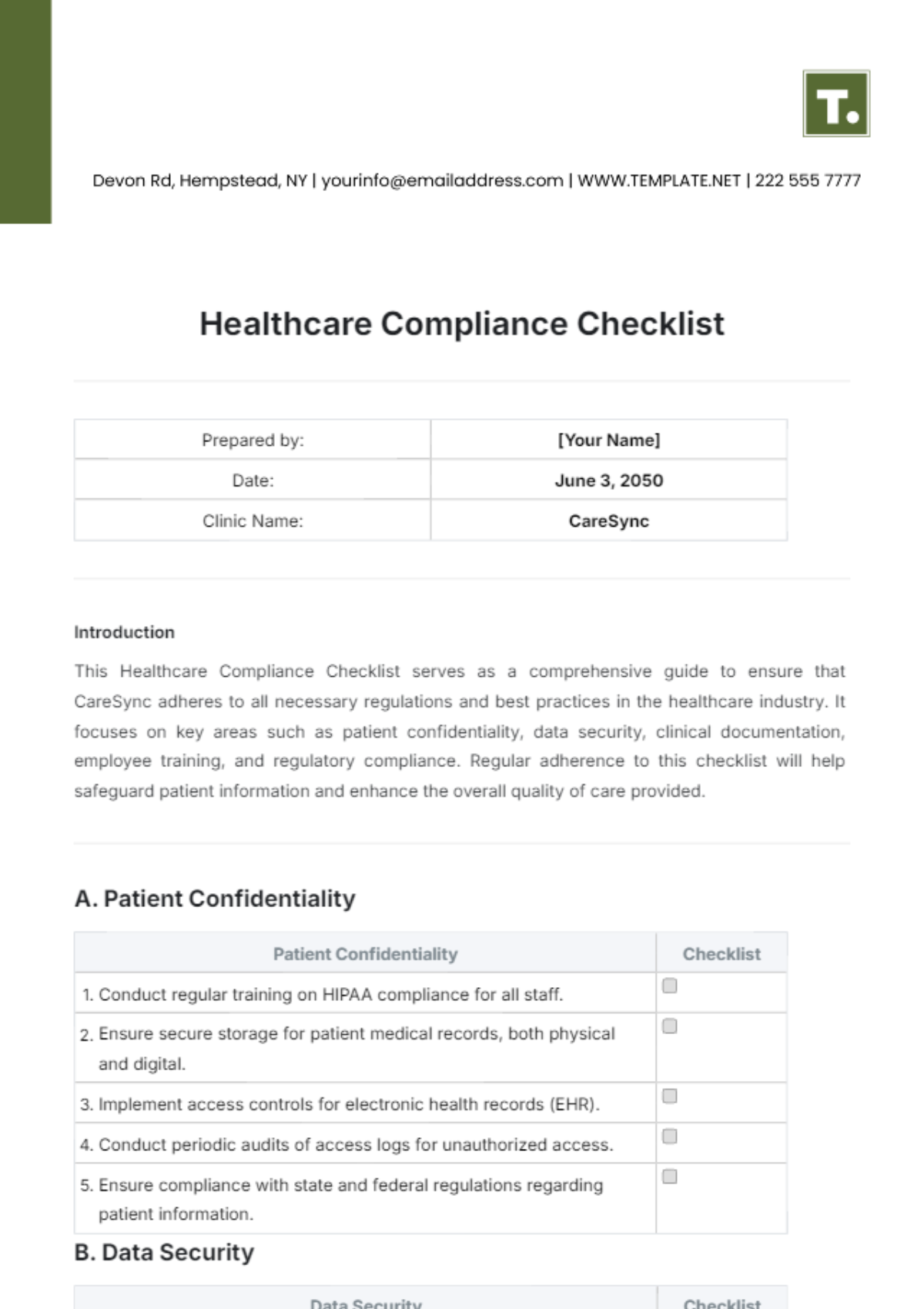
6. Security Awareness Training
A. Employee Training
Provide cyber security awareness training to all employees.
Educate employees about common cyber threats, phishing attacks, and social engineering tactics.
Conduct periodic security awareness assessments and simulations.
B. Incident Response Training
Train employees on how to recognize and report security incidents promptly.
