Architecture Monitoring Checklist
This Architecture Monitoring Checklist ensures ongoing compliance and quality control. Users should diligently follow each item to continuously assess and document architectural integrity, performance, and adherence to standards, ensuring all aspects of the monitoring process are thoroughly addressed.
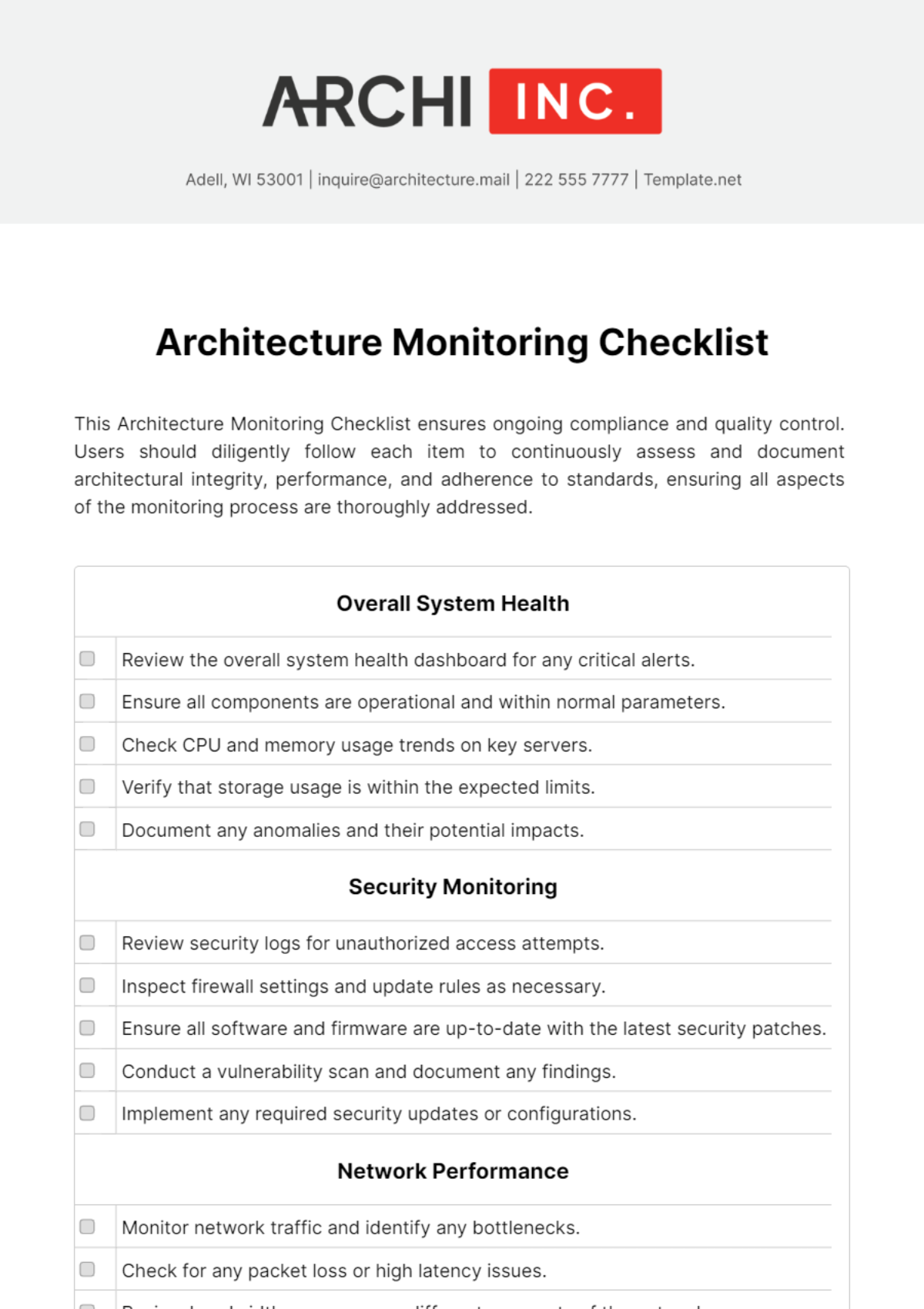
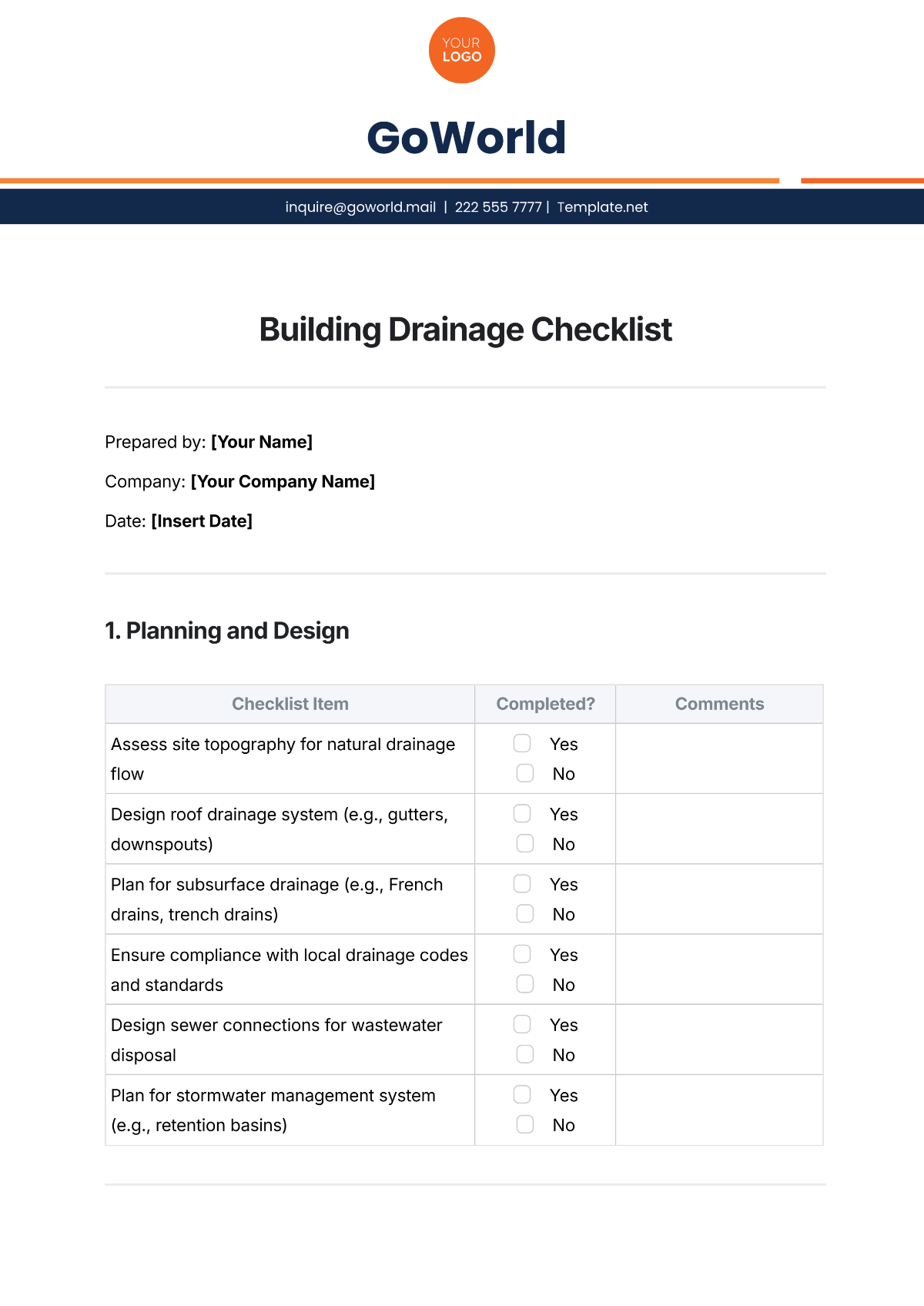
Overall System Health | |
Review the overall system health dashboard for any critical alerts. | |
Ensure all components are operational and within normal parameters. | |
Check CPU and memory usage trends on key servers. | |
Verify that storage usage is within the expected limits. | |
Document any anomalies and their potential impacts. | |
Security Monitoring | |
Review security logs for unauthorized access attempts. | |
Inspect firewall settings and update rules as necessary. | |
Ensure all software and firmware are up-to-date with the latest security patches. | |
Conduct a vulnerability scan and document any findings. | |
Implement any required security updates or configurations. | |
Network Performance | |
Monitor network traffic and identify any bottlenecks. | |
Check for any packet loss or high latency issues. | |
Review bandwidth usage across different segments of the network. | |
Verify the redundancy setup is functional and tested. | |
Document and address any performance issues identified. | |
Application Performance | |
Monitor application performance metrics such as response time. | |
Identify and diagnose any application-level errors. | |
Ensure sufficient application resource allocation. | |
Analyze database performance and optimize queries as needed. | |
Document any application performance bottlenecks and plan remediation. | |
Backup and Recovery | |
Verify that backup jobs run successfully and without errors. | |
Check the integrity and accessibility of backup files. | |
Ensure that recovery plans are up-to-date and tested regularly. | |
Document any issues found during backup and recovery tests. | |
Plan and execute any necessary adjustments to backup schedules or methods. | |