Free Printable Cybersecurity Incident Report

Prepared by: [Your Name]
I. Executive Summary
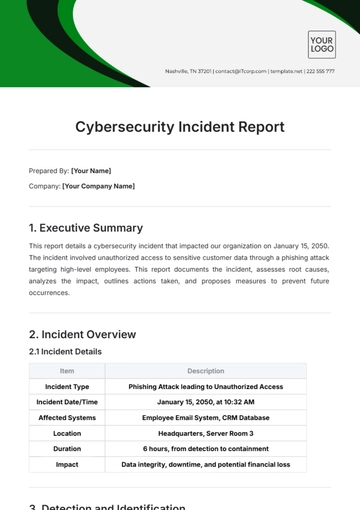
This report outlines the details of a cybersecurity incident that occurred on October 15, 2023. The breach involved unauthorized access to sensitive customer data at [YOUR COMPANY NAME]. The objective of this report is to document the event, analyze the impact, response, and recovery actions, and provide recommendations to mitigate future risks.
II. Incident Description
1. Introduction
The incident was detected by the IT security team on October 15, 2023, at approximately 10:00 AM. Anomalous behavior was identified in the network traffic indicating a potential breach. The incident involved unauthorized access to the internal server, compromising personal and financial customer data.
2. Timeline of Events
Time | Event |
|---|---|
October 15, 2023, 10:00 AM | Suspicious network activity detected |
October 15, 2023, 10:30 AM | Incident response team activated |
October 15, 2023, 11:00 AM | Confirmed unauthorized access |
October 15, 2023, 12:00 PM | Isolation of affected systems initiated |
3. Type of Attack
The attack was identified as a sophisticated phishing attempt that exploited vulnerabilities in the email system. The attackers used social engineering techniques to gain access to user credentials, subsequently infiltrating company servers.
III. Impact Analysis
1. Data Compromised
The breach resulted in the unauthorized access and potential exfiltration of the following data:
Customer personal information (names, addresses, phone numbers)
Financial data including credit card information
Internal communications and operational documents
2. Business Operations
The incident caused temporary disruption to business operations as the affected systems were taken offline to prevent further damage. This affected customer service response times and resulted in some loss of customer trust.
IV. Response and Recovery
1. Immediate Actions
Upon detection, the security team immediately isolated the compromised systems and secured entry points. A comprehensive investigation was launched to determine the scope and origin of the breach.
2. Long-term Measures
The following long-term measures have been implemented to strengthen security:
Enhanced email filtering and monitoring systems
Regular cybersecurity training and awareness programs for employees
Upgrade of network security protocols and infrastructure
V. Recommendations
1. Preventive Measures
To prevent future incidents, it is recommended that [YOUR COMPANY NAME] implements multi-factor authentication across all sensitive systems, conducts regular security audits, and maintains an up-to-date incident response plan.
2. Awareness Programs
Continuous education and training programs should be established to ensure employees stay informed about the latest cybersecurity threats and prevention tactics. This should include phishing simulation exercises and awareness workshops.
VI. Conclusion
The cybersecurity incident, though contained, highlighted several vulnerabilities within [YOUR COMPANY NAME]'s IT infrastructure. Through the actions outlined in this report, the company aims to bolster its defense mechanisms, ensuring greater protection of customer and corporate data moving forward.
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
The Printable Cybersecurity Incident Report Template from Template.net offers an editable and customizable solution for documenting security incidents. Easily modify the template to fit your organization's needs with our AI Editable Tool. Whether you're responding to a breach or a threat, this professional template ensures clear, accurate reporting, saving time and enhancing efficiency.
You may also like
- Sales Report
- Daily Report
- Project Report
- Business Report
- Weekly Report
- Incident Report
- Annual Report
- Report Layout
- Report Design
- Progress Report
- Marketing Report
- Company Report
- Monthly Report
- Audit Report
- Status Report
- School Report
- Reports Hr
- Management Report
- Project Status Report
- Handover Report
- Health And Safety Report
- Restaurant Report
- Construction Report
- Research Report
- Evaluation Report
- Investigation Report
- Employee Report
- Advertising Report
- Weekly Status Report
- Project Management Report
- Finance Report
- Service Report
- Technical Report
- Meeting Report
- Quarterly Report
- Inspection Report
- Medical Report
- Test Report
- Summary Report
- Inventory Report
- Valuation Report
- Operations Report
- Payroll Report
- Training Report
- Job Report
- Case Report
- Performance Report
- Board Report
- Internal Audit Report
- Student Report
- Monthly Management Report
- Small Business Report
- Accident Report
- Call Center Report
- Activity Report
- IT and Software Report
- Internship Report
- Visit Report
- Product Report
- Book Report
- Property Report
- Recruitment Report
- University Report
- Event Report
- SEO Report
- Conference Report
- Narrative Report
- Nursing Home Report
- Preschool Report
- Call Report
- Customer Report
- Employee Incident Report
- Accomplishment Report
- Social Media Report
- Work From Home Report
- Security Report
- Damage Report
- Quality Report
- Internal Report
- Nurse Report
- Real Estate Report
- Hotel Report
- Equipment Report
- Credit Report
- Field Report
- Non Profit Report
- Maintenance Report
- News Report
- Survey Report
- Executive Report
- Law Firm Report
- Advertising Agency Report
- Interior Design Report
- Travel Agency Report
- Stock Report
- Salon Report
- Bug Report
- Workplace Report
- Action Report
- Investor Report
- Cleaning Services Report
- Consulting Report
- Freelancer Report
- Site Visit Report
- Trip Report
- Classroom Observation Report
- Vehicle Report
- Final Report
- Software Report