Establish incident response procedures and protocols for handling security breaches.
Conduct regular drills and exercises to test incident response readiness.
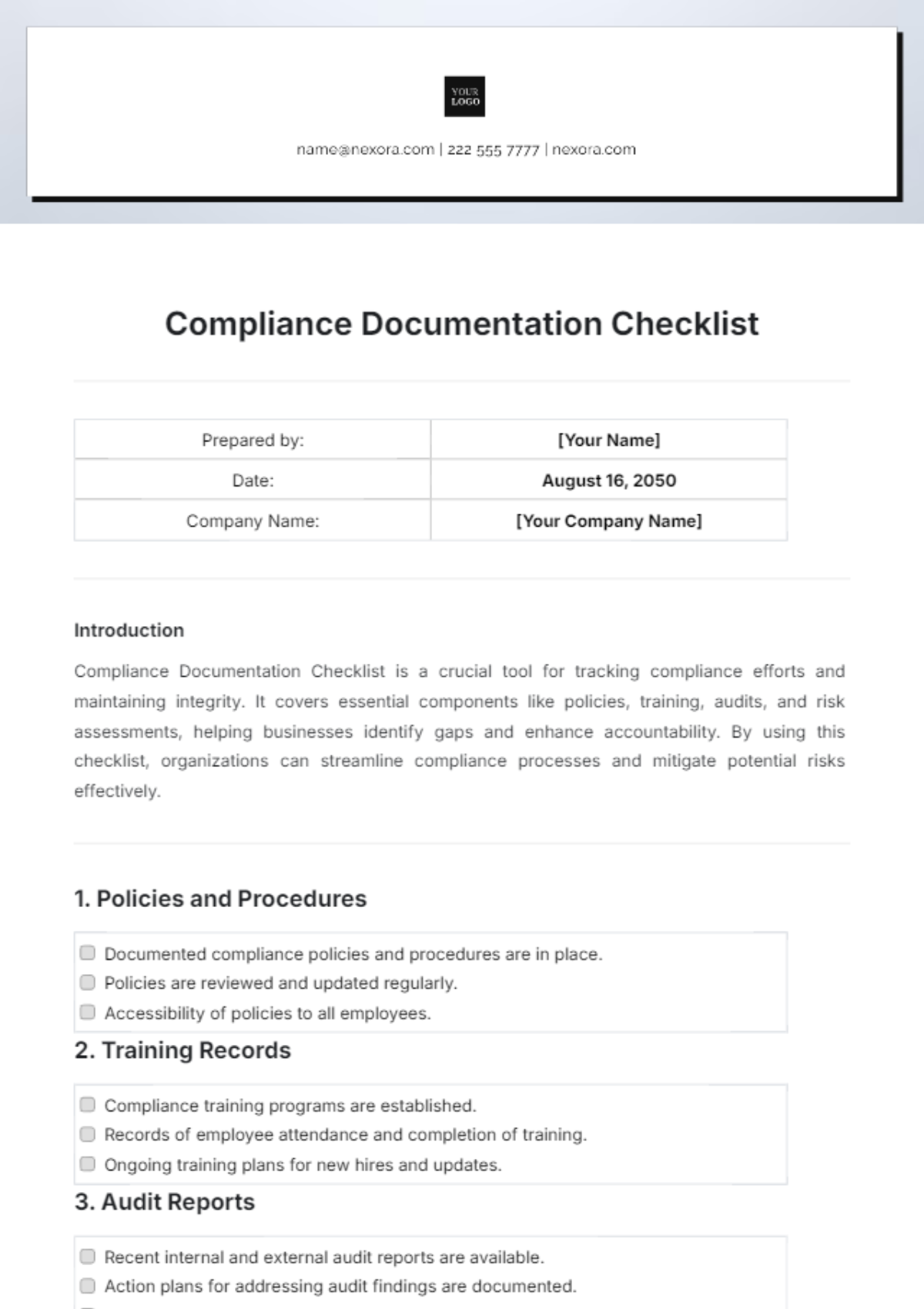
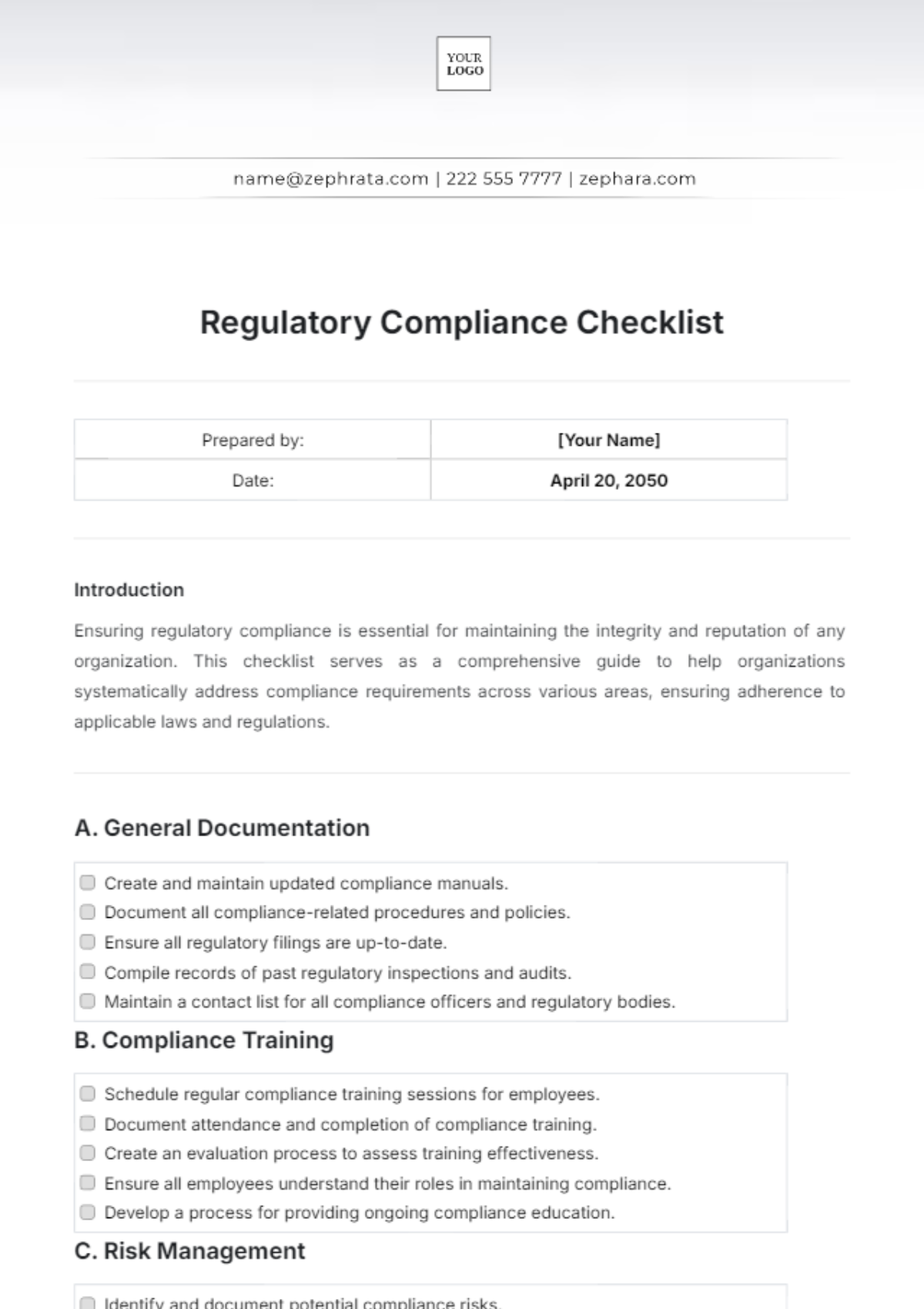
7. Regulatory Compliance
Compliance Assessment
Ensure compliance with relevant regulations and industry standards (e.g., GDPR, HIPAA, PCI DSS).
Conduct regular compliance assessments and audits to identify gaps and ensure adherence.
Maintain documentation of compliance efforts and remediation actions.
8. Signature
By signing below, you acknowledge that you have reviewed and understand the contents of this Cyber Security Compliance Checklist.

[YOUR NAME]
[YOUR COMPANY NAME]
[YOUR COMPANY ADDRESS]
Date: [DATE]